About Cloud Access Policies
Cloud Access Policies are used to protect cloud data access and manage devices. Cloud Access Policies can be set up to block access to all service uploads. For example, configured policies can require step-up authentication before downloading a file.
Also, Cloud Access Policies specify the correct behavior for managed and unmanaged devices. This is managed by provisioning certificates to devices and creating policies that require an unmanaged device to register before accessing a page, for example. Certificates are OS-agnostic, version-independent, and can be easily revoked or cycled, offering you a great deal of control and flexibility in cloud access management.
Policies are built on conditions (rules) and actions. Conditions are used with IS or IS NOT arguments to define the specific situation when a policy should be enacted. Actions then determine what happens when a policy is enacted.
They are supported for both Reverse and Forward Proxy integrations.
Cloud Access Policies are evaluated in order from top to bottom. For details, see Reorder Cloud Access Policies.
Provisioning Certificates
At a high level, certificates are created using a Certificate Authority or Public Key Infrastructure (PKI) system, or OpenSSL.
- The cert is distributed to managed endpoints via an MDM, GPO, or other package management utility. If this distribution method isn't available for all endpoints, the certs can be manually imported into a computer's local certificate store (root permissions required).
- The signing certificate, which is public, is uploaded to Skyhigh CASB.
- Then, optionally, a URL is configured to allow Skyhigh CASB to query the Certificate Revocation List to verify that the existing certs are valid.
Device Certificate Check Workflow
The certificate check workflow allows Skyhigh CASB to verify that certificates are valid and to determine if endpoints are managed or unmanaged. When a device requests access to an endpoint, Skyhigh CASB checks the endpoint for a required certificate, which must be signed by the CA public certificate (which is imported into Skyhigh CASB). If the endpoint has a valid certificate (signed by the CA), Skyhigh CASB considers the endpoint managed. If the endpoint does not have a certificate signed by a CA, the endpoint is considered unmanaged.
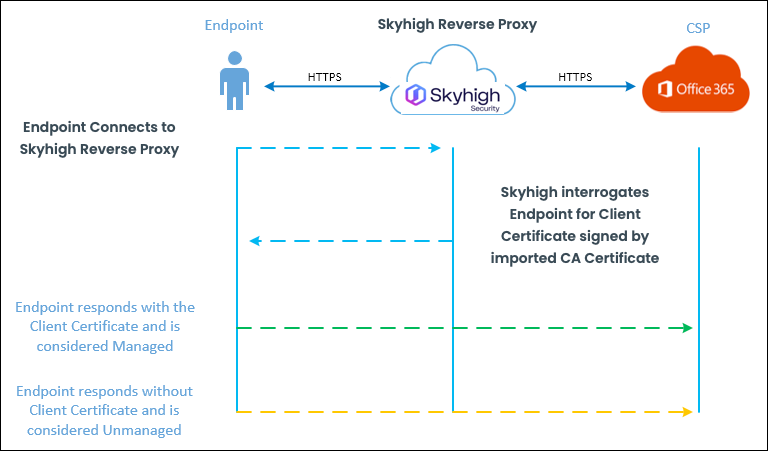
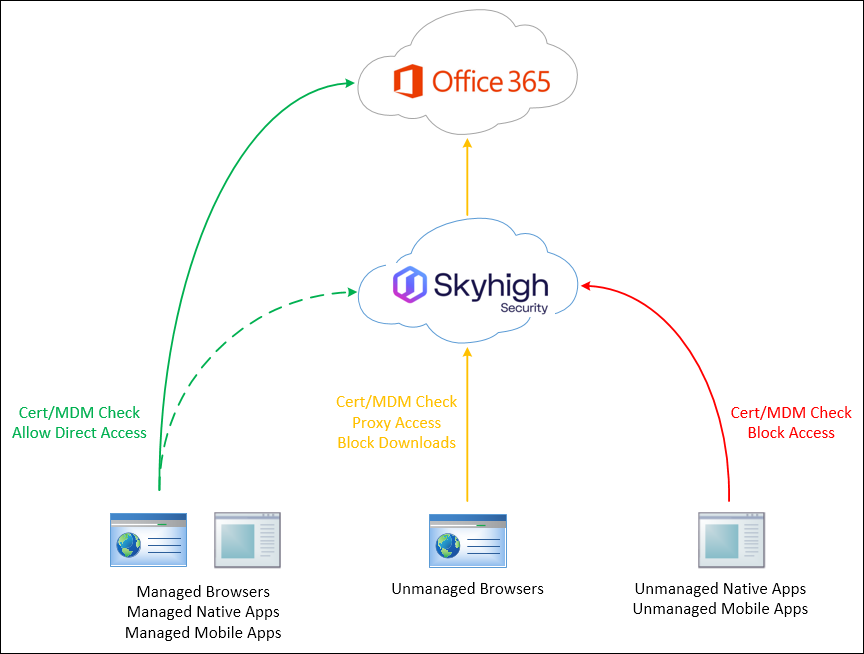
Sample Gold Standard CAP Visualization for Office 365
Cloud Access Policies Page
The Cloud Access Policies page is located at Policy > Access Control > Access Policies.
Cloud Access Policies are evaluated in order from top to bottom.
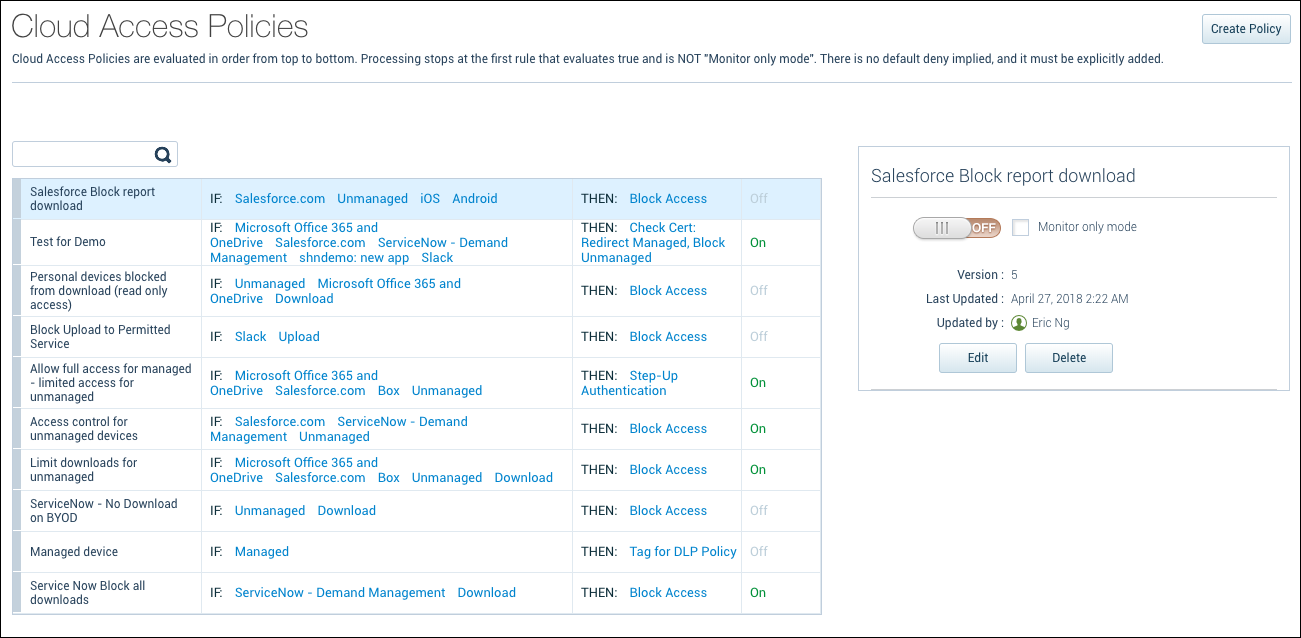
The Cloud Access Policies page provides the following information and actions:
- Create Policy. Click to Create a Cloud Access Policy.
- Reorder. Click to Reorder Cloud Access Policies.
- Policy
- IF
- THEN
- On/Off

