Create a Shadow/Web DLP Policy
| Save Evidence: Save Evidence is an advanced DLP feature that requires entitlement to a separate add-on SKU. Contact Skyhigh Support or your account manager for assistance. |
Create a Data Loss Prevention (DLP) policy for Shadow services or Web/URL categories to make sure that sensitive data is not exfiltrated by regular user access.
For example, you can create a policy that detects and blocks all personally identifiable information (PII) from being shared by users of Citrix ShareFile.
Prerequisites
To create a Shadow/Web DLP Policy using the Skyhigh CASB DLP Policy Wizard, your user account must have the following roles:
- DLP Policy Manager
- Web Policy Manager
Policy Wizard Rules
To scope your policy, the DLP Policy Wizard uses the following rules:
- AND/OR to refine the rule.
- Change IS to IS NOT to create exceptions.
- There is no THEN for scoping.
- Click Next when complete.
Create a DLP Policy
- Sign in to Skyhigh CASB and go to Policy > DLP Policies > DLP Policies.
- Under Actions, go to Shadow/Web Policy and click Create New Policy. (You can also create a Shadow/Web DLP Policy at Policy > Web Policy > Policy, on the Data Protection (DLP) > Web DLP tab.)
- On the Name & Scope wizard, configure the following information:
- Name. Enter a unique name for your policy.
- Description. Add an optional description for the policy.
- Scope. The policy is applied to all traffic by default. You can edit this to reduce the scope to specific traffic using any combination of the following criteria. (For this example, click Service, and in the Search for Service pane, search for and select Citrix ShareFile.)
- Client IP. The IP address of the endpoint.
- Connection IP. The IP address of the firewall or other device between your organization's network and the cloud. (Your public IP address.)
- Location. Any location name configured in the UI for Web Policy.
- Service. The cloud service to which it applies.
- Service Group. The group that contains the cloud service to which it applies.
- User Name. Name of the user making the web request.
- User Group. Names of one or more groups where the user making the Web request is a member.
- URL/Domain/Host. The URL/Domain/Host name of the user making the web request.
- Web Category. Category of the URL requested by the user.
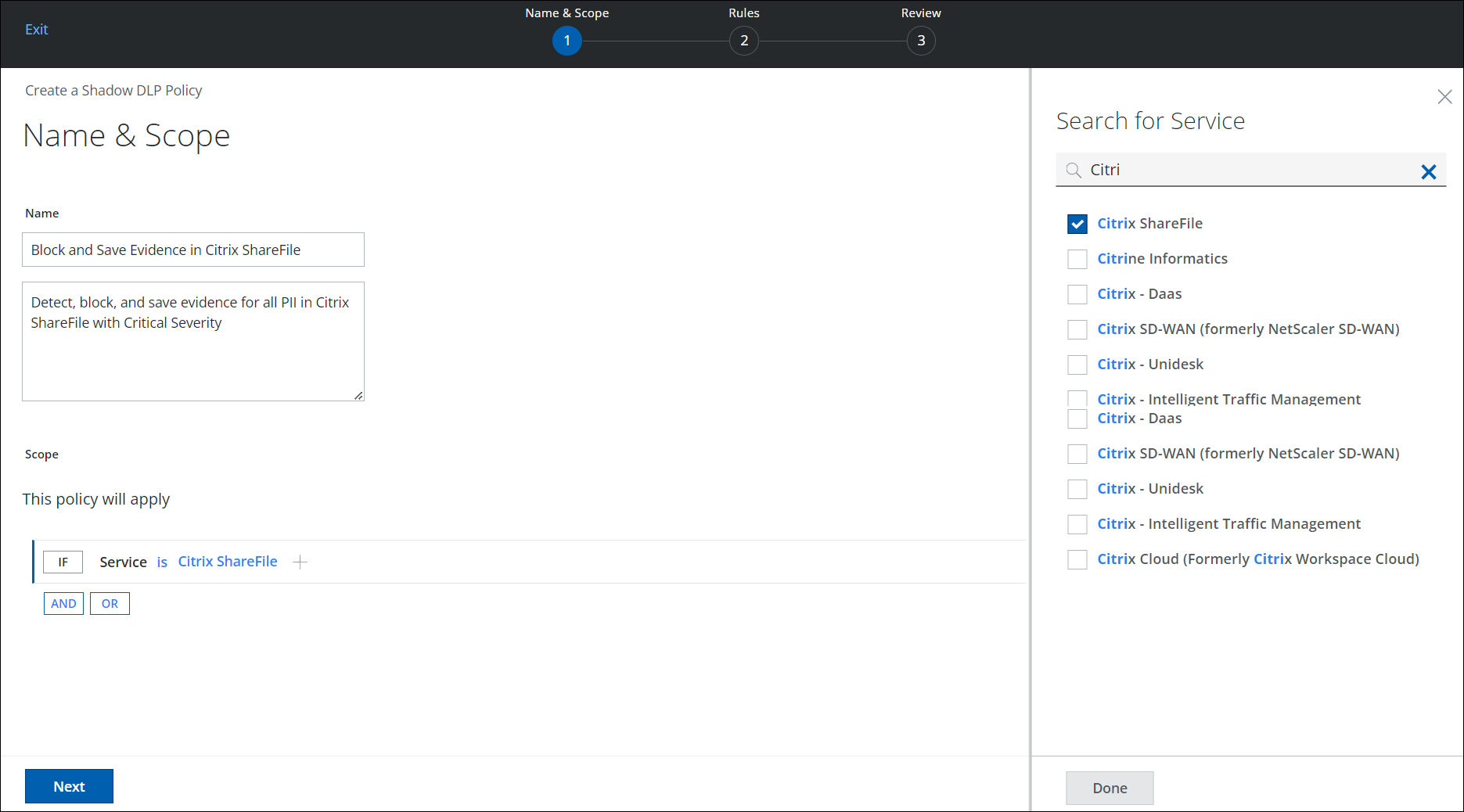
- Click AND or OR to add another criteria parameter. Otherwise, click Next.
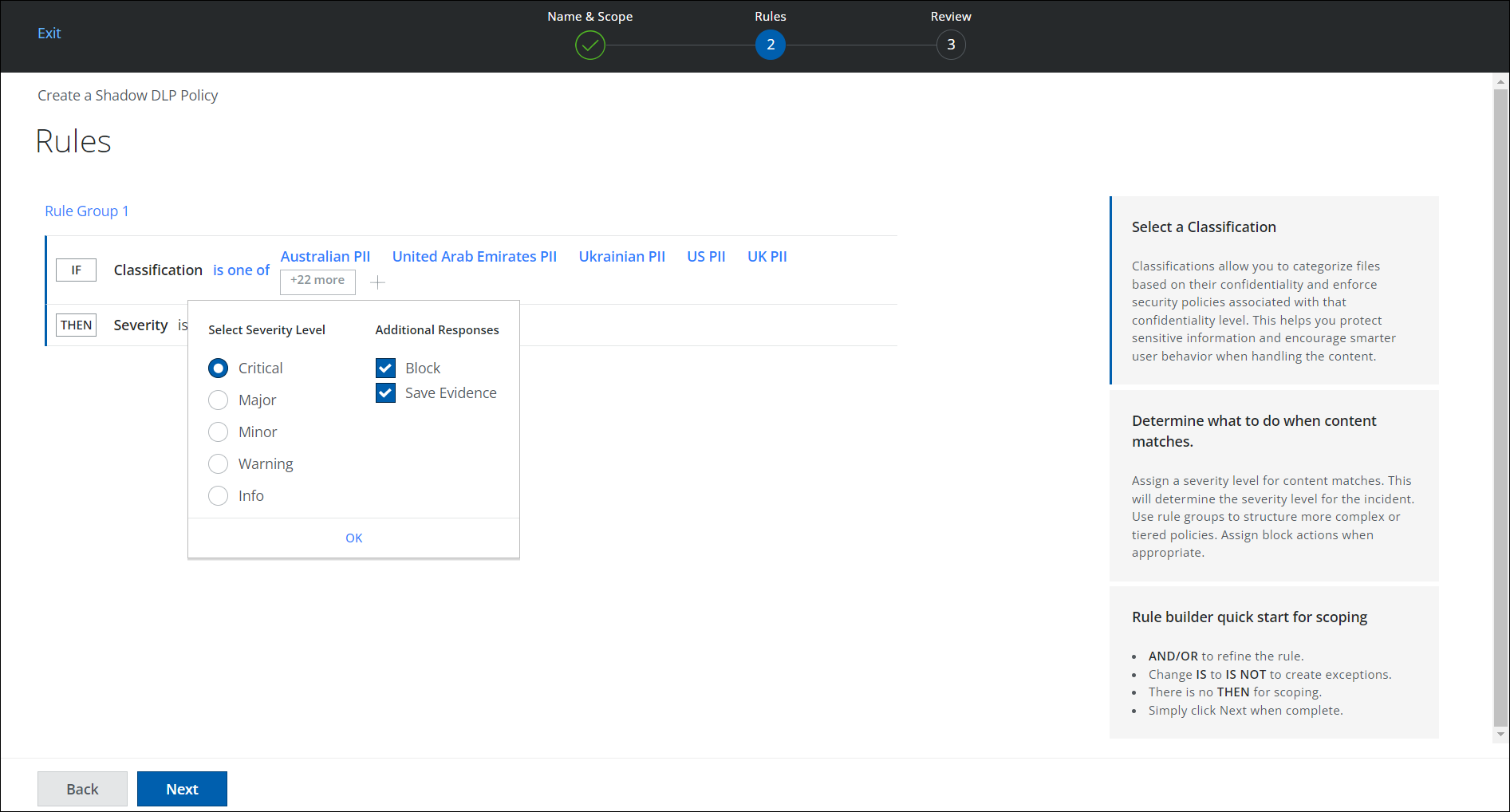
- On the Rules wizard, set a condition for a rule that triggers a response if this condition matches. If this data is involved, the response is triggered.
- Classification. Classification allows you to categorize files based on their confidentiality and enforce security policies associated with confidentiality levels. Click Select, then in the Select Classification pane, search for and select the Classification you want to use. (For this example, click PII > select all PII.)
- Skyhigh. Default Classifications provided by Skyhigh Security.
- Custom. Create Custom Classifications.
- All Classifications. Displays all available Classifications.
- Severity. Assign severity level for content matches. This determines the severity level of the incident. Click Then, then select the severity of the incident. (For this example, select Critical.)
- Critical
- Major
- Minor
- Warning
- Info
- Additional Responses. Select an optional response, if required. (For this example, select Block and Save Evidence). For more details on save evidence, see Save DLP Evidence.
- Classification. Classification allows you to categorize files based on their confidentiality and enforce security policies associated with confidentiality levels. Click Select, then in the Select Classification pane, search for and select the Classification you want to use. (For this example, click PII > select all PII.)
- Click Next.
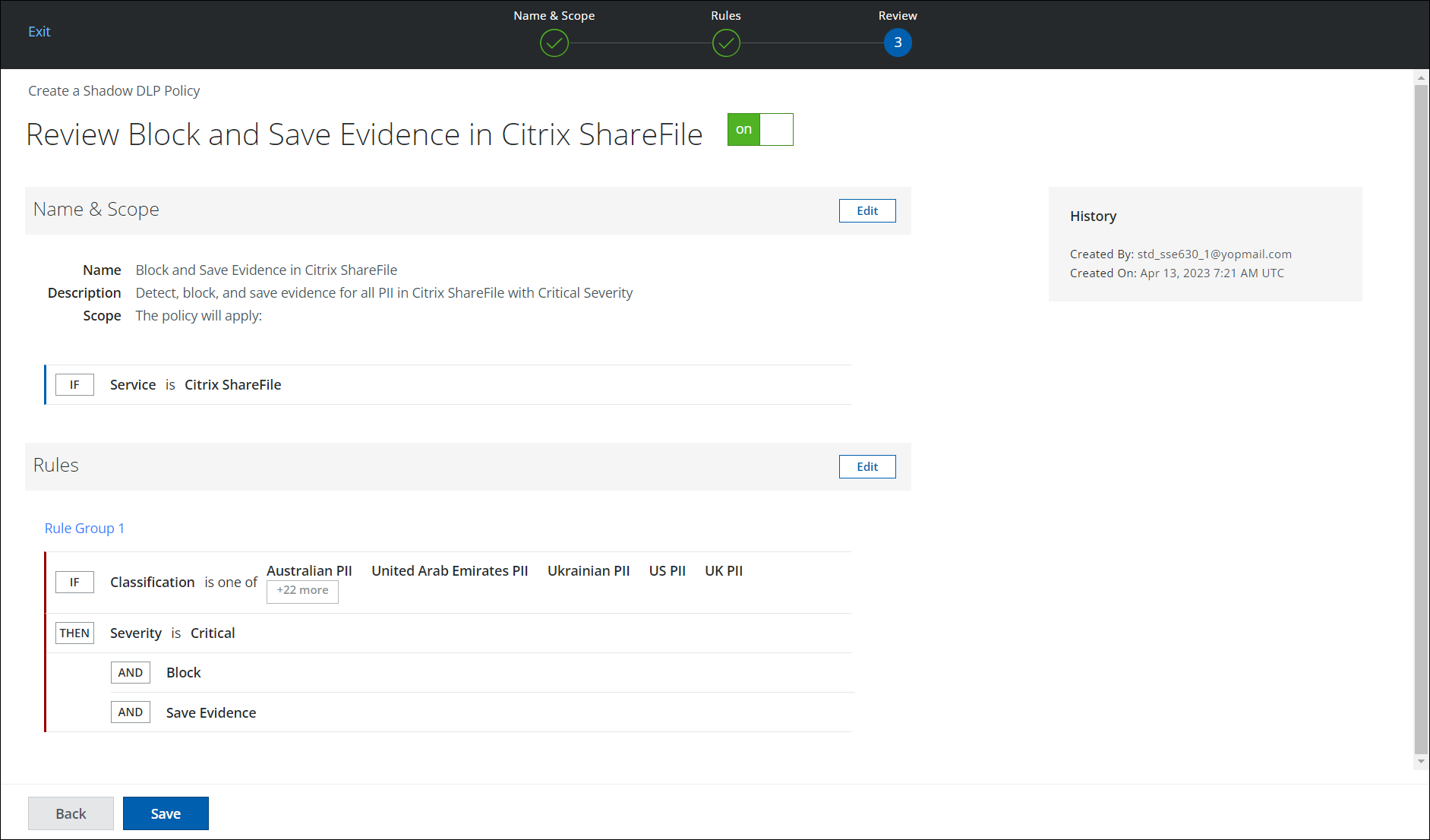
- On the Review page, review the policy you have created. To make any edits, click Edit.
- Click Save.
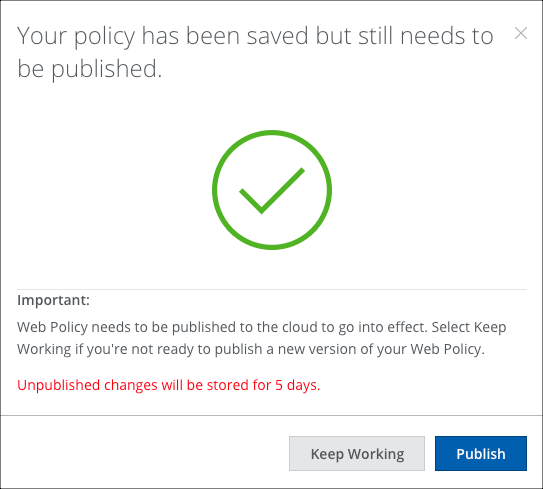
- Your policy is saved but still needs to be published to be enabled.
- Keep Working. Click to continue editing. You are alerted by the shield icon in the Skyhigh CASB navigation bar when a Web Policy change is waiting to be published.
- Publish. Click to publish your policy.
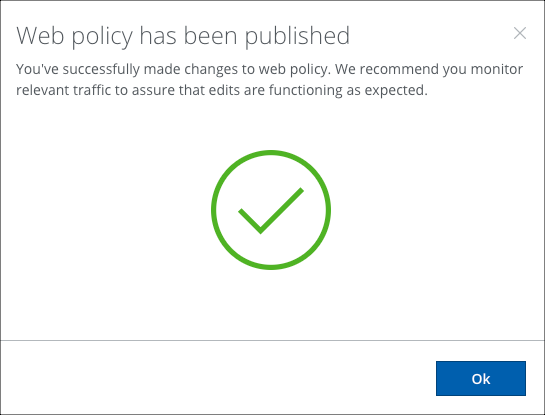
- Your policy is published and enabled. Click OK.
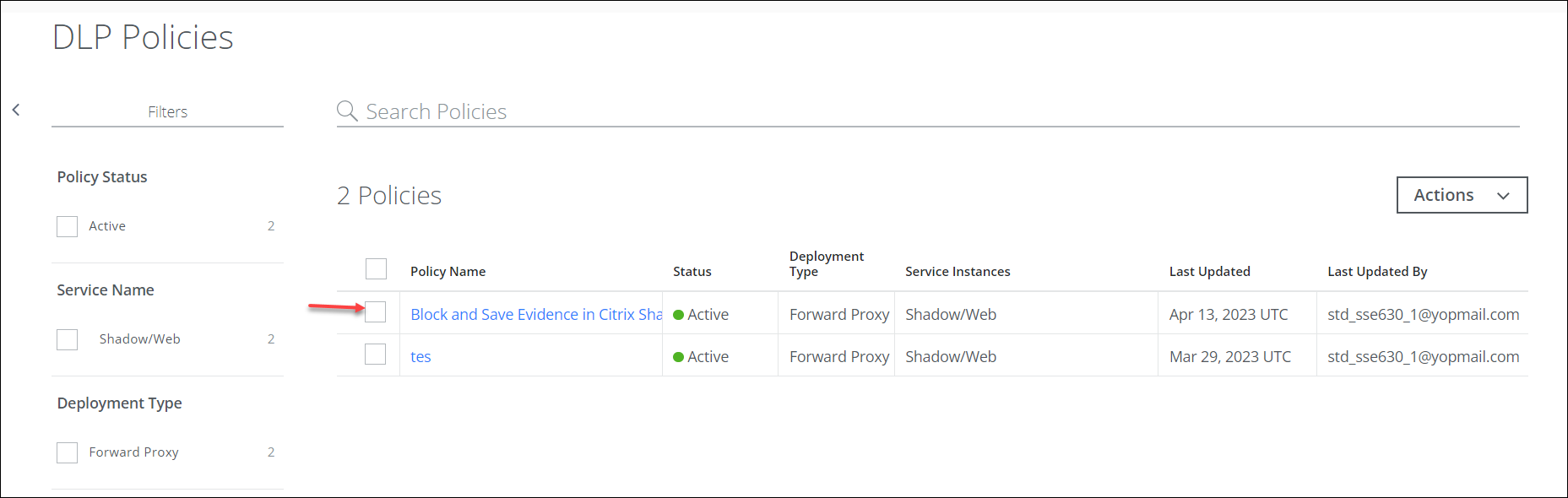
- Your new Shadow/Web Policy is displayed on the following pages
- Policy > DLP Policies > DLP Policies
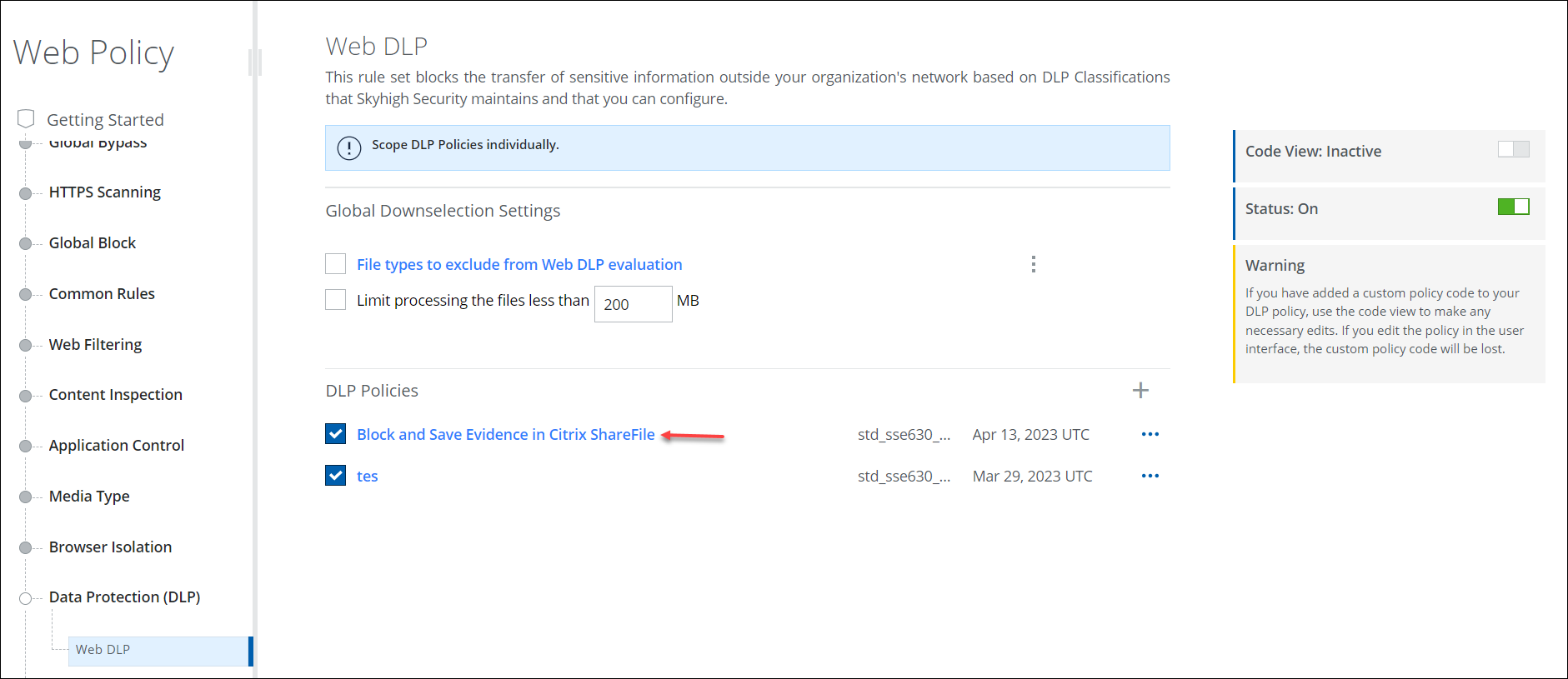
- Policy > Web Policy > Policy
- Policy > DLP Policies > DLP Policies
If any DLP policies are violated, you can view the incidents and apply the necessary remediation actions on the Incidents > Policy Incidents page. For details, see Shadow/Web DLP Incidents.
Sample Policies
You can use Shadow/Web DLP policies for the following use cases:
- Apply DLP Policies to Shadow Services. You can create a DLP Policy, for example, to detect and block all Personally Identifiable Information (PII) within a specific Shadow cloud service's UI. You can select any cloud service listed in the Cloud Registry.
- Apply DLP Policies to a Service Group. You can add services your organization considers risky to a Service Group, then apply your DLP policies to that Service Group. For example, you could add the keyword "Confidential" to a policy and block it for all services listed in the Service Group, "No Approval to Operate". Then when you add services to this group, perhaps weekly, the policy will apply to those new services from now on. You can also exempt selected services or Service Groups.
- Apply DLP Policies to Multiple Services. You can write different policies for different services, and those policies can coexist on a single tenant without interference. For example:
- Block all PII data going to Evernote.
- Detect documents with the keyword "Confidential" going to Sharefile and create an incident, but don't block access or send an alert.
- Detect documents marked as "Sensitive" going to all services in the Service Group "Medium Risk" and send an email alert to users.
- Manage DLP Policy Incidents. You can view all Shadow/Web policy incidents and remediation actions in the Skyhigh CASB Incidents > Policy Incidents page.

