Shadow IT Deployment Architectural Components
Skyhigh CASB
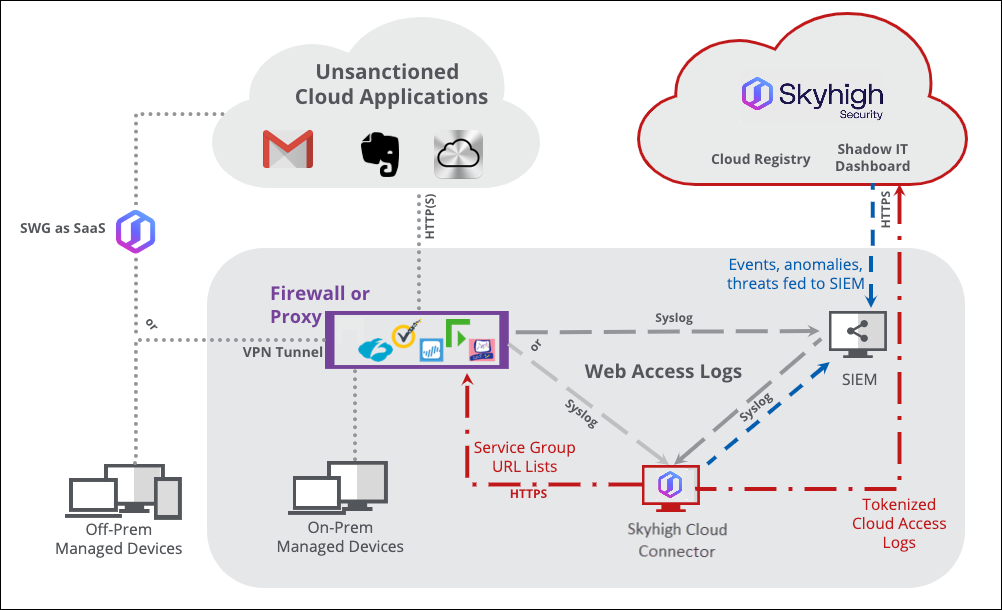
Figure 2 – Shadow IT CASB Architecture
Analytics
Scores and metrics associated with cloud services are stored in the Skyhigh CASB Cloud Registry. Logs received by customers’ firewall or proxy infrastructure are continuously combined with registry data to enable rich security analytics.
Centralized Configuration
Nearly all configuration of Skyhigh CASB for Shadow IT (risk weighting, service groups, log parsing, etc.) is completed within Skyhigh CASB interface. Where appropriate, configuration is pushed down to the Skyhigh Cloud Connector to facilitate centralized management
Reporting
Manual or automated reporting is performed within the Cloud Dashboard. In the case of tokenized reports that need to be detokenized, Skyhigh Cloud Connector is utilized for this function.
Skyhigh WSGS (as SaaS or on-premises)
Web Filtering and Logging
A traditional use case for Skyhigh Web Security Gateway Service, web filtering provides for enforcement of acceptable use policies for the World Wide Web. Generally, sites are either allowed or disallowed by category but can also include risk score and black/white-list.
The WGCS generated logs that detail what URLs were visited by whom, when, and how much data was transferred. See the following section on the Cloud Connector for details on how these logs are consumed for Shadow IT discovery and governance.
Selective Tunneling and DLP
Some solutions such as Skyhigh Security Service Edge provide an endpoint client that steers traffic for inspection based on policy. In this case, traffic headed toward selected services are directed to on-premises or SaaS-based services for SSL decryption and inspection. For example, a document transferred to a personal Office 365 instance would be inspected (and blocked, if necessary) in-transit.
While many SWGs are capable of this functionality, choosing a solution such as Skyhigh Security Service Edge allows for a unified DLP policy for both sanctioned and unsanctioned cloud services as well as on the endpoint hardware itself (e.g., removable storage policy).
On-Premises Components (Cloud Connector)
Log Parsing
Web access logs are fed into Skyhigh CASB through the on-premise Skyhigh Cloud Connector software. Most deployments will automate this log feed with Syslog either directly from the devices generating the logs or aggregated through a SIEM. It is also possible to process logs stored in a file share or transferred to the Skyhigh Cloud Connector through SCP, FTP, etc.
Skyhigh Cloud Connector sifts through the logs received for IP or URL matches found in the Cloud Registry and uploads (over HTTPS) relevant fields such as source IP or username, protocol, bytes uploaded, bytes downloaded, etc. to Skyhigh CASB for analysis and reporting.
Active Directory Integration
User attributes such as those describing department, group, or geography information that are stored in Active Directory or LDAP can be synchronized into Skyhigh CASB and used for building both Shadow and Sanctioned IT reports and policies.
Tokenization
Some organizations require that personally identifiable information that may include a username or source IP address protected before being transmitted to a third party such as Skyhigh Security. In these cases, the Skyhigh Cloud Connector performs on-premises tokenization such that a one-way salted hash database is maintained on the local server and only tokens are sent to the cloud for analysis. Tokenization is transparent for administrators authorized to detokenize since the dashboard is designed for client-side detokenization.
SIEM Integration
In addition to analyzing logs receive from a SIEM, the Skyhigh Cloud Connector also leverages the SIEM to centralize events, anomalies, and threats generated by Skyhigh CASB.
Skyhigh Cloud Connector uses syslog to push events into the SIEM, however customers can also pull this information directly using the Skyhigh CASB REST API.
Firewall and Proxy Integration
When Skyhigh CASB Service Groups created in the Dashboard can be leveraged by existing firewall or proxy infrastructure by publishing URL lists on the Skyhigh Cloud Connector. For example, a service group containing a list of cloud storage provider URLs that do not encrypt data at rest could be pulled by the on-premises proxy or firewall devices at https://hostname-of-connector:8080/c...kycloudstorage.
Once Service Groups have been linked in the proxy or firewall policy, they can be used to provide enforcement, coaching, or trigger SSL decryption and DLP.

