Create a Vulnerability Policy
About Vulnerability Policies
A Vulnerability Scan policy determines the vulnerabilities to be included or excluded from an incident. Each vulnerability includes the following attributes:
| Attributes | Description |
|---|---|
| CVE Severity | Select a vulnerability severity level: High, Medium, and Low. |
| CVE ID | The unique identifier for the CVE. |
| Package | The entity that has the vulnerability (for example, an installed software package). |
| Namespace | The platform in which the vulnerability is found (for example, Ubuntu:18.04). |
| CVE Severity | Select a severity for the CVE incident: Critical, Major, Minor, Info, and Warning. |
You can enter multiple entries for CVE ID, Package, and Namespace fields separated by commas. Alternatively, you can also use the wildcard (*) for a wide range of selections.
Create a Vulnerability Policy from a Policy Template
To use the preconfigured Vulnerability Template, High-Severity CVEs, use the following steps:
- Go to Policy > Policy Templates.
- Filter for Policy Type > Vulnerability.
- For High-Severity CVEs, click Create Policy.
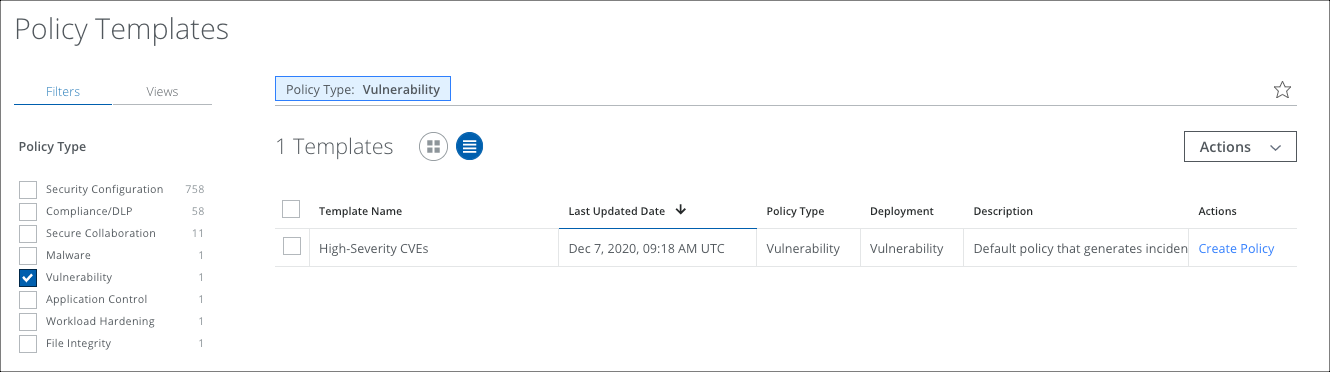
- The High-Severity CVEs policy displays on the Policy > Vulnerabilities page.
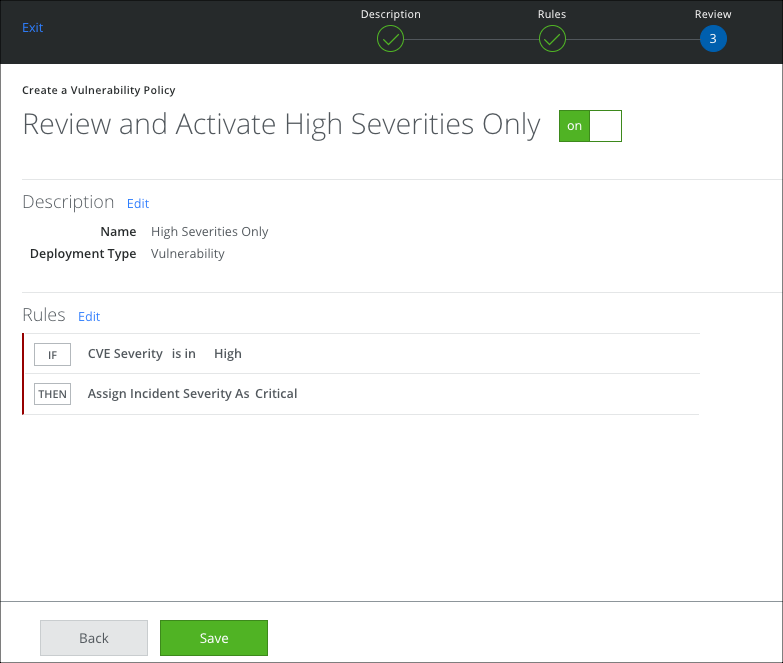
Create a Vulnerability Policy
You can create a Vulnerability Policy, or edit an existing policy to customize it for your requirements.
To create a policy, perform the following steps:
- Go to Policy > Vulnerabilities.
- Click Actions > Create Policy.
- On the Description page:
- Name. Enter the policy name
- Add Description. Enter an optional description for the policy.
- Available for On-Demand Scan. The policy is available to use with an On-Demand scan by default.
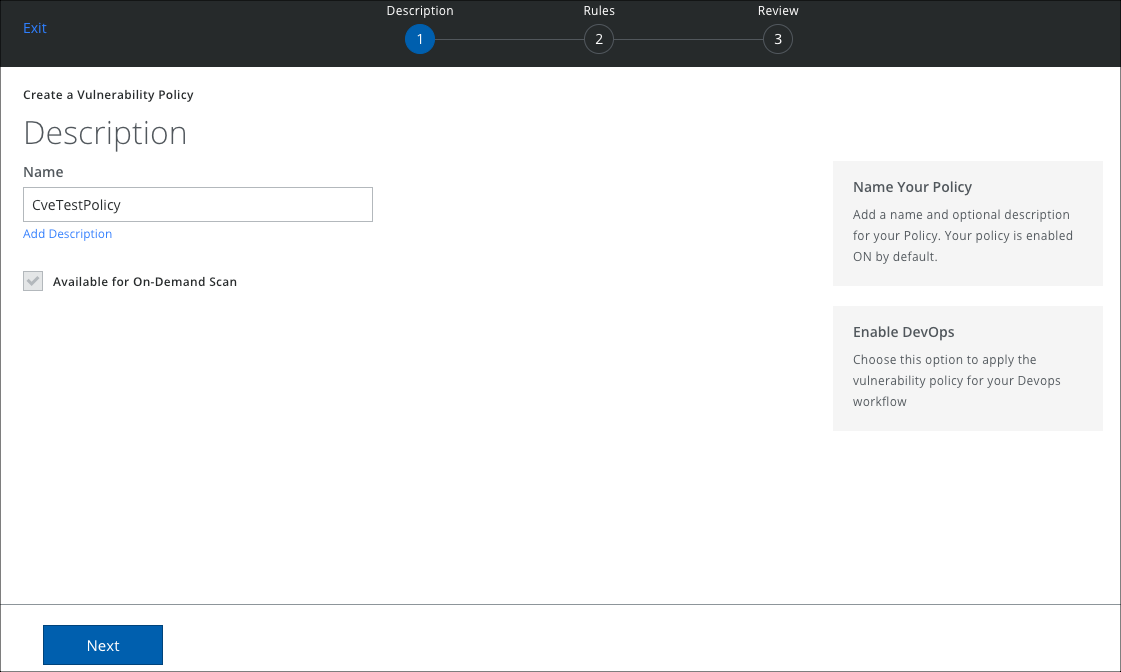
- Click Next.
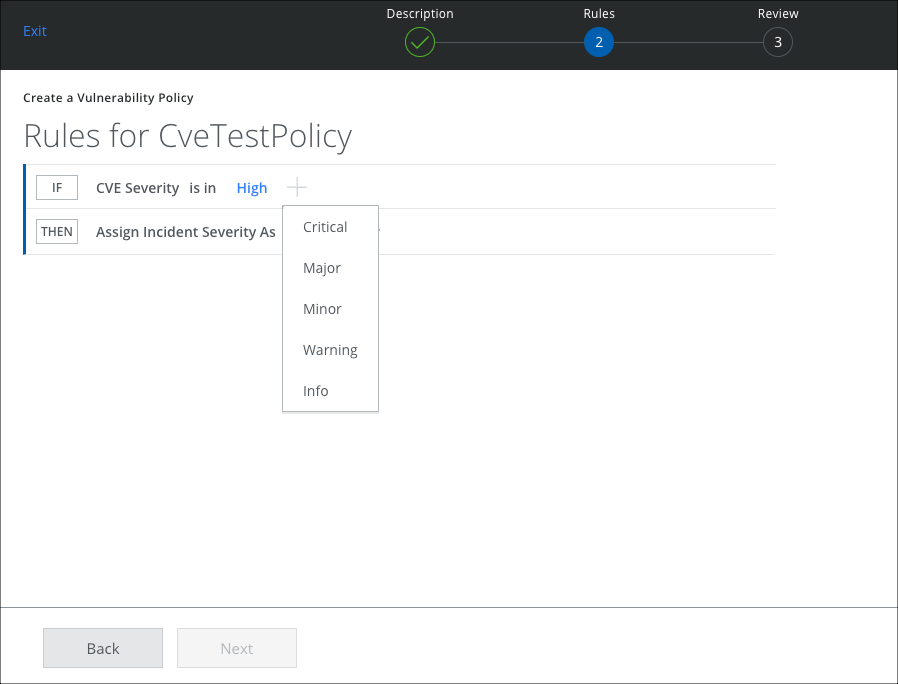
- On the Rules page, choose the attributes to set the rule and click Done.
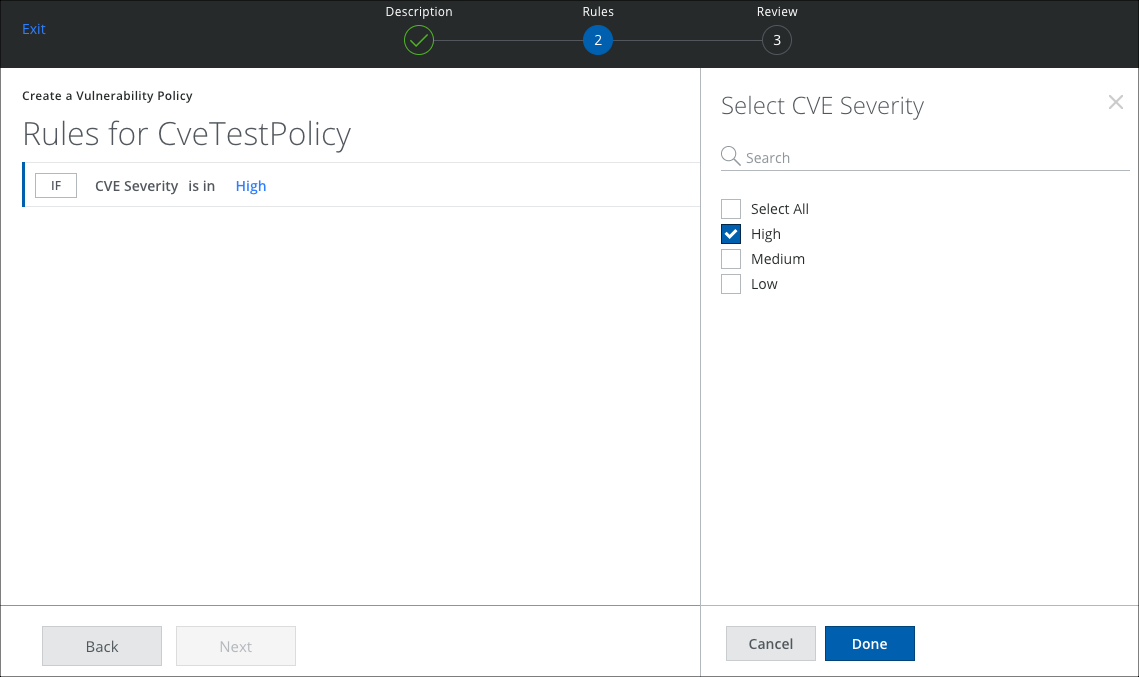
- To assign a severity to the incident, click Then and select a severity. Then click Next.
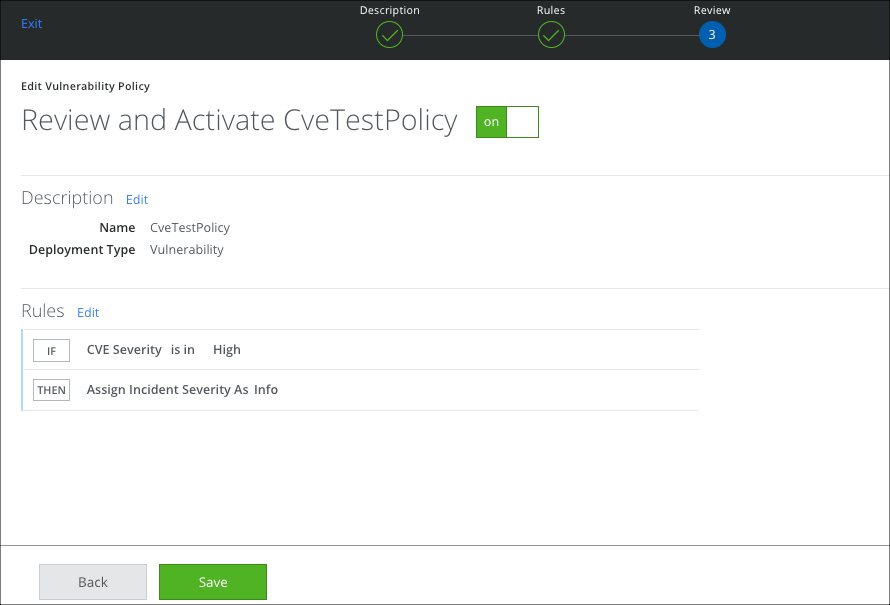
- Review your selections and click Save.
Create a Vulnerability Scan
Once your Vulnerability policy is created, configure a Vulnerability Scan to run and generate any possible incidents.
Deny List and Allow Lists
The most useful way to create CVE policies is by creating Deny Lists or Allow Lists. You can create a policy to deny or allow the vulnerabilities based on the attributes. This allows you to prioritize or ignore incidents with attributes specific to your needs. The attributes can be set using:
- is in operator to deny
- is not in operator to allow
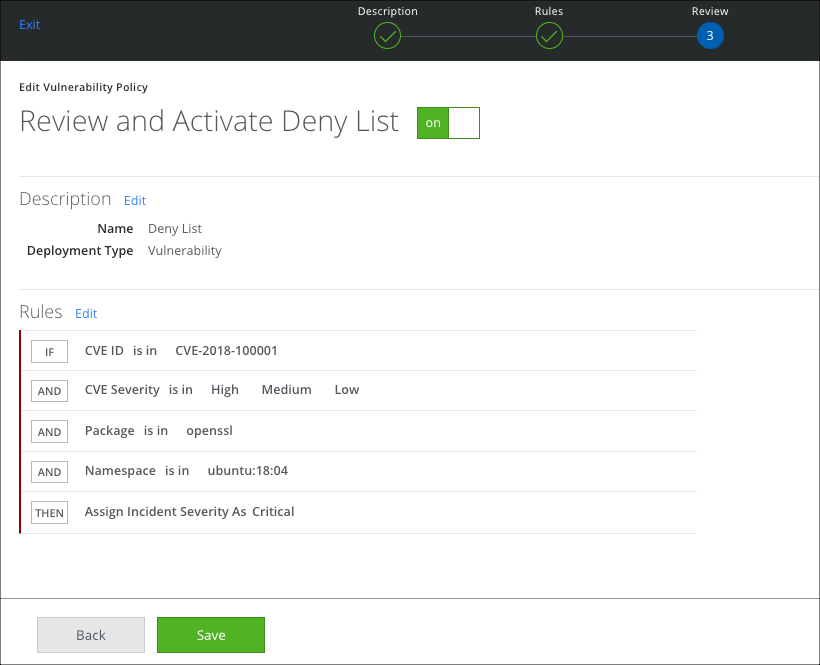
Deny List Policy Rules
In this Deny List policy, you have specified that you ARE interested:
- In a particular CVE regardless of its severity.
- In the feature openssl.
- In the namespace ubuntu:18.04.
Whenever these rules match, Skyhigh CASB creates a High severity incident. This allows you to make sure that certain Features, Namespaces, CVE Severities, and CVE IDs are never ignored.
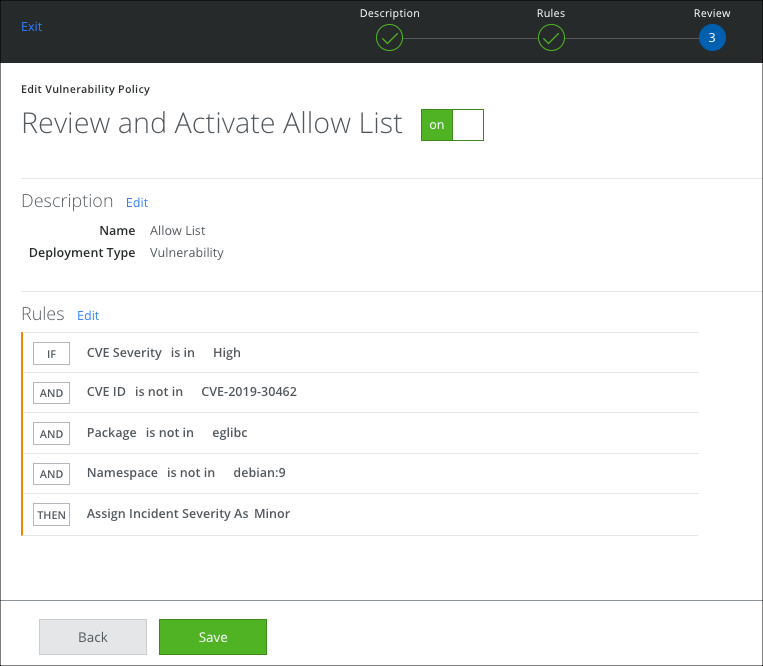
Allow List Policy Rules
In this Allow List policy, you have specified that you ARE NOT interested:
- In a particular CVE.
- In Medium, or Low severity CVEs.
- In the feature eglibc.
- In the namespace debian:9.
So any CVE that matches these rules is assigned an incident severity of Minor. Under Responses, you have specified that incidents must be created only for High severities. So no incidents are created that are less than High. This allows you to ignore certain Features, Namespaces, CVE Severities, and CVE IDs.
Severity Filters for Scans Created before 5.0.2
Severity filters remain the same for scans created before Skyhigh CASB 5.0.2. This is for backward compatibility. However, all new scans require a policy to be attached to the scan configuration.
The easy way to migrate to the new paradigm keeping the old behavior is to create a policy and only select the CVE Severity.