Integrate Microsoft Azure with Skyhigh CASB
Before you enable Microsoft Azure, make sure that you have an Azure account with permissions that allow you to read security configurations of Azure resources to be monitored by Skyhigh CASB.
Note: The Skyhigh single sign-on (SSO) users are not supported for the Microsoft Azure onboarding.
Required Roles in Azure
Users require the following roles in Azure:
- Config Audit
- Reader
- Reader and Data Access
NOTE: Reader and Data access permission is required for the Config Audit policy "Azure blob storage containers should not be world readable".
- Activity Monitoring
- Reader
- Reader and Data Access
- DLP and Malware (including Quarantine)
- Reader and Data Access
NOTE: If you have any firewall or network restrictions for the Azure Subscriptions or Storage Accounts then Skyhigh CASB IP addresses should be added to the allow list. For details, see Skyhigh CASB - IP Addresses.
Configure Roles in Azure
- Log in to the Microsoft Azure Portal.
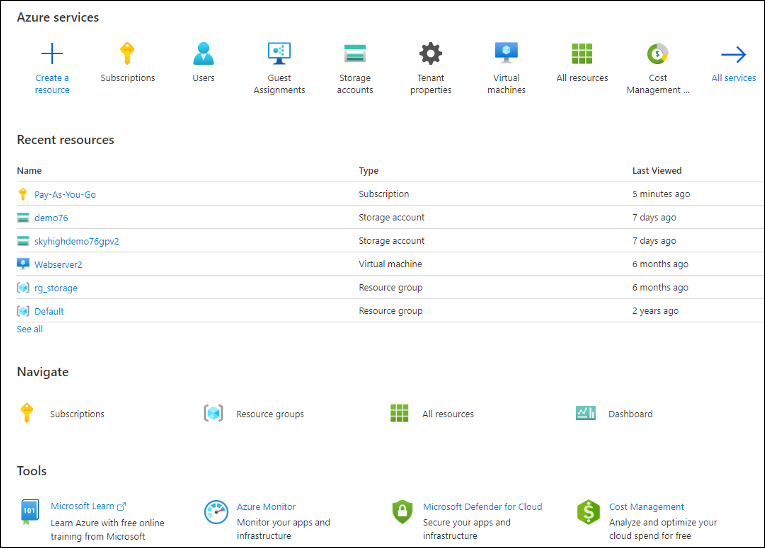
- Under Azure services, click Subscriptions.
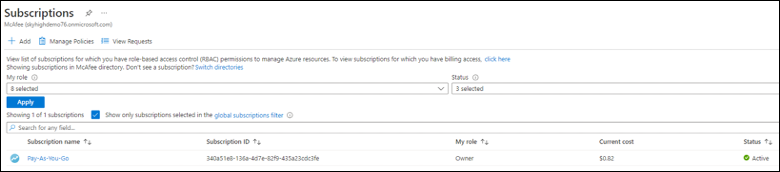
- Select the Subscription from the list.
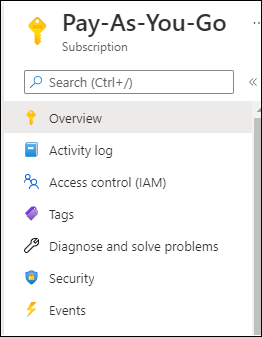
- Select to Access control (IAM)
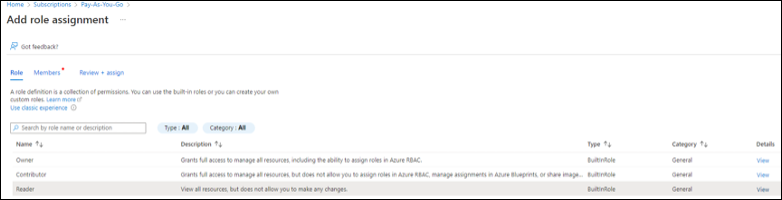
- On the Check access tab, click Add role assignment.
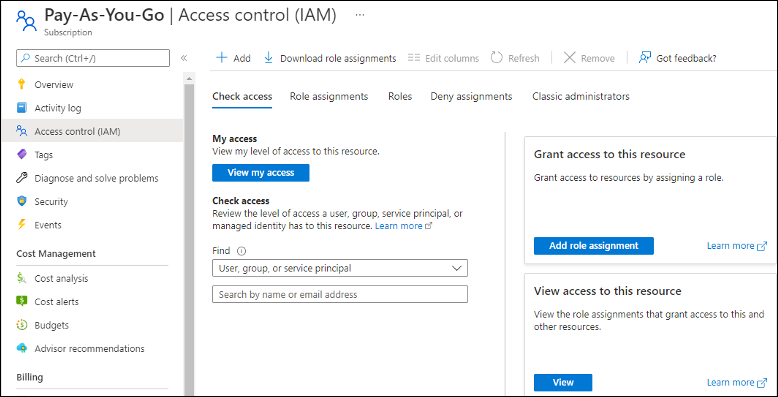
- As the role, select Reader, then click Next.
- Select Members to reader permission, then click Next.
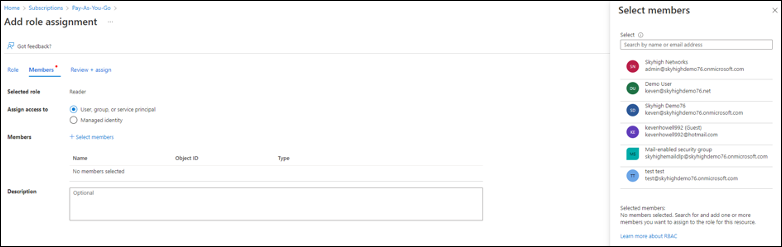
- Select User. The User displays under the name field with the Object ID. Then click Next.
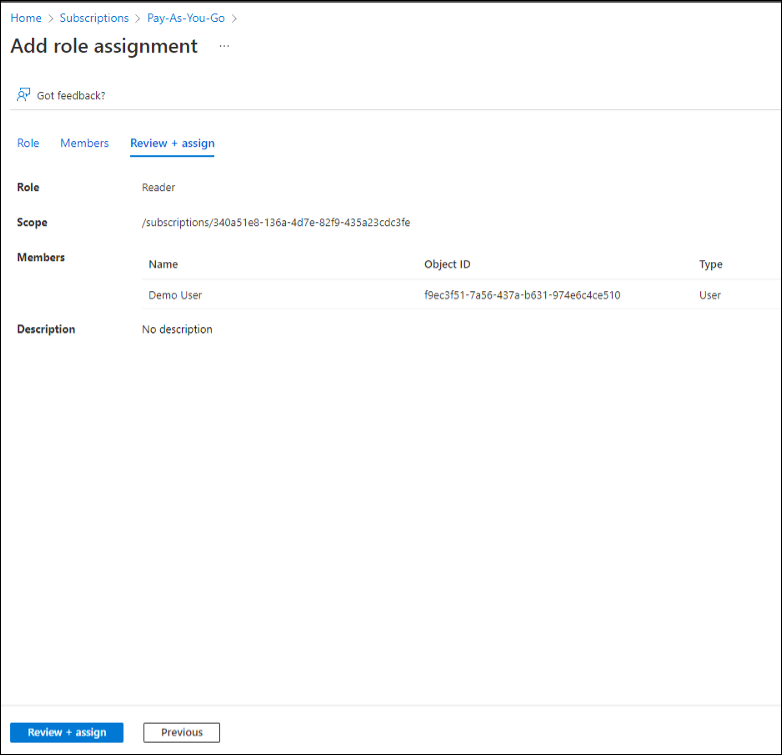
- Review and assign the role assigment, the click Review + assign.
Enable Azure
To enable Azure:
- Go to Settings > Service Management.
- Click Add Service Instance and select Microsoft Azure.
- Add an Instance Name and click Done.

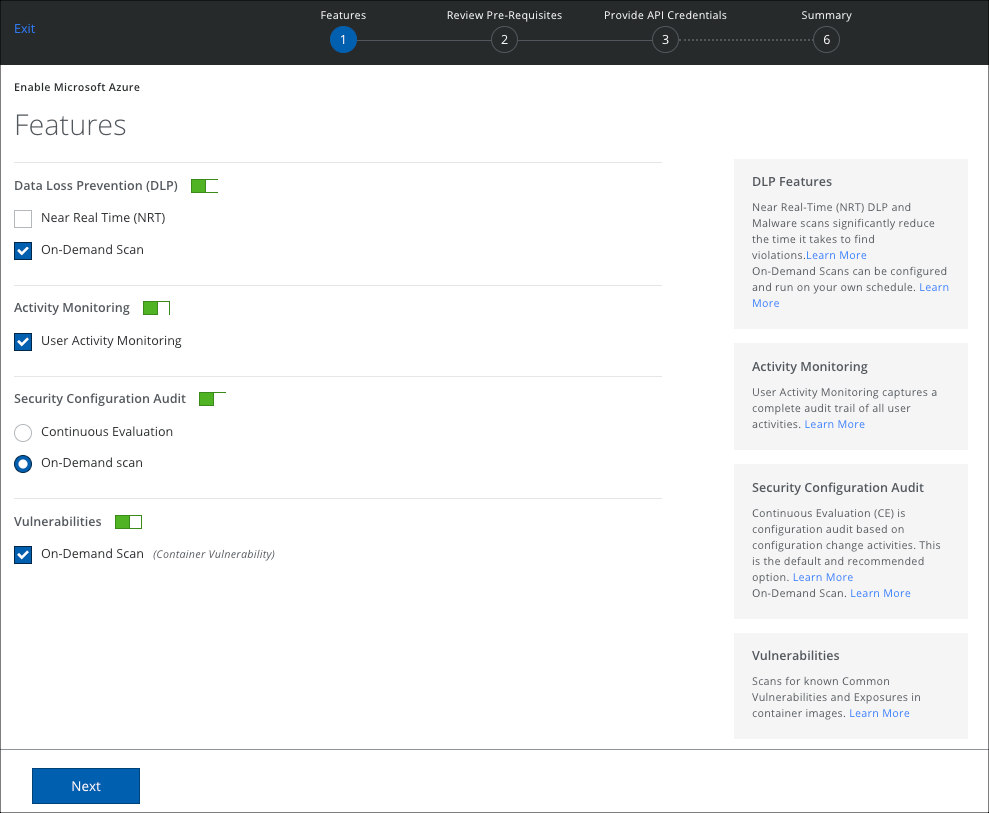
- Select the features you want to enable for your Azure account.
- DLP. Use On-Demand Scans to examine cloud services for content that violates your policies and support targeted investigations. Enable On-Demand Scan to run your scan immediately or set the scan schedule to daily or weekly.
- Activity Monitoring. Activity Monitoring allows forensic auditing and investigation of individual activities.
- Security Configuration Audit. Security Configuration Audit allows your policy team to monitor and discover if your cloud services have been configured per industry best practices.
- Vulnerabilities. Scans for Common Vulnerabilities and Exposures in container images.
- Review the mandatory Pre-requisites, click the checkbox, and click Next.
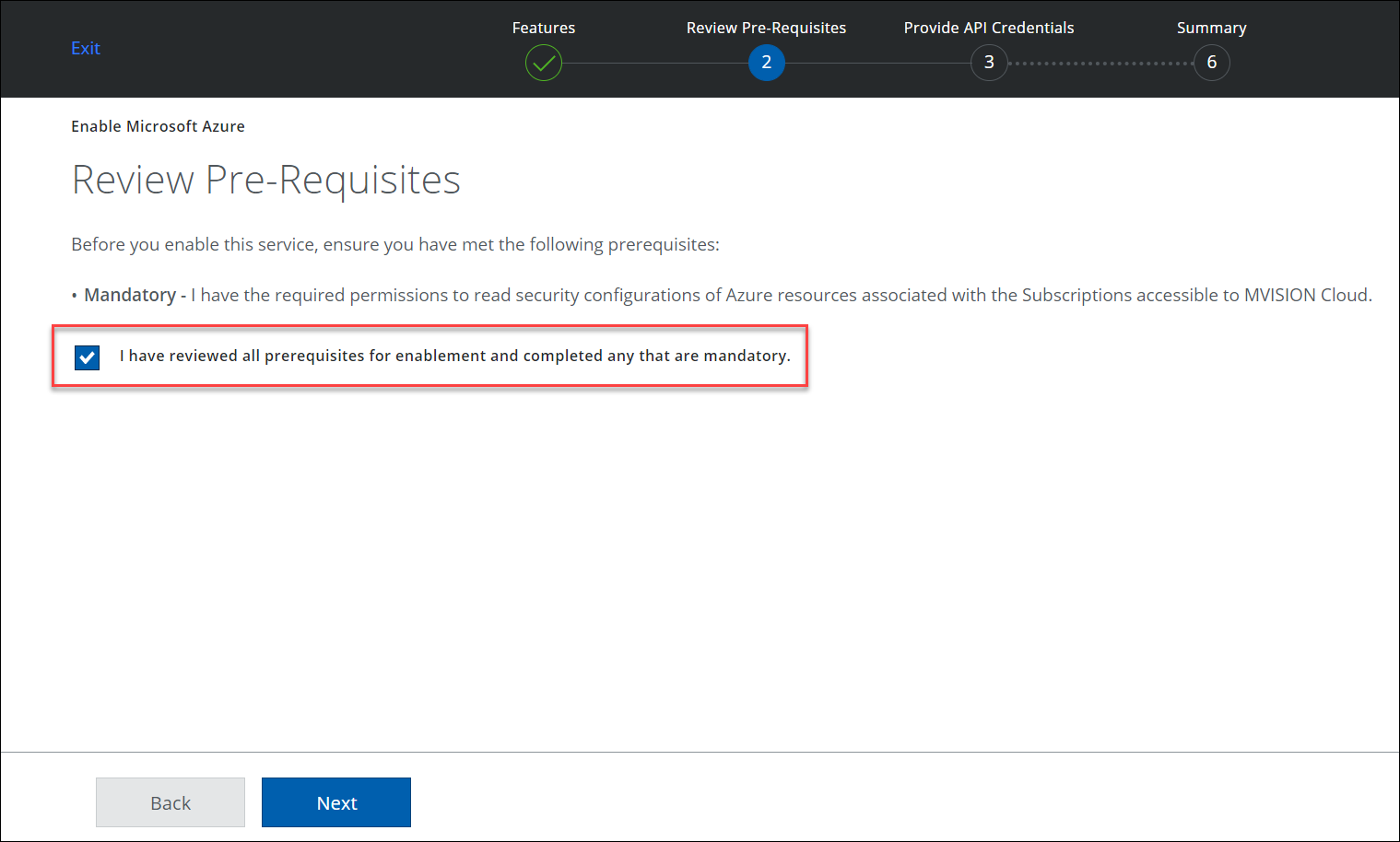
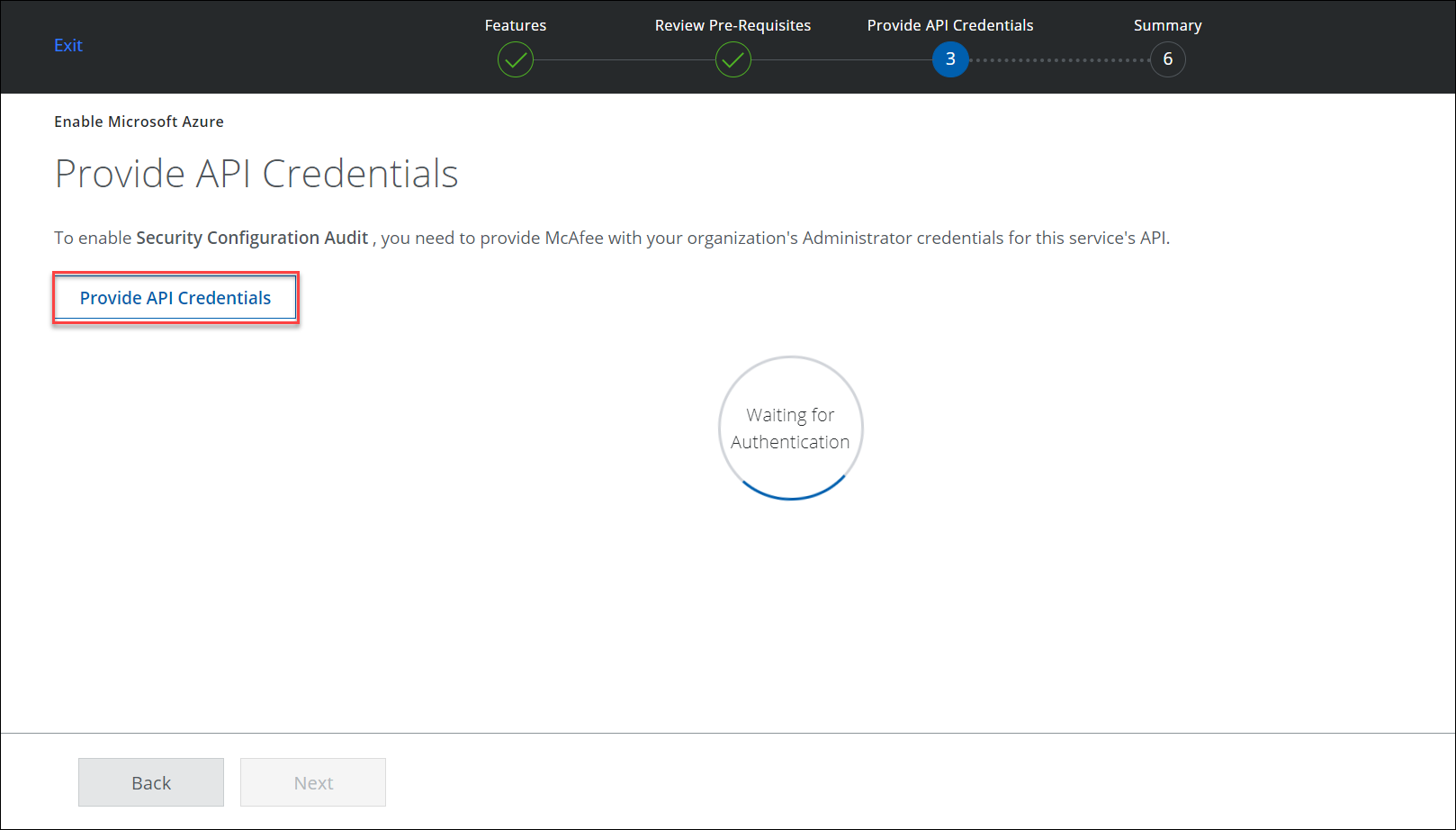
- Click Provide API Credentials.
Microsoft O365 (or Azure) login window appears.
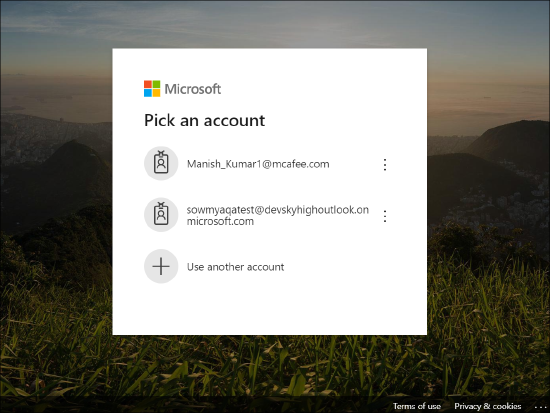
- Enter your O365 (or Azure) credentials, or pick an existing account.
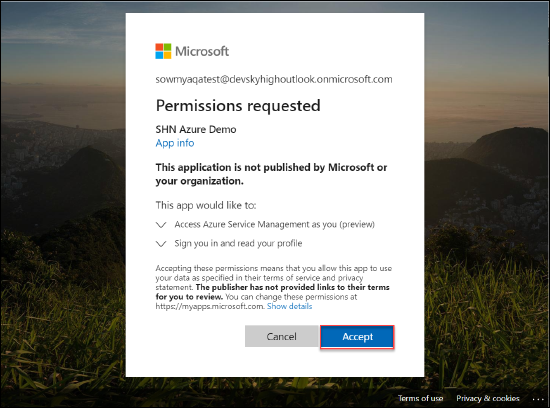
- Review the permissions and click Accept.
- API Access is Enabled. Click Next.
Make sure you have configured the roles in Skyhigh CASB.
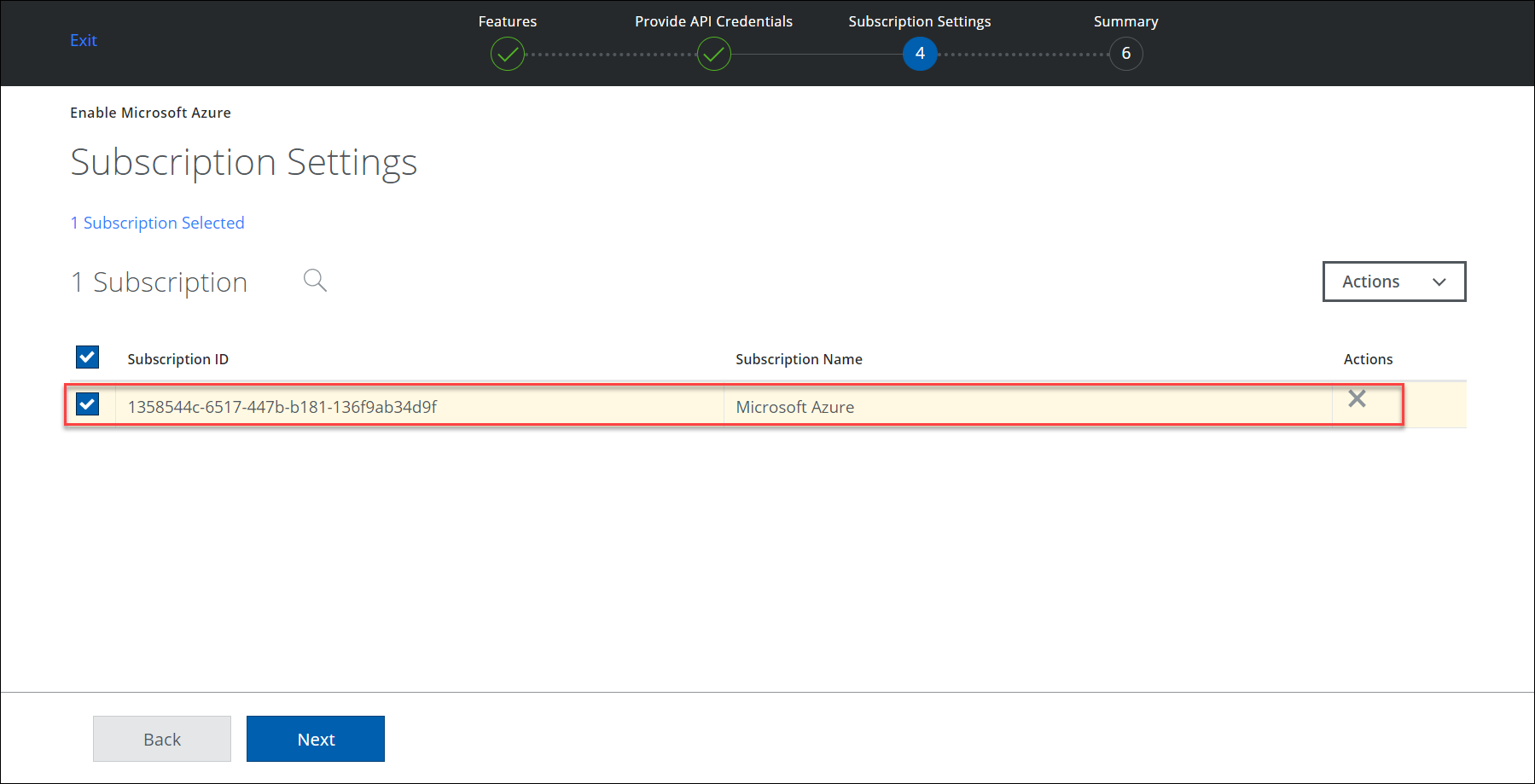
- Select a Subscription ID from the list. Click Next.
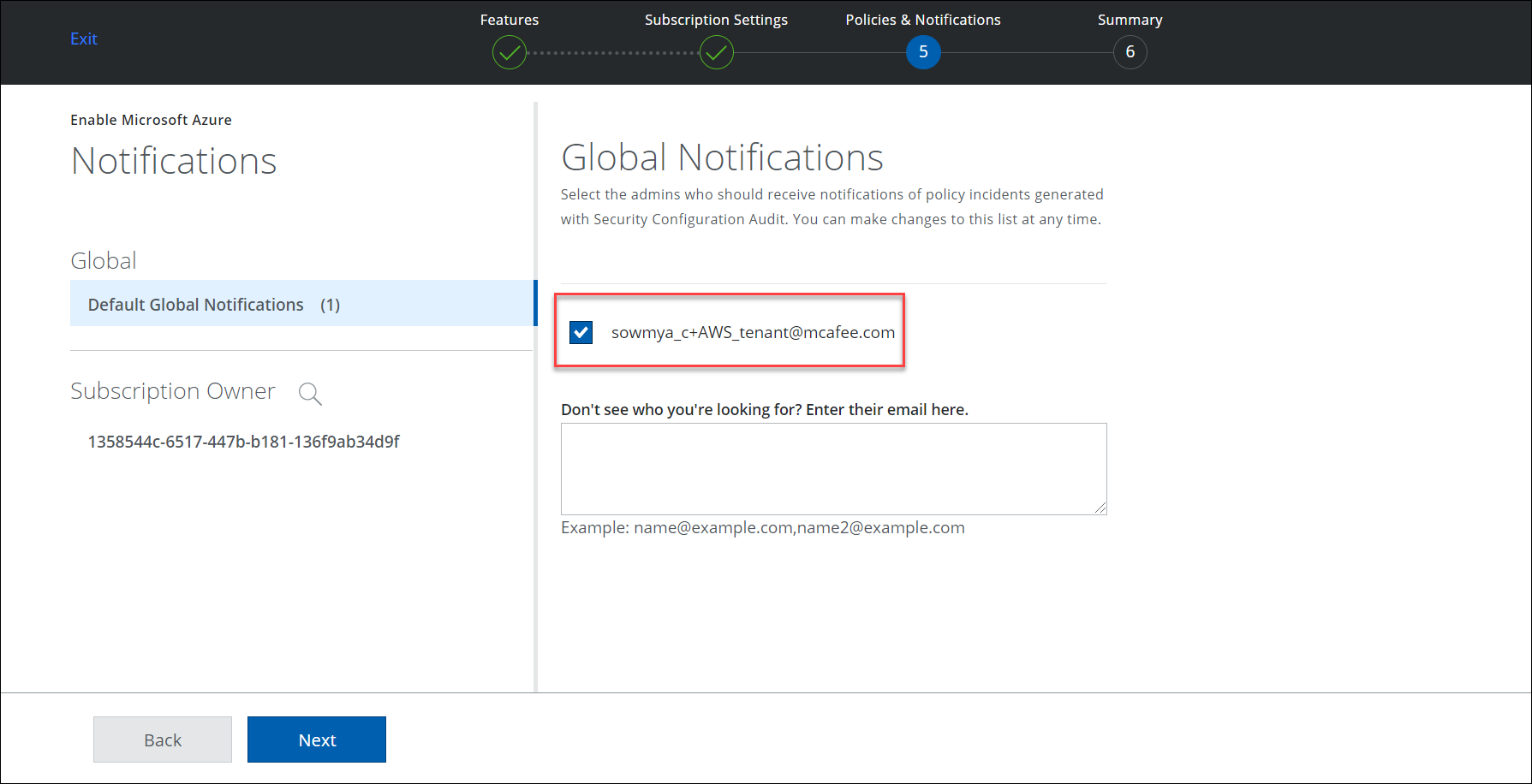
- Select the Subscription Owner's email to notify any Configuration Audit Policy violation incidents. Alternatively, you can manually enter an email in the description box.
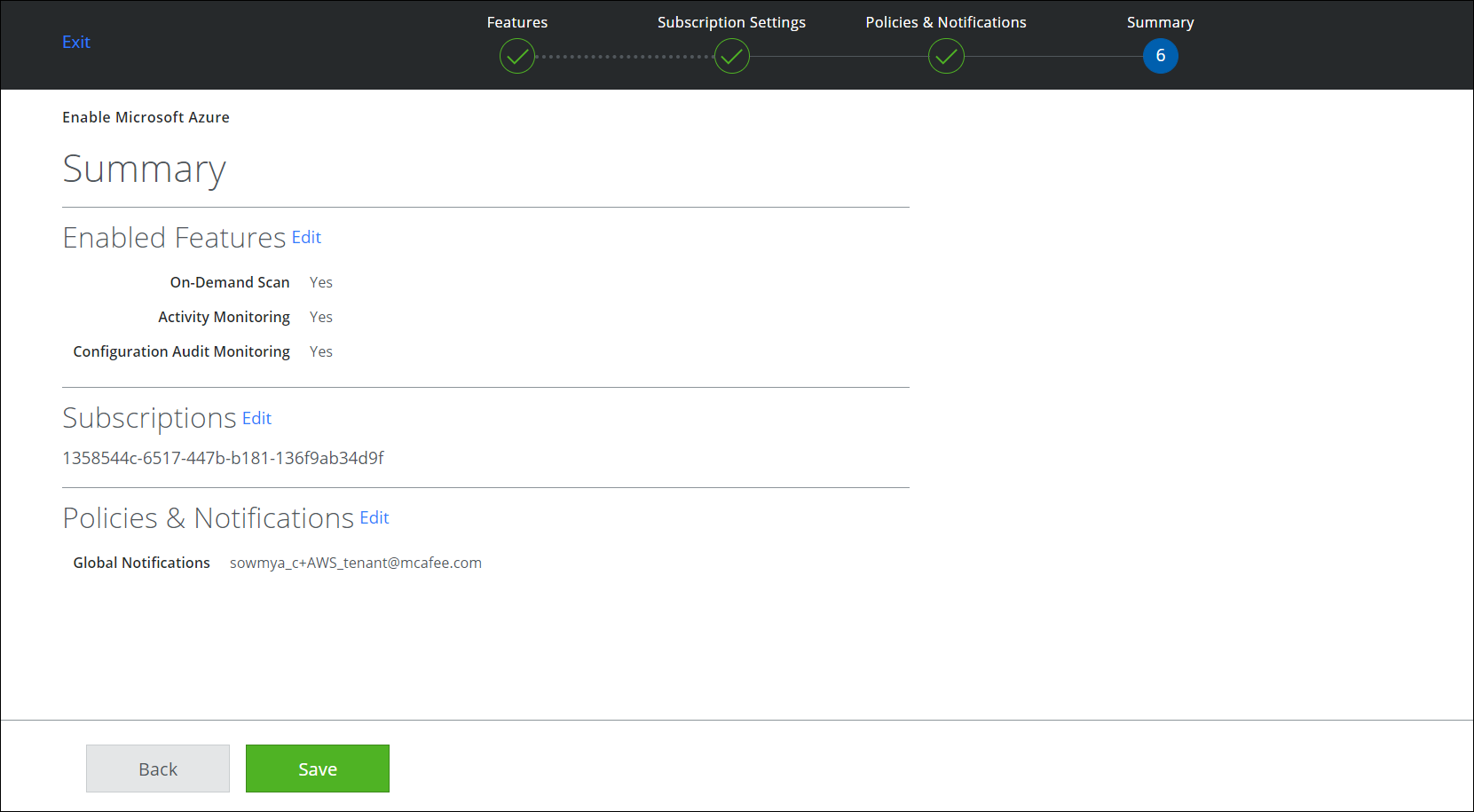
- Review your settings and click Save.
Azure is enabled in the Service Management page.

