Vulnerability Incidents
The Policy Incidents page is a central repository of all incidents that have violated policies.
To view incidents that occur during your Vulnerability Scan:
- Go to Incidents > Policy Incidents.
- Filter for Incident Type > Vulnerability Violations.
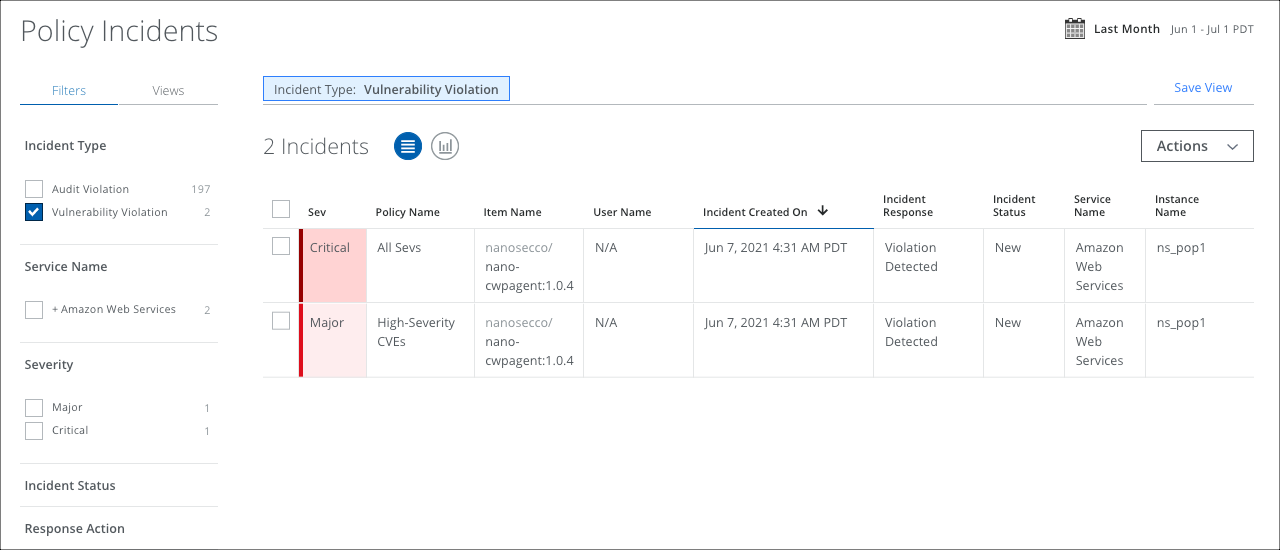
For complete details on the Policy Incidents page, see Policy Incidents Page.
Vulnerability Incident Cloud Cards
Click an incident table row to open the Vulnerability Incident Cloud Cards, which provides an extended view of incident details. The Cloud Cards include a list of all Vulnerabilities, then a link to the specific CVE you want to investigate. They also provide links to more information on container images and VM instances.
NOTE: To create a Vulnerability Report, see Report - Vulnerabilities.
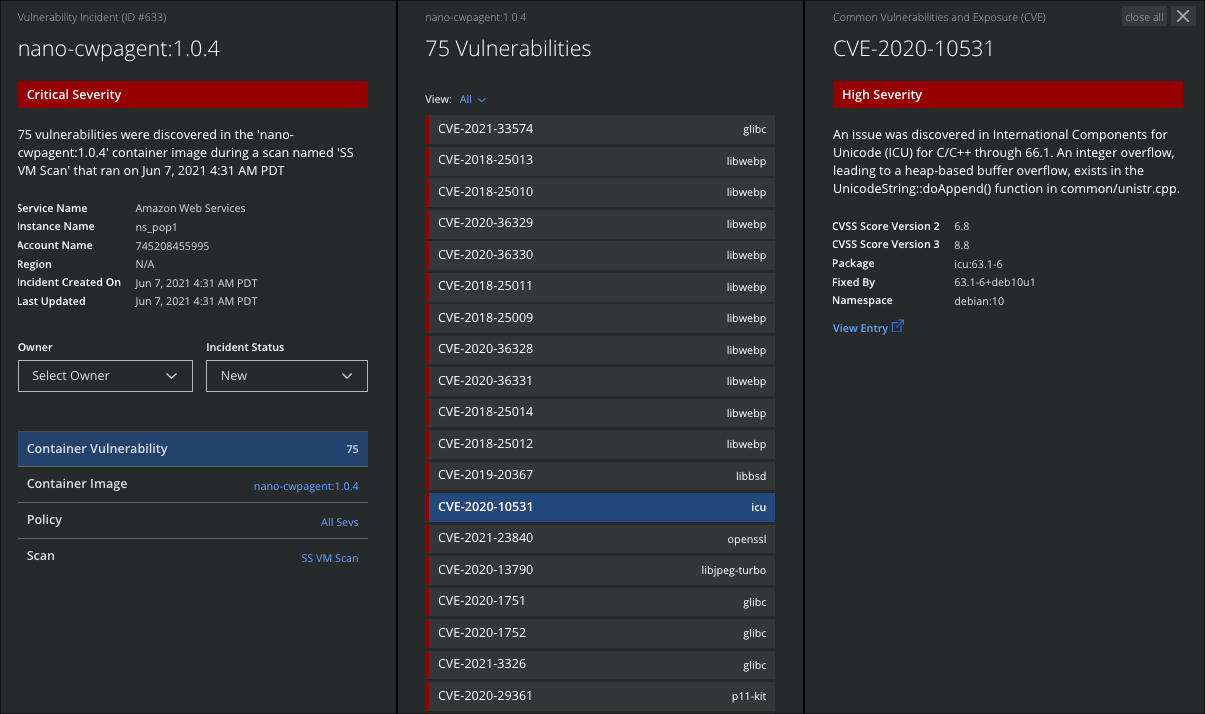
The Vulnerability Incidents Cloud Card provides the following information:
- ID
- Severity
- Service Name
- Instance Name
- Account Name
- Region
- Incident Created On
- Last Updated
- Owner. Select to assign an owner.
- Incident Status. Select to assign an Incident Status.
- Vulnerabilities. Click to open the Vulnerabilities pane. This lists all the Vulnerabilities found. Click an individual Vulnerability for more details, including:
- CVSS Score. The CVSS Version number and score for the Vulnerability. If no score is available, the score number displays as N/A.
- Package
- Namespace
- View Entry. Click to view the CVE entry at cve.mitre.org.
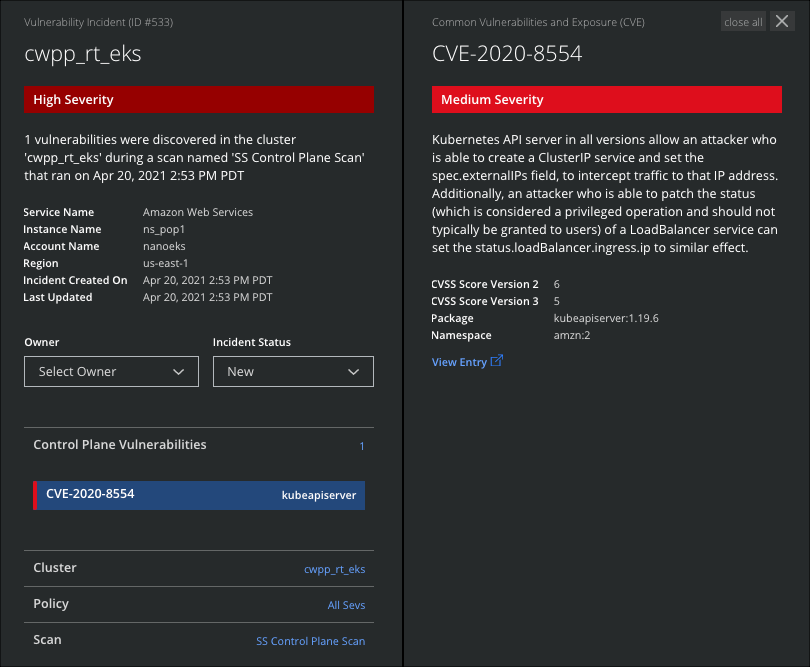
- Control Plane Vulnerabilities. Vulnerabilities in the main nodes of a cluster are displayed here.
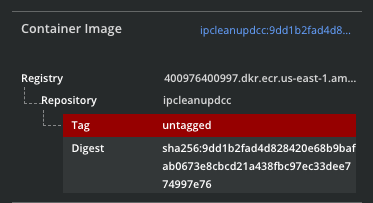
- Container Image. Opens a view of Registry and Repository details.
- VM Instance. Click to open the VM Instance in the Resources page.
- Policy
- Scan
- Incident History
Incident Severity vs. Vulnerability Severity
Vulnerability incidents use the severity designations Critical, Major, Minor, Info, and Warning.
Individual Vulnerabilities use the severity designations High, Medium, and Low.
Vulnerability Report
To generate a report for Container Incidents and Vulnerabilities, click Actions > Create Report > Vulnerability Report.
For details, see Report - Vulnerabilities.

