Configure SAML and SSO for Skyhigh Cloud Administrators
IMPORTANT: You must enable SSO and configure SAML from the Trellix Identity Provider (found under product selection) page. The SAML Configuration (found under Settings > User Management > SAML Configuration) page is decommissioned and this page is read-only. To enable SSO and configure SAML from the Trellix Identity Provider page, you must have a Skyhigh User Manager role with Manage access. To add or edit the user access on the Users (found under Settings > User Management > Users) page, see About the Users Page. For SSO and SAML configuration details, see Primary User - Identity Provider.
Skyhigh Security allows you to configure a login workflow that enables Skyhigh Security Cloud administrators to log in to Skyhigh CASB via Single Sign-On (SSO). You can enable SSO and configure Security Assertion Markup Language (SAML) for Skyhigh Security Cloud admins to enhance security and streamline access management.
NOTE: Skyhigh CASB provides you with the ability to create and manage multiple SAML configurations without impacting your existing Skyhigh CASB SAML configuration. Your existing SAML-based logins continue to work as expected. Follow the steps below to create a new SAML configuration that is saved separately within Skyhigh Security IAM systems.
Use these steps to enable SSO and configure SAML:
- ► Step 1: Set up SAML in Your IdP App
-
You must set up SAML in your IdP application to use the IdP App's SAML configuration details such as Issuer URL, Single Sign-On URL, and SAML certificate in Skyhigh CASB. The following example uses Okta as the IdP app for reference.
To set up SAML in your IdP app:
- Log in to Okta.
- In the Okta Admin console, go to Applications > Applications.
- On the Applications page, click Create App Integration.
- Select SAML 2.0 as the Sign-in method, and click Next.
- Under General Settings, configure the following:
- App Name. Enter the name for your Single Sign-on solution.
- App logo (Optional). Upload the logo for your Single Sign-on solution.
- App Visibility. Set the visibility of your application icon to users or in the Okta Mobile application.
- Click Next.
- Under Configure SAML, enter any URL as placeholder information for the following:
- Single sign-on URL.
- Audience URI (SP Entity ID).
- Default RelayState.
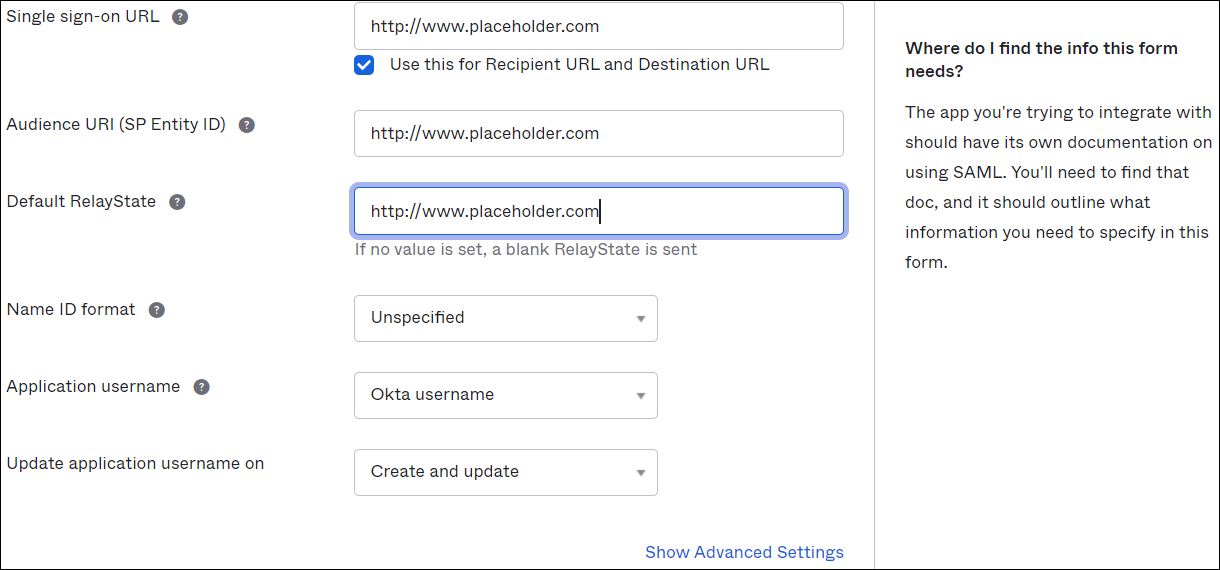
- Click Next.
- Under Feedback, configure the following:
- Are you a customer or partner?. Select I'm an Okta customer adding an internal app.
- App type. Activate the checkbox to specify that the Single Sign-On application is internal.
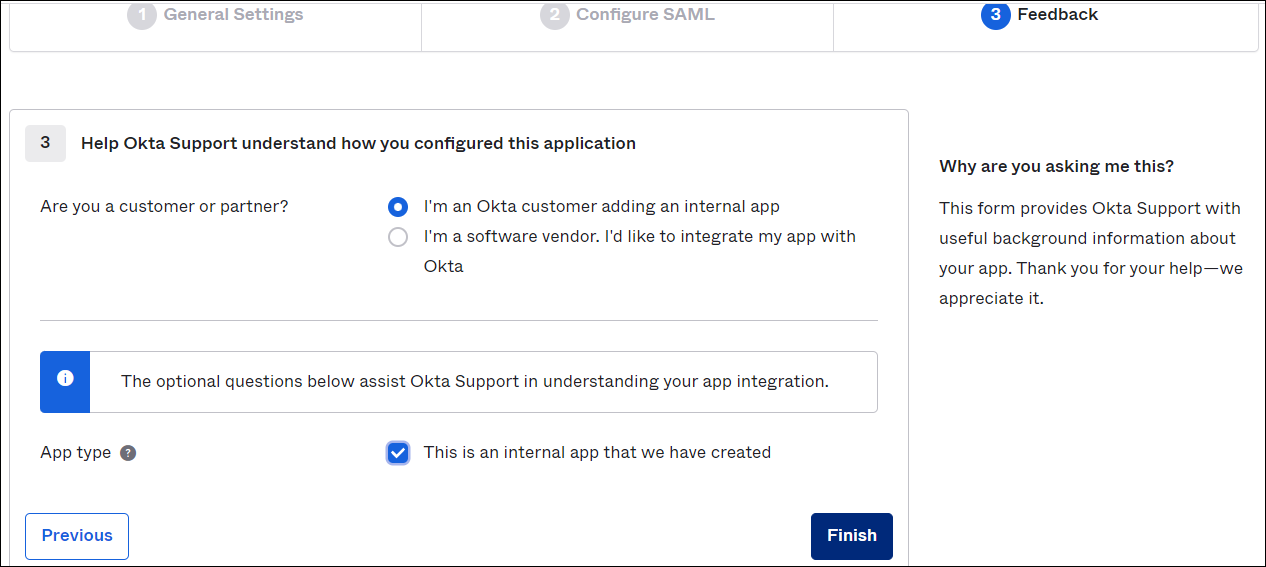
- Click Finish.
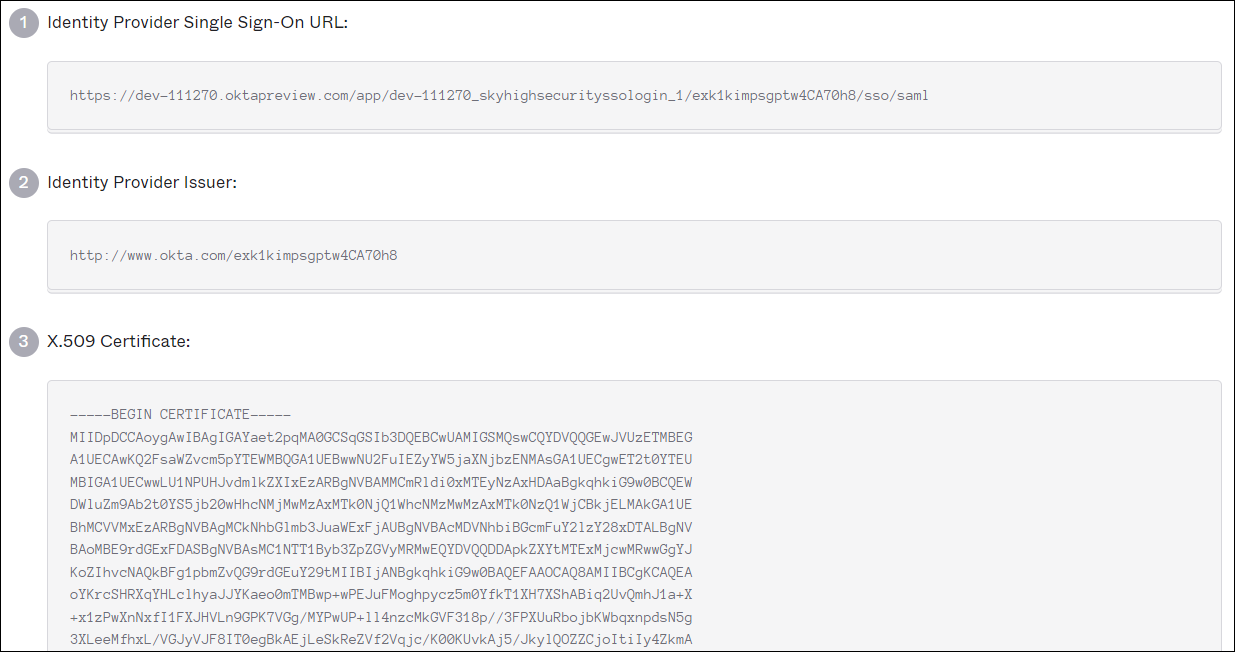
- On the SAML Setup page, under SAML Setup, click View SAML setup instructions. Use the following information to configure SAML in Skyhigh CASB:
- Identity Provider Single Sign-On URL. This is the Login URL required for Skyhigh CASB.
- Identity Provider Issuer. This is the Issuer URL required for Skyhigh CASB.
- X.509 Certificate. Download this certificate to upload it to Skyhigh CASB.
- ► Step 2: Configure SAML
-
You must configure SAML from the Trellix Identity Provider page. To configure SAML, follow the instructions provided on Primary User - Identity Provider. The Identity Provider page allows you to add or update the configurations to enable Single Sign-On (SSO) using your identity provider. The supported protocol is SAML 2.
- ► Step 3: Configure Your IdP App SAML Settings
-
Once you have connected Skyhigh CASB to IAM, you must return to Okta and update your IdP App's SAML settings with the SAML configuration details received from Skyhigh CASB.
To configure your IdP app SAML settings:
- In the Okta admin console, go to Applications > Applications.
- Select the General tab for your newly created IdP application.
- For SAML Settings, click Edit.
- Click Next.
- On the Edit SAML Integration page, under SAML Settings, configure the following:
- Single Sign-On URL. Enter the Assertion Consumer Service URL from Skyhigh CASB.
- Audience URI. Enter the Audience URL from Skyhigh CASB.
- Default RelayState. Set this value to https://auth.ui.trellix.com/.
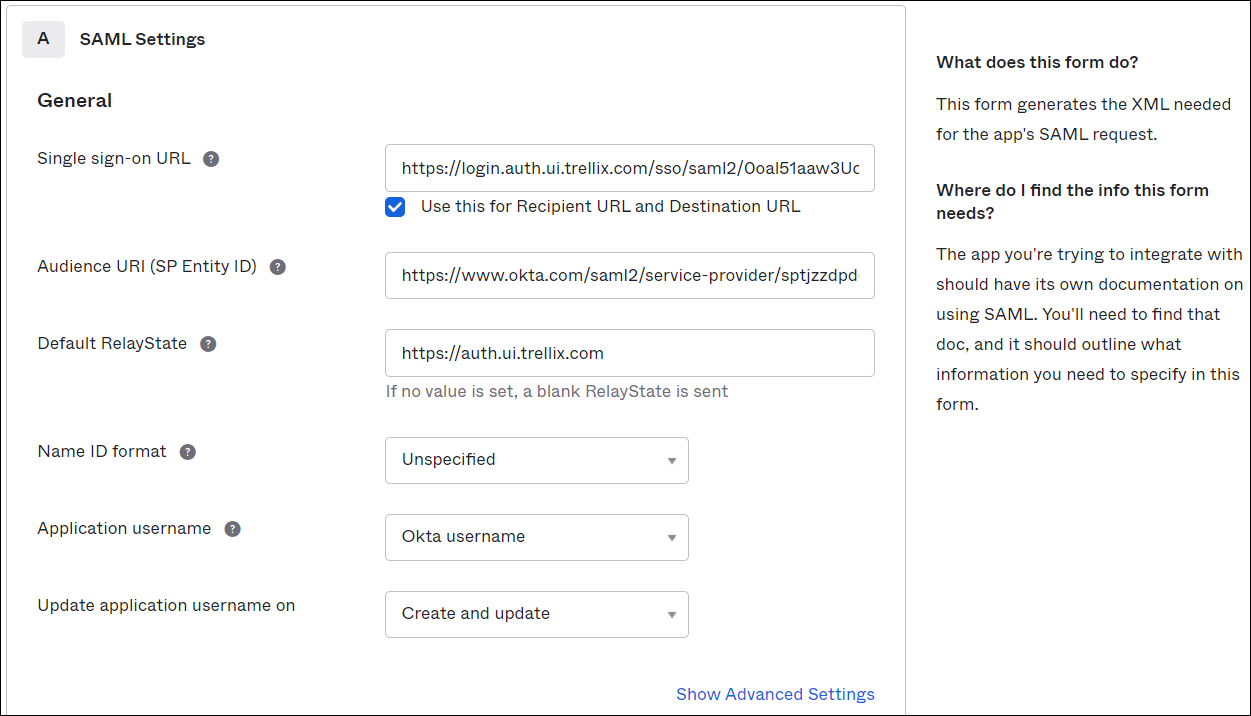
- Click Next, and click Finish.
- Select the Assignments tab to enable SSO for selected users.
- Go to Assign > Assign to People.
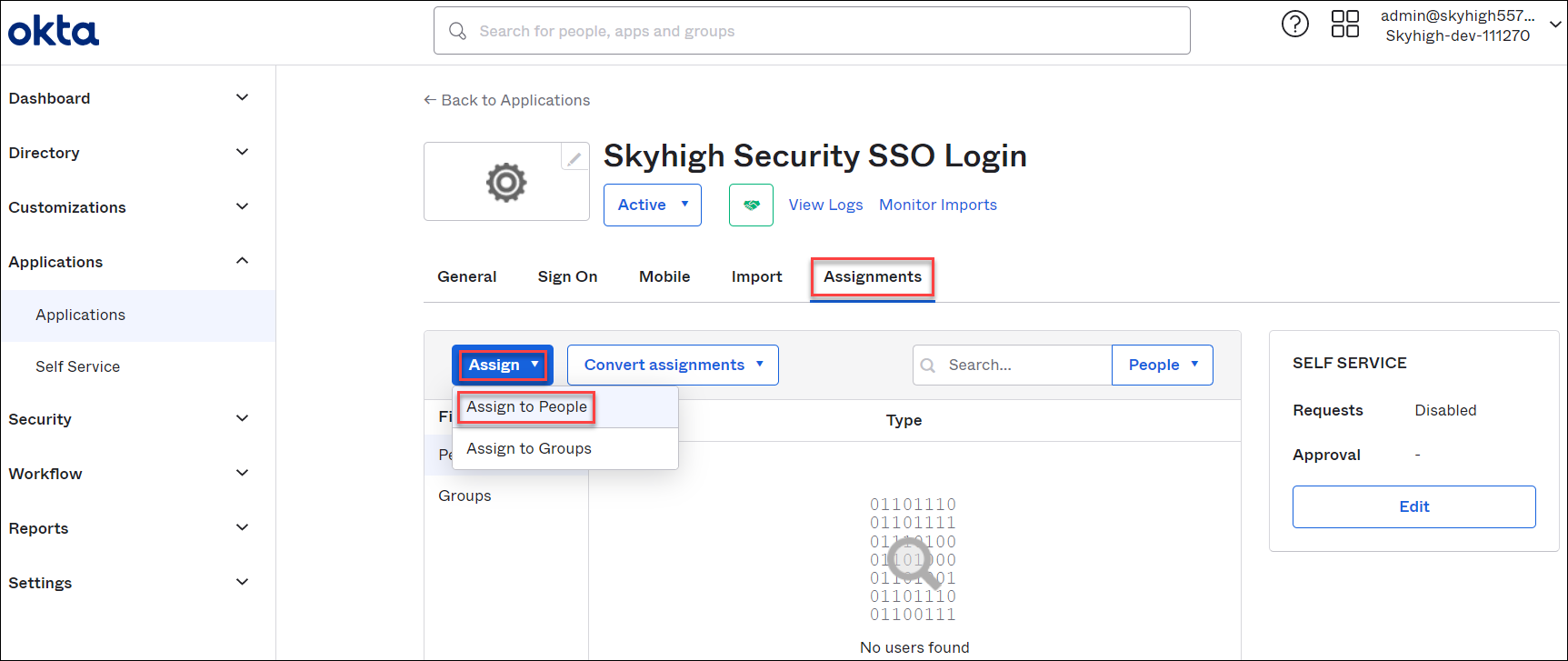
- Select Assign corresponding to the user, and click Done.
NOTES
- To enable SSO for new users, create a new user in Okta with the same email address and password as the Skyhigh CASB user.
- SCIM (System for Cross-domain Identity Management), and automatic user creation are not supported.
- Click Save and Go Back.
- Click Done.
- Configure the app to send the following user attributes to the IdP provider. (These are recorded in the Skyhigh Security IAM section. Individual users have the option to edit First Name and Last Name at any time after logging into Skyhigh CASB.)
- First Name
- Last Name
- Email.
IMPORTANT: You can test SSO login for Skyhigh CASB once you enable SSO and configure SAML for Skyhigh Security Cloud admins. This confirms that Skyhigh Security Cloud admins can log in to Skyhigh CASB without separate login credentials. For details, see Test SSO Login for Skyhigh CASB.
Test SSO Login for Skyhigh CASB
To test SSO login for Skyhigh CASB:
- Go to your organization's Okta domain. For example, myorg.okta.com.
- Log in to Okta using admin credentials.
These credentials must belong to the admin assigned with SSO while configuring your IdP app's SAML settings.
NOTE: You can only log in to Skyhigh CASB via SSO from your IdP application. If you try to log in to Skyhigh CASB via SSO from the Skyhigh Security login page, an error is displayed.
- Under My Apps, select the newly configured application.
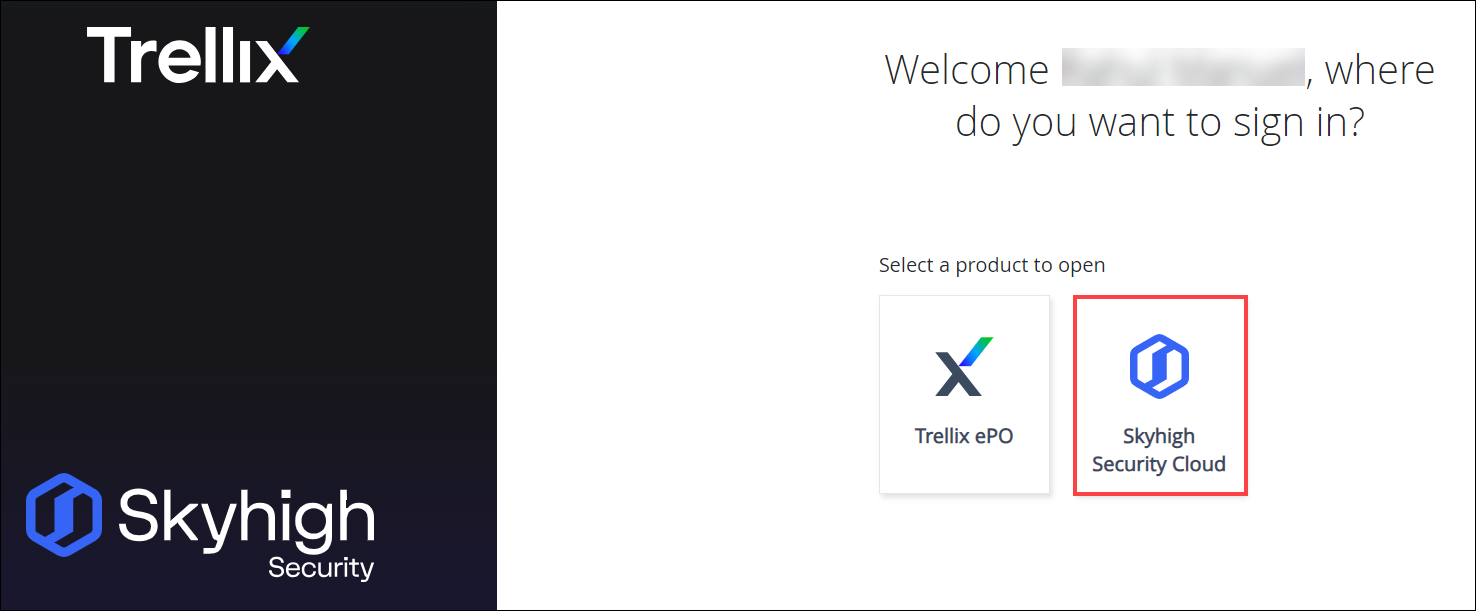
Once the configuration is successful, you are redirected to the Skyhigh CASB dashboard or the product selection page (Trellix ePO or Skyhigh Security Cloud). - On the product selection page, select Skyhigh Security Cloud, then perform the allowed admin activities in Skyhigh CASB.
Troubleshoot SSO Login for Skyhigh CASB
If the SSO user is not in the Skyhigh Security Cloud login database, you can receive a nondescript 400 error code from the IdP.
To troubleshoot SSO:
- Make sure the user has been assigned to the application in the IdP.
- Make sure the user exists in the Skyhigh CASB page Settings > User Management > Users.
- Make sure the user's first name, last name, and login ID configured in the IdP match what is in Skyhigh CASB.

