Cloud Connector Config SIEM Integration (SaaS)
You can export Anomalies, Threats, Incidents, and Audit Logs from Skyhigh CASB to your third-party SIEM systems (Security Information and Event Management) using SIEM Integration (SaaS).
IMPORTANT:
- You must have the Skyhigh Cloud Connector user role to install and configure Cloud Connector. For details, see About User Roles and Access Levels.
- To download the latest version of the Cloud Connector, see Download Skyhigh Cloud Connector. Before installing the Cloud Connector, make sure all prerequisites have been met. For details, see Skyhigh Cloud Connector Prerequisites.
- You must access Skyhigh CASB user interface from the same network on which your Cloud Connector is installed. Otherwise, an error message displays and you cannot enable the feature or configure settings. Error message: "SIEM settings cannot be accessed outside of your company's network. You need to be inside your company's network to turn on the feature."
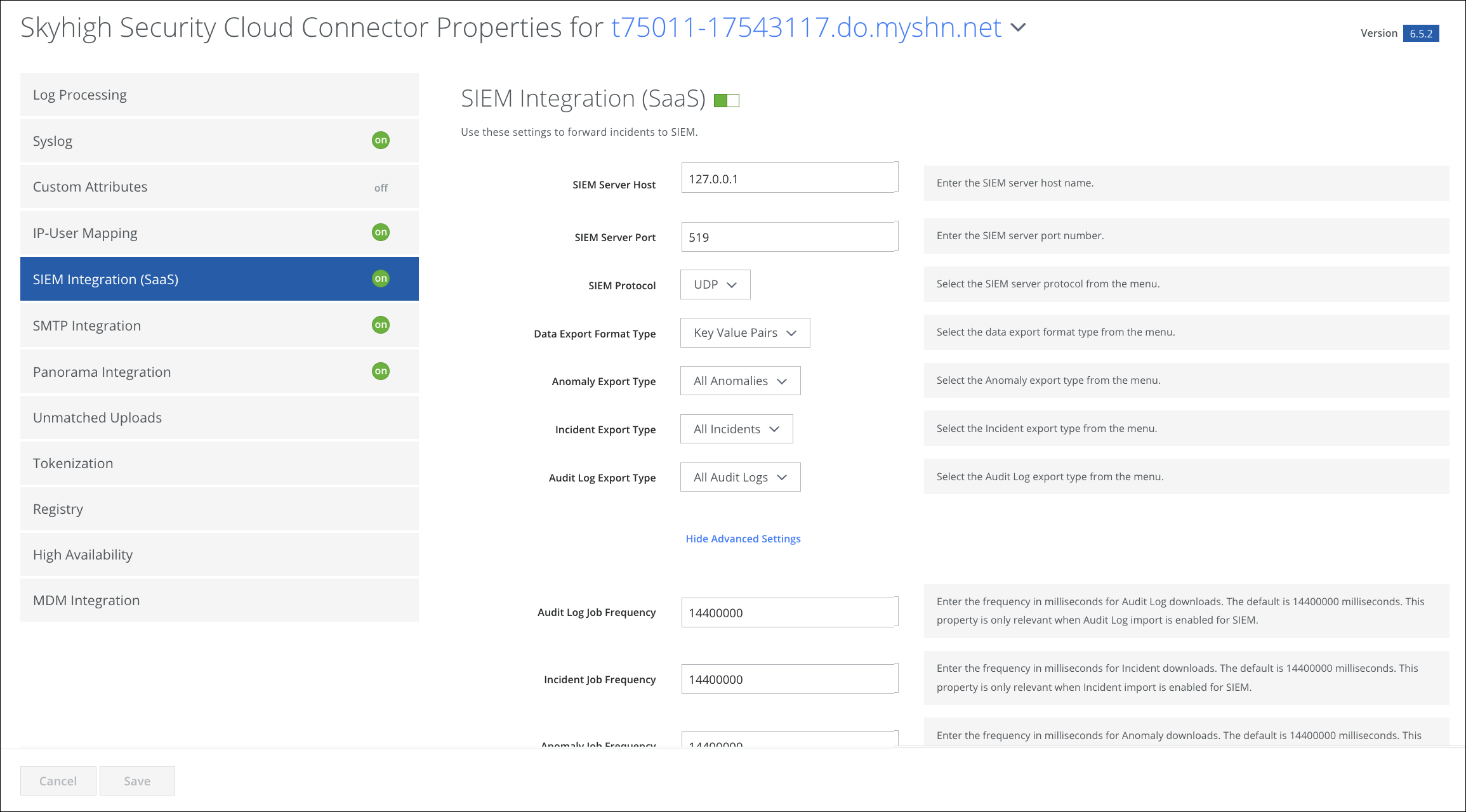.png?revision=1)
| Field | Description |
|---|---|
| SIEM Server Host | Enter the SIEM server hostname. |
| SIEM Server Port | Enter the SIEM server port number. |
| SIEM Protocol |
Select the SIEM server protocol from the menu:
|
| Data Export Format Type |
Select the data export format type from the menu:
|
| Anomaly Export Type |
Select the Anomaly export type from the menu:
|
| Incident Export Type |
Select the Incident export type from the menu:
|
| Audit Log Export Type |
Select the Audit Log export type from the menu.
|
Advanced Settings
Click Show Advanced Settings to display.
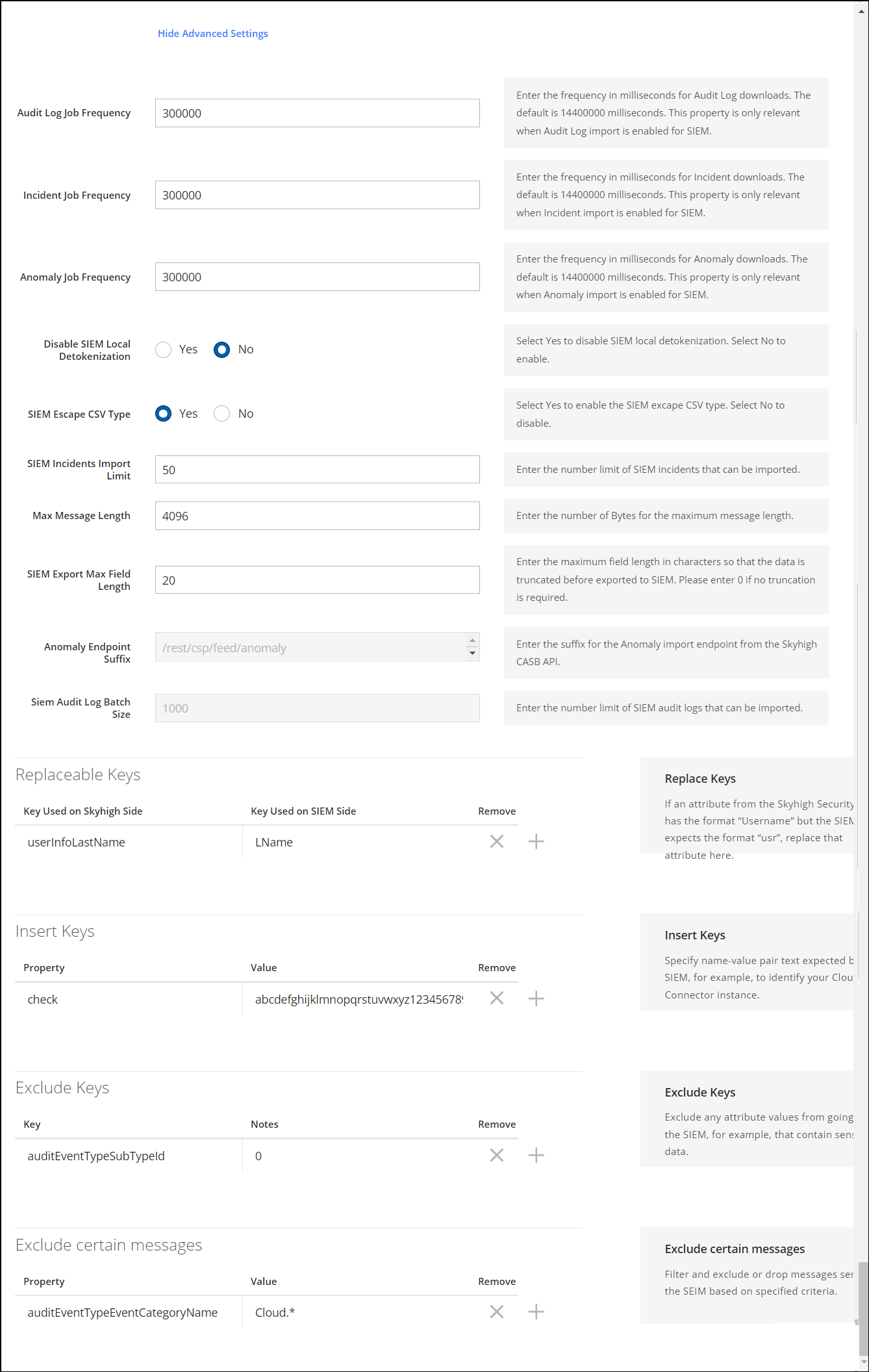
| Field | Description |
|---|---|
| Audit Log Job Frequency | Enter the frequency in milliseconds for Audit Log downloads. The default is 14400000 milliseconds. This property is only relevant when Audit Log import is enabled for SIEM |
| Incident Job Frequency | Enter the frequency in milliseconds for Incident downloads. The default is 14400000 milliseconds. This property is only relevant when Incident import is enabled for SIEM. |
| Anomaly Job Frequency | Enter the frequency in milliseconds for Anomaly downloads. The default is 14400000 milliseconds. This property is only relevant when Anomaly import is enabled for SIEM. |
| Disable SIEM Local Detokenization | Select Yes to disable SIEM local detokenization. Select No to enable. |
| SIEM Escape CSV Type | Select Yes to enable the SIEM escape CSV type. Select No to disable. |
| SIEM Incidents Import Limit | Enter the number limit of SIEM incidents that can be imported. |
| Max Message Length | Enter the number of Bytes for the maximum message length. |
| SIEM Export Max Field Length | Enter the maximum field length in characters so that the data is truncated before it is exported to SIEM. Please enter 0 if no truncation is required. |
| Anomaly Endpoint Suffix | Enter the suffix for the Anomaly import endpoint from the Skyhigh CASB API. |
| SIEM Audit Log Batch Size | Enter the number limit of SIEM audit logs that can be imported. |
| Replaceable Keys | If an attribute from the Skyhigh Security feed has the format “Username” but the SIEM expects the format “usr”, replace that attribute here. |
| Insert Keys | Specify name-value pair text expected by the SIEM. For example, to identify your Cloud Connector instance. |
| Exclude Keys | Enter any key and its value to be excluded from the data exporting to SIEM. |
| Exclude certain messages | Filter and exclude or drop messages sent to the SIEM based on specified criteria. For example, certain messages that contain sensitive data. |

