Configuring TACACS Authentication
Authentication to the local Admin App running on the Skyhigh CASB on-prem proxy can be configured to use the TACACS+ protocol in combination with an external TACACS+ server to authenticate and authorize access to the local Admin App.
TACACS+ is intended only for controlled access to the admin app on the on-prem proxy. End-user authentication to Salesforce is done via SAML proxy, not using TACACS+.
IMPORTANT: Policy configuration is done in the Skyhigh CASB Dashboard. Log into the Skyhigh CASB Dashboard using your Skyhigh CASB credentials (which are different from TACACS+ credentials).
Step 1: Configure the TACACS+ Servers
Log into the Skyhigh CASB Network's on-prem proxy's local Admin App using the credentials created during installation of the OVF. Navigate to the section (screenshot will be added at time of release) concerning local authentication.
For each TACACS+ server, you must supply the following:
- Hostname or IP address of the TACACS+ server
- Port # of the TACACS+ service. Default value is 49.
- The shared secret specific to that server.
A test button is provided that will allow the admin to enter in a username and password combination that will be used in a trial authentication to the TACAS+ server. The results of the test authentication will be shown. If the TACACS+ server cannot be reached at this stage, go back and check the settings you used in this step.
At least one server must be completely specified for TACACS+ authentication to work. Optionally, you can add configurations for an additional two servers. Each server will have its own shared secret. The authentication code will try to authentication against each configured TACACS+ server in the order that they are configured.
The Skyhigh CASB TACACS+ client uses the following settings for authentication and authorization. These are not configurable:
- The authentication type is PAP
- The service is LOGIN
- The "port" string in the TACACS+ messages will be set to the string, "AdminApp"
- The "remote address" will be set to the IP address of the connecting client's machines (the IP of the machine from the admin is accessing the admin app)
- The privilege level will be set to USER
After successful authentication, the software will send an authorization request to the TACACS+ server with additional parameter:
- "service" will be set to "SkyhighEncryptionGW"
The proxy will expect to get back an attribute from the TACACS+ server that would indicate one of the following conditions:
- The user is not authorized for this service
- The user is allowed read-only access to the admin app
- The user is allowed full access to the admin app
The packet and logic flow is illustrated here:
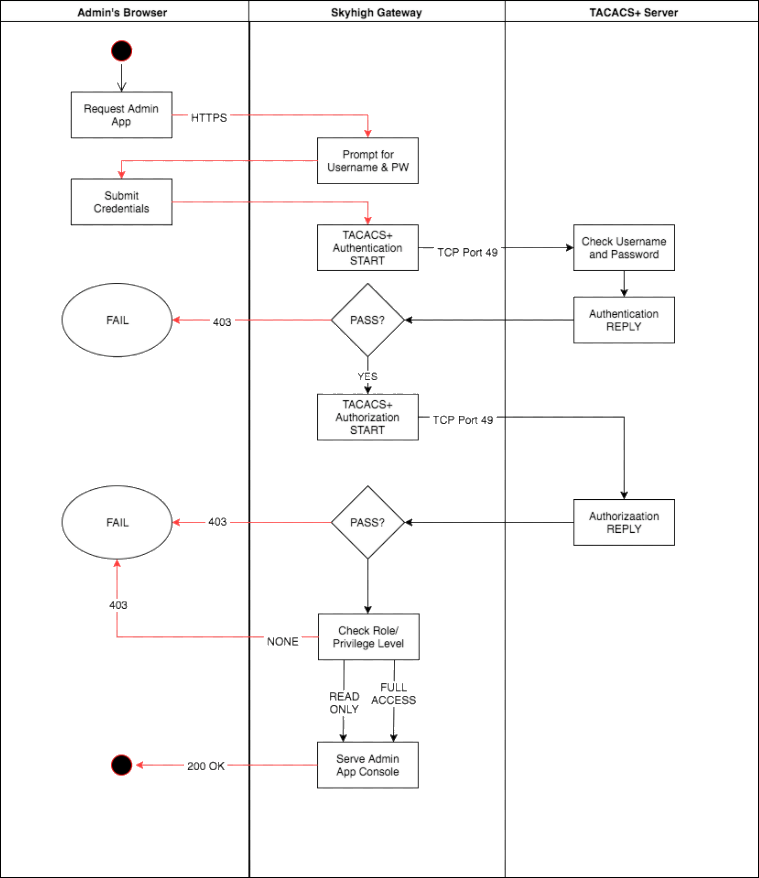
(Optional) Step 2: Disable Local Login
After you have successfully configured TACACS+ and have tested it end to end, login to the admin app and disable local authentication. This will render the software in a state that only successful TACACS+ authentication will allow local access to the proxy. This step is not recommended. Instead, Skyhigh CASB recommends leaving the local access credentials in place but limit their use and distribution.
NOTE: TACACS+ events and errors will be sent to the log file. If external logging is enabled, this log messages will be logged externally.

