Configure a Domain Using a Directory Server
NOTE: This setup is applicable for the older Skyhigh Cloud Connector versions prior to 4.2. Newer versions of the Cloud Connector must have the AD integration performed from the Cloud Connector Console. For details, see Cloud Connector Config Custom Attributes.
Before you map information from your Directory Server to your log data, you must allow the Skyhigh Cloud Connector to connect to your Directory Server. After configuring Custom Attributes, you can map User Attributes to Custom Attributes. This allows administrators to map users and incidents in Skyhigh Security Cloud more easily.
To configure a Domain using a Directory Server:
- Open a web browser and enter the IP Address you set during installation into the address bar.
- Sign in using an email address and password with Cloud Connector privileges.
- Go to Enterprise Integration > Active Directory Integration.
- Click Add a Domain.
- For User Data Source, select Directory Server.
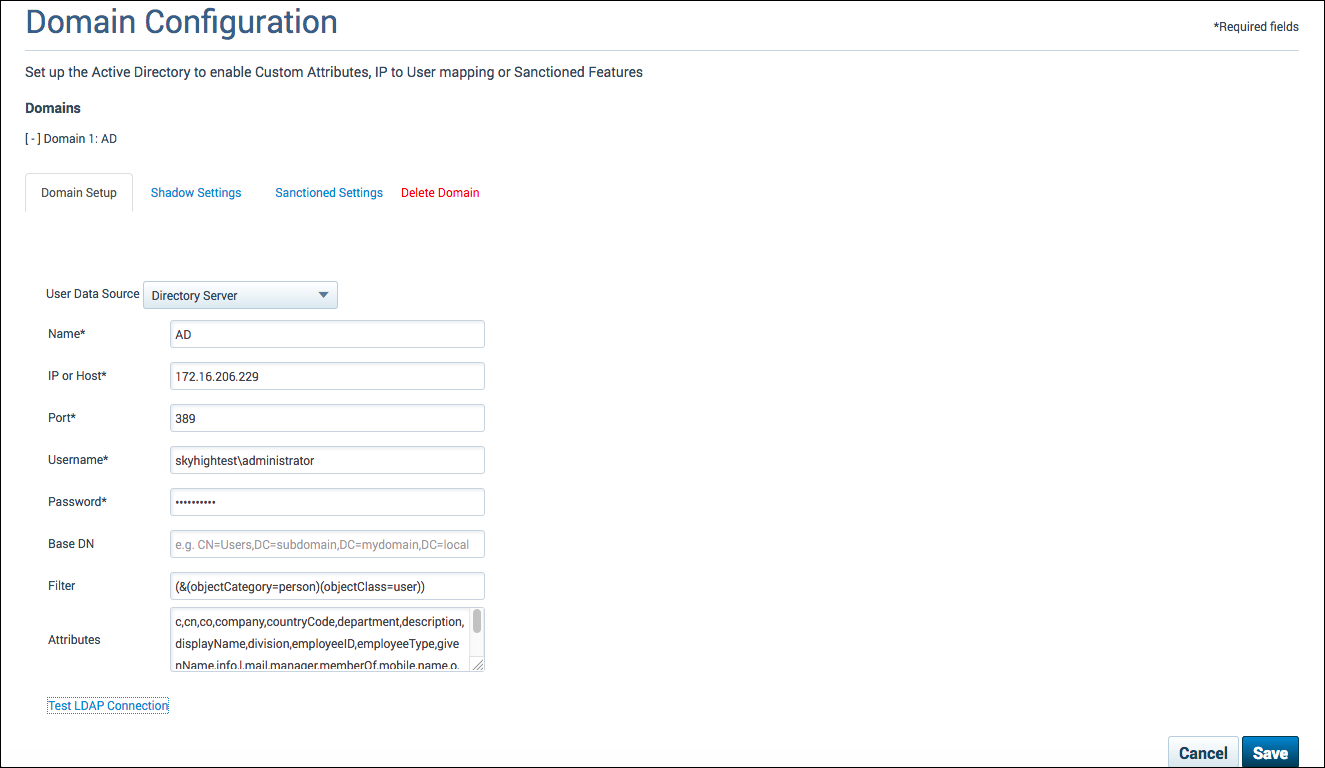
- To connect to your Directory Server, enter the following information:
- Name: The unique name for your integration. This is a user-defined name that will help you identify this integration and it must be unique.
- IP or Host: The IP Address or Host Name for your Directory Server.
- Port: The port where the active directory is listening.
- Username: The user name you would like Cloud Connector to use for authentication with your Directory Server.
- Password: The authentication password for your specified user name.
- Base DN: (Optional) A field that you can use to search your Directory Server for specific data.
- Filter: (Optional) A field used to limit search results. This is a predefined filter that will be applied to AD Data.
- Attributes: A field used to identify the attributes you would like to retrieve from the directory server. This is a predefined filter that will be applied to AD data. Review the default Attributes list to make sure all required Attributes are included. If an Attribute you need it missing, add it to the list. For more information, see LDAP Configuration.
- Click Test LDAP Connection.
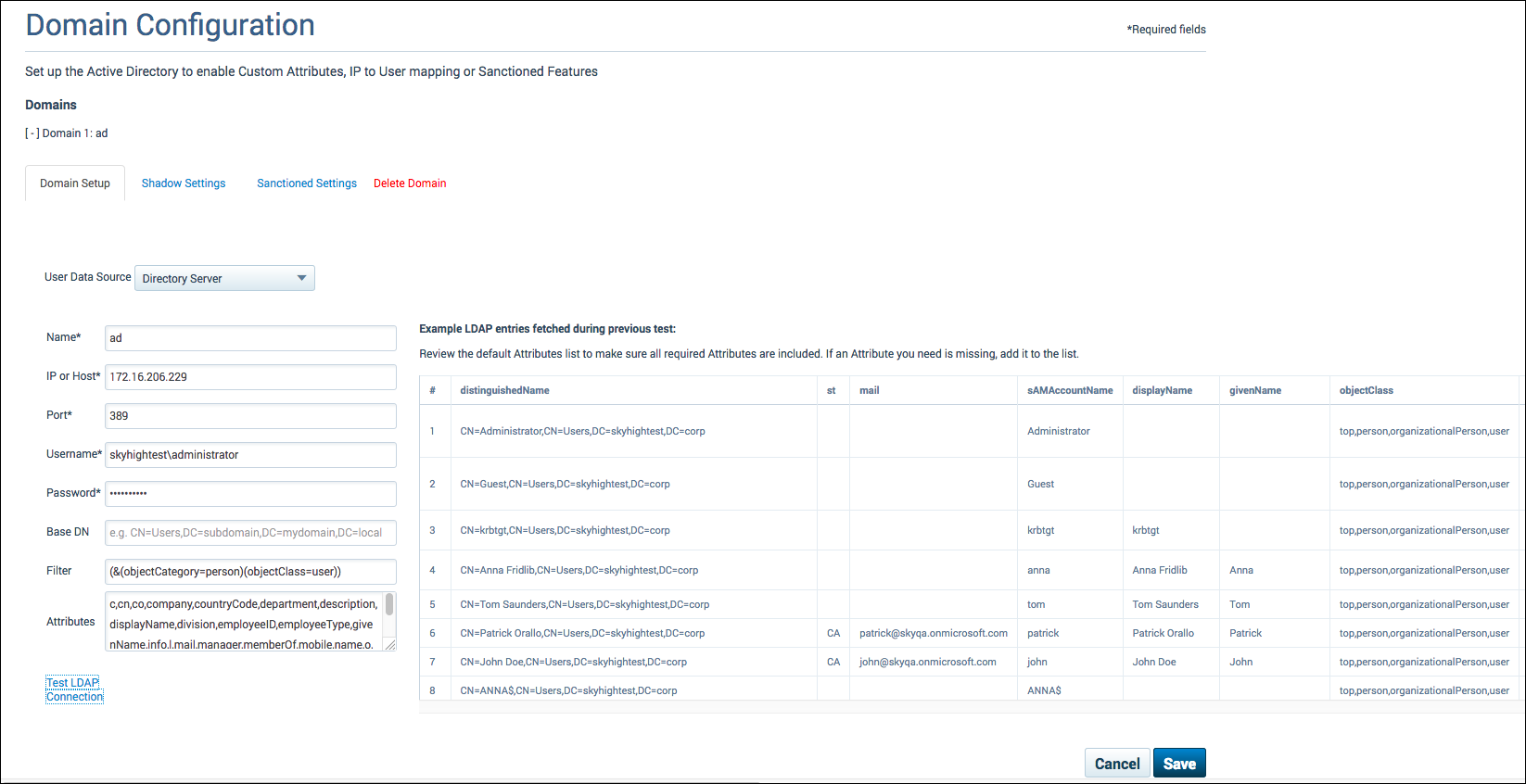
- Click Save.
IMPORTANT: The Save button will produce an error until at least one Shadow or Sanctioned setup is configured. Click x to dismiss it.
LDAP Configuration
Cloud Connector 3.5 and later defaults to a list of commonly used attributes to prevent the issue from appearing as binary.
Do not configure the LDAP integration to query binary objects. Doing so may cause issues. Also, update the LDAP configuration so that it does not import other LDAP objects, such as computers and groups. This change will also decrease the leveldb store size, as Skyhigh CASB only imports attributes that are needed, instead of all binary attributes.
Configure the Attributes field as follows:
- The Attributes field should contain only fields that are used, for example:
dn,sAMAccountName,memberOf,name - Add an LDAP filter to query ony for objects that actually have the attribute set that is used, for example:
(&(sAMAccountName=*)(memberOf=*)(name=*))
With these two settings, the LDAP connection is correctly configured and will not fail.
The new activeDirectory.json file in the .config directory looks like the following example:
{ "activeDirectorySetups": [{ "name": "Domain", "activeDirectoryDataSource": { "host": "cs.msds.kp.org", "port": 389, "userName": "SvcSkyhigh", "password": "%C3%90%C2%BFy%C3%9A%C3%8CI%C2%9B%1E", "activeDirectoryQuery": { "base": "DC=cs,DC=msds,DC=kp,DC=org", "filter": (&(sAMAccountName=*)(memberOf=*)(name=*)), "attributes": dn,sAMAccountName,memberOf,name }, "activeDirectorySslSettings": null }, "csvDataSource": null, "shadowActiveDirectorySettings": { "enableIpToUserMapping": false, "customAttributes": { "uniqueUserAdAttribute": "sAMAccountName", "customAttributeMappings": [{ "displayName": "Firewall Host Name", "customAttributeId": "custom3", "mappedTo": null }, { "displayName": "Display Name", "customAttributeId": "custom4", "mappedTo": "name" }, { "displayName": "Firewall Serial", "customAttributeId": "custom1", "mappedTo": null }, { "displayName": "usageType", "customAttributeId": "custom2", "mappedTo": null }, { "displayName": "Member of", "customAttributeId": "custom5", "mappedTo": "memberOf" } ] } }, "sanctionedActiveDirectorySettings": null } ] }
Virtual Attributes
The goal of Virtual Attributes is to provide additional formatted attributes that can be used in policies instead of using the AD attribute directly. Virtual Attributes are formatted to prevent the Skyhigh CASB dashboard from presenting too many values.
The following Virtual Attributes are available.
distinguishedName Attribute
Based on the value of the distinguishedName attribute of a user account, Skyhigh CASB creates additional virtual attributes to allow access to the organizational unit (OU), or other information about the location of the user object in the directory tree.
The following examples are based on the object's distinguishedName CN=User,CN=US,DC=shntest,DC=corp
| Name | Description | Example |
|---|---|---|
| virtual_DN | The distinguishedName of the current object in regular format. | CN=User,CN=US,DC=shntest,DC=corp |
| virtual_dnHierarchy | The distinguishedName of the parent object in regular format. | CN=US,DC=shntest,DC=corp |
| virtual_dnHierarchy_ws | The distinguishedName of the parent object with a comma replaced by a space. | CN=US DC=shntest DC=corp |
| virtual_dnHierarchy_short | The Common Name (cn) of the parent object. | US |
memberOf Attribute
If you add the Active Directory attribute memberOf, Skyhigh CASB creates additional virtual attributes to reformat the values to be more readable, and to allow better filtering on user group memberships.
| Name | Description | Example |
|---|---|---|
| memberOf | The distinguishedName attribute of each user group, in regular format. | CN=Group1,DC=shntest,DC=corp CN=Group2,DC=shntest,DC=corp |
| virtual_memberOf_ws | The distinguishedName attribute of each user group, with commas replaced by spaces. | CN=Group1 DC=shntest DC=corp CN=Group2 DC=shntest DC=corp |
| virtual_memberOf_short | The list of Common Names (cn) of each user group. | Group1 Group2 |
manager Attribute
If you add the Active Directory attribute manager, Skyhigh CASB creates additional virtual attributes to reformat the values to be more readable.
| Name | Description | Example |
|---|---|---|
| manager | The distinguishedName of the value of the manager attribute. | CN=Joe Bloggs,CN=EMEA,DC=shntest,DC=corp |
| virtual_manager_ws | The distinguishedName of the value of the manager attribute, with commas replaced by spaces. | CN=Joe Bloggs CN=EMEA DC=shntest DC=corp |
| virtual_manager_short | The Common Names (cn) of the value of the manager attribute. | Joe Bloggs |
userAccountControl Attribute
If you add the Active Directory attribute userAccountControl, then LP will create two virtual attributes based on the flag and status of the user account, in addition to the userAccountControl attribute.
For details, see https://msdn.microsoft.com/en-us/library/ms680832(v=vs.85).aspx.
| Name | Value | Flag | Description |
|---|---|---|---|
| virtual_UAC_AccountDisabled | True / False | ADS_UF_ACCOUNTDISABLE | Set to True if the user account is disabled. |
| virtual_UAC_NormalAccount | True / False | ADS_UF_NORMAL_ACCOUNT | Set to True if this is a default account type that represents a typical user. |

