Create an In VPC Scan for AWS
To run a DLP scan in your Amazon Virtual Private Cloud environment (instead of running it in Skyhigh CASB), you can now use a deployed POP to expand DLP control to S3 buckets in their native VPC environment. Think of In VPC Scans as in-tenant inspections of data.
A POP must be properly configured before you can run an In-VPC scan. Also, an IAM role must have permissions to allow the scan to run.
In-VPC scans are supported for AWS, Azure, and Google Cloud Platform (GCP).
Prerequisites
To assign read-only permissions to an IAM role to allow DLP scanning:
An IAM role is created during the POP deployment. You will need to edit that existing role to add a permission that allows the POP to list or download files in an S3 bucket.
- In the AWS console, go to the CloudFormation tab. Find the template used previously to set up the POP.
- Click Outputs and copy the value of the cwppRole key.
- Go to the Identity and Access Management area of the AWS console. Select Roles and search for the role you copied.
- Click the role name to view all permissions assigned to this role. If Amazons3Readonlyaccess or Amazons3FullAccess are already assigned to role, you can skip the remaining steps in this section.
- Click Attach Policies and search for Amazons3Readonlyaccess.
- Select the checkbox next to Amazons3Readonlyaccess policy and click Attach policy.
To verify that assigned read-only access permission was added to the IAM role, switch back to the permissions tab for the role and look for Amazons3Readonlyaccess.
To update S3 bucket policy:
After assigning roles to access an S3 bucket, connect your S3 bucket to the VPC created during POP deployment. By default all micro-POP components are deployed within this VPC. To allow these components to access S3 buckets for scanning, the bucket policy needs to be updated. Repeat this process on each S3 bucket you want to include in DLP scans.
- In the AWS console,, go to the Cloud Formation tab and locate the cloud formation template used to set up the POP.
- Click Outputs and copy the value of the VPC key.
- Go to Services > S3.
- Select a bucket and switch to the permissions tab.
- Scroll to Bucket Policy.
- Click Edit to update the policy.
- Add VPC and IAM roles (IAM role can be found in CFT > Outputs) to allow access in the bucket policy. Choose one of the following options:
Option one:
"Statement": [{
"Sid": "Stmt1597678544375",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
],
"Condition": {
"StringNotEquals": {
"aws:SourceVpc": "<<vpc id>>"
},
"ArnNotEquals": {
"aws:PrincipalArn": [
"arn:aws:iam::<<account id>>:role/<<IAM role>>"
]
}
}
}]
Option two:
"Statement": [{
"Sid": "Stmt1597678544375",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
],
"Condition": {
"StringEquals": {
"aws:SourceVpc": "<<vpc id>>"
},
"ArnEquals": {
"aws:PrincipalArn": [
"arn:aws:iam::<<account id>>:role/<<IAM role>>"
]
}
}
}]
Creating a scan
To create an In VPC Scan:
- Go to Policy > On-Demand Scan.
- Click Actions > Create a Scan.
- The Scan Creation Wizard is displayed. On the General Info page enter the following:
- Scan Type. Select DLP & Malware. For In VPC scans, Malware is not supported.
- Name. Enter a unique identifier so that you can rerun the scan later.
- Description. Enter an optional description for the scan.
- Service Instance. Select the AWS S3, Azure, or GCP instance you want to scan.
- Where would you like to run this scan? Select In VPC.
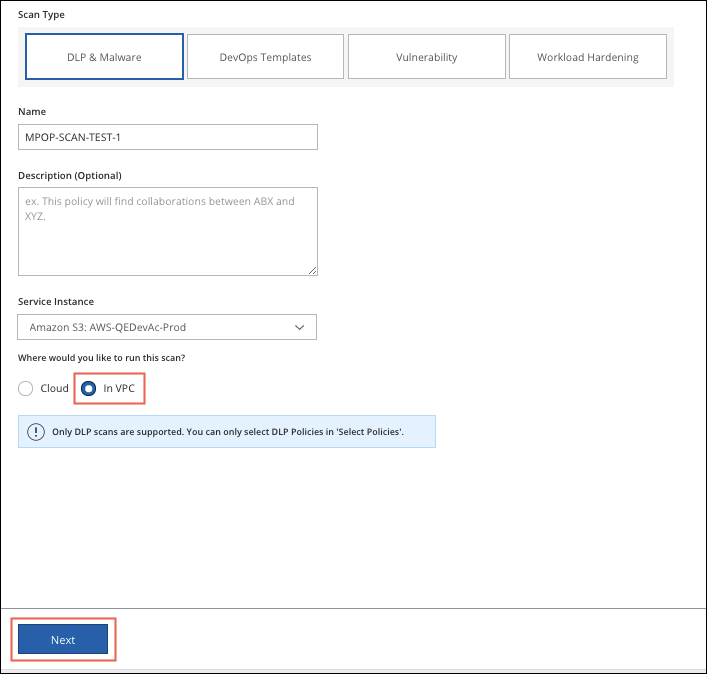
- Click Next.
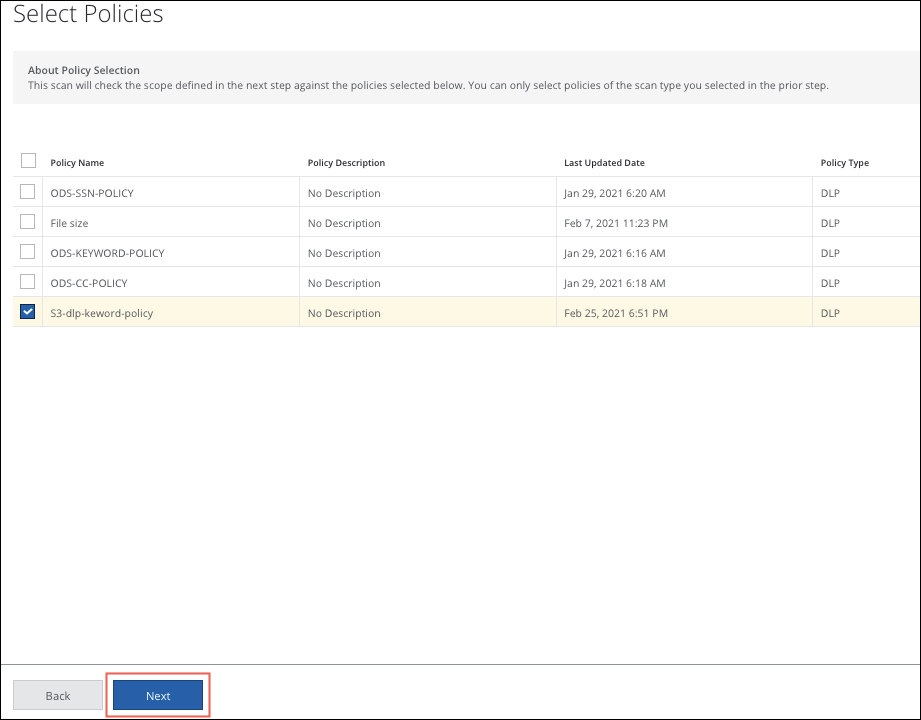
- The Select Policies page displays the active DLP policies supported for In VPC scans. Select the policies you want to use, and click Next.
- In the Configure Scan screen, set the following:
- Data Scope. Choose one of the following:
- Full. Scans all content every time the scan is run.
- Incremental. Scan only content that has changed since the last successful scan.
- Scan Dates. Select All, to scan all data. Or select Last X Days to limit the scan to the specified time period.
- Buckets:
- Exclude CloudTrail Bucket. The Exclude CloudTrail Bucket checkbox is activated by default. Deactivate the checkbox to include the CloudTrail bucket in a scan.
- Buckets to Scan:
- Use a Predefined Dictionary. Select a Predefined Dictionary from the menu. For more information, see this topic.
- Manually enter Buckets. Enter the buckets you want to scan in the box below.
- For Skyhigh CASB PoP, click Select PoP and then choose an available pre-configured option from the side panel and click Done.
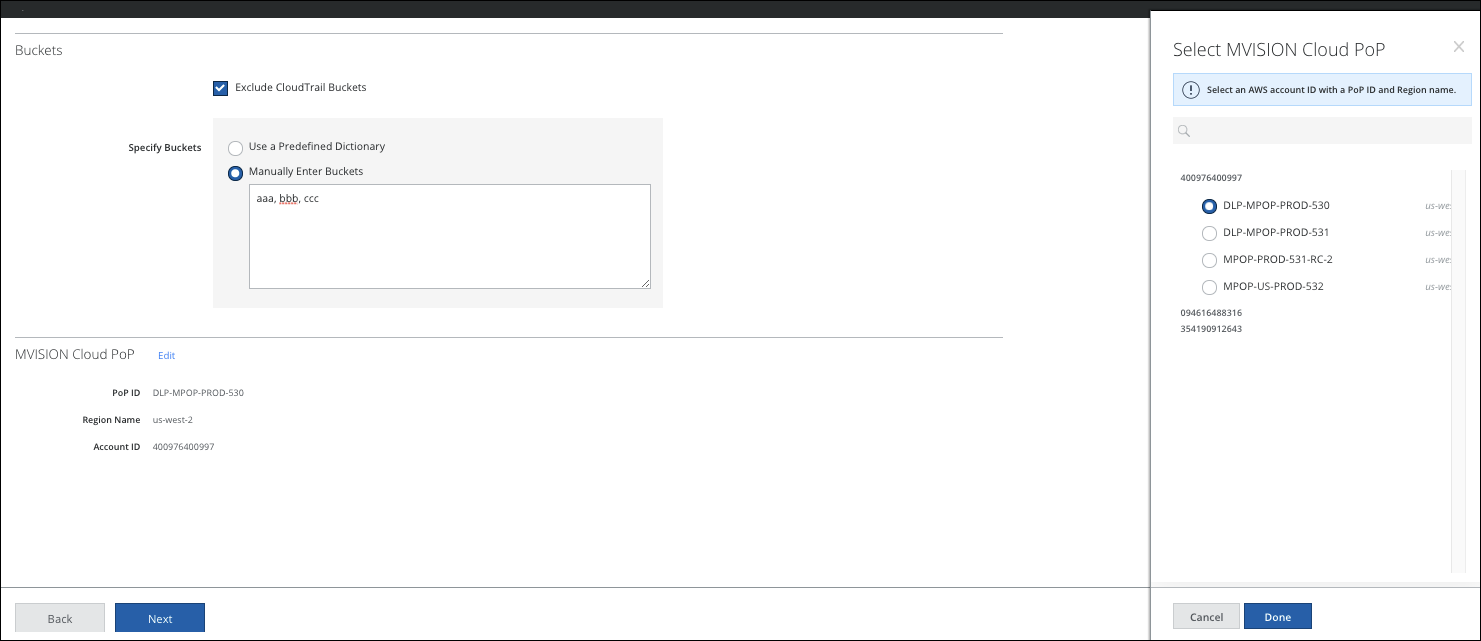
- Click Next.
- On the Schedule Scan page, select the schedule to run your scan and click Next:
- None (On-Demand Only). Run the scan once now.
- Daily. Run the scan once a day. Configure the time and time zone.
- Weekly. Run the scan once a week. Configure the day, time, and time zone.
- On the Review and Activate page, review your settings for the On-Demand Scan, and click Save. Click Back to make changes.

