Continuous Evaluation for Configuration Audit
- Last updated
-
-
Save as PDF
Skyhigh CASB provides Continuous Evaluation (CE) for IaaS services including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). It constantly monitors activities that lead to configuration changes for IaaS services and triggers Security Configuration Audit policies to report the violations. When CE is enabled, you will see Configuration Audit violations faster, as they are monitored continuously, instead of catching violations only once in 24 hours as reported by On-Demand Scans. CE is the default and recommended option.
For comparison:
Also note that:
- CE requires User Activity Monitoring to be enabled.
- When CE is enabled:
- On-Demand Scan frequency is disabled by default. In other words, the scans are created and present, but won't run once a day by default.
- On-Demand Scans are scheduled when accounts, subscriptions, or projects are added or removed to either baseline or update the status of existing incidents.
- When a new IaaS account is added enabling the account level feature flag allows On-Demand Scan to run for newly added IaaS accounts instead of all accounts. To set this feature flag, contact Skyhigh Security Support.
Enable Continuous Evaluation
- Go to Service Management, choose the IaaS CSP, and an instance.
- Under Setup, click Edit.
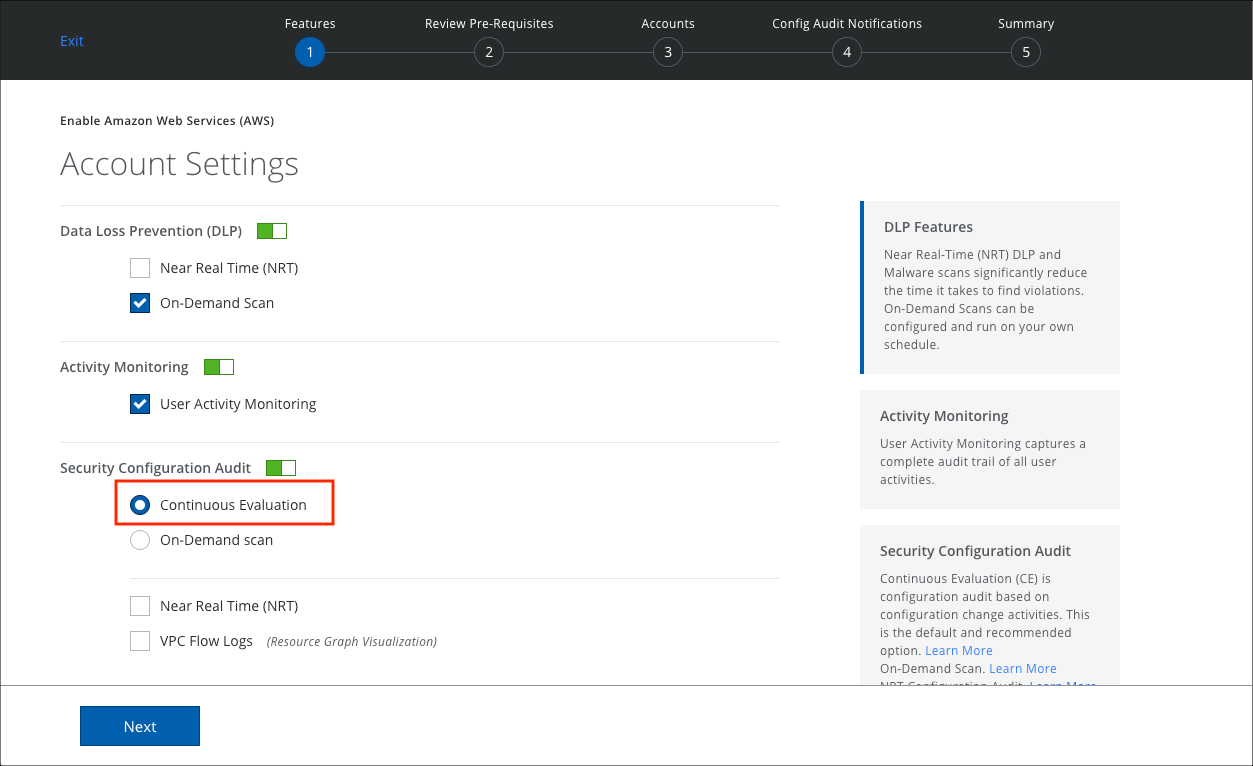
- Under Activity Monitoring, make sure User Activity Monitoring is enabled.
- Under Security Configuration Audit, Continuous Evaluation is the default selection.
- Click Next and finish configuring the instance as needed.
When Continuous Evaluation is Enabled
When CE is enabled:
- You will receive violations on the Incidents > Policy Incidents page more frequently and throughout the day, compared to before CE was enabled, when incidents were updated only once in 24 hours.
- If you have configured Email Notification for Incidents, you will receive those emails throughout the day, instead of once in 24 hours.
- Activities are populated much faster in the Incidents> User Activity > Activity Monitoring page.
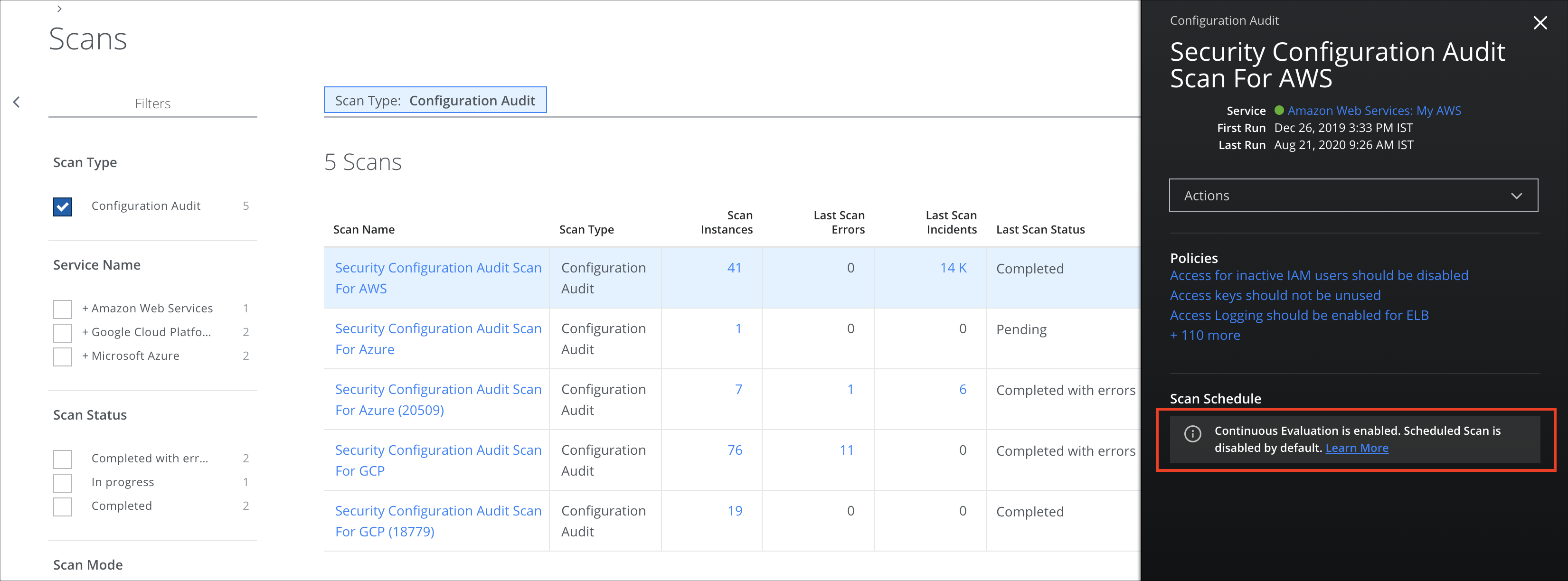
- On the Policy > On-Demand Scans page, scan instances are not updated. Also, fewer scan incidents are reported. So when you select the scan, in the Scan Details pane, you see the message, "Continuous Evaluation is enabled. Scheduled Scan is disabled by default." IaaS services in your environment are monitored continuously for any violations and they are reported by CE, so fewer incidents are reported by On-Demand Scans.
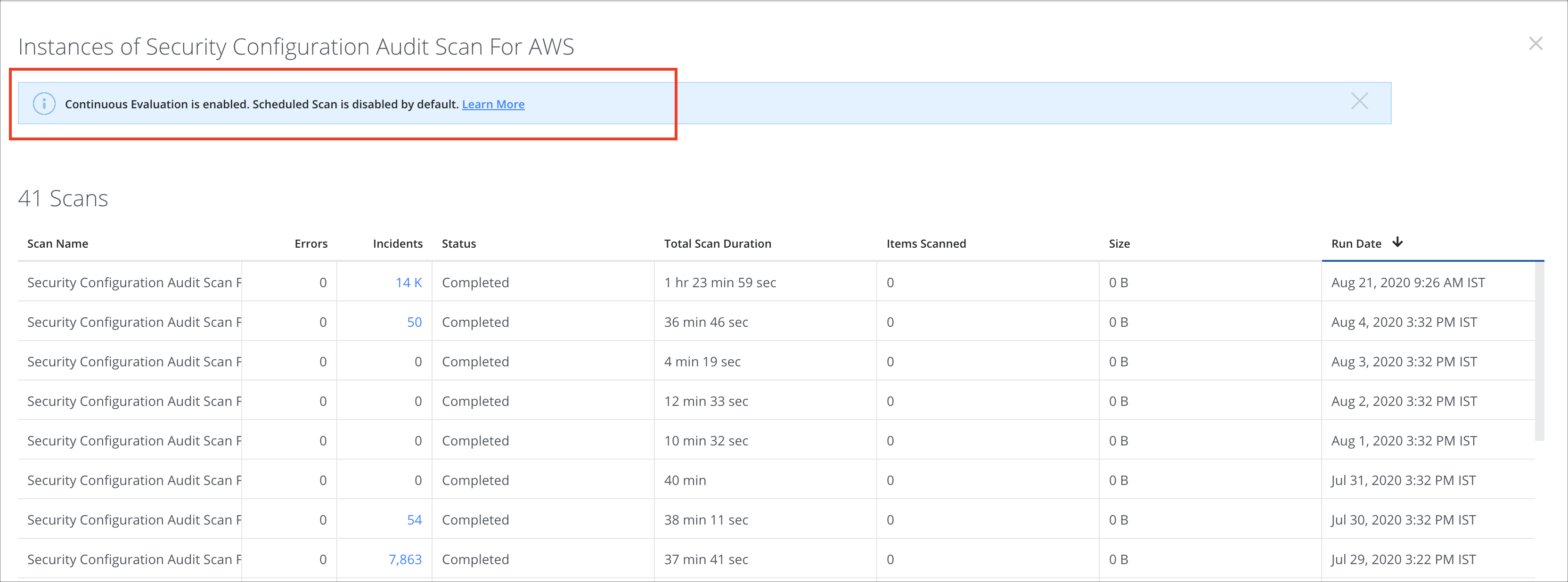
- Also, on the Scan Instances page, you see the message, "Continuous Evaluation is enabled. Scheduled Scan is disabled by default."
NOTES:
- Evaluation of the following policies depends on the data that is cached by AWS, so the incidents might not be updated as part of CE flow.
- Hardware MFA should be enabled for the root account
- MFA should be enabled for root account
- Root account access key should not exist
- Security Center, Security Center Recommendations policies, and Network Security Group policies are not supported via CE flow for Azure. The unsupported policies are listed below in the table.
|
Security Center Recommendations Policies
|
Security Center Policies
|
Network Security Group Polices
|
|
• A maximum of 3 owners should be designated for your subscription
• Adaptive Application controls should be enabled in Azure Security Center
• All resources should not be allowed to access your application
• An Azure Active Directory administrator should be provisioned for SQL servers
• Application protection should be finalized
• Auditing on SQL server should be enabled
• CORS should not allow every resource to access your Function App
• CORS should not allow every resource to access your Web App
• Custom domains should be used for Function App
• Custom domains should be used for Web application
• Deprecated accounts should be removed from the subscription
• Deprecated accounts with owner permissions should be removed from your subscription
• Diagnostic logs in Event Hub should be enabled
• Disk encryption should be applied on your Virtual Machines
• Endpoint protection health issues should be resolved on your machines
• External accounts with owner permissions should be removed from your subscription
• External accounts with read permissions should be removed from your subscription
• External accounts with write permissions should be removed from your subscription
• Function App should only be accessible over HTTPS
• IP restrictions for Function App should be configured
• IP restrictions for Web App should be configured
• Latest supported .NET framework version should be used for Web Application
• Latest supported Java version should be used for Web Application
• Latest supported Node.js version should be used for Web Application
• Latest supported PHP version should be used for Web Application
• Latest supported Python version should be used for Web Application
• MFA for accounts with owner permissions on the subscription should be enabled
• MFA for accounts with read permissions on the subscription should be enabled
• MFA for accounts with write permissions on the subscription should be enabled
• Monitoring agent health issues should be resolved on virtual machines
• Monitoring agent should be installed on virtual machine scale sets
• Network traffic should be routed through NGFW only
• OS version should be updated
• Remote debugging should be turned off for Function App
• Remote debugging should be turned off for Web Application
• There should be more than one owner assigned to your subscription
• Unrestricted network access should be disabled in storage account
• Virtual Machines should be rebooted after system updates
• Vulnerabilities in security configuration on the machines should be remediated
• Vulnerability assessment solution should be installed on your virtual machines
• Web app should redirect all HTTP traffic to HTTPS in Azure App Service
• Web Sockets should be disabled for function Application
• Web Sockets should be disabled for Web Application
|
- Enable Next Generation Firewall monitoring should be enabled in Azure Security Center
- Monitor Adaptive Application Whitelisting should be enabled in Azure Security Center
- Monitor Disk Encryption should be enabled in Azure Security Center
- Monitor Endpoint protection should be enabled in Azure Security Center
- Monitor JIT Network Access should be enabled in Azure Security Center
- Monitor maximum number of owners should be enabled in Security Center
- Monitor Network Security groups should be enabled in Azure Security Center
- Monitor OS vulnerabilities should be enabled in Azure Security Center
- Monitor SQL Auditing should be enabled in Azure Security Center
- Monitor SQL Encryption should be enabled in Azure Security Center
- Monitor SQL Vulnerability Assessment results should be enabled in Azure Security Center
- Monitor Storage Blob Encryption should be enabled in Azure Security Center
- Monitor system updated should be enabled in Security Center
- Monitor Web Application Firewall should be enabled in Azure Security Center
- Vulnerability Assessment should be enabled in Azure Security Center
- ASC Default policy setting "Monitor SQL Auditing" is not "Disabled"
- Built-in RBAC rules should be enabled in Security Center
- ClusterProtectionLevel property to EncryptAndSign in Service Fabric should be set
- CORS restrictions for API App should be enabled in Security Center
- CORS restrictions for API Function should be enabled in Security Center
- CORS restrictions for API Web should be enabled in Security Center
- Data collection should be enabled in Security Center
- DDoS Protection Standard should be enabled in Security Center
- Diagnostic logs in Azure Search service should be enabled in Security Center
- Diagnostic logs in Batch accounts should be enabled in Security Center
- Diagnostic logs in Data Lake Analytics accounts should be enabled in Security Center
- Diagnostic logs in Data Lake Store accounts should be enabled in Security Center
- Diagnostic logs in Event Hub accounts should be enabled in Security Center
- Diagnostic logs in Key Vault should be enabled in Security Center
- Diagnostic logs in Logic Apps should be enabled in Security Center
- Diagnostic logs in Service Analytics should be enabled in Security Center
- Diagnostic logs in Service Bus should be enabled in Security Center
- Diagnostic logs in Service Fabric should be enabled in Security Center
- Encryption should be enabled on Automation account variables in Security Center
- Metric alerts in Batch accounts should be enabled in Security Center
- MFA for accounts with read permissions should be enabled in Security Center
- MFA for accounts with write permissions should be enabled in Security Center
- MFA on accounts with owner permissions on the subscription should be enabled in Security Center
- Minimum number of owners should be enabled in Security Center
- Monitor access rules in Event Hubs should be enabled in Security Center
- Monitor Azure Active Directory Authentication in Service Fabric should be enabled in Security Center
- Monitor classic compute VMs should be enabled in Security CenterMonitor classic storage accounts should be enabled in Security Center
- Monitor diagnostic logs in Azure App Services should be enabled in Security Center
- Monitor diagnostic logs in Azure Redis Cache should be enabled in Security Center
- Provisioning of an Azure AD administrator for SQL server should be enabled in Security Center
- Remote debugging should be disabled for API App in Security Center
- Remote debugging should be disabled for Function App in Security Center
- Remote debugging should be disabled for Web App in Security Center
- Remove deprecated accounts should be enabled in Security Center
- Remove deprecated accounts with owner permissions should be enabled in Security Center
- Remove external accounts with owner permissions should be enabled in Security Center
- Remove external accounts with read permissions enabled in Security Center
- Remove external accounts with write permissions should be enabled in Security Center
- Secure transfer to storage accounts should be enabled
- Security Contact Emails' should be set in Security Center
- Security Contact Phone number should be set in Security Center
- Send email also to subscription owners' should be 'ON'
- Send email notification for high severity alerts' should be 'ON'
- Service Bus namespace authorization rules should be enabled in Security Center
- SQL Encryption recommendations should be enabled in Azure Security Center
- System Configurations should be enabled in Security Center
- Unrestricted network access to storage account should be disabled in Security Center
- Use latest Java version in Web App should be enabled in Security Center
- Use latest PHP version in Web App should be enabled in Security Center
- Use latest Python version in Web App should be enabled in Security Center
- Use of HTTPS in API App should be enabled in Security Center
- Use of HTTPS in function App should be enabled in Security Center
- Use of HTTPS in Web App should be enabled in Security Center
|
- NSG Flow logs should be enabled
|




