Integrate Shift Left Inline APIs with Bitbucket and AWS CI/CD Services
Integrate Shift Left Inline
Skyhigh CASB provides a security solution to evaluate the DevOps templates in both offline and inline mode. Using inline mode, you can integrate the repository and CI/CD tools with Shift Left inline APIs, and Skyhigh CASB evaluates the security vulnerabilities present in the DevOps template file.
Skyhigh CASB supports evaluating DevOps templates for AWS and Azure including Terraform support. You can also integrate Shift Left with Bitbucket's CI/CD tool and Bitbucket pipelines.
Integrate Atlassian Native CI/CD Tools
Prerequisites
Before integration, make sure you have met the following prerequisite:
- Create a Bitbucket repository using the link Create a repository in Bitbucket.
Configure Bitbucket Pipelines
Perform the following steps to set up Bitbucket pipelines integration with Shift Left inline APIs.
-
Create a file named bitbucket-pipelines.yml in the repo's root directory and add the following content.
-
To evaluate only the changed files use the following script:
-
# This is a sample build configuration for Docker.
# Check our guides at https://confluence.atlassian.com/x/O1toN for more examples.
# Only use spaces to indent your .yml configuration.
# -----
# You can specify a custom docker image from Docker Hub as your build environment.
image: atlassian/default-image:2
pipelines:
default:
- step:
name: "Shift Left Integration with Bitbucket"
script:
- git log HEAD -1 --name-only --pretty="format:" > changes.txt
- cat changes.txt | { egrep -i '.json|.tf|.yml|.yaml' || true; } > changes_latest.txt
- if test "$( wc -l < changes_latest.txt )" -gt 0; then
- data=$(cat changes_latest.txt | while read line; do echo $line; done)
- data=$(echo $data | tr ' ' ',')
- pipe: mcafeemvision/shift-left-atlassian-pipe:1.1.0
variables:
MVISION_USERNAME: $MVISION_USERNAME
MVISION_PASSWORD: $MVISION_PASSWORD
MVISION_ENVIRONMENT: $MVISION_ENVIRONMENT
CLOUD_SERVICE_PROVIDER: $CLOUD_SERVICE_PROVIDER
FILES: $data
WORKSPACE: $BITBUCKET_WORKSPACE
SLUG: $BITBUCKET_REPO_SLUG
COMMIT_ID: $BITBUCKET_COMMIT
- fi
- To evaluate all files every time a build is triggered, use this script:
# This is a sample build configuration for Docker.
# Check our guides at https://confluence.atlassian.com/x/O1toN for more examples.
# Only use spaces to indent your .yml configuration.
# -----
# You can specify a custom docker image from Docker Hub as your build environment.
image: atlassian/default-image:2
pipelines:
default:
- step:
name: "Shift Left Integration with Bitbucket"
script:
- find ./ -type f \( -iname \*.yaml -o -iname \*.yml -o -iname \*.tf -o -iname \*.json\) > changes.txt
- if test "$( wc -l < changes.txt )" -gt 0; then
- data=$(cat changes.txt | while read line; do echo $line; done)
- data=$(echo $data | tr ' ' ',')
- pipe: mcafeemvision/shift-left-atlassian-pipe:1.1.0
variables:
MVISION_USERNAME: $MVISION_USERNAME
MVISION_PASSWORD: $MVISION_PASSWORD
MVISION_ENVIRONMENT: $MVISION_ENVIRONMENT
CLOUD_SERVICE_PROVIDER: $CLOUD_SERVICE_PROVIDER
FILES: $data
WORKSPACE: $BITBUCKET_WORKSPACE
SLUG: $BITBUCKET_REPO_SLUG
COMMIT_ID: $BITBUCKET_COMMIT
- fi
- Commit and push the bitbucket-pipelines.yml file.
- Go to Settings > Repository variables. You are redirected to the Repository variables page.
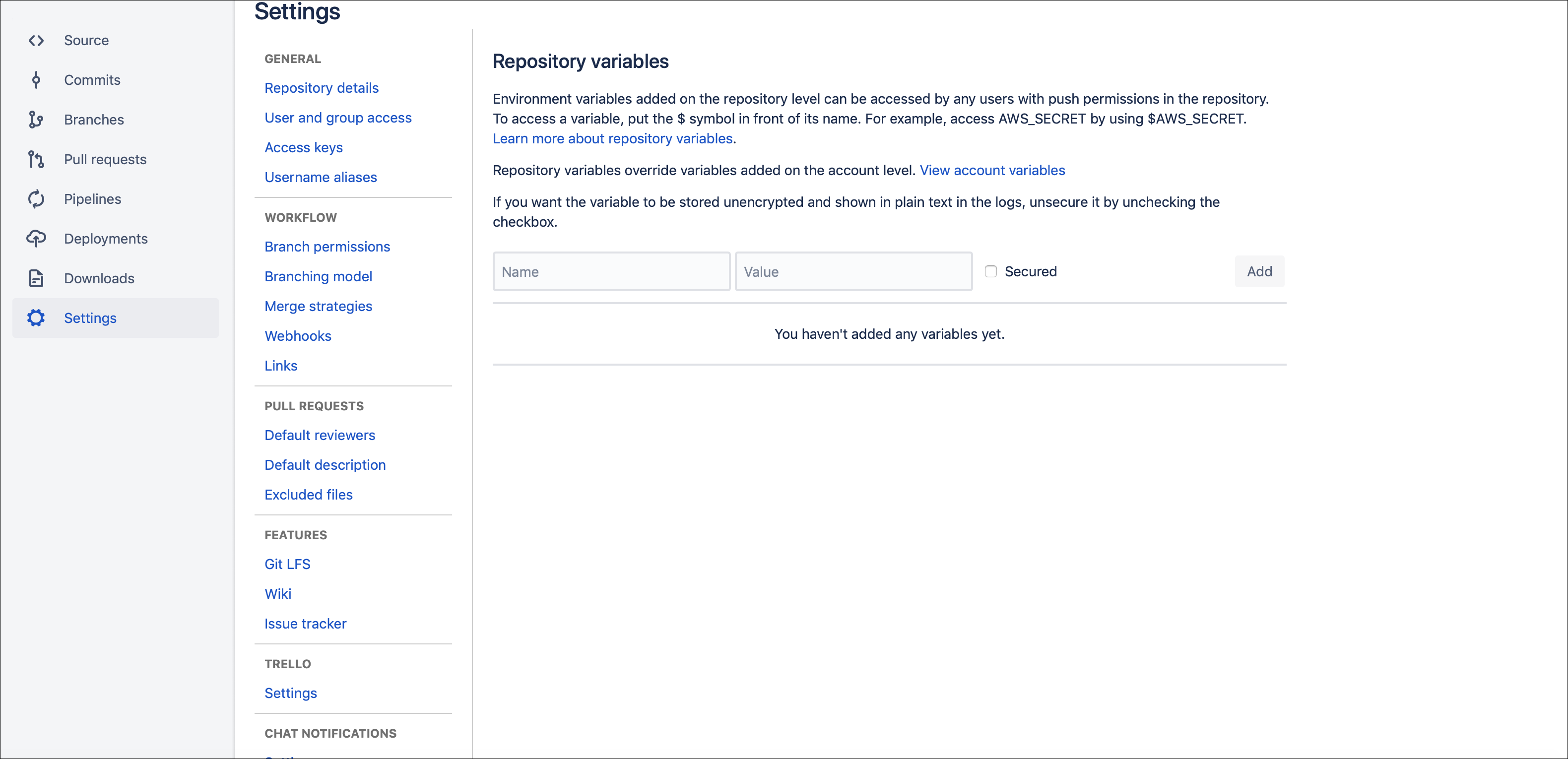
- Add the following variables and values in the repository variable page:
- Add Name as CLOUD_SERVICE_PROVIDER and Value as aws (to evaluate AWS DevOps templates) or azure (to evaluate Azure resource manager templates).
- Add Name as MVISION_USERNAME and Value as the username of Skyhigh CASB and select the secured checkbox.
- Add Name as MVISION_PASSWORD and Value as the password of Skyhigh CASB and select the secured checkbox.
- Add Name as MVISION_ENVIRONMENT and Value as the environment URL (https://www.myshn.net) of Skyhigh CASB.
- Enable pipelines.
The Bitbucket pipeline integration with Skyhigh CASB Shift Left inline API is complete.
Any push to the Bitbucket repo triggers a build in pipelines, which calls the Shift Left inline APIs to check for vulnerabilities present in the DevOps template committed in Bitbucket.
Integrate Shift Left Inline with AWS CodeCommit and CodeBuild
Perform the following steps to integrate AWS CI/CD tools with Shift left inline:
- Go to AWS CloudFormation page and select Create stack > With new resources (standard).
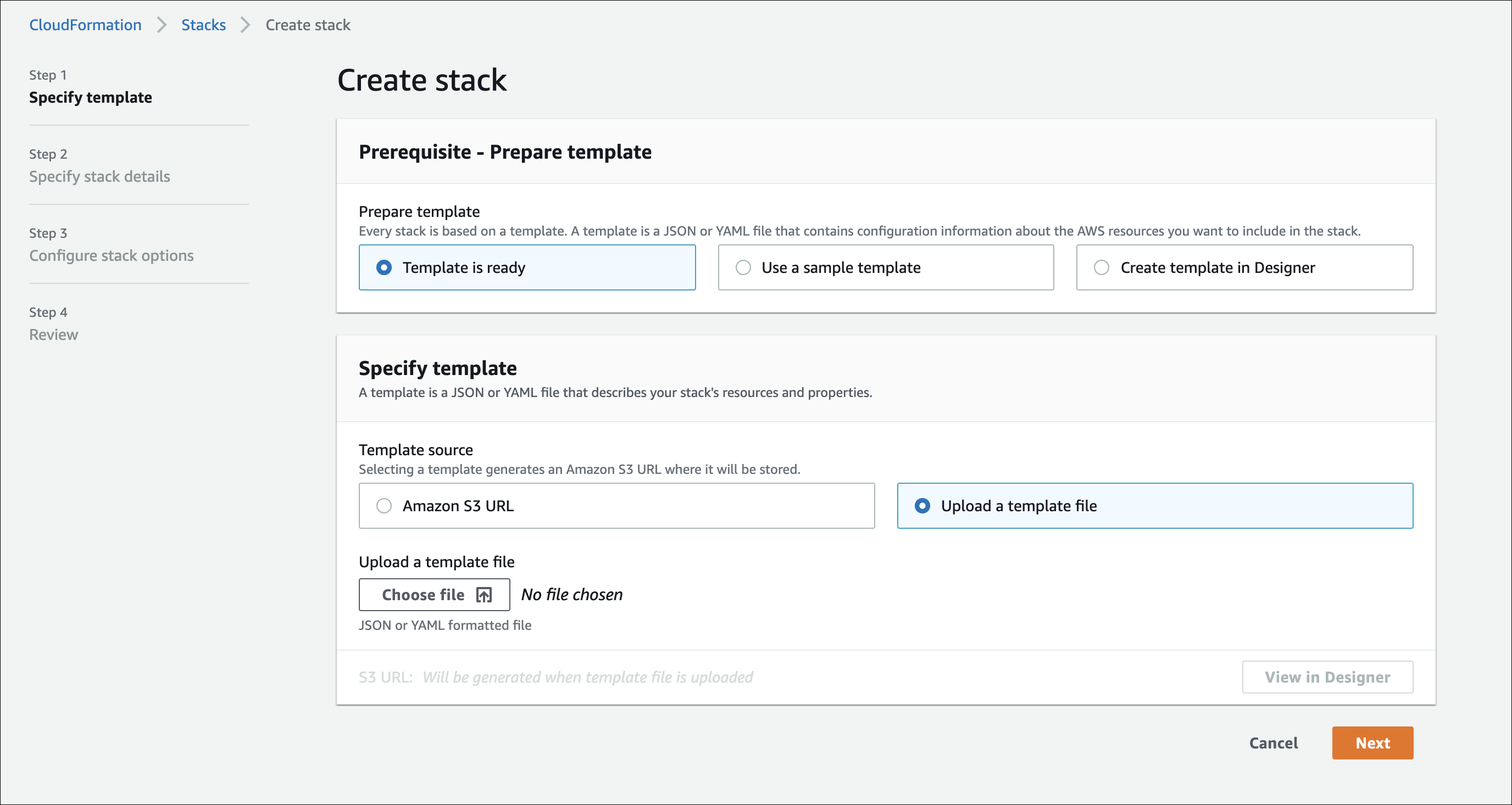
NOTE: You can skip steps 1–6 if you already have an AWS setup.
- Upload the shift-left-aws-mvision.yaml cloud formation and click Next.
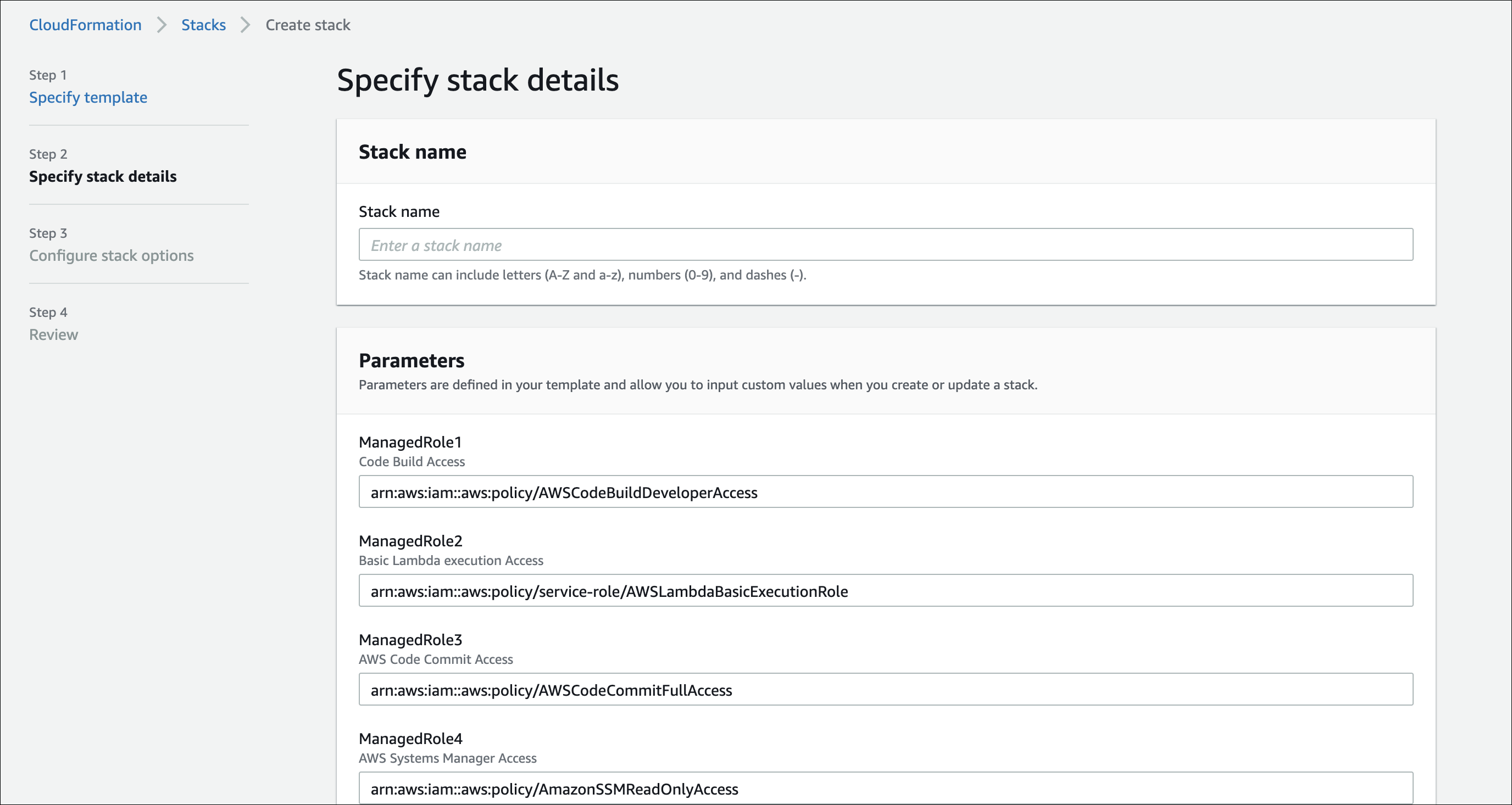
- Enter the stack name and click Next.
The Configure stack options page opens. - Click Next.
- In the review page, select the checkbox I acknowledge that AWS CloudFormation might create IAM resources with custom names and click Create Stack.
- Make sure the stack creation is complete with status CREATE_COMPLETE.
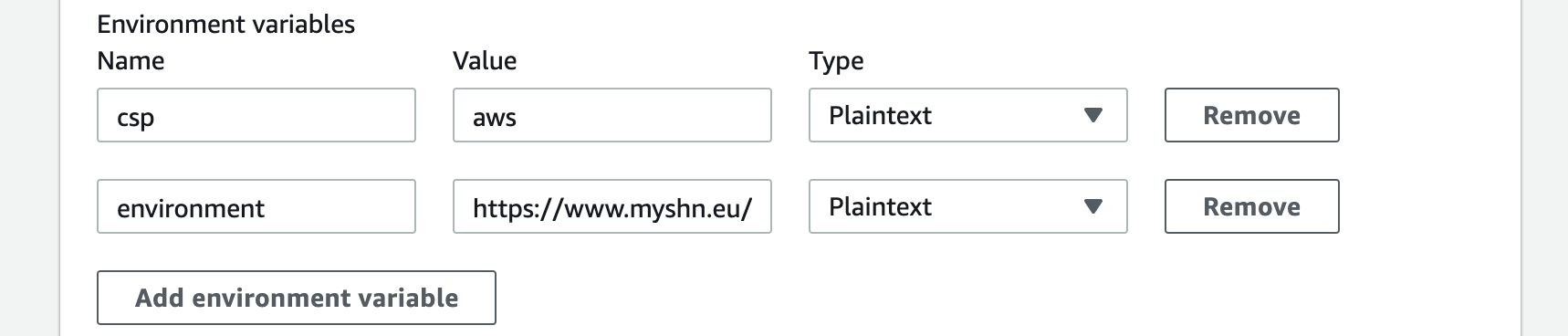
- Navigate to the CodeBuild, select build-shift-left-integration. Click Edit and select the Environment. In the Edit Environment page, select Additional Configuration and add environment as shown below.
- For tenants in US Prod, provide the environment value as https://www.myshn.net/
- For tenants in EU, provide the environment value as https://www.myshn.eu/
- For tenants in Canada, provide the environment value as https://www.myshn.ca/
- Download the buildspec.yml.
- Go to the AWS CodeCommit page, and select the repo shift-left-repo. Under the repo, select Add file > Upload file and upload the file downloaded in
Step 7. Provide Author Name, Email address, and click Commit changes. - Once the file is committed, go to the AWS Systems Manager. Select the Parameter Store from the left menu.
- Click Create parameter and you are navigated to the Parameter details page.
- Populate the following values and make sure the parameters are created in the same region as the repository and code build.
- Name with /codebuild/mvision_username and enter the Skyhigh CASB username and click Create Parameter.
- Name with /codebuild/mvision_password and enter the Skyhigh CASB password and click Create Parameter.
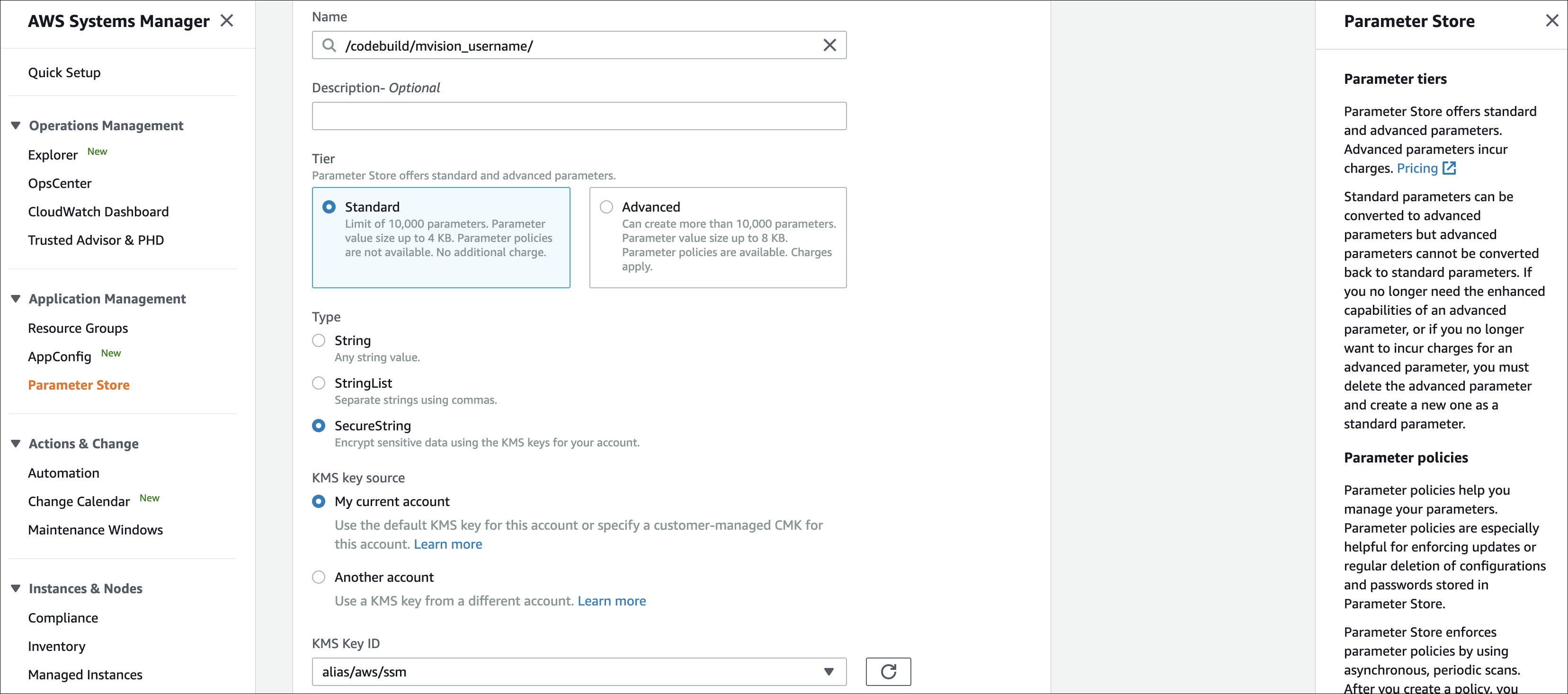
- Navigate to the AWS Lambda page, and select the lambda function invoke-code-build-<<account_id>>.
You are navigated to the lambda function. - Go to the Configuration tab and click Add trigger.
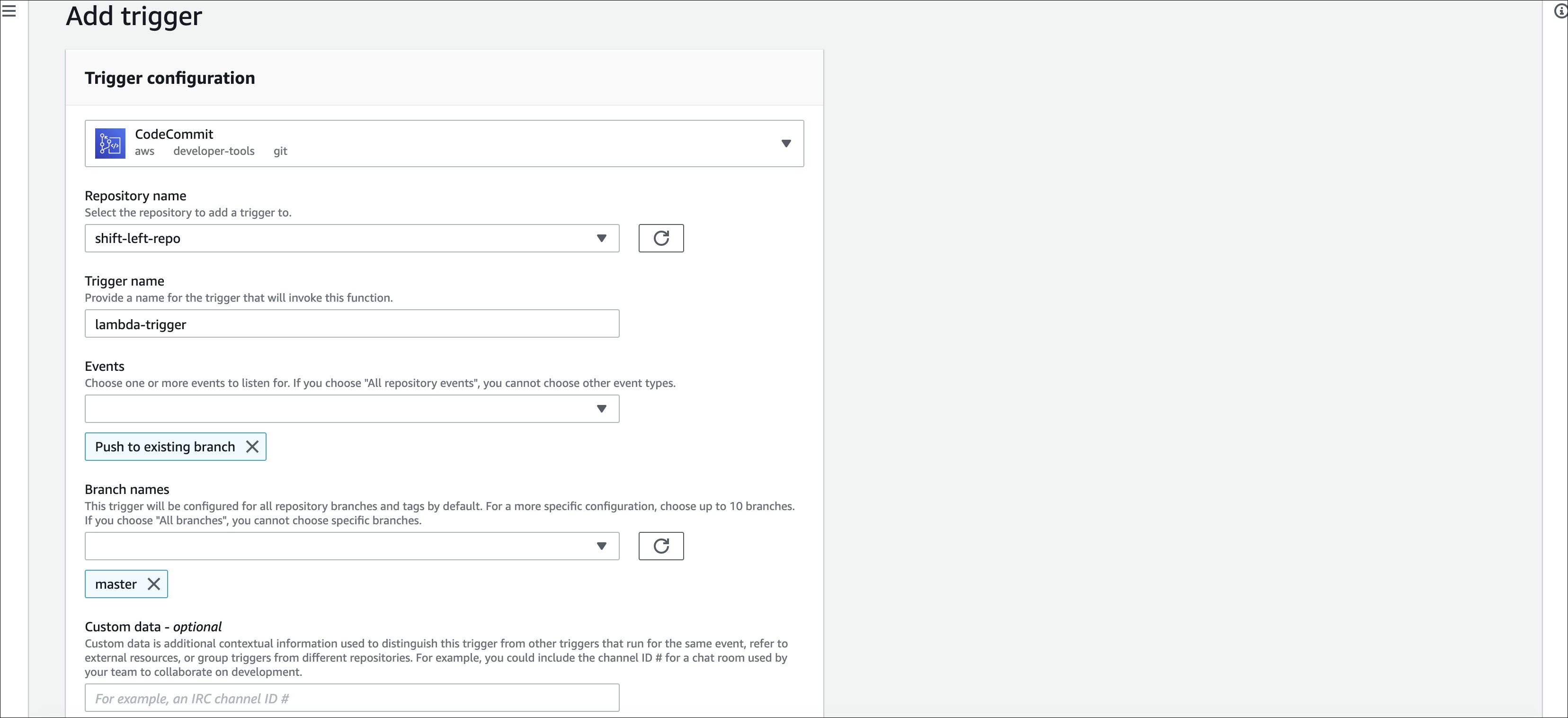
- Add the following trigger configuration:
- Select a trigger as CodeCommit.
- Select the Repository name as shift-left-repo.
- Provide a name for the trigger in the Trigger name textbox.
- Select the Events as Push to existing branch.
- Select the Branch names as master and click Add.
- The CodeCommit trigger is added to the lambda.
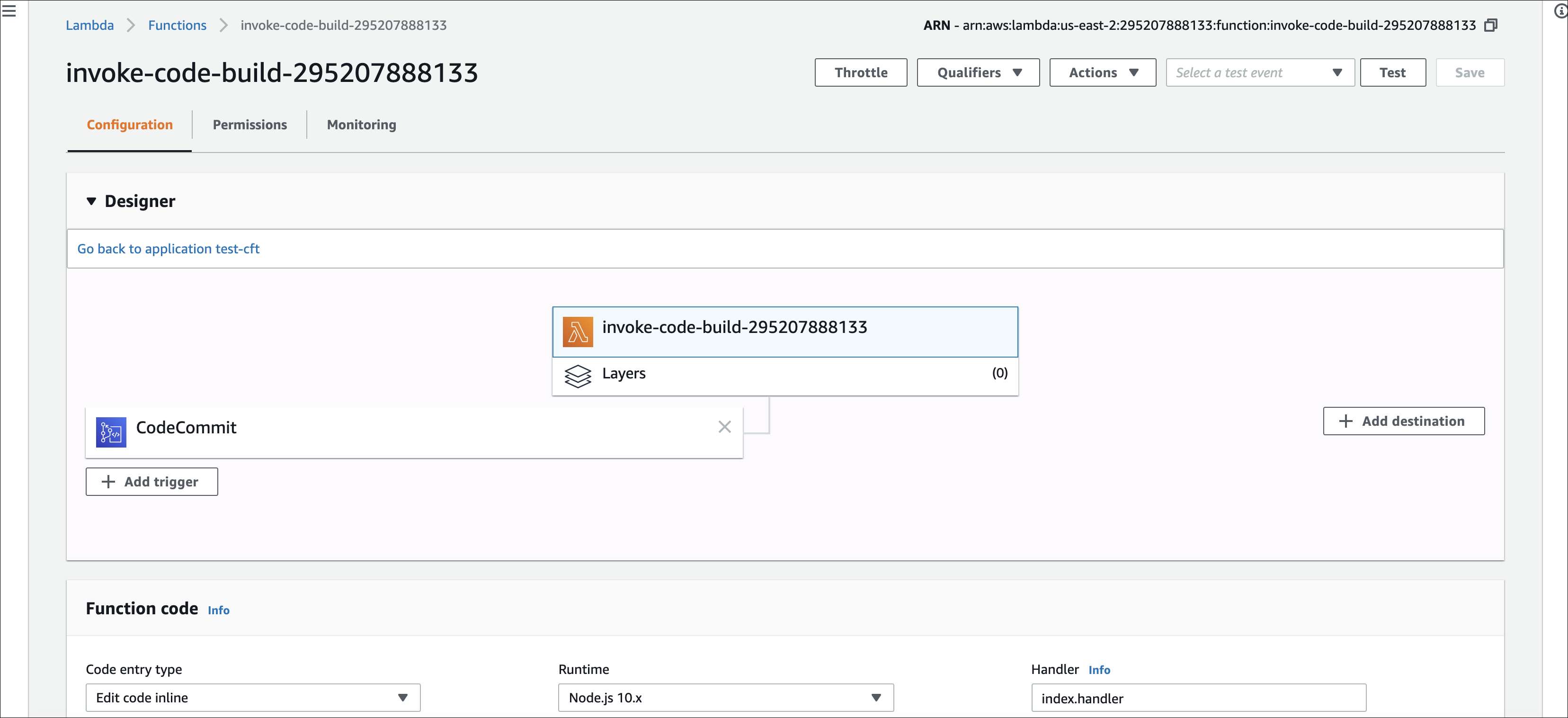
The CodeCommit and CodeBuild integration with Skyhigh CASB Shift Left inline API is complete.
Any push to the CodeCommit repo triggers a build in CodeBuild, which calls the Shift Left inline APIs to check for vulnerabilities present in the DevOps template committed in CodeCommit.

