Configure IAM Roles for AWS with CloudFormation Templates
Skyhigh CASB uses AWS CloudFormation Templates to create the IAM roles required to configure AWS accounts. Permissions for all Skyhigh CASB features are consolidated in CloudFormation Templates. You do not have to track and provide permissions separately for each feature.
This topic describes the permissions required to configure AWS with Skyhigh CASB using the templates.
For more information, see AWS CloudFormation Templates.
About CloudFormation Templates
Use CloudFormation Templates to create IAM roles and add the permissions required to configure an AWS account for use with Skyhigh CASB.
The templates contain permissions for all supported Skyhigh CASB features in separate sections.
If you have not enabled a feature, remove the permissions for that feature by deleting the appropriate section from the template before you create the Skyhigh CASB IAM role.
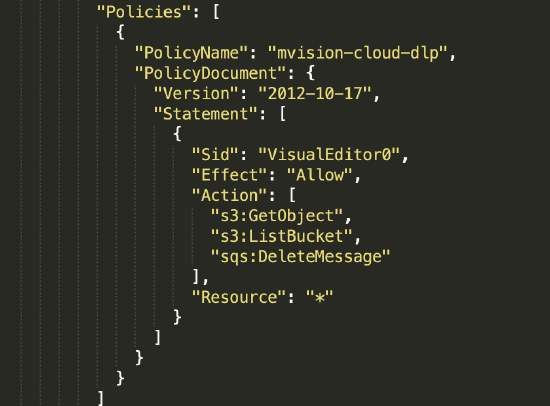
For example, if you do not want to enable DLP, remove the section "PolicyName": "mvision-cloud-dlp" from the template before creating the IAM role, as shown:
The templates expect the following inputs:
- Role Name. The Skyhigh CASB IAM role name.
- Account ID. Skyhigh CASB AWS Account ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
- External ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
AWS Managed Policy SecurityAudit
The SecurityAudit policy is the recommended permission model for Skyhigh CASB.
The SecurityAudit policy grants permissions to view configuration data for many AWS services and to review their logs, so you do not have to provide permissions for each AWS service individually.
Download the CloudFormation Template to create the Skyhigh CASB IAM role with SecurityAudit policy and additional required permissions.
The templates expect the following inputs:
- Role Name. The Skyhigh CASB IAM role name.
- Account ID. Skyhigh CASB AWS Account ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
- External ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
If you do not want to use the template to create the Skyhigh CASB IAM role, then follow the steps in Integrate AWS and attach the SecurityAudit policy along with the following additional permissions for security configuration audit:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"sqs:ReceiveMessage",
"sqs:DeleteMessage",
"s3:GetObjectVersion",
"logs:FilterLogEvents",
"logs:GetLogEvents",
"logs:GetLogGroupFields",
"logs:GetLogRecord",
"es:ListTags",
"elasticache:ListTagsForResource",
"eks:DescribeNodegroup"
],
"Resource": "*"
}
]
}
If you have enabled features other than Configuration Audit, then download the template and copy the appropriate sections for the additional permissions, as follows:
- DLP & Malware. Copy the permissions from the section "PolicyName": "mvision-cloud-dlp".
- Near Real Time DLP. Copy the permissions from the section "PolicyName": "mvision-permissions-for-near-real-time-dlp"
- Container Vulnerability Scan. Copy the permissions from the section "PolicyName": "mvision-cloud-vulnerability-scan".
- Container Security. Copy the permissions from the section "PolicyName": "mvision-permissions-for-container-security".
- VPC Flow Logs. Copy the permissions from the section "PolicyName":"mvision-cloud-config-audit-vpc-flow-log".
NOTE: Permissions for SSM are required only for runtime Docker policies. For more information, see Install the SSM Agent on Amazon EC2 Instances.
AWS Managed Policy ReadOnlyAccess
The ReadOnlyAccess policy provides read-only access to all AWS services and resources. Using this policy, you do not need to track and provide permissions for each AWS service individually. And whenever a new service is supported, the permission for it is also added automatically.
Download the CloudFormation Template to create the Skyhigh CASB IAM role with the ReadOnlyAccess permission attached.
The templates expect the following inputs:
- Role Name. The Skyhigh CASB IAM role name.
- Account ID. Skyhigh CASB AWS Account ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
- External ID. You can find this in Settings > Service Management under Setup in your AWS instance. Click Edit.
If you do not want to use the template to create the Skyhigh CASB IAM role, follow the steps in Integrate AWS and attach the ReadOnlyAccess managed policy.
If you have enabled DLP, you must also provide the following additional permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"sqs:DeleteMessage"
],
"Resource": "*"
}
]
}
Minimum Permissions
Use Minimum Permissions only if you do not want to configure your AWS account with SecurityAudit or ReadOnlyAccess based permissions, and you want to provide granular permissions for each AWS service and features supported by Skyhigh CASB.
IMPORTANT: This option is not recommended. If you use Minimum Permissions, as new policies, support for new AWS services, or new features of Skyhigh CASB are added, you will need to keep a track of a long list of additional permissions, which could cause missing permissions related issues.
We recommend that you download and use the Cloud Formation Template to create a custom IAM role with Minimum Permissions.
The template expects the following inputs:
- Role Name. The Skyhigh CASB IAM role name.
- Account ID. Skyhigh CASB AWS Account ID. You can find this in Settings > Service Management under Setup in your AWS instance.
- External ID. You can find this in Settings > Service Management under Setup in your AWS instance.
If you do not want to use the template to create the Skyhigh CASB IAM role, follow the steps in Integrate AWS.
Download the template and copy the appropriate sections for the minimum permissions for each Skyhigh CASB feature:
- Security Configuration Audit. Copy the permissions from the section "PolicyName": "mvision-cloud-config-audit".
- DLP & Malware . Copy the permissions from the section "PolicyName": "mvision-cloud-dlp".
- Activity Monitoring. Copy the permissions from the section "PolicyName": "mvision-cloud-activity-monitoring".
- Container Vulnerability Scan. Copy the permissions from the section "PolicyName": "mvision-cloud-vulnerability-scan".
- Container Security. Copy the permissions from the section "PolicyName": "mvision-permissions-for-container-security".
- VPC Flow Logs. Copy the permissions from the section "PolicyName":"mvision-cloud-config-audit-vpc-flow-log".
- Near Real-Time Configuration Audit. For permissions and instructions, see Near Real-Time Configuration Audit.
Migrate to the SecurityAudit Role
If you are currently using ReadOnlyAccess or Minimum Permissions to configure your AWS account, and you want to migrate to the SecurityAudit role, follow these steps:
- Assign the SecurityAudit AWS managed policy to the Skyhigh CASB IAM role.
- Assign the additional permissions detailed in AWS Managed Policy SecurityAudit.
- Remove all the other permissions from the IAM role (except SecurityAudit).
Change History
|
Release |
Changes |
|---|---|
| 5.3.2 | Added permissions required for the new resource type - AWS CodeBuild |
|
5.2.1
|
Updated CFTs to include the permissions required for the VPC flow logs |

