IaaS Architecture
Skyhigh CASB for IaaS operates completely in a similar fashion to SaaS API mode with a near-real-time event feed and remediation occurring over an API connection to the IaaS provider. Additionally, Skyhigh CASB for IaaS works with code automation software such as Jenkins, also via API, to scan for and prevent vulnerable code from being deployed. Control connections are also established between the micro-segmentation shims installed on containers and Skyhigh CASB.
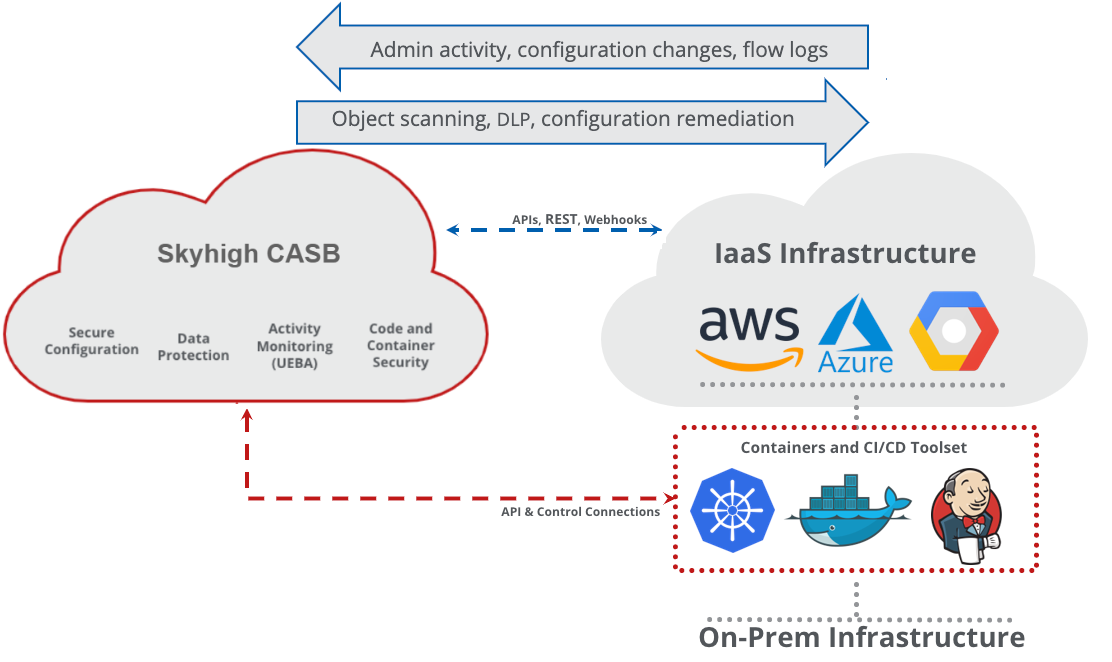
Figure 6 – CASB Architecture: IaaS
API Connection to IaaS Provider
As shown by the blue dashed line in Figure 6, Skyhigh CASB establishes an API connection with the IaaS provider. This connection supports the following functionality:
- Activity Monitoring – All admin activity and API calls are recorded by Skyhigh CASB by subscribing to feeds provided by the IaaS vendor such as AWS CloudTrail, AWS Config Events, or Azure Activity Monitor.
- Secure Configuration Management – Skyhigh CASB monitors both the live configuration and those stored in templates and compares them standards.
Changes to the environment are automatically detected through Activity Monitoring and re-scanned when necessary. When required, API calls are made back into the IaaS to remediate the problem. For example, if an instance were found not to have a required network policy applied, Skyhigh CASB would change its configuration to apply it either through a direct API call or by calling a customer-defined function such as Lambda.
-
Object Storage DLP - Object storage such as AWS S3, Google GCS, or Azure Blob Containers are scanned against DLP policies for sensitive data. Upon finding a violation, Skyhigh CASB can alert, quarantine, or delete the data.
The above functionality relies on API calls made directly to the IaaS provider and will require appropriate roles, permissions, and access keys to be provisioned for Skyhigh CASB. For example, a read-only account can be created for scanning configuration and storage, but if remediation is required then appropriate Skyhigh CASB will need a role with permissions enough to make the desired changes or function calls.
API Connections with CI/CD and Container Orchestration Tools
The red dashed line shown in Figure 6 shows connections made to various components that support CI/CD automation and container orchestration to provide the following services:
- Infrastructure-as-Code Security – As part of a project’s build process, Skyhigh CASB scans infrastructure-as-code, such as a CloudFormation template, for policy violations allowing IaaS security problems to be caught earlier in the development cycle before they pose a risk to the organization.
- Container Component Scanning – Container manifests are scanned for vulnerable or outdated third-party libraries at build time.
- Container Orchestration Posture Management – The configuration of the container orchestrator (such as Kubernetes or OpenShift) is checked for security problems and adherence to best practices both before and after deployment.

