Microsoft Teams Secure Collaboration Use Cases
Supported Features
Skyhigh CASB for Microsoft Teams supports these features for the secured collaboration of users:
- Identify and remove sensitive content shared with unauthorized external/guest users.
- Monitor and remove guest users from unauthorized domains.
- Monitor and remove unauthorized guest users from internal-only conversations or private channels.
- Identify and remove sensitive content shared in specific teams/channels.
- Identify and remove sensitive content shared by internal users with guest users.
Identify and Remove Sensitive Content Shared With Unauthorized External/Guest Users
Skyhigh CASB for Microsoft Teams allows security admins to define the DLP policies to monitor and remove sensitive data posted in channels having unauthorized external/guest users as members. Messages or files posted in the regular channels and 1:1 or 1: many chat conversations are monitored and deleted.
Make sure to define the policy for the following service instances:
- Teams Instance. Monitors and deletes sensitive messages posted in regular channels or chat conversations.
- SharePoint Instance. Monitors and deletes sensitive files posted in regular channels.
- OneDrive Instance. Monitors and deletes sensitive files posted in 1:1 or 1:many chat conversations.
For example, say your organization has the domain myorg.com. Some of the teams in 'MyOrg' Office 365 tenant have guest users as members. So the organization wants to detect and remove any sensitive data such as credit card numbers posted in channels having guest user presence.
To identify and remove the sensitive content posted in channels having guest users, define the DLP policy for Microsoft Teams in the Skyhigh CASB as described.
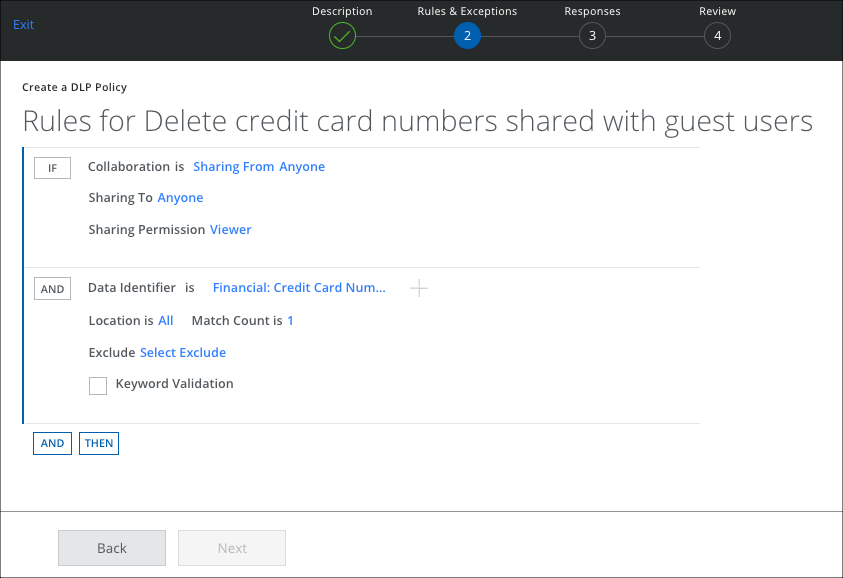
Rule Group
For the DLP Policy, create the Collaboration for Files and Folders associated with the Rule Group to identify the sensitive data.
To create a Collaboration for files and folders:
- Go to Policy > DLP Policies.
- Click Actions > Sanctioned Policy > Create New Policy.
- On the Description page, enter a name, description, and deployment type. For Services, select SharePoint. Then select the users the policy will apply to.
- On the Rules page, select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Anyone.
- For Sharing Permission, make a selection.
- Click AND and select any rule options such as Data Identifier, Keyword, or Regular Expression.
Exception Group
To add an exception to a policy:
- Click Add Exception.
- Select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Specific Users/Domains and Manually enter users/domains. Enter the domain names, for example, internal-domain1.com, internal-domain2.com, etc. In this case, the internal domain of the organization is myorg.com.
- For Sharing Permission, make a selection.
- Click Next.

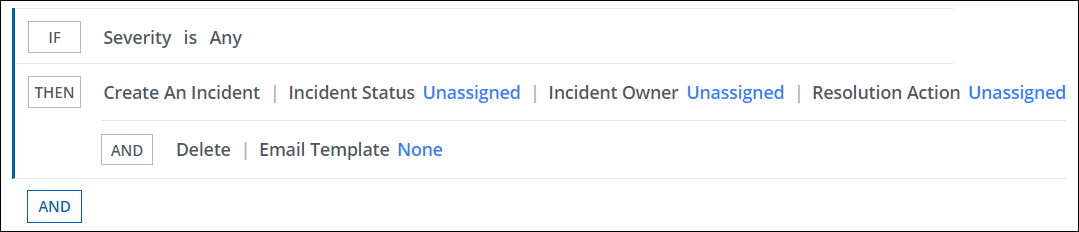
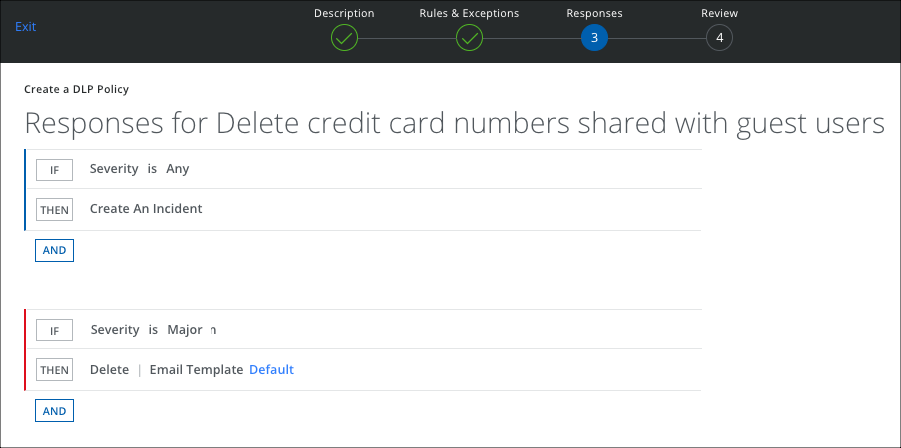
Response Action
To add a response action to a policy:
- On the Response page, click AND, and select Delete to remove the sensitive data.
- Select an Email Template.
- Click Next.
- Review your policy and click Save.
Monitor and Remove Guest Users from Unauthorized Domains
IMPORTANT: If you have been using the Teams API for Skyhigh CASB in your tenant, to leverage the feature Monitor and Remove Unauthorized Guest Users from Unauthorized Domains, as well as the Internal Teams Channels/Multi-Chat, you must re-enable API access.
Skyhigh CASB for Microsoft Teams allows security admins to define DLP policies to monitor and remove any unauthorized guest users joining teams.
For example, say you have an organization that wants to allow guest users from allowed domains allowed-domain1.com and allowed-domain2.com but wants to remove any guest users from other domains joining teams. This can be accomplished by defining DLP policies for Microsoft Teams in Skyhigh CASB as described below.
Rule Group
To create a Collaboration for Files and Folders:
- Go to Policy > DLP Policies.
- Click Actions > Sanctioned Policy > Create New Policy.
- On the Description page, enter a name, description, and deployment type. For Services, select SharePoint. Then select the users the policy will apply to.
- On the Rules page, select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Anyone.
- For Sharing Permission, make a selection.
- Click AND and select any rule options such as Data Identifier, Keyword, or Regular Expression.

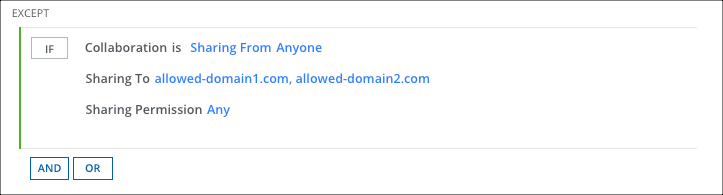
Exception Group
To add an exception to a policy:
- Click Add Exception.
- Select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Specific Users/Domains and Manually enter users/domains. Enter the domain names, for example, allowed-domain1.com, allowed-domain2.com, etc. If any guest user joins Teams from outside of the listed domains, then the policy is triggered.
- For Sharing Permission, make a selection.
- Click Next.
Response Action
To add a response action to a policy:
- On the Response page, click AND and select Revoke Sharing for and Everyone to remove the guest user.
- Select an Email Template.
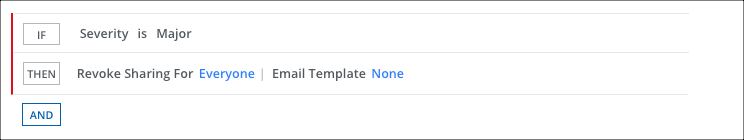
- Click Next.
- Review your policy and click Save.
Monitor and Remove Unauthorized Guest Users from the Internal Teams Channels/Multi-Chat
NOTE: If Microsoft Teams API access is already enabled in your tenant, you must re-enable API access to enable this use case. This is applicable for Multi-Chat also.
Skyhigh CASB for Microsoft Teams allows security admins to define the DLP policies to monitor and remove the unauthorized guest users joining internal-only teams (teams meant for internal conversations only).
To monitor and remove the unauthorized guest user from the internal-only teams, define the DLP policy for Microsoft Teams in the Skyhigh CASB as described.
Rule Group
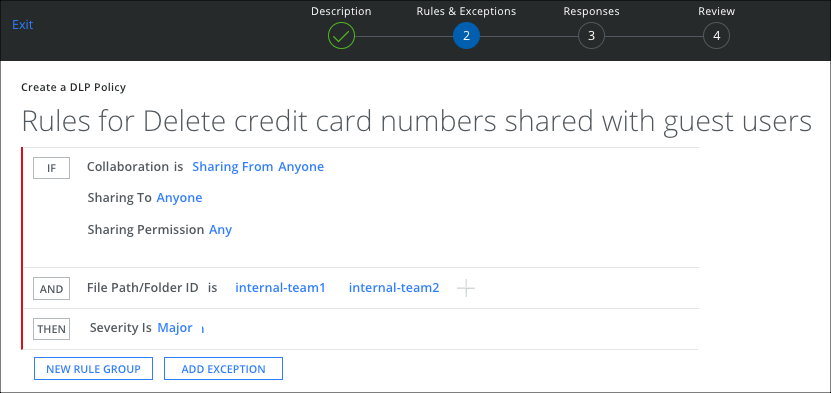
Create a Collaboration rule for Files and Folders.
- Go to Policy > DLP Policies.
- Click Actions > Sanctioned Policy > Create New Policy.
- On the Description page, enter a name, description, and deployment type. For Services, select SharePoint. Then select the users the policy will apply to.
- On the Rules page, select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Anyone.
- For Sharing Permission, make a selection.
- Click AND and select File Path/Folder ID, then Manually enter Select File Path/Folder ID and enter the list of internal team names.
- Click Done.
Exception Group
To add an exception to a policy:
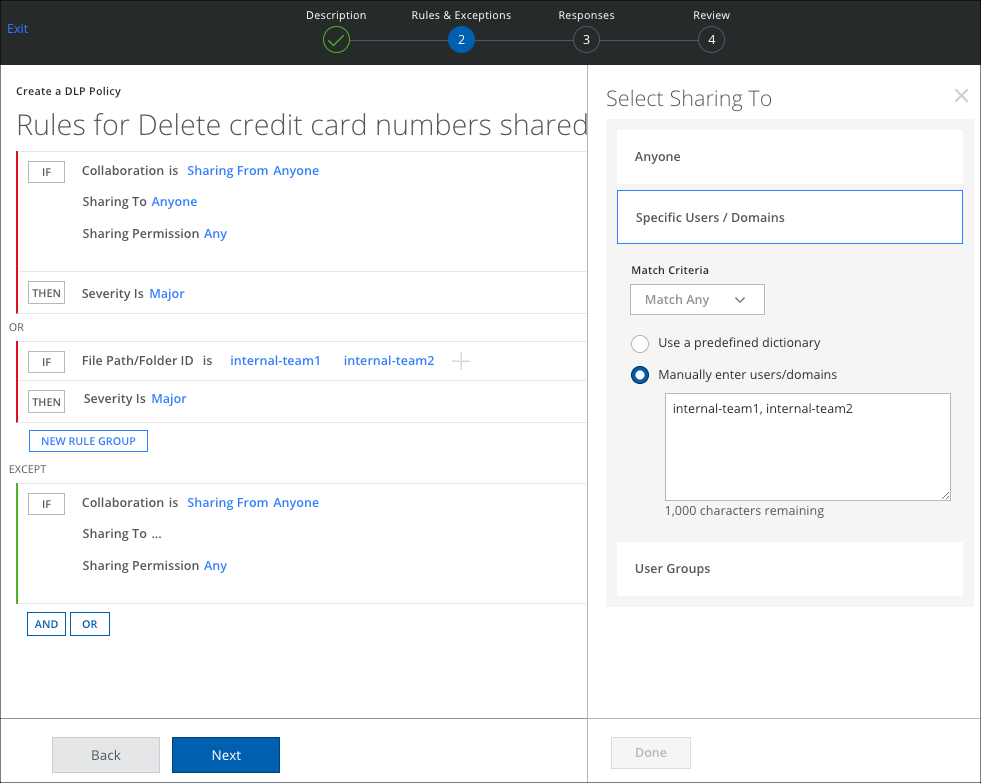
- Click Add Exception, select Collaboration.
- Select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Specific Users/Domains, and Manually enter users/domains.
- Enter the list of internal domains or list of allowed domains for To field. For example, allowed-domain1.com, allowed-domain2.com. If any guest user joins Teams from a domain outside of the listed domains, then the policy is triggered.
- Click Next.
Response Action
To add a response action to a policy:
- On the Response page, click AND and select Revoke Sharing for and Everyone to remove the guest user.
- Select an Email Template.
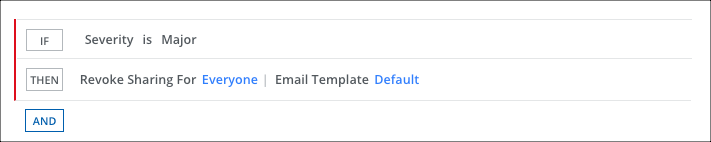
- Click Next.
- Review your policy and click Save.
Identify and Remove Sensitive Content Shared in Specific Teams / Channels
Microsoft Teams dedicate channels within a team to keep conversations organized by specific topics, projects, disciplines, etc. To create a channel , you must create a Team Name, then add the channels to it. Skyhigh CASB for Microsoft Teams allow security admins to define the DLP policies to monitor and remove the sensitive content shared in any specific teams /channels.
For example, say you are sharing the sensitive content such as credit card details in the teams name external.team1 and the associated channels with that team such as Channel 1 and Channel 2 also receives the same sensitive information. To remove the sensitive content from that specific teams/ channels, define the DLP policy for Microsoft Teams in the Skyhigh CASB as described.
Rule Group
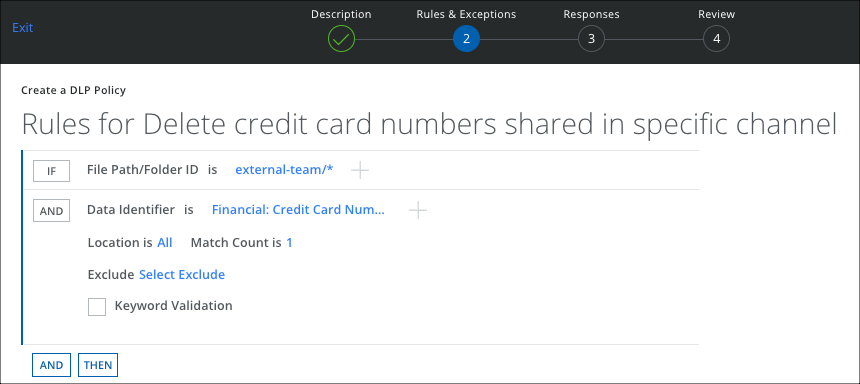
Create File Path/Folder ID collaboration rule.
- Go to Policy > DLP Policies.
- Click Actions > Sanctioned Policy > Create New Policy.
- On the Description page, enter a name, description, and deployment type. For Services, select SharePoint. Then select the users the policy will apply to.
- On the Rules page, select File Path/Folder ID, then Manually enter Select File Path/Folder ID and enter the team-name/* to monitor all channels in that team or provide the specific team-name/channel-name to monitor specific team/channel.
- Click Done.
- Click AND and select any options such as Data Identifier, Keyword, Regular Expression.
Response Action
To add a response action to a policy:
- On the Response page, click AND, and select Delete to remove the sensitive data.
- Select an Email Template.
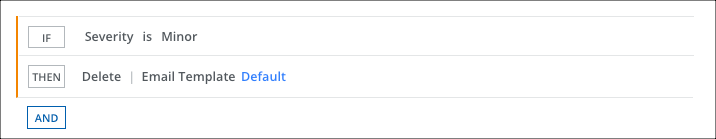
- Click Next.
- Review your policy and click Save.
Identify and Remove Sensitive Content Shared with Guest Users
Skyhigh CASB for Microsoft Teams allows security admins to define the DLP policies to monitor and remove sensitive data posted in meeting chats or group chats having guest users as members. Messages posted by internal users in meeting chats or group chats with a guest user present, are monitored and deleted.
For example, say your organization has the domain sedlp.onmicrosoft.com, and when internal users post sensitive data in a meeting chat or group chat while a guest user is present, the DLP policy should be triggered. This secure collaboration feature provides your organization with visibility into guest user details and allows it to detect and remove any sensitive data posted in meeting chats or group chats with guest user presence.
To identify and remove sensitive content posted by internal users in meeting chats or group chats with guest users, define the DLP policy for Microsoft Teams in Skyhigh CASB as described.
Rule Group
For the DLP Policy, create the Collaboration for Files and Folders associated with the Rule Group to identify the sensitive data.
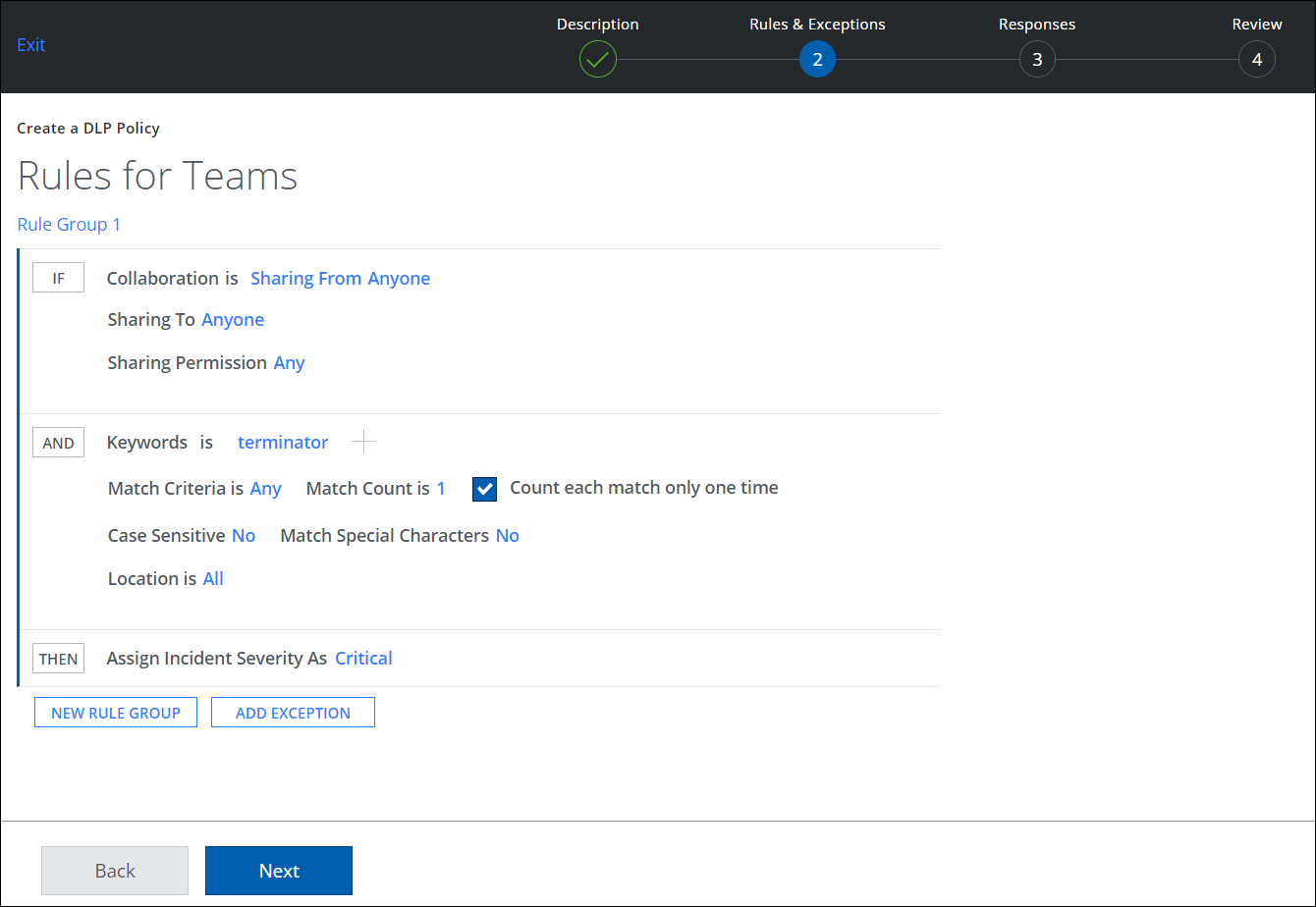
To create a collaboration rule for files and folders:
- Go to Policy > DLP Policies.
- Click Actions > Sanctioned Policy > Create New Policy.
- On the Description page, enter a name, description, and deployment type. For Services, select Microsoft Teams. Then select the users the policy will apply to.
- On the Rules page, select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Anyone.
- For Sharing Permission, make a selection.
- Click AND and select any rule options such as Data Identifier, Keyword, or Regular Expression.
Exception Group
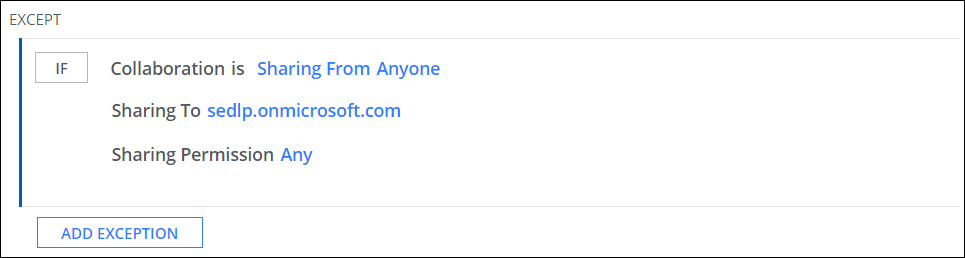
To add an exception to a policy:
- Click Add Exception.
- Select Collaboration.
- For Sharing From, select Anyone.
- For Sharing To, select Specific Users/Domains and Manually enter users/domains. Enter the domain names, for example, sedlp.onmicrosoft.com, allowed-domain1.com, etc. If a guest user joins the Teams meeting chat or group chat, the policy is triggered.
- For Sharing Permission, make a selection.
- Click Next.
Response Action
To add a response action to a policy:
- On the Responses page, click AND, and select Delete to remove the sensitive data.
- Select an Email Template.
- Click Next.
- Review your policy and click Save.