Configure Cloud Connector in High-Availability Mode
This topic describes the requirements and an overview for configuring Skyhigh Cloud Connector in High-Availability (HA) mode. In production, the Skyhigh Security Support or Professional Services can help you with configuration.
Skyhigh Cloud Connector High-Availability mode provides two main benefits:
- If one or more Cloud Connectors become unavailable, logs continue to be processed.
- Horizontal scaling of log processing to help distribute the load.
Hardware and Network Requirements
- Additional Virtual Machines for High-Availability Cloud Connectors, usually 2–3 Cloud Connectors in High-Availability mode. For complete Virtual Machine requirements, see Skyhigh Cloud Connector Prerequisites.
- Syslog, SCP, or FTP from the proxy, firewall, or SIEM to the shared drive or network location.
- HTTPS port 443 outbound from all Cloud Connector to Skyhigh CASB.
- Shared storage for logs.
- Dedicated folder for locked files.
NOTE: If you use a shared drive as a log location, configure the Log File Directory using the following pattern: //server/folder.
- OPTIONAL: An internal Network Load Balancer (NLB) can be used to distribute the syslog feed from the proxy/firewall/SIEM to the different ECs in the High-Availability cluster. Each EC handles the incoming syslog stream and writes the log to the shared drive or network location.
Standard Single Cloud Connector Architecture
This diagram shows the standard single Cloud Connector configuration for Shadow IT log processing.
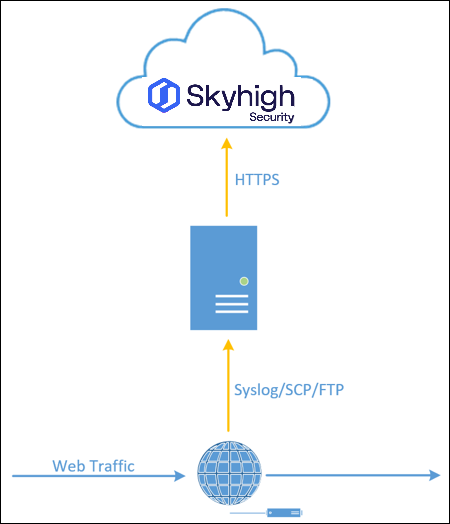
- Outbound web traffic passes through the customer’s proxy, firewall, or SIEM.
- The logs from the proxy, firewall, or SIEM are sent to Cloud Connector via syslog, SCP, or FTP.
- Cloud Connector parses the logs, tokenizes any internal sensitive data (IPs/usernames), and compresses the data.
- The data is sent to Skyhigh CASB over authenticated HTTPS for processing.
High-Availability Cloud Connector Architecture
This diagram shows the High-Availability Cloud Connector configuration for Shadow IT log processing.
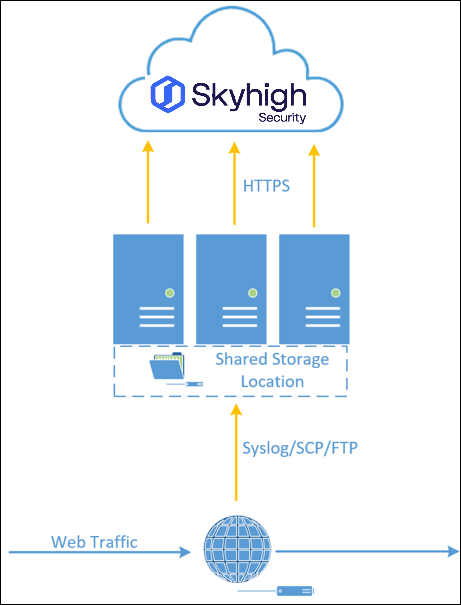
- Outbound web traffic passes through the customer’s proxy, firewall, or SIEM.
- The logs from the proxy, firewall, or SIEM are sent to a shared drive or network location via syslog, SCP, or FTP.
- This shared drive or network location is accessible by all Cloud Connectors (read and write).
- Based on first availability, one of the High-Availability Cloud Connectors parses the logs, tokenizes any internal sensitive data (IPs/usernames), and compresses the data. Once a log is accessed by one CC, others consider the file locked and instead pick up another file for processing.
- If a CC goes down, other CCs continue to access the shared location and continue to process the logs.
- The data is sent to Skyhigh CASB over authenticated HTTPS for processing.

