Skyhigh Security Cloud Release Notes 6.3.1 (April, 2023)
Skyhigh Security Service Edge 6.3.1 will be released to the EU Production environment on April 25, 2023, and to the US Production environment on May 2, 2023.
Skyhigh Data Protection
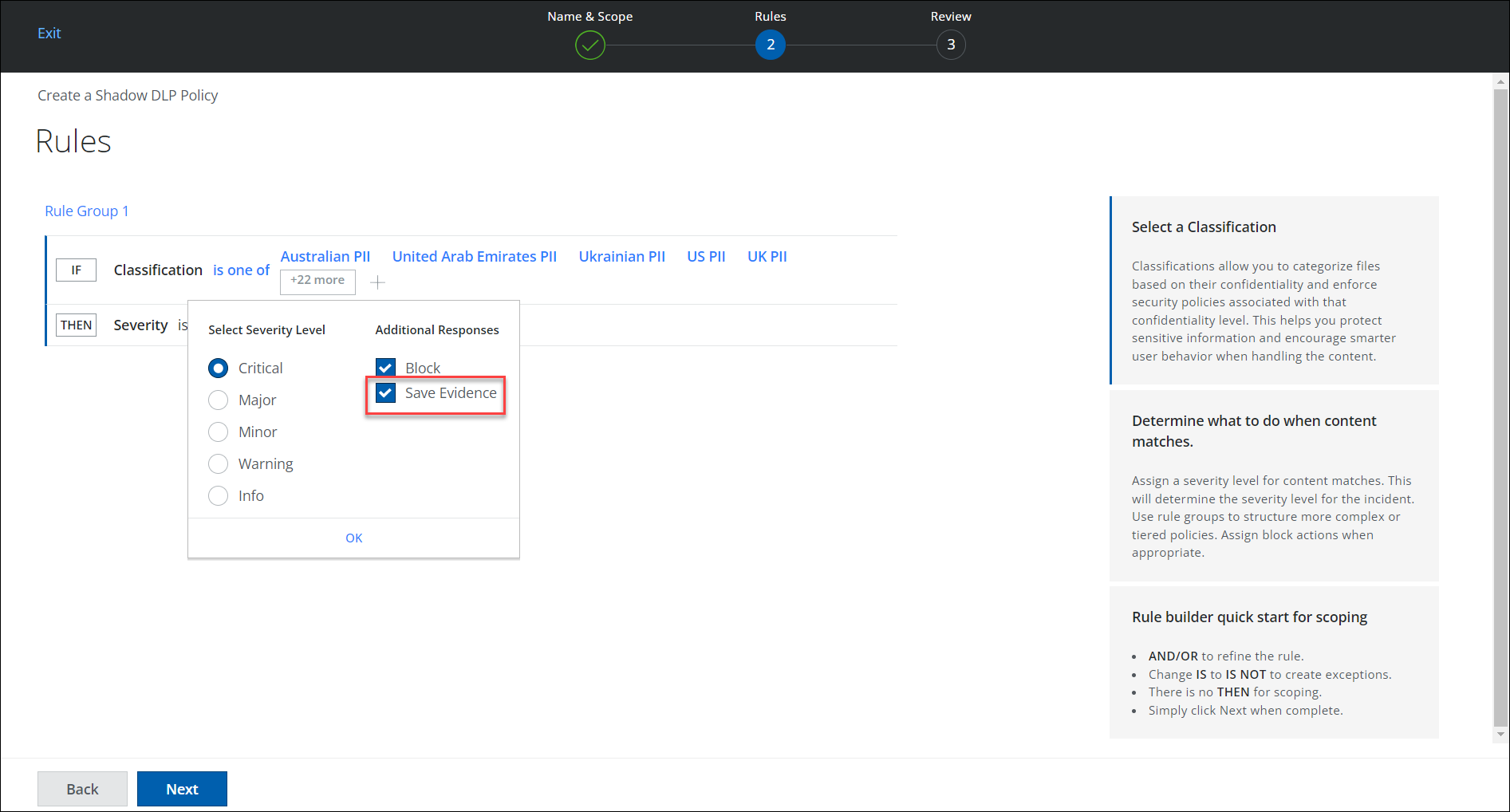
Save DLP Evidence Support for SWG (Limited Availability)
An additional response named Save Evidence can be found when creating a new rule in Web DLP Policy. When this response is triggered, you can save and store your web evidence files on your own data storage. This enables you to perform additional forensics on generated incidents. To store the web evidence files, data storage must be configured, and for the current release only the AWS data storage provider is supported. You can also download all the evidence files in bulk using the API. For details, see Save DLP Evidence.
Skyhigh Secure Web Gateway (Cloud)
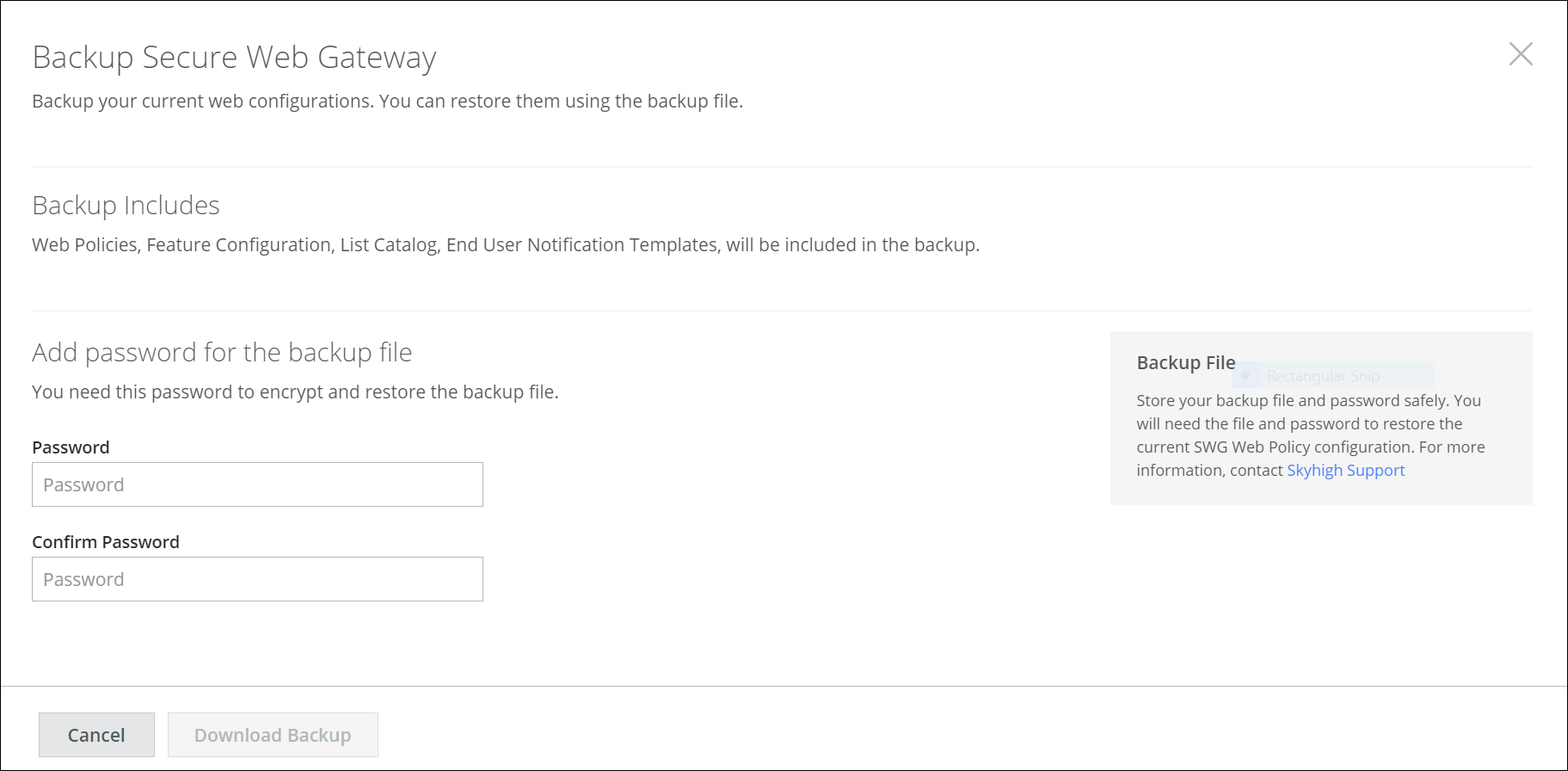
Backup and Restore Web Policies (Limited Availability)
When working on your web policy with Secure Web Gateway, new options for restoring are available. Using these options, you can:
-
Back up your web policy in a backup file and after continuing to work on your web policy for some time, restore it to the previous state using the backup file.
For more information, see Back Up Your Web Policy and Restore Your Web Policy from a Backup File. - Replace the web policy that you are currently working on and restore a web policy instead that uses the default values as they were preconfigured when you initially set up Secure Web Gateway.
For more information, see Restore the Default Values for Your Web Policy.
Skyhigh CASB
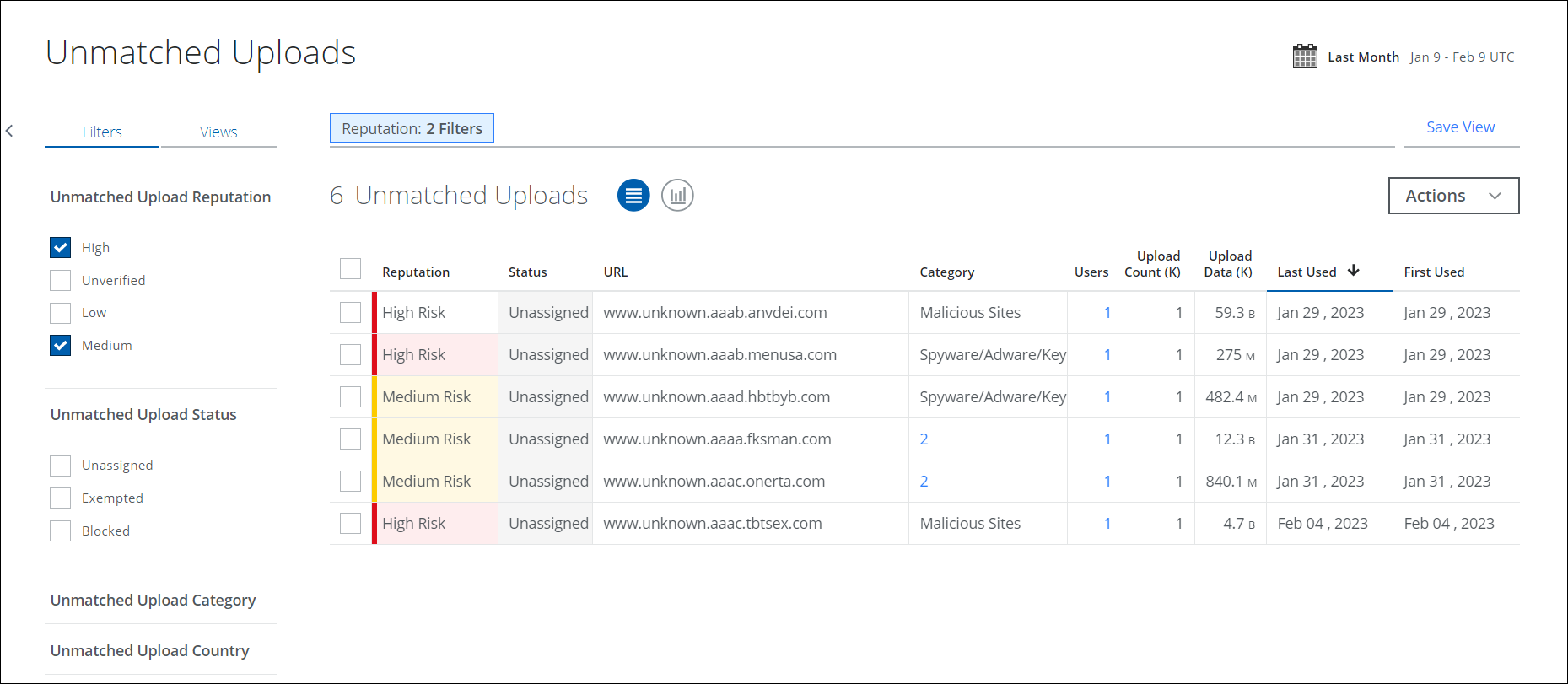
Redesigned Unmatched Uploads
The Unmatched Uploads page (found under Analytics > Unmatched Uploads) displays any data moving outbound from the organization to a destination that is not mapped in the Cloud Registry. The data could be a new (unmapped cloud service) or a potentially suspicious destination. This page provides information about the number of users and volume of data being sent to these destinations with enrichment information like reputation, IP address, and location.
This improved version of the Unmatched Uploads page provides granular information about the users accessing these destinations as well as the risk (or reputation) of these destinations. There are new workflows that allow users to update the status of the URLs if that is a trusted unmatched cloud service and request new cloud services to be added to the Registry.
This page provides powerful search and filtering capabilities and exports detailed information on users responsible for unmatched uploads that to a CSV file. The Saved View can be created for your search query and you can add dashboard cards from Saved View. In addition, the status of multiple unmatched uploads can be modified simultaneously. The Unmatched Uploads data is stored for 100 days unless the Skyhigh SSE Data Retention option is purchased which extends the data retention for a full year. For details, see Unmatched Uploads.
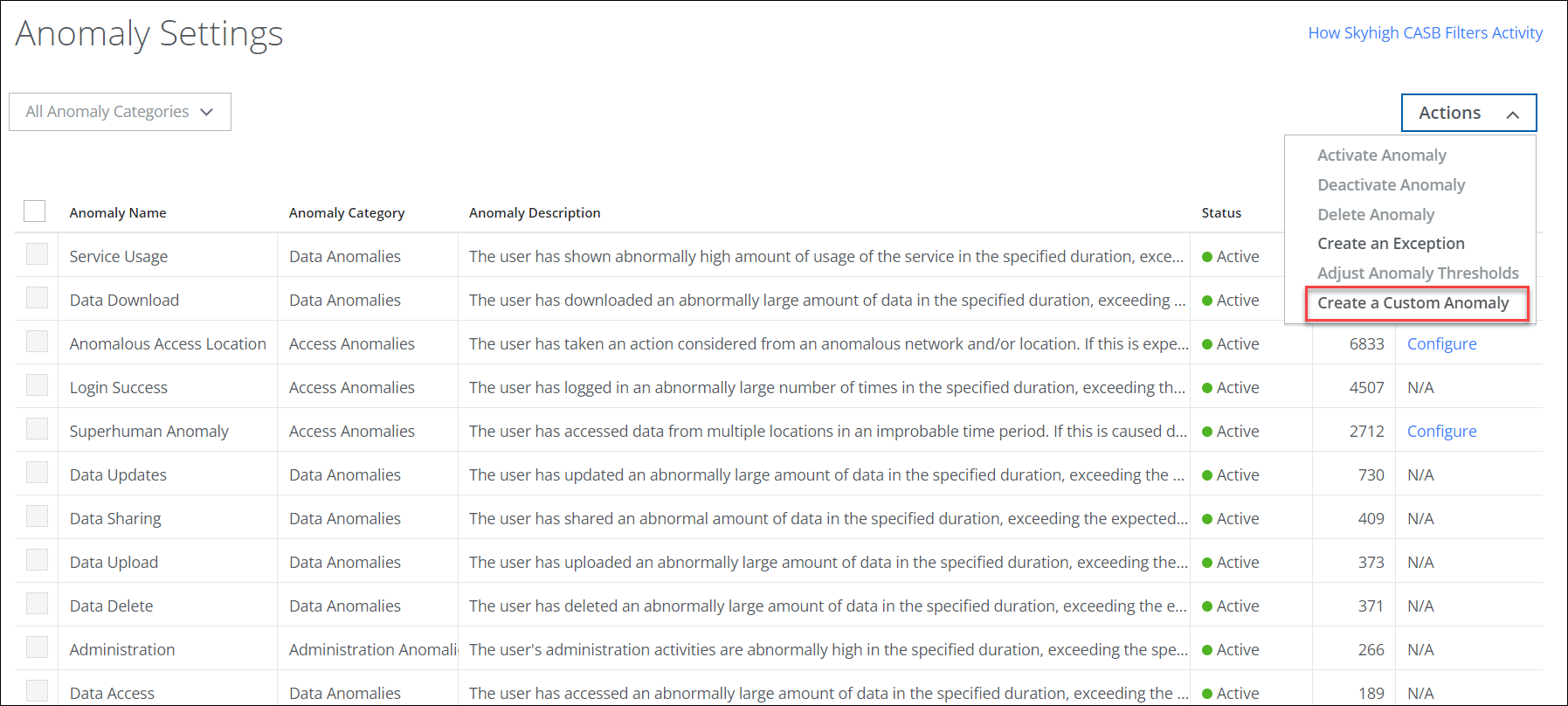
Custom Anomaly
Custom Anomaly is a new anomaly type or category on the Anomaly Setting page (found under Incidents > Anomalies > Anomaly Settings) that enables you to create your own anomaly structure based on the risk parameters identified in the Sanctioned IT cloud service activities. You can define Custom Anomalies by configuring the rule with the available risk parameters such as activity type/category, activity count, location, source, source IP, user agent, device ID, and device. Constructing anomalies allows you to align with your organization's risk posture and raise an incident when anomalies are detected so that users can investigate and take necessary remediation action. Custom anomalies can be removed, activated, or deactivated. For details, see Custom Anomalies.
Custom anomalies can be defined with different risk parameters. For an example, a possible use case for Activity Type/Category is given here: suppose you want the anomalies to be triggered when a user fails to log in to Salesforce outside of India, or Indonesia and attempts to log in more than five times a day. You can achieve this by defining custom anomalies with the required criteria, and when those criteria are met, incidents are generated.
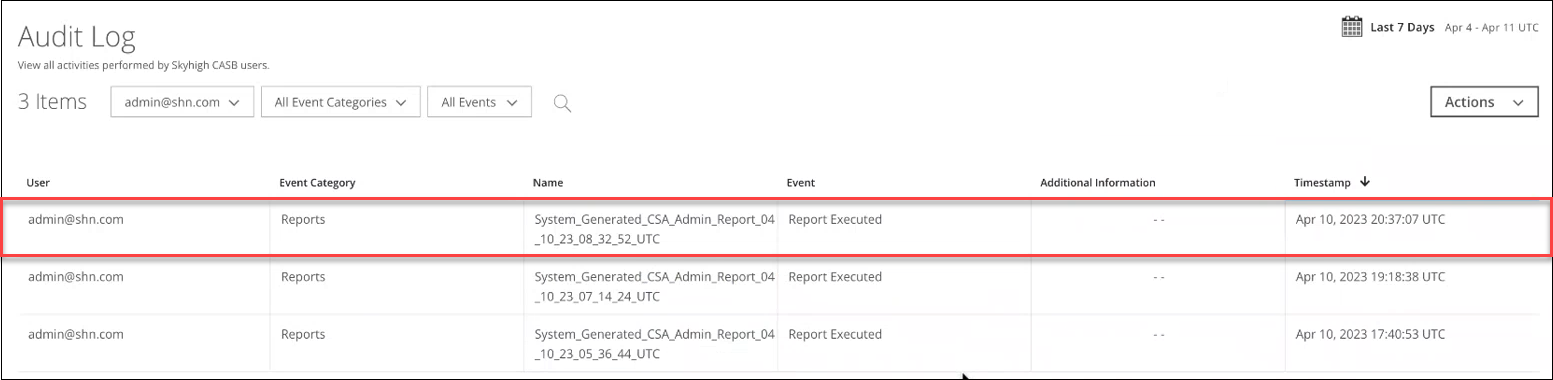
Cloud Security Advisor Admin Report Events in the Audit Log
The Audit Log now includes Cloud Security Advisor Admin Report events. For details, see Audit Log Events. Users can view the System Generated CSA Admin Report execution details on the Audit Log page (found under Settings > Audit Log). For details, see View CSA Admin Report Events in the Audit Log.
Skyhigh CNAPP
New and Updated Azure CIS v2.0 Policy Templates
CIS Benchmarks are based on technical configuration settings used to maintain and increase enterprise security, especially when used in conjunction with other essential cyber hygiene tasks. In this release, 11 new Azure Policy templates have been added and 3 existing Azure Policy templates have been updated for the CIS v2.0 benchmark. For details, see Policy Templates for Azure.

