Tokenize Custom Attributes for Shadow IT
Your Custom Attribute data can be tokenized before sending it to Skyhigh CASB. Your data will not be saved in the clear, and tokenization mapping will not leave your premises.
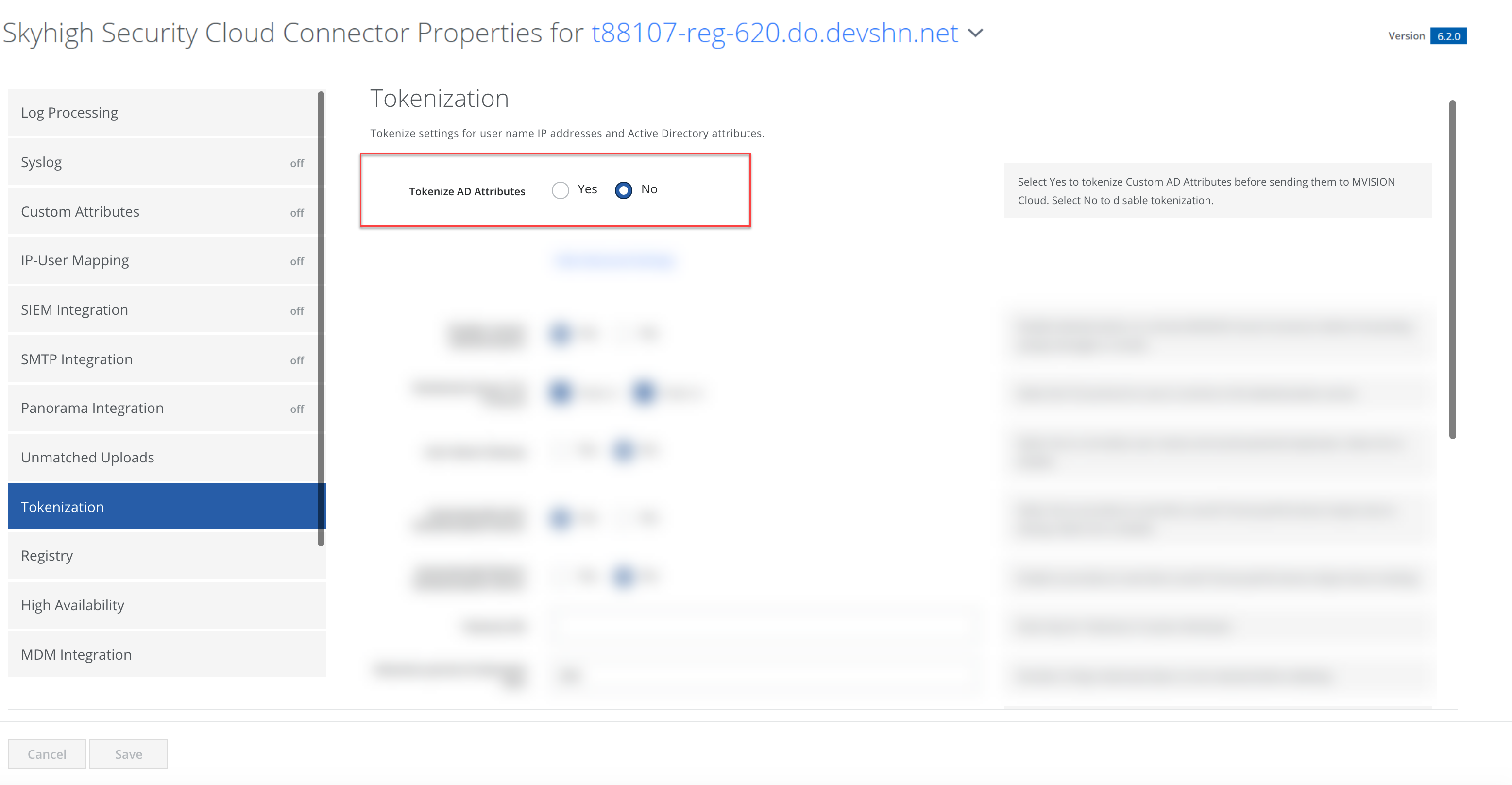
After migrating to cloud configuration, you can enable the tokenization for custom attributes in the Skyhigh CASB user interface, at Settings > Infrastructure > Cloud Connector > Tokenization tab.
For Tokenize AD Attributes, select Yes to tokenize Custom AD Attributes before sending them to Skyhigh CASB . Select No to disable tokenization.
NOTES:
- These tokenized custom attributes will show up "as is", in other words, tokenized on the Skyhigh CASB dashboard if the user doesn't have detokenization permissions.
- Each tokenized AD attribute is saved as a separate line item in MapDB.txt. So, if three AD attributes are tokenized, three individual lines will be present in MapDB.txt for that user.
To support and persist tokenization of these AD attributes, extra disk space will be required, depending on your tokenization method. Please contact Skyhigh Security Support for more information on the estimated file size.
fileSystemWatcher.tokenizationDnComponent Property
For Cloud Connector 3.5 and later, the previous normalization algorithm used in HMACSHA256 does not handle LDAP distinguished names properly.
If there is an equals sign (=) in the value, the normalizer will only take the string after the last one. Many distinguished names that typically end in dc=com will be normalized to a single value: com.
In order to preserve existing normalizations, a new configurable property has been added: fileSystemWatcher.tokenizationDnComponent. It defaults to empty.
If this property is set as fileSystemWatcher.tokenizationDnComponent=CN, it will modify the algorithm's attempts to extract the first configured distinguished name component, and if not present, it will then fallback to the original method.

