Integrate with VMware Workspace ONE UEM
NOTE: The partner name formerly known as Airwatch is now VMware Workspace ONE UEM. So, this topic has been updated with relevant information. However, the screenshots still refer to Airwatch, which will be updated in future releases.
Integrating with VMware Workspace ONE UEM expands the managed/unmanaged device workflow in Skyhigh CASB. Once you complete the integration, configure VMware Workspace ONE UEM to deploy the device and user certificates when a device is enrolled (which requires an external Certificate Authority). When a device enrolls with VMware Workspace ONE UEM , the device UUID is determined. This data is captured and added to the certificate that is provided to the mobile device.
Skyhigh Cloud Connector is configured on-premises to pull device information from VMware Workspace ONE UEM . This provides a user ID database for UUID that is used to provide additional user validation. The information (ID and UUID per user) is retrieved from VMware Workspace ONE UEM via API.
IMPORTANT: A Skyhigh CASB tenant can support only one MDM integration. If your organization requires multiple MDM integrations, leverage the multi-instance feature in Skyhigh CASB and set up each integration in its own instance.
Prerequisites
- Reverse proxy enabled for the cloud service you want to protect
- VMware Workspace ONE UEM instance, which has already been integrated with an Enterprise Certificate Authority
- Skyhigh Cloud Connector virtual machine ready for MDM integration
- Cloud service deployment (Office 365 for example) with a valid user account
- SSO integrated with the cloud service
- SSO configured to use the Skyhigh CASB reverse proxy
Step 1: Create a Certificate Authority in VMware Workspace ONE UEM
- Using the instructions found in Configure Active Directory Certificate Authority in VMware Workspace ONE, create a CA to connect to the Cloud Connector.
- Make sure to choose the following:
- Protocol. Choose ADCS. Use VMware Workspace ONE UEM Cloud Connector (VCC) to connect to the Windows Enterprise Certificate Authority.
- Server Hostname. Enter the FWDN on the server in AWS, co-located with ACC. This must be resolvable to VCC and point to the CA.
- Authority Name. Enter the name of the CA server as shown in the Windows Certificate Authority manager (hostname with the domain prefixed and CA appended).
- Authentication. Choose Service Account using a standard AD user account.
Step 2: Add a Certificate Request Template in VMware Workspace ONE UEM
It is important the request have a subject alternate name (SAN) that includes the DeviceUid. When a device registers with VMware Workspace ONE UEM, the AW agent detects the device UID. This is then included in the certificate request from AW to the CA server. The UID is then included in the provided certificate and this is what Skyhigh CASB needs to see to validate the device certificate.
To Add a Certificate Request:
- Using the instructions found in Add Certificate Template in VMware Workspace ONE UEM, create a Certificate Template.
- Make sure to choose the following:
- Subject Name. Set to CN={EmailAddress}
- SAN type. Choose DNS Name and {DeviceUid}
Step 3: Add Device Profiles in VMware Workspace ONE UEM
Device profiles are created for each device type to be managed by VMware Workspace ONE UEM. Each profile is configured to use the CA server as it's source for credentials.
Instructions are found here:
Step 4: Configure Skyhigh CASB
To enable device certificate checking:
1. Choose Access Control > Device Management.
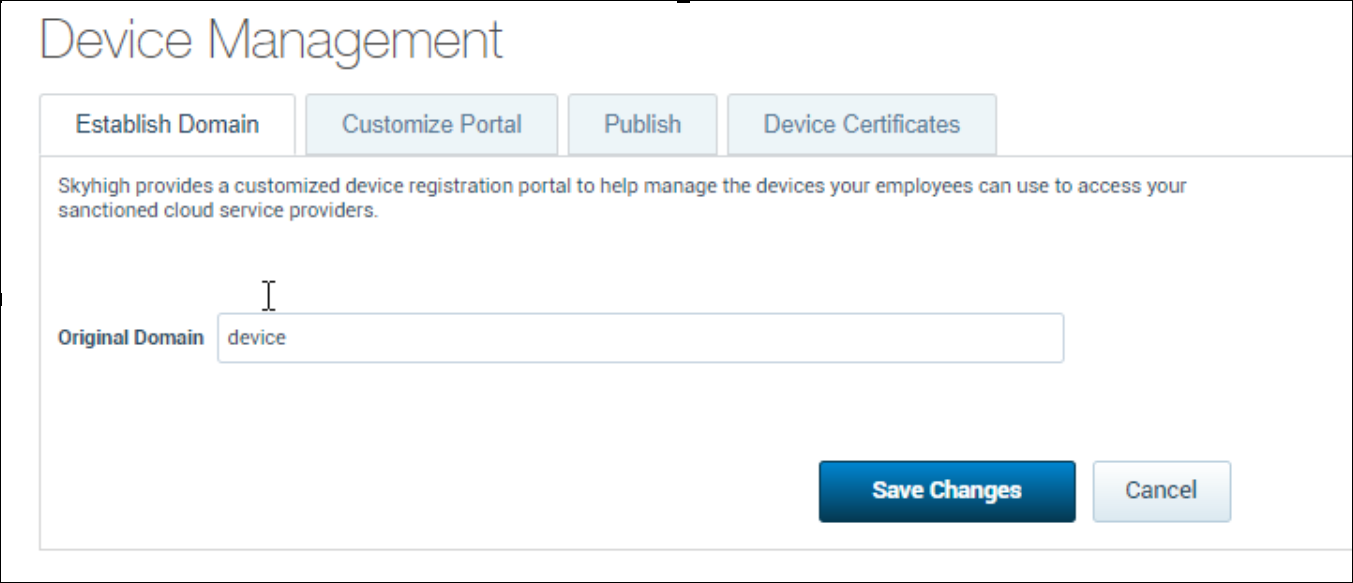
2. Under the Establish Domain tab, enter or verify that the Original domain is set to the device.
3. Under the Customize Portal tab, enable the feature. This feature enables the device UID check. Choose Device Management portal colors.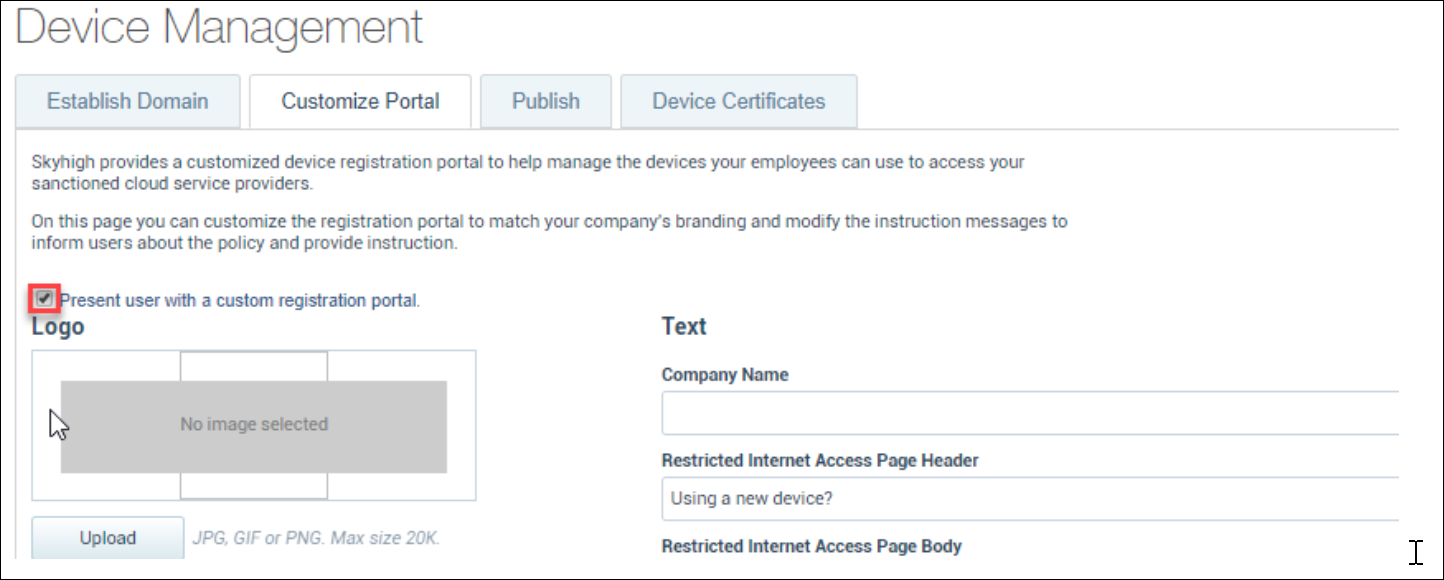
3. Download the VMware Workspace ONE UEM CA file. This is the public certificate of the CA server that signs the mobile device certificates.
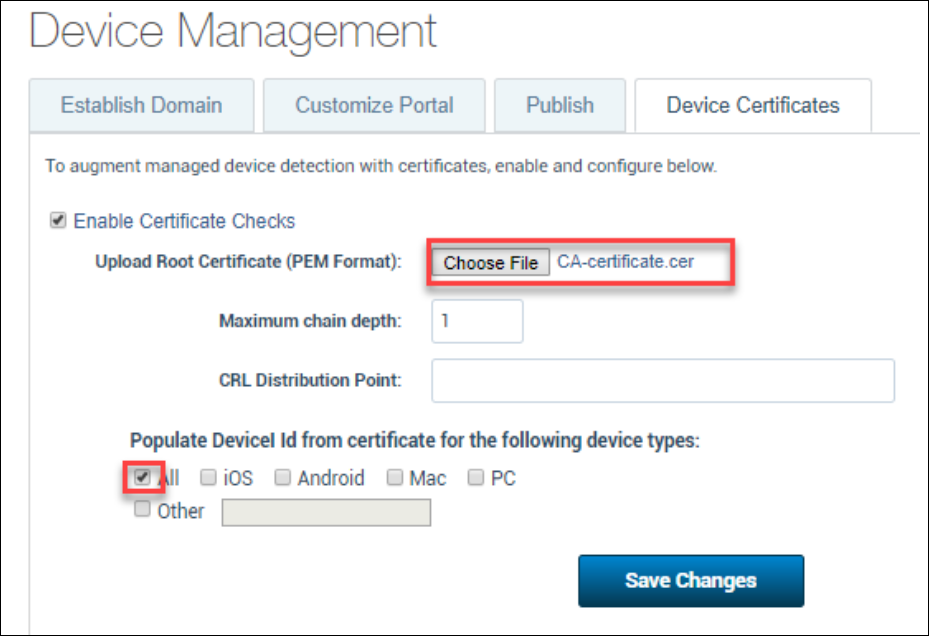
4. Under the Device Certificates tab, upload the CA certificate and set the Populate Device ID from the certificate for the following device types to All.
Step 5: Enable Cloud Access Policies
Cloud Access Control Policies are used to provide the correct behavior for managed and unmanaged devices by creating policies that require an unmanaged device to register before accessing a page, for example. Certificates are OS-agnostic, version-independent, and can be easily revoked or cycled, offering you a great deal of control and flexibility in cloud access management.
Policies are built on conditions (rules) and actions. Conditions are used with IS or IS NOT arguments to define the specific situation when a policy should be enacted. Actions then determine what happens when a policy is enacted.
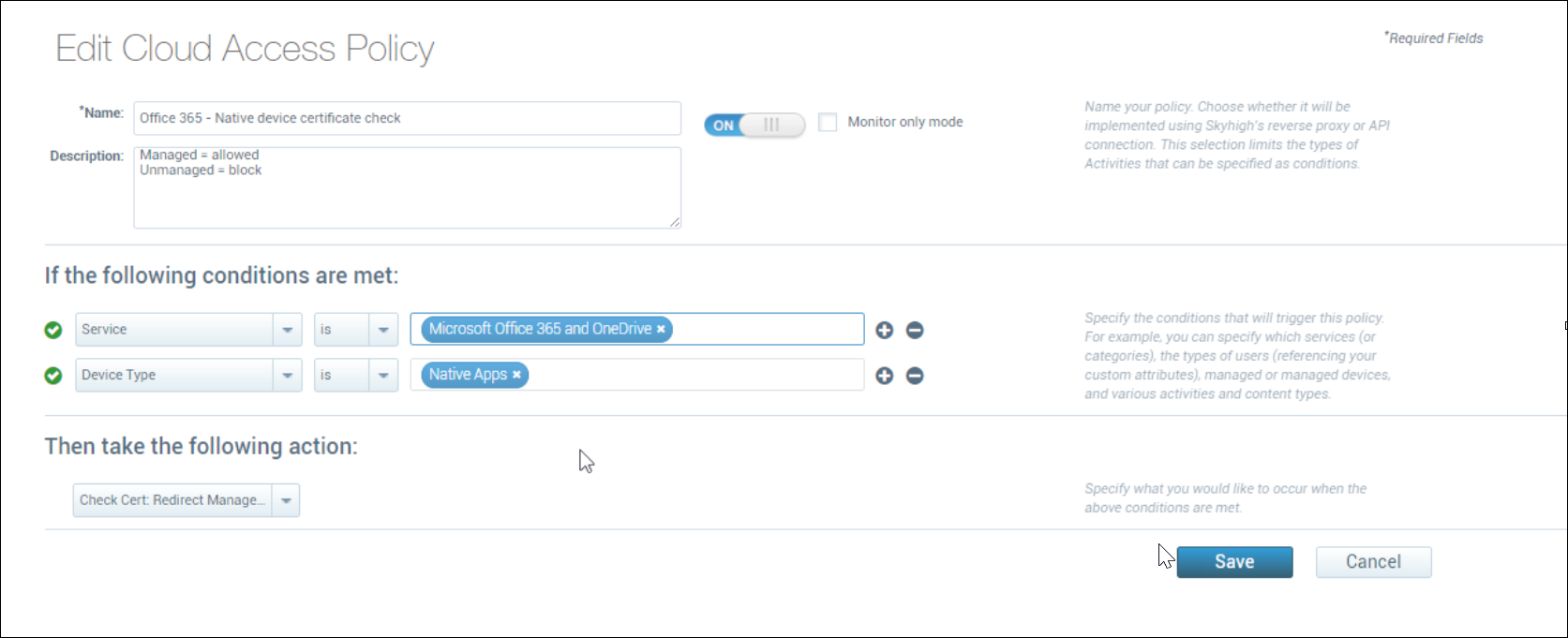
You need a cloud access policy configured to check for the certificate. For example, you could create a Cloud Access policy that does the following:
- If:
- 'Service' is 'Microsoft Office 365 and OneDrive'
- AND
- 'Device Type' is 'Native Apps'
- Then:
- Check cert: Redirect Managed, Block Unmanaged.
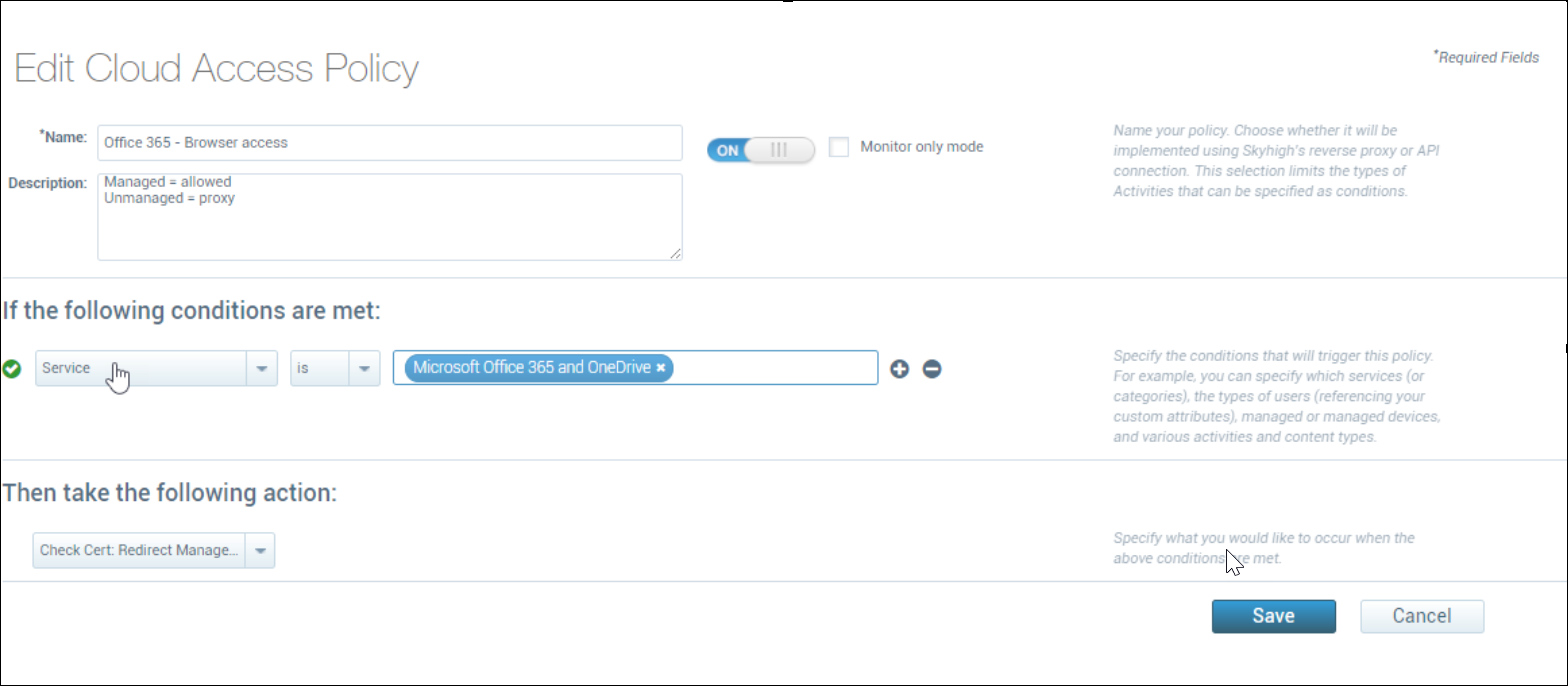
Another example:
- If:
- Service is Microsoft Office 365 and OneDrive
- Then:
- Check cert: Redirect Managed, Proxy Unmanaged
For more information, see Cloud Access Policies.
Step 6: Connect the Cloud Connector
Connect Skyhigh Cloud Connector to VMware Workspace ONE UEM using the API via the command-line tool (shnlpcli). The Cloud Connector is responsible for connecting to the VMware API periodically (default is once per day) and pull down the user to UUID information. This is then uploaded to Skyhigh CASB for use in CAPol.
The following parameters are set using shnlpcli:
| Name | Value (for lab) | Notes |
|---|---|---|
| mdmType | vmware | This is set to the MDM type |
| mdmDevicesRestUrl | https://techp.awmdm.com/api/v1/mdm/devices/search | This is the API endpoint. Adjust the URL to match the environment. |
| mdmTenantCode | vBxfGiQ68pC3KCoBrwelq+954BSBRiMw2kSkaXyaMMc= | This is the API key. Obtain in VMware Workspace ONE UEM under settings > system > advanced >api > rest api |
| mdmUsername | apiadmin | This is an VMware Workspace ONE UEM user with access to the API |
| mdmPassword | Skyhigh123! | This is the password associated with the API admin account |
| mdmHostname | techp.awmdm.com | The VMware Workspace ONE UEM instance hostname |
To connect Cloud Connector:
1. Stop the Cloud Connector service if it is running
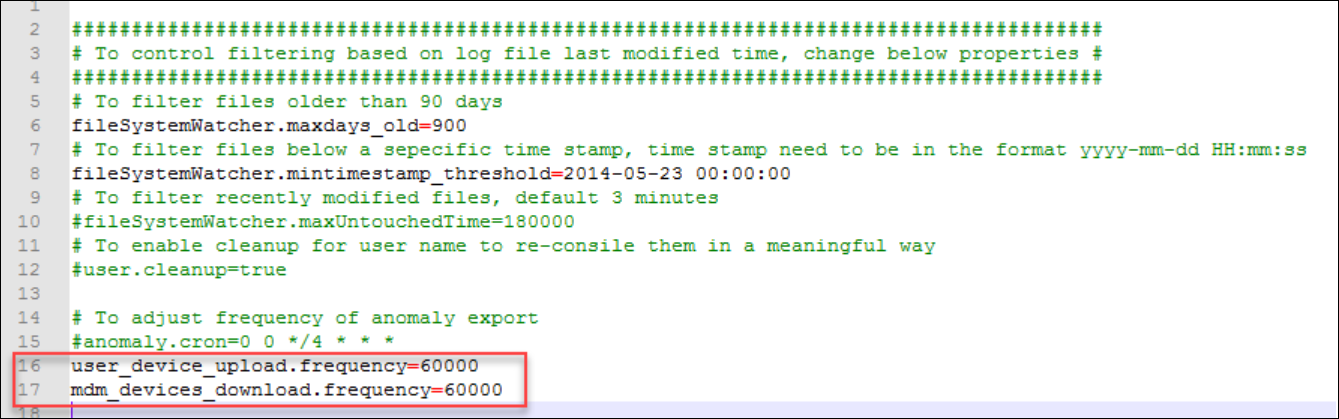
2. Edit the logprocessor.local.properties file and add the following lines:
-
user_device_upload.frequency=60000
-
mdm_devices_download.frequency=60000
3. Enter the following commands to connect the VMware Workspace ONE UEM API
| shnlpcli sp --name mdmType --val vmware shnlpcli sp --name mdmDevicesRestUrl --val https://techp.awmdm.com/api/v1/mdm/devices/search shnlpcli sp --name mdmTenantCode --val vBxfGiQ68pC3KCoBrwelq+954BSBRiMw2kSkaXyaMMc= shnlpcli sp --name mdmPassword --val Skyhigh123! shnlpcli sp --name mdmUsername --val apiadmin shnlpcli sp --name mdmHostname --val techp.awmdm.com |
4. Start the Cloud Connector service.
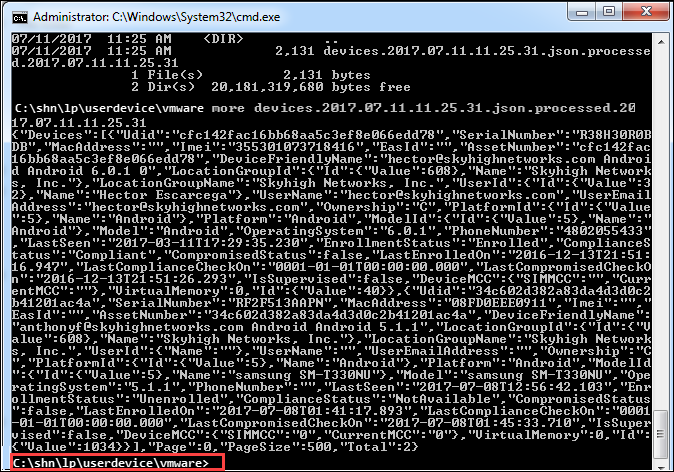
5. The MDM sync occurs one per day by default. Once it has synced, you should see a new folder on the root of the hard drive (c:\shn). Within the folder C:\shn\lp\userdevice\vmware you will see a JSON file, which contains the information pulled from VMware Workspace ONE UEM. This confirms the integration is working.