Firewall Exception List
You can allow web traffic that matches the items on the exception list to bypass the Cloud Firewall or send traffic through the Cloud Firewall. You can configure domains, IP addresses, ports, and processes in the exception list.
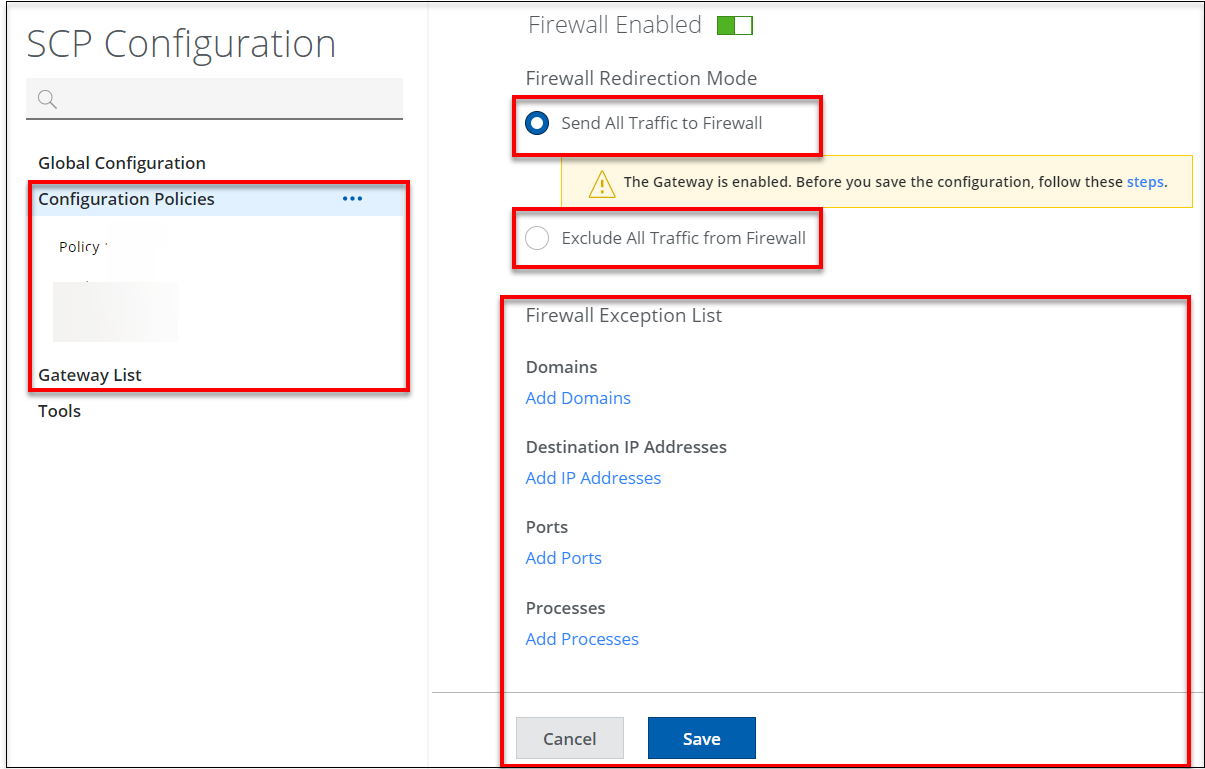
Configure items to bypass Cloud Firewall - Send all traffic to Firewall mode
- In the Firewall Exception List section, complete the following:
- Domains — Click Add Domains to open Exclude Traffic to Domains.
- From the Add Domain drop-down list, select Add Inline.
- Domain — Enter the domain names. The traffic to these domains bypasses Cloud Firewall. For example, Google.com.
- Comment — Enter additional information.
- + — Click this to configure another domain.
Note: You can use the Import CSV option to import the domain name list.
- From the Add Domain drop-down list, select Add Inline.
- IP Addresses — Click Add IP Addresses to open Exclude Traffic to IP Addresses.
- From the Add IP Address drop-down list, select Add Inline.
- IP Address — Enter the IP address names. The traffic sent to these IP addresses bypasses Cloud Firewall. Addresses can be configured individually, as a range, or using a subnet. For examples, 192.168.1.1, 172.31.255.10–172.31.255.20, 10.50.0.0/255.255.128.0, 10.50.0.0/17
- Comment — Enter additional information.
- + — Click this to configure another IP address.
Note: You can use the Import CSV option to import the domain name list.
- From the Add IP Address drop-down list, select Add Inline.
- Port — Click Add Ports to open Exclude Traffic to Ports.
- From the Add Port drop-down list, select Add Inline.
- Port — Enter the ports. The traffic sent to these ports bypasses Cloud Firewall.
- Protocol — Select the protocol supported by the specified port number.
- Comment — Enter additional information.
- + — Click this to add more ports.
Note: You can use the Import CSV option to import the port number list.
- From the Add Port drop-down list, select Add Inline.
- Process — Click Add Process to open Exclude Traffic from Processes.
- From the Add Process drop-down list, select Add Inline.
- Process — Enter the process names. The traffic from these processes bypasses Cloud Firewall. Enter the process that runs on the endpoints. Windows process names must end with .exe. For example, Chrome.exe, zoom.exe. teams.exe, msedge.exe. Make sure to add
svchost.exeto manage all inbound connections when sending all traffic to firewall.
Note: Entering the process name is mandatory, and the list is valid even if you do not provide any entries in other fields like Path, signer name, and descriptions.
- Path — Enter the file system path from where the process is executed. You can use wildcard while specifying path.
- Signer Name — Enter the application signer's name. You can check the Subject field of the certificate to enter the signer's name. For example, *O=signerName*CN=SignerName*
- Description — You can check the General tab of the application Properties to enter the description.
- + — Click this to configure another process.
Note: You can use the Import CSV option to import the process name list.
- Process — Enter the process names. The traffic from these processes bypasses Cloud Firewall. Enter the process that runs on the endpoints. Windows process names must end with .exe. For example, Chrome.exe, zoom.exe. teams.exe, msedge.exe. Make sure to add
- From the Add Process drop-down list, select Add Inline.
- Domains — Click Add Domains to open Exclude Traffic to Domains.
Configure items to send through Cloud Firewall - Exclude All Traffic from Firewall mode
- In the Firewall Exception List section, complete the following:
- Domains — Click Add Domains to open Send Traffic to Domains Through the Firewall.
- From the Add Domain drop-down list, select Add Inline.
- Domain — Enter the domain names. The traffic to these domains bypasses Cloud Firewall. For example, Google.com.
- Comment — Enter additional information.
- + — Click this to configure another domain.
Note: You can use the Import CSV option to import the domain name list.
- From the Add Domain drop-down list, select Add Inline.
- IP Addresses — Click Add IP Addresses to open Send Traffic to IP Addresses Through the Firewall.
- From the Add IP Address drop-down list, select Add Inline.
- IP Address — Enter the IP address names. The traffic sent to these IP addresses bypasses Cloud Firewall. Addresses can be configured individually, as a range, or using a subnet. For examples, 192.168.1.1, 172.31.255.10–172.31.255.20, 10.50.0.0/255.255.128.0, 10.50.0.0/17
- Comment — Enter additional information.
- + — Click this to configure another IP address.
Note: You can use the Import CSV option to import the IP addresses list.
- From the Add IP Address drop-down list, select Add Inline.
- Port — Click Add Ports to open Send Traffic to Ports Through the Firewall.
- From the Add Port drop-down list, select Add Inline.
- Port — Enter the ports. The traffic sent to these ports bypasses Cloud Firewall.
- Protocol — Select the protocol supported by the specified port number.
- Comment — Enter additional information.
- + — Click this to add more ports.
Note: You can use the Import CSV option to import the ports list.
- From the Add Port drop-down list, select Add Inline.
- Process — Click Add Process to open Send Traffic from Processes Through the Firewall.
- From the Add Process drop-down list, select Add Inline.
- Process — Enter the process names. The traffic from these processes bypasses Cloud Firewall. Enter the process that runs on the endpoints. Windows process names must end with .exe. For example, Chrome.exe, zoom.exe. teams.exe, msedge.exe
Note: Entering the process name is mandatory, and the list is valid even if you do not provide any entries in other fields like Path, signer name, and descriptions. - Path — Enter the file system path from where the process is executed. You can use wildcard while specifying path.
- Signer Name — Enter the application signer's name. You can check the Subject field of the certificate to enter the signer's name. For example, *O=signerName*CN=SignerName*
- Description — You can check the General tab of the application Properties to enter the description of a process.
- + — Click this to configure another process.
Note: You can use the Import CSV option to import the process name list.
- Process — Enter the process names. The traffic from these processes bypasses Cloud Firewall. Enter the process that runs on the endpoints. Windows process names must end with .exe. For example, Chrome.exe, zoom.exe. teams.exe, msedge.exe
- From the Add Process drop-down list, select Add Inline.
- Domains — Click Add Domains to open Send Traffic to Domains Through the Firewall.

