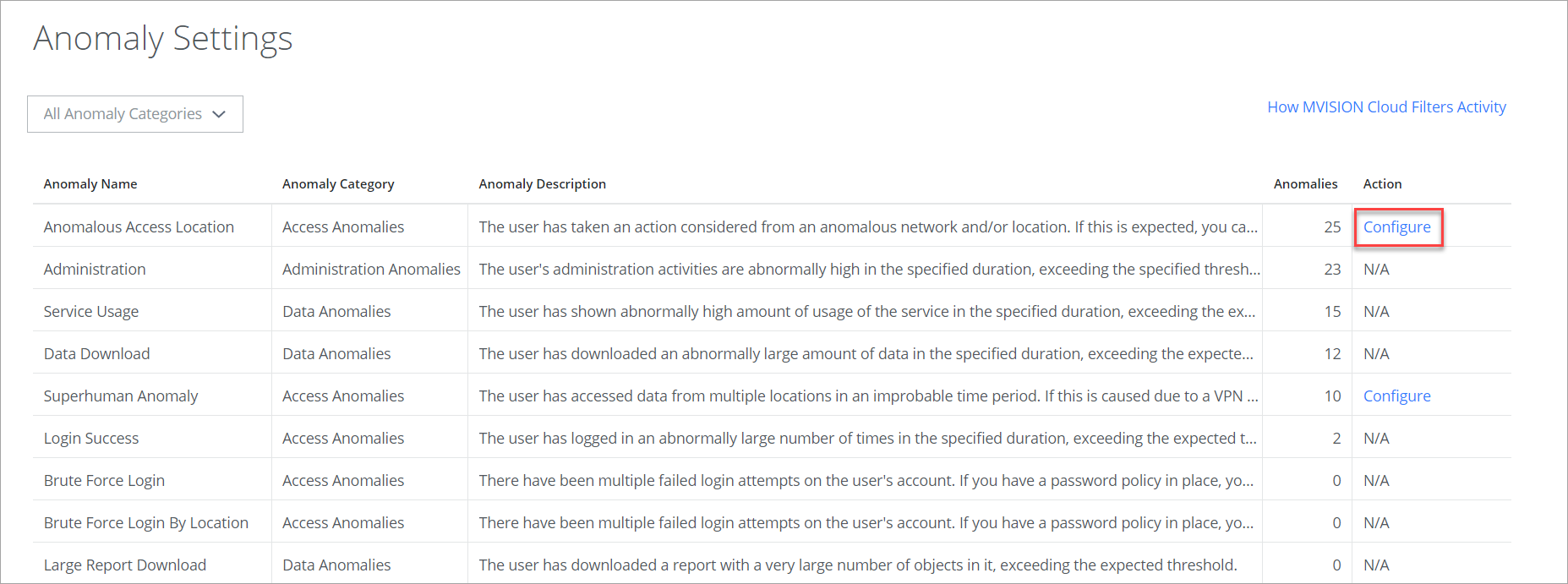
Configure Anomalous Access Location Filters
Anomalous Access Locations are a specific type of Access anomalies that may indicate potentially compromised accounts or insider threats. This anomaly is detected when a user registers activity from an IP Address, Geographic Location, or an Organization that is suspicious, block listed, or a competitor. Anomalies are detected using Skyhigh CASB's block list leveraging User and Entity Behavior Analytics (UEBA).
To access Anomalous Access Location, go to Incidents > Anomalies > Anomaly Settings.
To configure Anomalous Access Location Filters, click Configure.
There are seven filters that fine-tune Anomalous Access Locations. Your organization can leave some filters turned off if they don't assist your workflow. The goal is to find settings to help eliminate false anomalous events and zero in on the anomalies that are especially mission-critical.
Anomalous Access Location Filters support these functions:
- User Agent Allow listing. Supported for managed devices or applications. Here, a user can allow the browser. Any activities passing through the allow list browser do not trigger an anomalous event. But if any other browsers are used besides allow list browsers, an anomaly could be triggered.
- User Agent Block listing. A user can block the browser, and if any activities are carried out in the block-listed browser, an anomaly could be triggered.
- User Agent Activity Trust. An in-built trust is calculated by the activities carried out by the users and consists of past and current user activities. If the user has taken the previously used user agent and the user device, your activities are allowed regardless of where the user is logging in from.
- User Agent Threats. Identifies malicious activities based on spurious or known bad user agents.
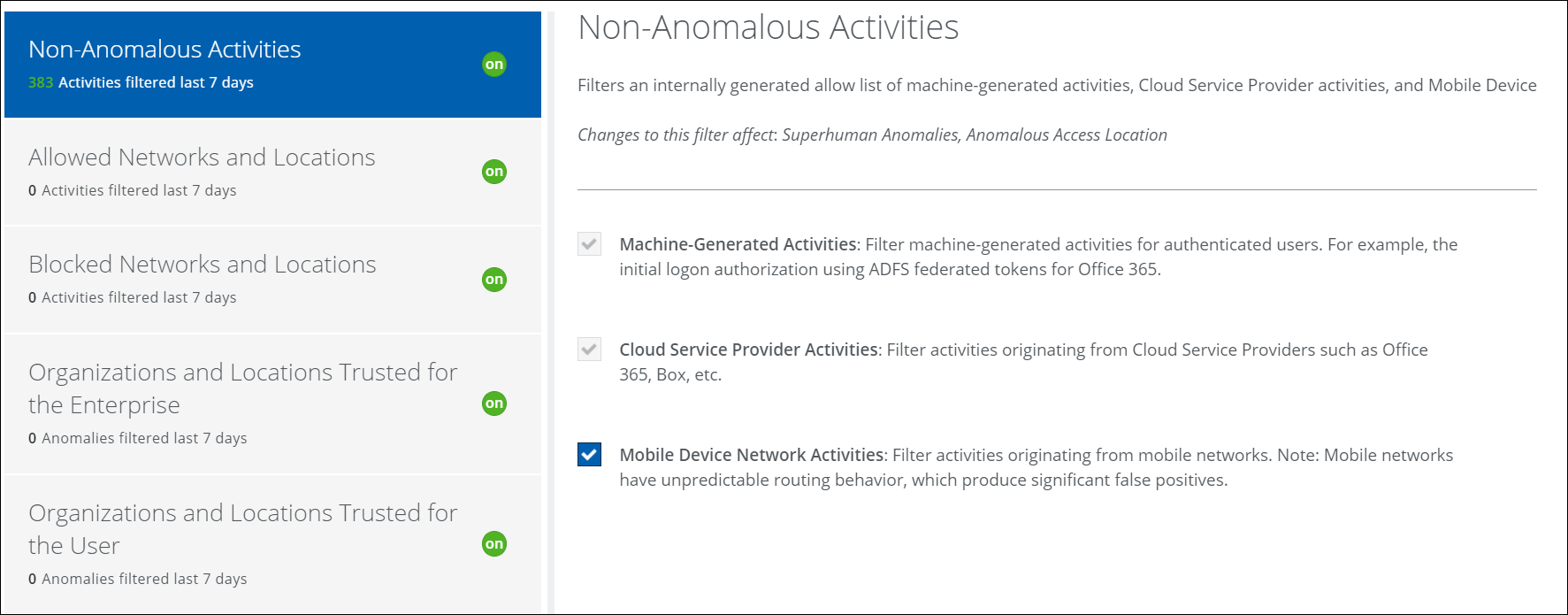
Non-Anomalous Activities
This filter works from an internally generated allow list of machine-generated activities for authenticated users, activities from Cloud Service Provider activities, and activities originating from Mobile Device Network activities.
This filter is on by default and cannot be turned off, but you can refine what is filtered.
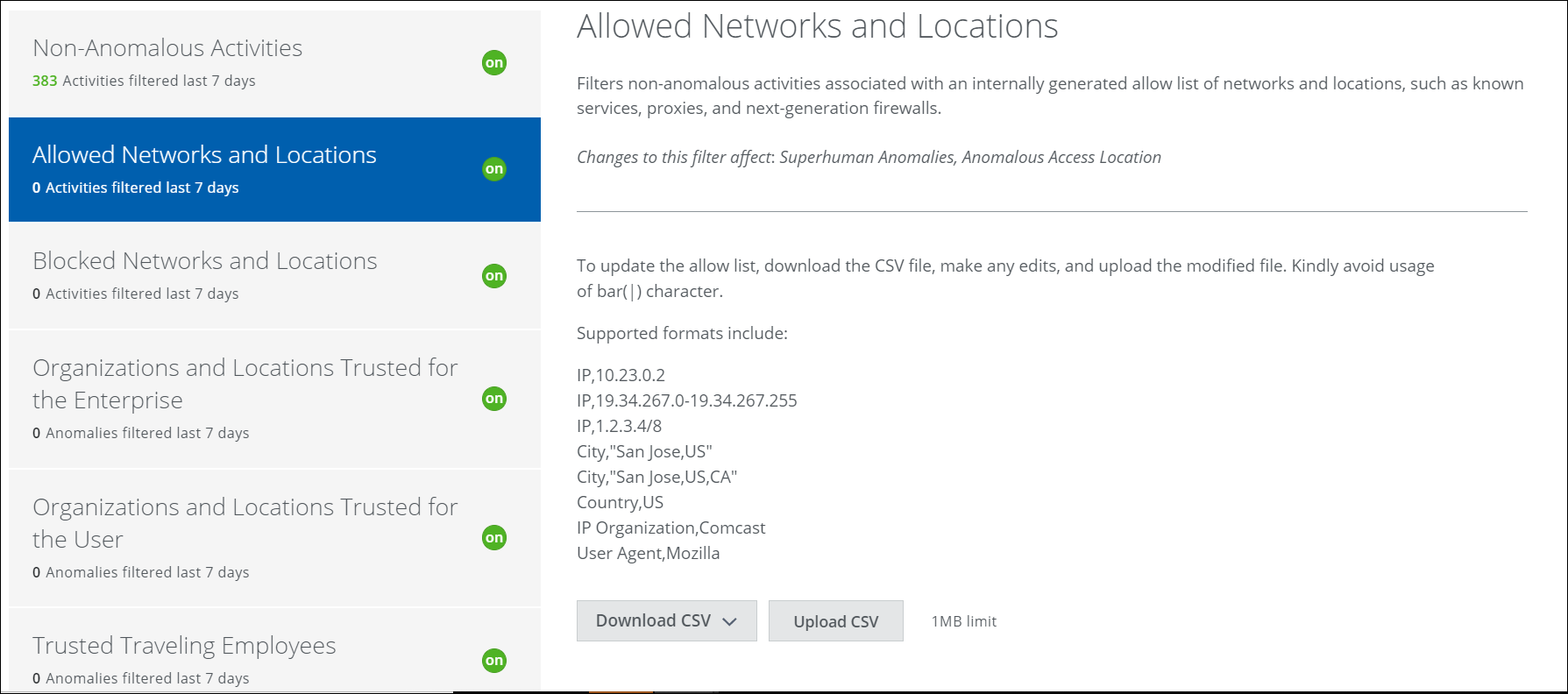
Allowed Networks and Locations
When enabled, this filter identifies anomalies that are generated from a list of edge devices, proxies, firewalls, and locations to catch switching behavior caused by activities generated with metadata associated with devices at the edge of your internal network. Activity passing through allow list IPs does not trigger anomalous events. But if an email is opened from an IP where there is no allowed egress point, an anomaly could be triggered.
User Agent-based allow listing is supported for managed devices or applications. For example, if a user or enterprise using the browser then they can provide the allowed list browser, and the user activities from that browser are allowed.
This filter is on by default and cannot be turned off, but you can refine what is filtered by editing the allow list CSV file. The CSV file supports User-Agent Allow List. You can add the allow list browser list in the CSV file.
The CSV used by Allowed Networks and Locations can be updated at any time, but filtering is not retroactive on changes to this file.
To update the Allow List IP addresses:
- To get a list of the current IP addresses, click Download CSV.
- Make any edits and save the CSV. Make sure to use supported formats.
- Click Upload CSV and then provide the updated CSV file.
Blocked Networks and Locations
This filter uses a Skyhigh CASB-generated block list of threat feed information including possible threatening networks, network types, competitors, cities, and countries to make sure that anomalies are always triggered.
This filter is on by default and cannot be turned off, but you can refine what is filtered by editing the block list CSV file. The CSV file supports User Agent-based block listing. You can add the block-listed browser list in the CSV file.
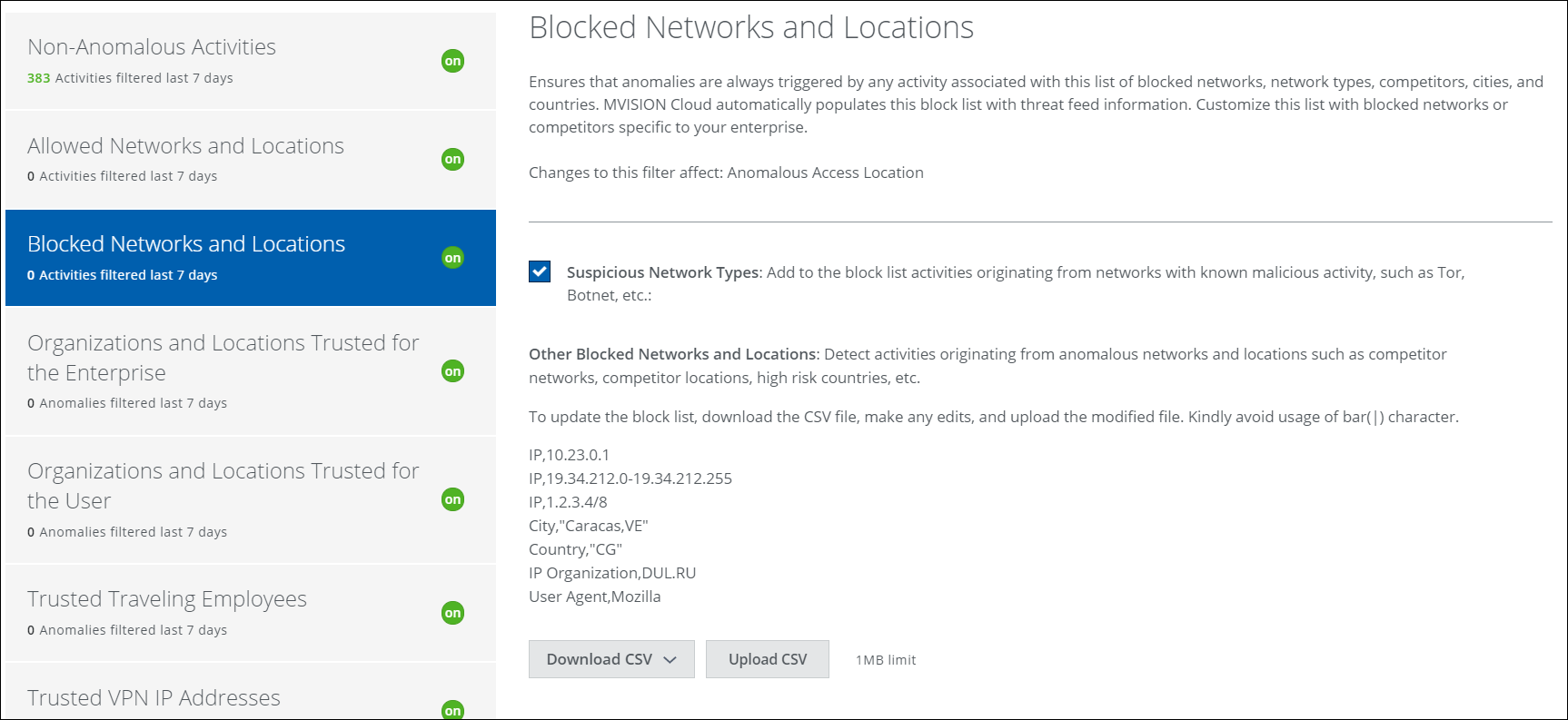
To update the block list:
- To get the current block list of network IP addresses and possible threatening locations, click Download CSV.
- Make any edits and save the CSV. Make sure to use supported formats.
- Click Upload CSV and then provide the updated CSV file.
Organizations and Locations Trusted for the Enterprise
This filter generates an allow list that represents the non-anomalous network activity level from remote offices. Org names and ISPs not identified with more activity than specified in the box (over the past 100 days) can trigger an anomaly. In other words, in our example below, if more than 5% of network traffic can be attributed to an ISP, then that traffic will be filtered.
IMPORTANT: In order to enable this filter, Allowed Networks and Locations must be enabled.
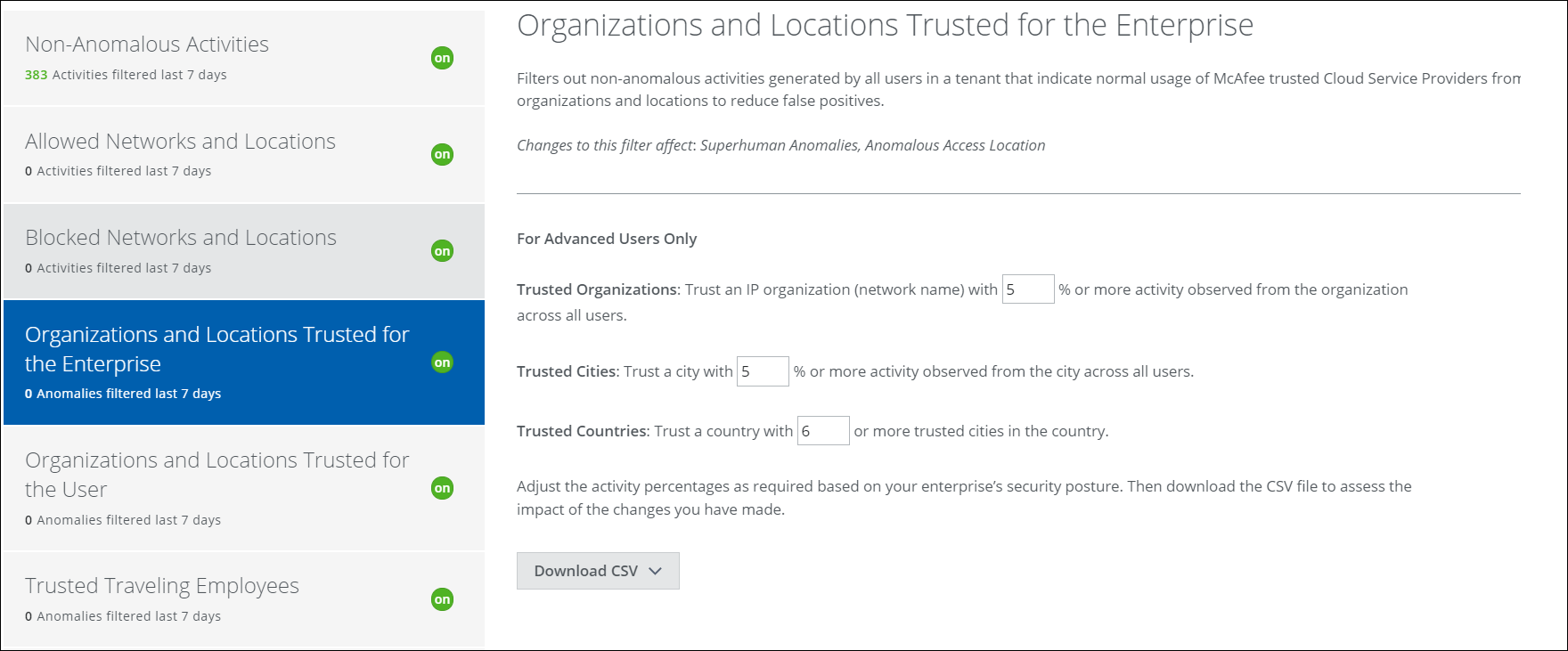
You can adjust the percentage of the total activity that is filtered for trusted organizations, cities, and countries. After each adjustment, download the CSV file to see exactly how the changes could affect filtering. A higher trust level means that more traffic must be attributed to an organization, city, or country before anomalies are triggered. A lower trust level means that less network traffic triggers fewer anomalies.
To adjust the trust level:
- Enter a new percentage or number in the text box.
- Download the CSV to check to see which ISPs are affected by the adjustment. Repeat if necessary.
Organizations and Locations Trusted for the User
Network traffic from satellite or home offices can create a lot of noise. If you have a widely distributed workforce, this filter can help tune out the non-anomalous activity that originates from offices you trust. Trust is measured by the percentage of network traffic from trusted organizations, cities, and countries.
IMPORTANT: In order to enable this filter, Allowed Networks and Locations and Organizations and Locations Trusted for the Enterprise must be enabled.
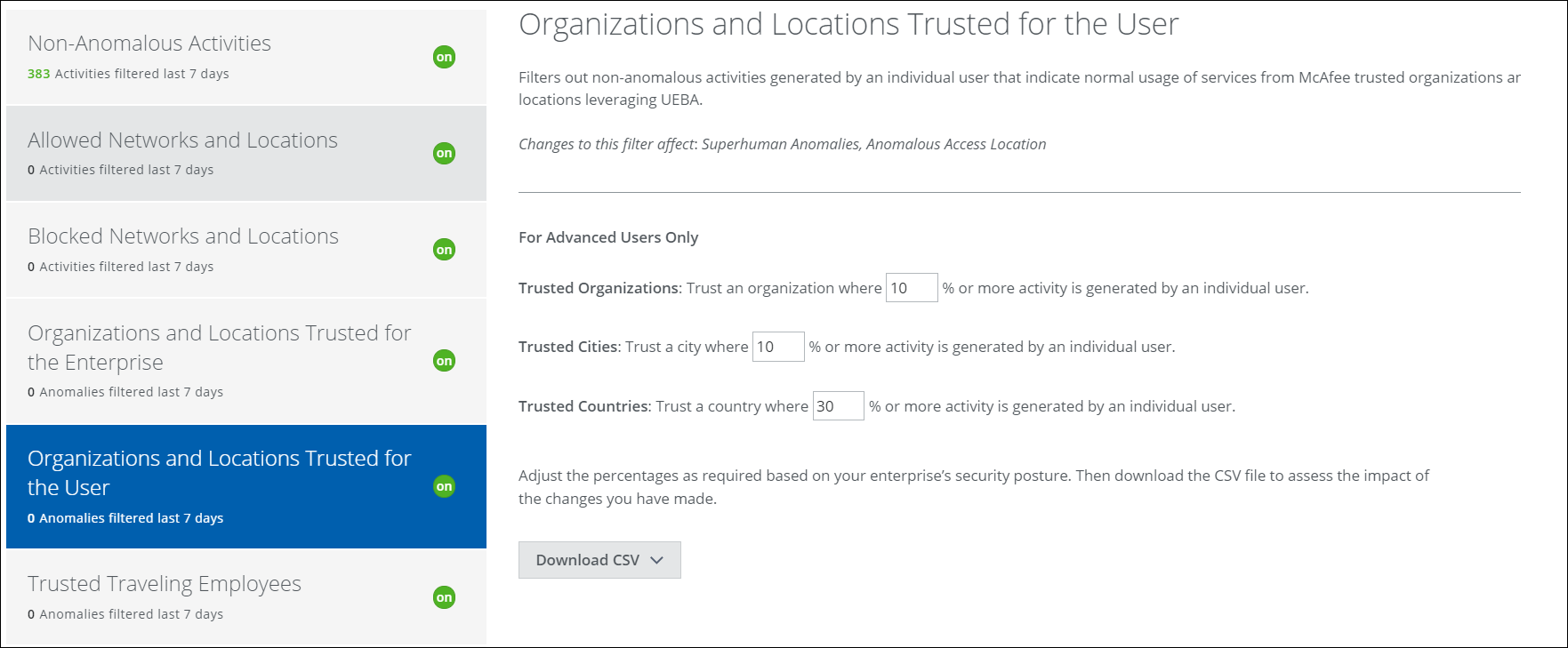
You can adjust the percentage of the total activity that is filtered. After each adjustment, download the CSV file to see exactly how the changes could affect filtering. A higher trust level means that more traffic must be attributed to an organization, city, or country before anomalies are triggered. A lower trust level means that less network traffic triggers fewer anomalies.
To adjust the trust level:
- Enter a new percentage in the text box.
- Download the CSV to check to see which ISPs are affected by the adjustment. Repeat if necessary.
Trusted Traveling Employees
This filter allows for the non-anomalous activity of regularly traveling employees to be filtered out, leveraging User and Entity Behavior Analytics (UEBA). The filter generates a CSV file of trusted traveling employees once a day. You can download the CSV file to view it.
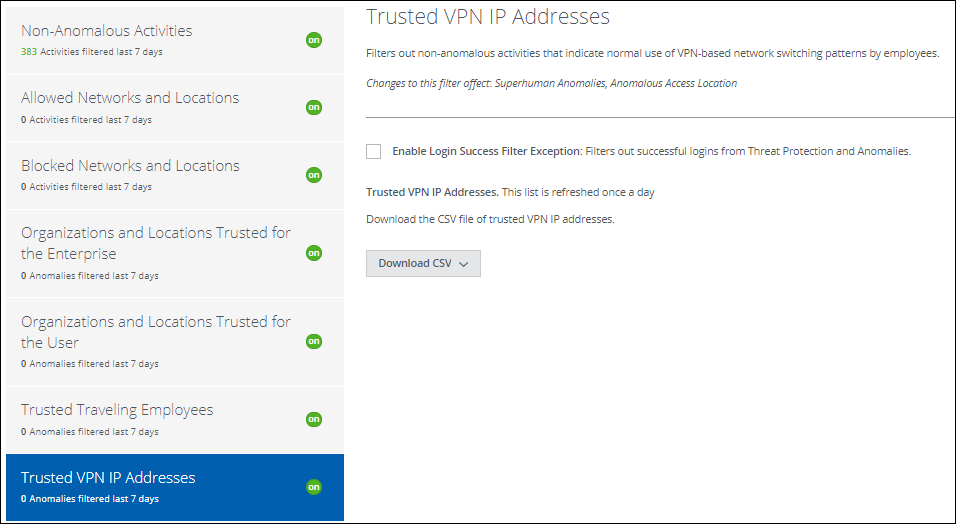
Trusted VPN IP Addresses
Trusted VPN IP Addresses filters normal user activity while a user is traveling and utilizing a CSP. You can refine the filter, and also download a CSV file of trusted VPN IP addresses.
IMPORTANT: In order to enable this filter, Allowed Networks, and Locations, Organizations and Locations Trusted for the Enterprise, and Organizations and Locations Trusted for the User must be enabled.