Configure Managed Devices through Certificates
To configure Managed Devices through certificates:
- Log in to Skyhigh CASB and go to Policy > Access Control > Device Management.
- Under Establish Domain tab, enter the original domain as device.
- Under the Device Certificates tab, configure the following:
- Activate the checkbox Enable Certificate Checks.
- Upload the root certificate of the client device. If the single root certificate is uploaded, then the Maximum chain depth is 1.
- The multiple certificates are uploaded when the customer environment has more than one certificate through multiple MDM's. For details on using multiple CA certificates, see Multiple Certificate Authorities.
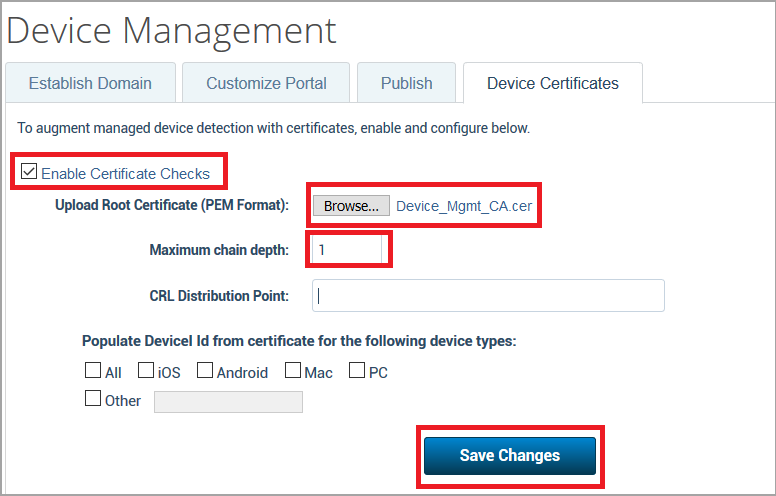
- The root certificates have to be concatenated by preserving both the BEGIN and END of both certificates and upload it as a single certificate file in the Skyhigh CASB. In this case, the maximum chain depth is 3.
- Click Save Changes.
Configuring Access Controls
NOTE: It is important to understand the limitations of the service provider and its associated applications that are supported by the reverse proxy. For example, Office 365 applications are not supported by Reverse Proxy but only the browser-based applications work for reverse proxy.
Configure the following access controls to cover the most common O365 use case:
- An unmanaged device (no certificate), using a native application gets blocked with a block message (rule 1 block unmanaged). For example, the OneDrive app on Windows.
- A managed device (with certificate), using a native application gets into O365 direct and no reverse proxy, it is possible to set up a sync (rule 1 redirect managed). For example, the OneDrive app on Windows.
- An Unmanaged device (no certificate), using Chrome (browser-based app) will get into O365 and redirected through a reverse proxy (rule 2 proxy unmanaged), where downloads are blocked. (rule 4 block access)
- A managed device (with certificate), using Chrome (browser-based app) will get in O365 directly and there will be no reverse proxy controls. (rule 2 - redirect managed)

Validate Office 365 Device Management
To verify the outcome of the managed device through certificates, perform the following validation scenarios:
Validate Managed Device
- From the trusted device, install the client certificate.
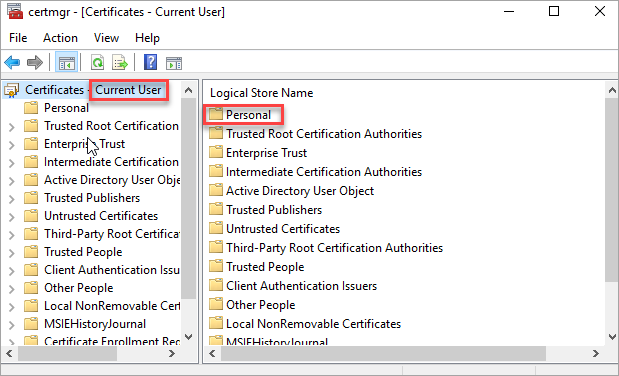
NOTE: If you are using Windows, make sure the certificate is stored in the user store and not in the machine store. If you open certmgr.msc, then you can see the certificate in the Current User > Personal folder.
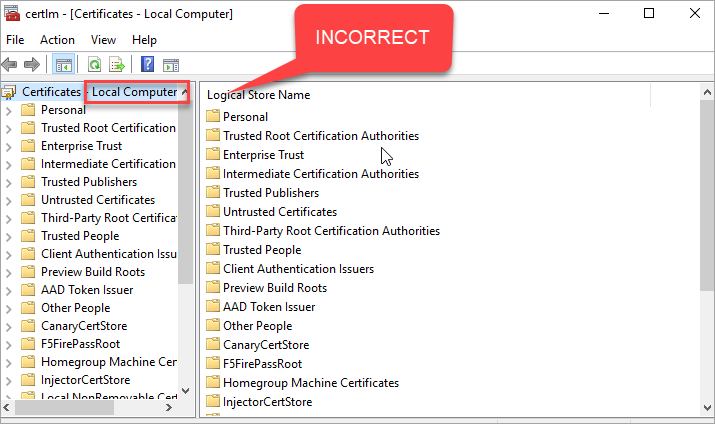
If you see the certificate in the Local Computer store, then this is the wrong place.
- Log in to Office 365. (https://login.microsoftonline.com)
- Log in with your demo SSO Office 365 account (CSP initiated). You are redirected to IDP for authentication.
- Once authenticated, you are redirected to the Office 365 Homepage.
- You are prompted to provide a client certificate, this validates your device is managed.
- If you are able to download a document, then your managed device has successfully passed through a certificate.
Validate Unmanaged Device
- From the trusted device, install the client certificate.
- Login to Office 365. (https://login.microsoftonline.com)
- Log in with your demo SSO Office 365 account (CSP initiated). You are redirected to IDP for authentication.
- Once authenticated, you are redirected to the Office 365 Homepage and you do not see any client certificate.
- You cannot download any document as the downloads option is blocked. This shows your unmanaged device.

