Create a Cloud Access Policy
To create a Cloud Access Policy:
- Go to Policy > Access Control > Access Policies.
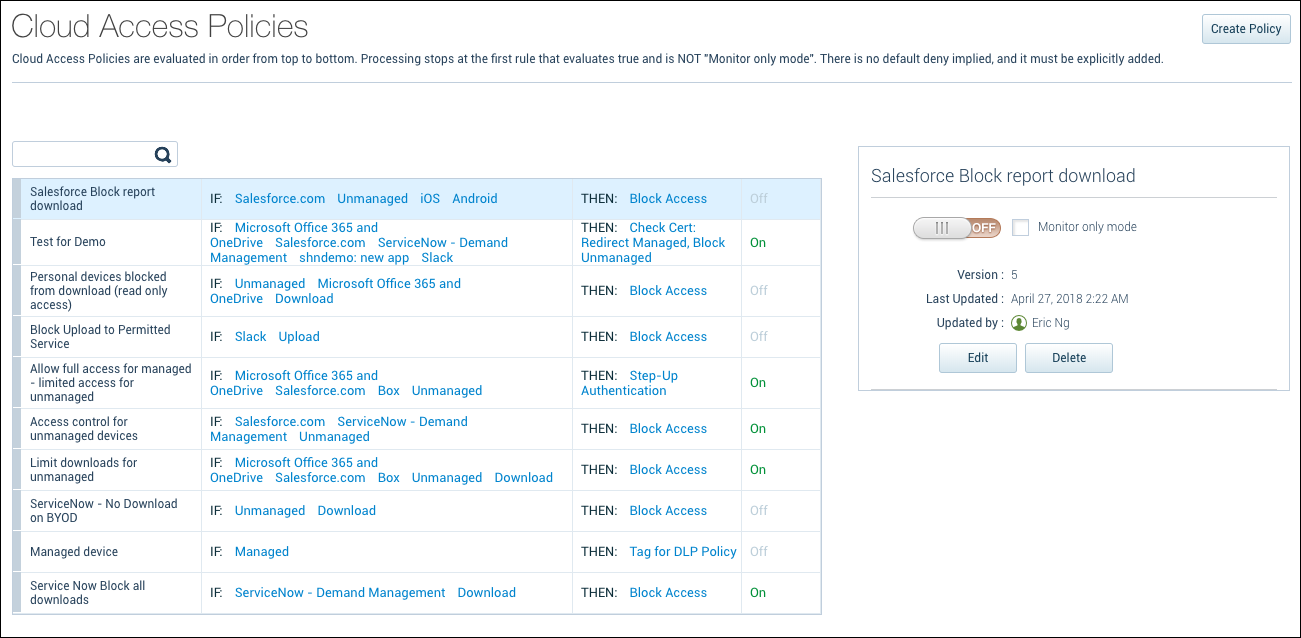
- Click Create Policy.
- Name. Enter a name for the Cloud Access Policy.
- Description. Enter an optional description of the policy.
- ON or OFF. Toggle to turn the policy ON or OFF.
- Monitor Only Mode. Select a monitor-only mode to have your rule create incidents only. The policy action is not taken.
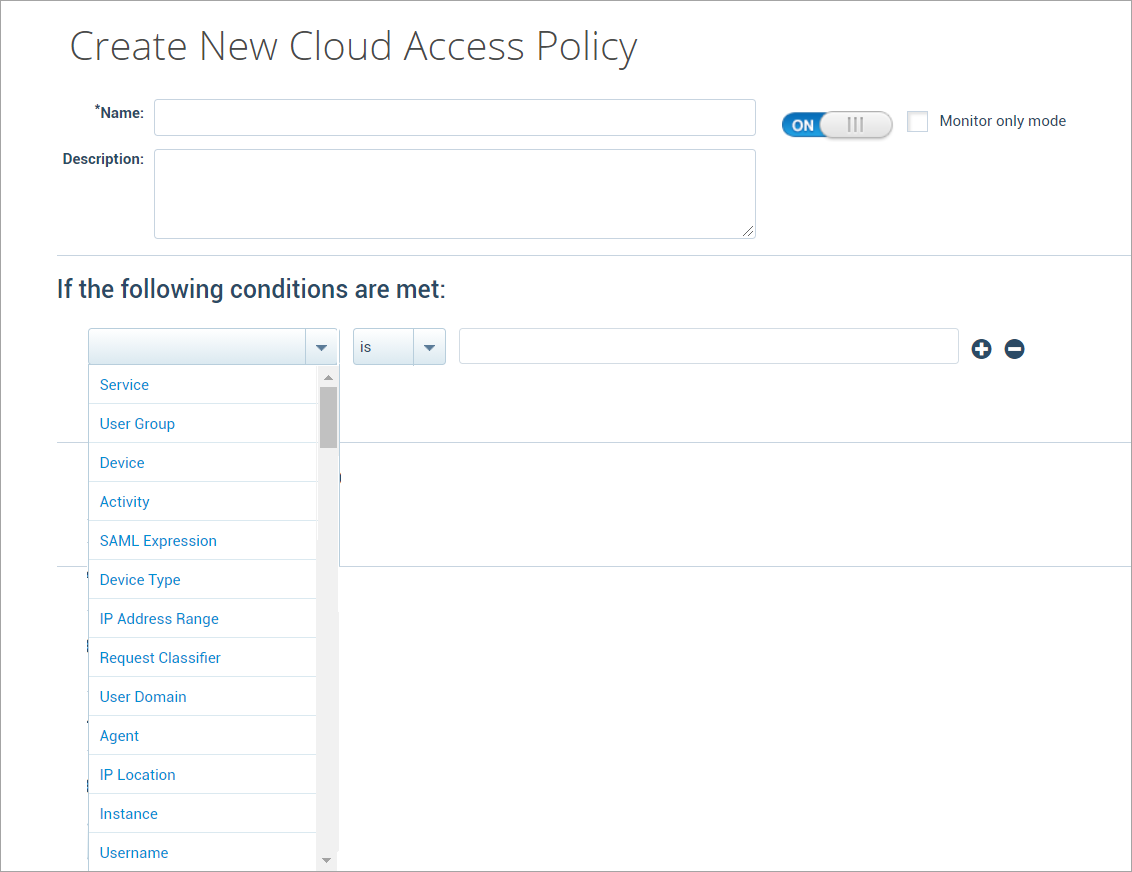
- Conditions. Policies are built around conditions (rules) and actions. Conditions are used with IS or IS NOT arguments to define the specific situation when a policy should be enacted. You can build out policies that contain several rules that include the following conditions:
- Service
- User Group
- Device
- Activity
- SAML Expression
- Device Type
- IP Address Range
- Request Classifier
- User Domain
- Agent
- IP Location
- Instance
- Username
NOTE: If you apply the conditions as User Group in the Cloud Access Policy, then the following parameter should be added in the Skyhigh CASB Admin portal.
- Under Addition config in TenantConfig page, add the following in the ADDITION CONFIG section. To add these parameter, contact Skyhigh Security Support.
{"common": {"usergroup_key":"ad_userprincipalname"}}
- Actions. Actions then determine what happens when a policy is enacted. Options include:
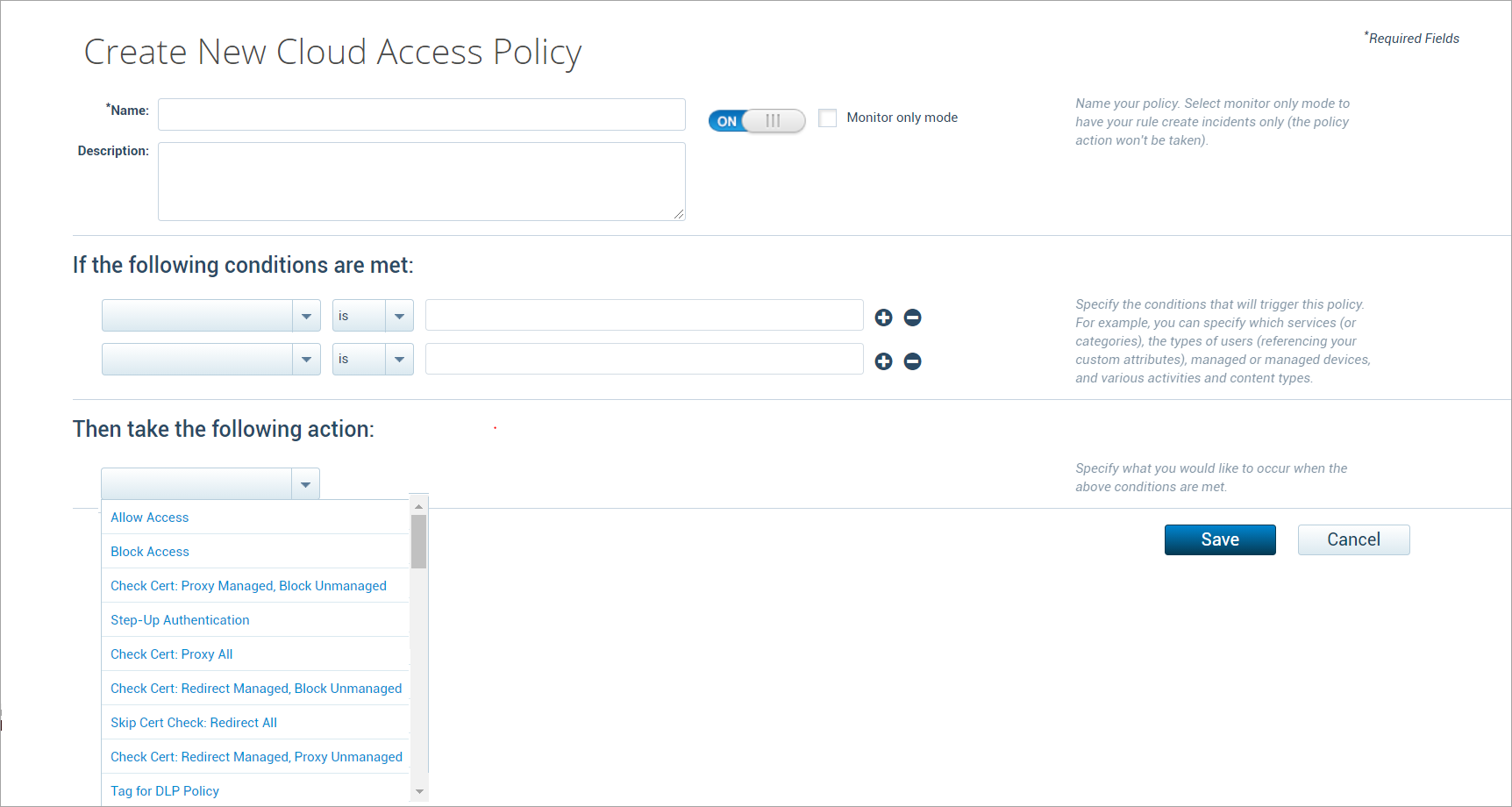
- Allow Access.
- Block Access.
- Check Cert Proxy Manage, Block Unmanaged. This binary policy for browser-based clients allows managed devices to access CSPs via the Skyhigh CASB reverse proxy. Unmanaged devices are blocked.
- Step-Up Authentication. Provides access to another authentication mechanism you define.
- Check Cert: Proxy All. This binary policy for browser-based clients allows CSP access to both managed and unmanaged devices post-authentication, but controls operations from unmanaged devices. For example, you can block downloads from unmanaged devices.
- Check Cert: Redirect Managed, Block Unmanaged. This binary policy for native clients allows managed devices to access CSPs via the Skyhigh CASB reverse proxy. Unmanaged devices are blocked. Skyhigh CASB is bypassed post-authentication for managed devices and redirected to CSP.
- Skip Cert Check: Redirect All. Skips authentication and redirects both managed and unmanaged devices to CSPs.
- Check Cert: Redirect Managed, Proxy Unmanaged. This binary policy for native clients displays the certificate check prompt in managed devices and allows managed devices to access CSPs via the Skyhigh CASB reverse proxy. Unmanaged devices are sent via proxy without a cert check prompt.
- Tag for DLP Policy. When all the CAP rules are evaluated as True, this action checks the DLP policy to perform a response based on the configured DLP policy. For this rule, a DLP policy needs to be configured with the particular Cloud Access policy.
- Click Save.

