About Threats
Threat Protection
To ensure data is safe and secure, organizations should be able to identify and effectively manage threats. In this lesson, we will look at threats and anomalies, identify compromised accounts, and understand data exfiltration.
Threat Vectors
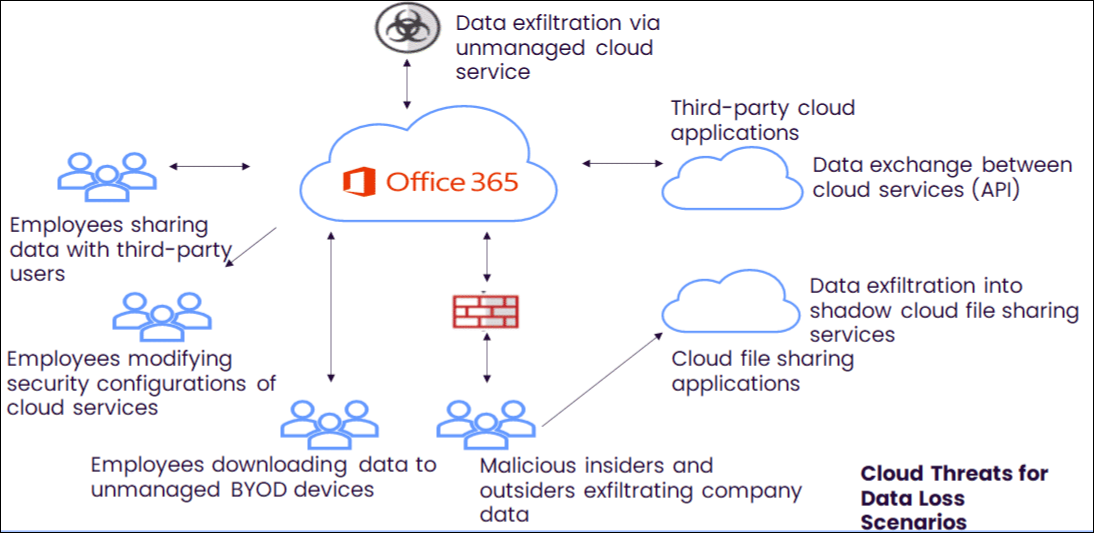
The cloud introduces a multitude of new threat vectors that can lead to data loss, including:
- Malicious or careless insiders who download data from a corporate sanctioned cloud service, then upload it to a Shadow IT cloud file-sharing service.
- An employee who downloads data onto a personal device, regardless of being on- or off-network, at which point control over that data is lost.
- A user endpoint device that syncs malware to a filesharing cloud service and exposes other users and the corporate network to malware.
- Data in a sanctioned cloud service that is lost to an insecure and unmanaged cloud service via an application programming interface (API) connection between the two services.
Securing the usage and data in the service is the customer’s responsibility, including how the service is used, who has access to data, and who is sharing what with whom. Therefore, it's important that a cloud threat protection solution is employed to get visibility, threat identification and resolution.
Threat Management
Managing threats and anomalies is an important aspect from a security perspective and needs to be managed on a daily basis. The Threats tab displays information about specific clusters of anomalies that strongly suggest your cloud services may have been compromised. Use this page to observe and respond to threats.
Anomalies should be marked as resolved or false positives after investigating. To reflect accurate data, you can create anomaly exceptions and in some cases change the anomaly threshold.
Threat Protection Features
Skyhigh CASB's Threat Protection enables real-time threat and anomaly detection and remediation for security, compliance, and data governance across all Sanctioned Cloud Services (including CNAPP services) such as Salesforce, Box, Microsoft Office 365, AWS, GCP, and more.
With a canonical Cloud API EngineTM powering it, Threat Protection delivers the following capabilities:
- Threat Protection User Interface. A unified Threat Protection dashboard at Incidents > Threats with an incident-response workflow for security risks arising from potential insider threats, compromised accounts, privileged user access, flight risk, and other risky data uses.
- Threat Modeling. Correlates multiple anomalous events within a cloud service or across cloud services to accurately separate true threats from simple anomalies.
- User Behavior Analytics. Uses data science to build a self-learning model of normal user behavior based on role, department, geo, and other heuristics across multiple CSPs to identify anomalies pointing to data exfiltration arising from potential Privileged Access, Compromised Accounts, or Insider Threats.
- Account Access Analytics. Analyzes login attempts to identify impossible cross-region access, brute force attacks, and untrusted locations indicative of compromised accounts.
- Privileged User Analytics. Monitors use and access to data from Privileged Users. Recommends options to minimize risk arising from misconfigured or excessive permissions granted to privileged users. Identifies "zombie" administrator accounts, data access patterns, inappropriate access to data, unwarranted escalation of permission, and user provisioning.
- Configurable Sensitivity. Provides an adjustable sensitivity scale for each anomaly type with real-time preview showing the impact of a change on anomalies detected by the system.
- Cloud Activity Monitoring. An immutable, comprehensive Activity Monitoring user interface that displays all user, admin, and third-party application activities for investigations and forensics. Provides a comprehensive audit trail of all user and administrator activities to support post-incident investigations and forensics.
- Data Exfiltration Analytics. Leverages machine learning to identify traffic patterns indicative of malware or botnets exfiltrating data from on-premises systems via cloud services.
- Darknet Intelligence. Identifies stolen credentials acquired in phishing attacks and leaked from breached cloud services to reveal users and services at risk.
- Outbound Data Intelligence. Integrates with malicious domain/IP databases, identifies uploads to untrusted destinations, and flags uploads associated with spyware, phishing, and botnets.
- Integration with SIEMs. Combines Skyhigh Security Cloud anomaly and event data with events from other systems and leverages your existing incident remediation process.
- Total Coverage Architecture. Leverages log collection, proxy chaining, packet capture, API, and reverse proxy deployment modes to support all cloud access scenarios.
- Geo-Location Analytics. Visualizes global access patterns in a Geo Location View and analyzes activity to identify cross-region accesses, failed, and successful attempts indicative of compromised accounts.
Threat Protection Terms
- Activity. An activity is an action taken by a user within a cloud service. When Skyhigh CASB is used to broker security for a cloud service, all activities can be accessed for investigation using Skyhigh CASB's Threat Protection.
- Anomaly. An anomaly is a set of activities that exceeds a threshold for “normal” behavior. Anomalies in your system can indicate inconsistent use across users, undefined policies around security, or unusual behavior. Not all anomalies represent threats or even represent malicious behavior.
- Date. The dates and times listed in Threat Protection are based on the time zone of the system accessing the Threat Protection interface, not the time zone where the activity occurred.
- Threats. Threats are collections of anomalies in normal behavior that point to potential security incidents happening within your organization for data on a cloud service. Because threats are only triggered when specific anomalies occur in concert, they are more likely to represent real breaches to your system to investigate.
- Anomaly Thresholds. The activity limits used to detect anomalies. Each type of activity has its own detection thresholds. Thresholds can either be set based on the individual behavior of each user (behavior-based thresholds) or keyed to pre-determined thresholds (organizational thresholds). Behavior-based thresholds can change based on the time of day or day of the week. Five hundred record downloads on Monday morning might be normal for a user but, the same number of record downloads on a Saturday night can trigger an anomaly. When the threshold is exceeded, an anomaly is generated.
Examples of thresholds include: - Download or Upload Counts. Users who download many files as part of their responsibilities are less likely to trigger an anomaly than a user who downloads 50,000 files the first time they log into the service.
- Administrative Actions. A user who creates several new accounts each month is less likely to generate an anomaly than a brand-new administrative account who creates 50 new users and deletes them all that day.
Threat Protection Pipeline
The Threat Protection back-end pipeline processes events in two separate streams: the real-time stream and the batch stream. User activities relevant to data exfiltration are processed in the real-time stream, and everything else is processed in the batch stream. For details, see Activities Processed in Real-Time.
Threat Protection Workflow
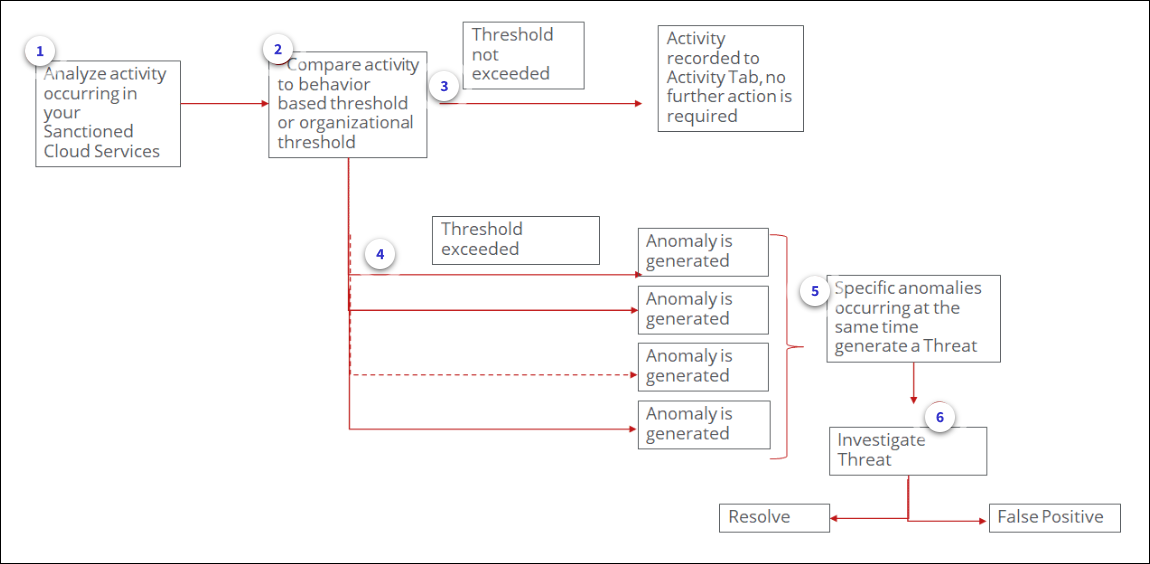
Identifying and resolving threats is one of the main purposes of the Skyhigh CASB Threat Protection platform. Threats alert you to potential security breaches by recognizing when multiple anomalies occur in concert to suggest a significant event. Understanding how threats are generated and how to respond to them is vital to success with Threat Protection.
Skyhigh CASB Threat Protection uses the following workflow steps:
- Threat Protection analyzes activity occurring within your Sanctioned Cloud Services.
- This activity is compared to the threshold for that activity. This threshold is either based on the user's specific behavior or leveled out to the normal behavior of your entire organization.
- If the activity does not exceed the threshold, the activity is recorded to the Activity Tab, and no further action is required.
- If the activity exceeds the threshold, an Anomaly is generated.
- When specific anomalies appear at the same time (for example, if there are significant Brute Force anomalies occurring at the same time as unusual Data Access) a threat is generated.
- Because Threats only occur when a specific pattern of Anomalies are generated, your team should investigate each threat, determining if the threat represents a valid security concern that should be addressed and resolved or if the threat was generated incorrectly and should be marked as a false positive. Either way, once a threat is marked, it will be removed from the Threats table.