About Skyhigh Cloud Firewall
With the growing adoption of users accessing remotely business applications from various locations directly over the Cloud is increasing the risk to the corporate assets. The emergence of Cloud Firewall solution is intended to secure data and applications hosted on the Cloud. Skyhigh Cloud Firewall secures access to applications and resources on the internet, accessed from every remote site and location, through a cloud-native service model.
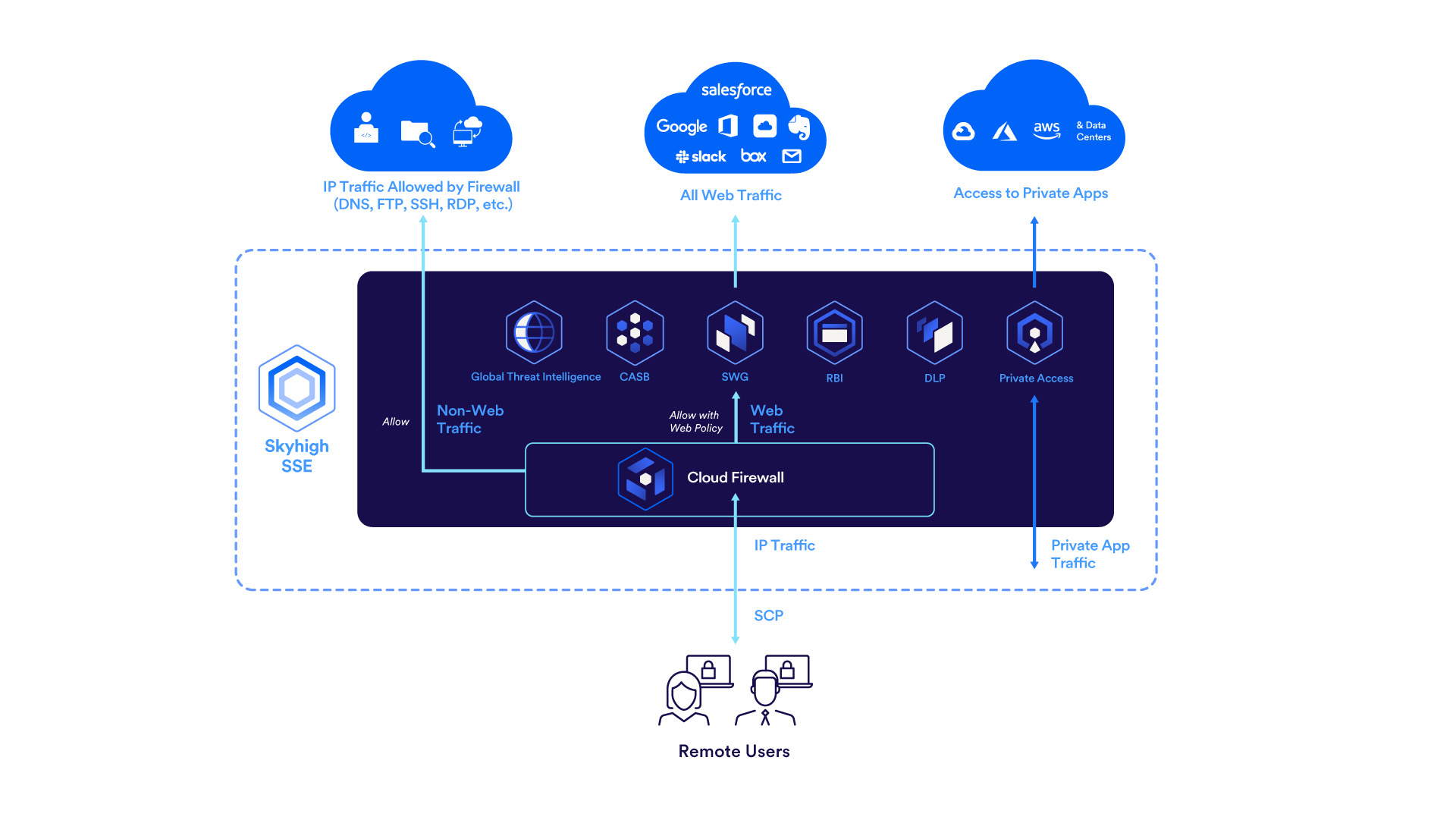
Skyhigh Cloud Firewall is a cloud-based firewall solution converged with Security Service Edge SSE to aggregate traffic from various sources that employ differing security postures. Skyhigh Cloud Firewall offers multi-layered protection and perform deep packet inspection, allowing organizations greater visibility, granular policy enforcement, and control over the applications to counter web-based threats.
With Skyhigh Cloud Firewall, you can monitor all outbound network traffic and prevent unauthorized access by enforcing firewall policies. Based on your organization’s information security policies, you can define a firewall policy to handle outbound network traffic for specific IP addresses, protocols, ports, and processes.
Key Features
- Protect cloud applications and networks from unauthorized and unwanted traffic.
- Advanced traffic management - Traffic splitting, traffic steering by intelligently forwarding certain traffic through Cloud Firewall and certain to the on-premise proxy.
- Enforce multiple firewall rules in a policy to filter and manage outbound traffic. For details about supported protocols, see Supported Protocols.
- Create firewall policies based on processes, ports, IP addresses, and domains.
- Create policies based on process names help to detect and control process based traffic. For example, Zoom or Teams traffic.
- Interoperability of Cloud Firewall with existing on-premise SWG for relaying outbound traffic in a corporate network when you don't have a direct internet access (no default route to redirect traffic and no external DNS).
- Visibility of your entire deployment coupled with analytics and reports that are actionable.
- Visibility and control aggregated data from Layer 7 to Layer 4 using the Cloud Firewall Dashboard. For example, you can monitor traffic from specific protocols, traffic flow from a source to a destination host, along with the application level traffic.
Getting Started
- Set up Client Proxy to redirect traffic to Cloud Firewall. For more information, see Set up Client Proxy.
- Complete the Cloud Firewall Settings.
- Configure firewall policy - Enforce the firewall policy rules to control, manage, and protect your entire network's outbound traffic. Based on several criteria, you can enforce policies to control the traffic (allowed/blocked/dropped/sent to Web Policy). For more information, see Configure Firewall Policies.
- Monitor your network traffic and prevent unauthorized traffic using Cloud Firewall Dashboard. This dashboard provides insights into the firewall traffic and the trend of allowed and blocked firewall events over the last seven days.
- Analyze firewall traffic and users using Cloud Firewall Analytics - Cloud Firewall Traffic, Cloud Firewall Users and Cloud Firewall Detailed Log reports.

