View Shadow IT Anomalies
Shadow IT Anomalies shows top-level information on the detected anomalies in your Shadow IT Services. To access this page, go to Incidents > Anomalies > Shadow Anomalies.
NOTE: If you have log tokenization enabled, you can search for users using real usernames by applying the search syntax real_username: salt. Here "salt" is the password string used while uploading the log files.
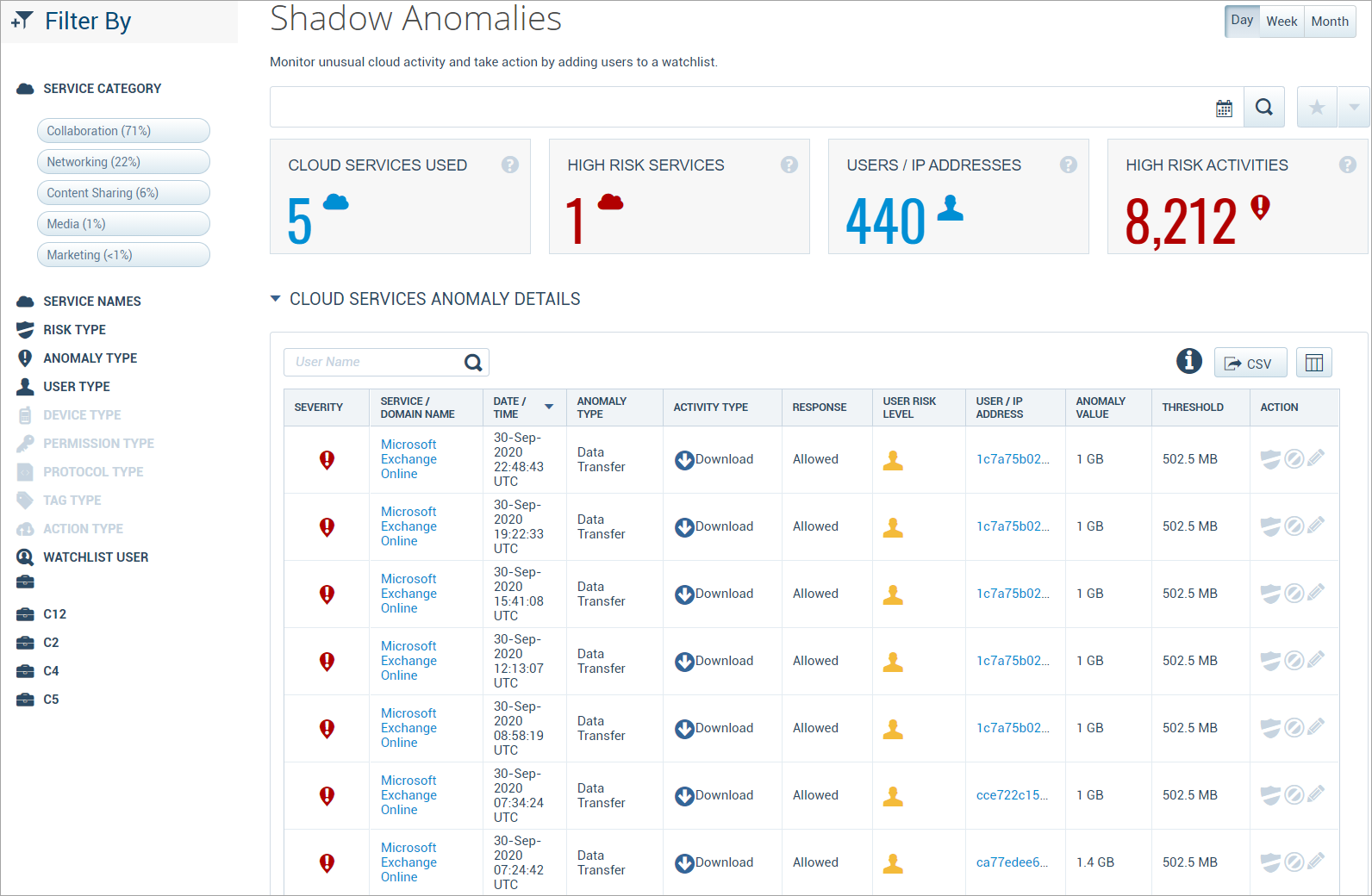
The Shadow Anomalies page provides the following information:
- Filters. Select options on the Filters tab to scope down your search.
- Search. Use the search bar to search for your service anomalies.
- Date Picker. Use the Date Picker to specify a date range to display data.
- Executive Summary
- Cloud Services Used. The total number of cloud services associated with detected anomalies.
- High Risk Services. The total number of cloud services with a risk score of seven or more that have anomalies.
- Users / IP Addresses. The total count of unique IP addresses or users detected creating anomalies. Due to IP address space allocation, this number may be bigger than the total number of users in your organization.
- High Risk Activities. The total number of detected anomalies.
Cloud Service Anomaly Details
The Cloud Service Anomaly Details section provides information on all the detected anomaly in your Shadow IT services.
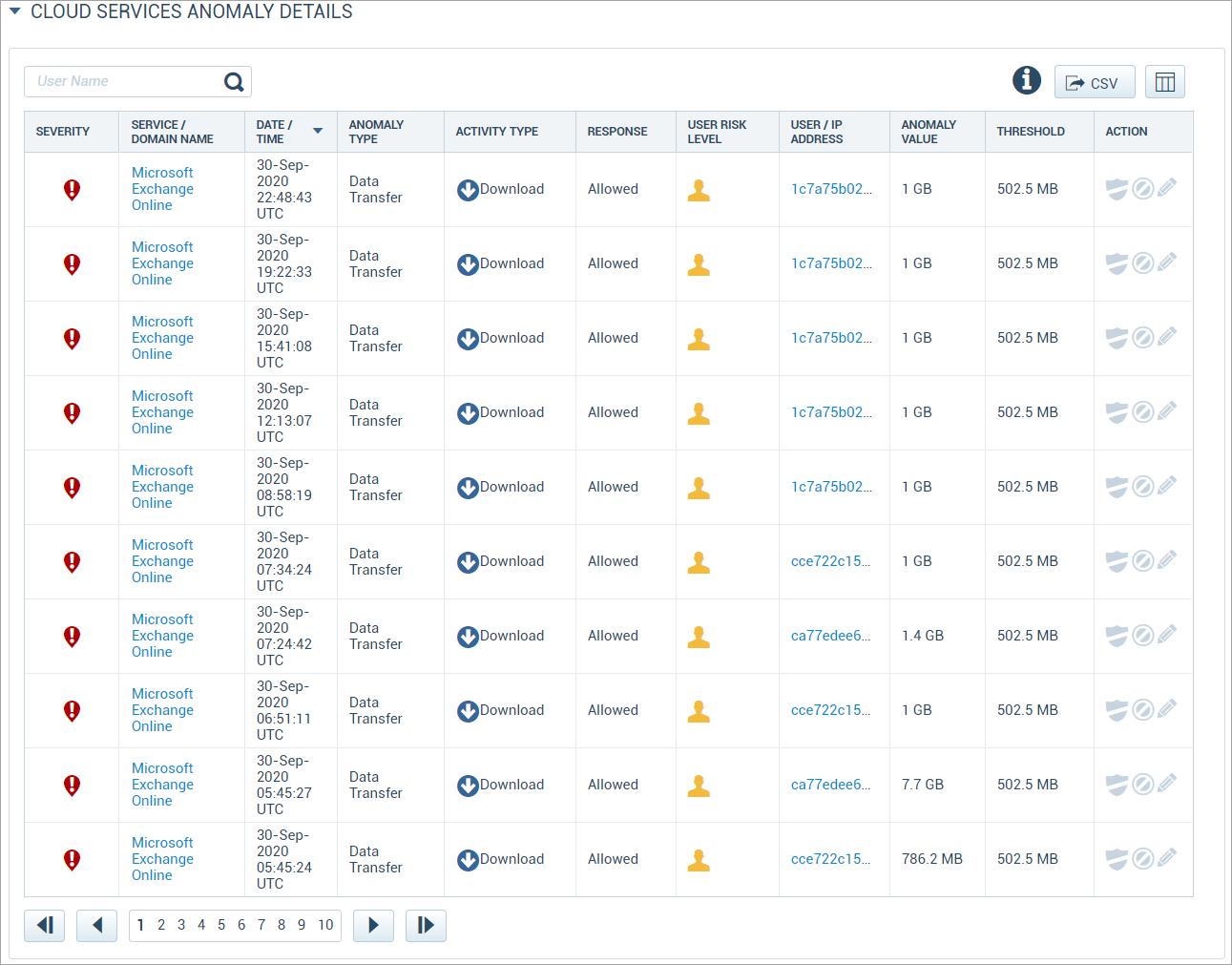
This table provides the following information and actions:
- Search. You can search for the specific User Name.
- CSV. Click the Export CSV icon to download a CSV file with the details of the table.
- Severity. The anomaly is ranked Low, Medium, or High Severity.
- Service/Domain Name. The Cloud Service where the anomaly occurred. Click any Service/Domain Name and you are redirected to the Active Services page. This page provides a report on review risk, service attributes, recent news, and terms and conditions for a specific service that is inactive in your organization. You can create a report in the PDF or Excel format and export the report through email.
- Date/Time. The time and date (based on your local time zone) when the anomaly occurred.
- Anomaly Type. The kind of anomaly that was triggered. See Anomaly Definitions below for a list of anomaly types.
- Activity Type. The event that occurred to trigger the anomaly. Activity types include:
- Discovered
- Download
- Upload
- Accessed
- Response. The Skyhigh CASB CASB response to the anomaly.
- User Risk Level. The risk score of the user, based on multiple data points representing user behavioral aspects such as usage patterns, the risk of services used, or total data movement.
- User/IP Address. The identity of the user who triggered the anomaly.
- Anomaly Value. The content of the anomaly, if it is a data-based anomaly.
- Threshold. The size of the anomaly.
- Action:
- Place /Remove User on/from Watchlist. Click the Shield icon to add the user to a watchlist.
- Valid. Click the Circle icon to mark the anomaly as valid.
- Set Threshold. Click the Pencil icon to set the threshold. For details, see Shadow IT Anomaly Threshold.