Detect Data Classification Tags
- Boldon James
- Titus
- Trellix
- Box
- Microsoft Azure
Skyhigh CASB supports other classification technologies, which apply tags to document metadata, as we define a DLP policy based on metadata tags.
Data Classification tools like Boldon James, Titus, and Microsoft Azure Information Protection (AIP) persist the classification label as part of document metadata. So the label travels with the document, and you can search for it. You can take action using an external compliance tool or policy engine. Skyhigh CASB's data extraction can extract both metadata and data from over 300 different types of files.
Detection Strategy
Skyhigh CASB provides a set of Policy Templates to detect on tags, Classification labels, or protective markings as part of the Policy Template for the most popular classification tools. There are two detection strategies to choose from: Broad Detection and Narrow Detection.
Broad Detection
For the Broad Detection strategy, you choose to detect on labels based on the user-friendly name of the label. For example, "Confidential", "Internal Only or "FOUO".
This detection strategy allows you to not only detect labels added by employees in your organization, but also to detect labels added by third-parties. For example, you can detect labels on a document you received from an external person who also uses a data classification tool, but not necessarily the same tool or policy that your organization is using.
In this case, the detection capability should be broad, as you would like to detect as many files as possible that might have a document classification, while knowing that certain false-positives might be detected.
You should create a DLP Policy rule to detect keywords in the Metadata section of the documents. This only matches files that have these words in the metadata and will not trigger if a document, for example, contains the word "confidential" in the flow text.
For example, with a keyword policy like this:
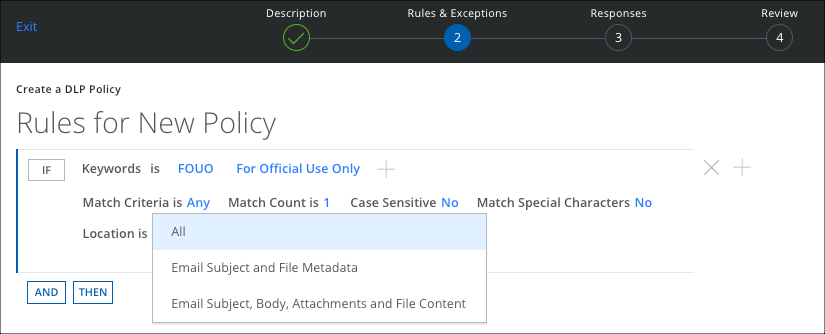
This matches files with one of the keywords "FOUO" or "For official use only" in the Metadata, but does not match when these words are found in the body of the file.
| Example | Properties / Metadata | File Contents |
|---|---|---|
| This file is matched by this policy as it has one of the keywords in the metadata | 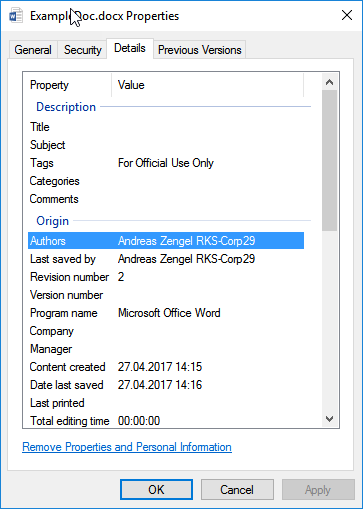 |
 |
|
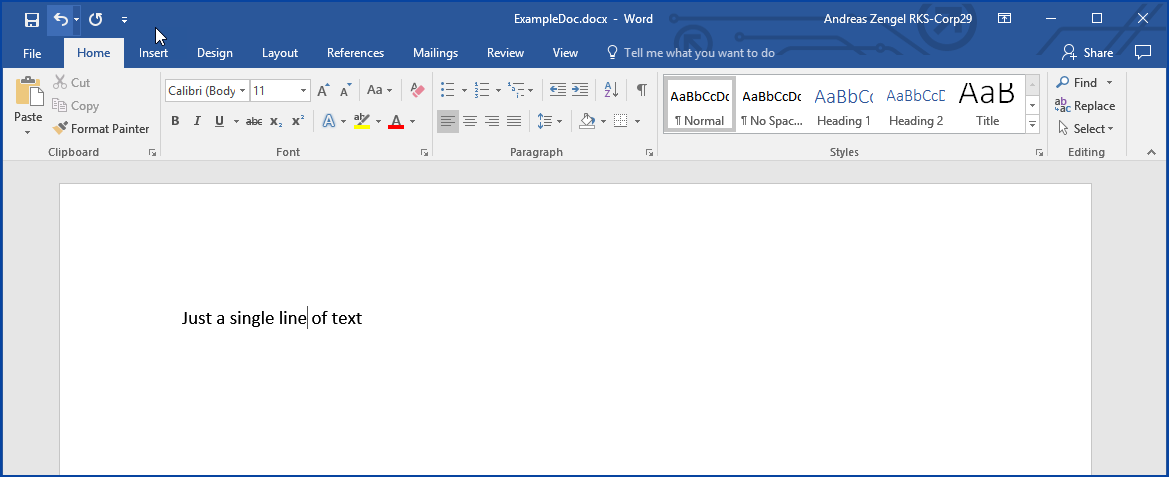
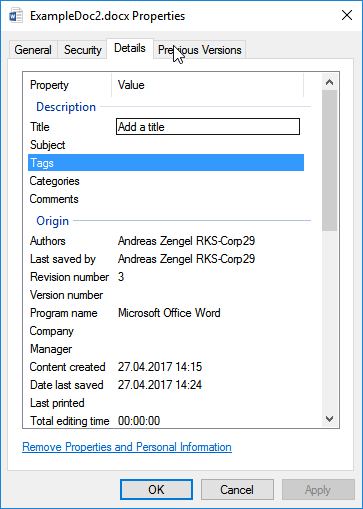
This file is not matched by this policy as it has one of the keywords in the body but not in the metadata |
 |
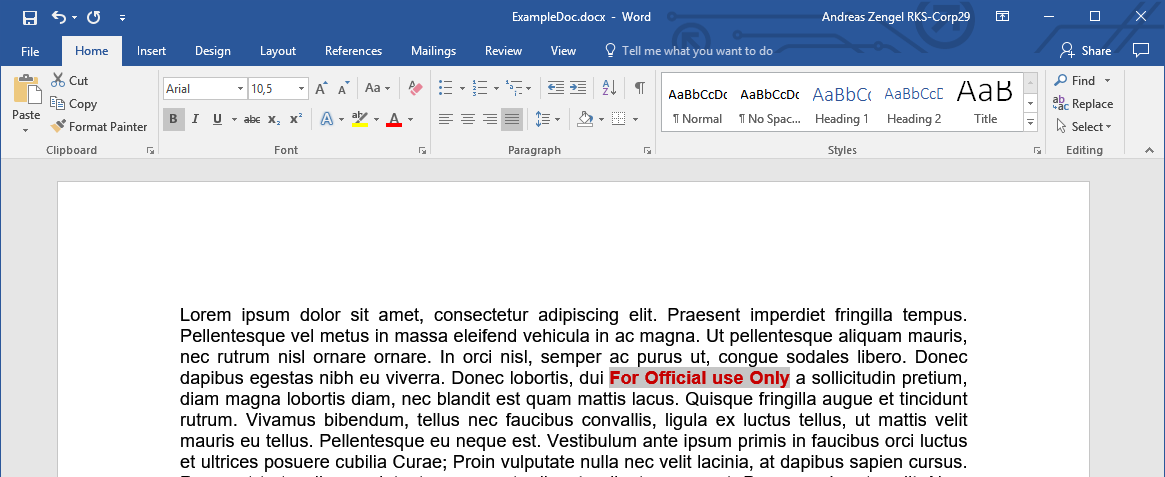 |
Narrow Detection
For the Narrow Detection strategy, you choose to build a policy that only matches on classification labels that are added by employees from our organization using your classification tool. This can be achieved by following the fact that every classification tool adds not only the user-friendly name of a label but also some additional metadata to uniquely identify the policy and the ID of the label.
This detection method is focused on finding classified documents that were classified inside your organization and does not detect any external or third-party classification tags. It also has a low false-positive rate.
You should create a DLP Policy rule to detect certain Regular Expressions or keyword proximity matching in the Metadata section of the documents. Set the regular expression to include the unique identifier for your classification tool or the unique identifier for your classification policy.
To create a policy, you can import Policy Templates for the most common document classification and tagging solutions from the DLP Policy Templates section by searching for Document Classification Solutions.
Boldon James
For Boldon James, it is best to use keyword proximity matching to match on the internal tag name and the policy id. The following matches on all documents marked as Confidential within the organization that uses the Boldon James Policy with the unique ID b669e953-f8eb-49a8-a8f3-ffec153ba63e.
"id_classification_confidential b669e953-f8eb-49a8-a8f3-ffec153ba63e"~50
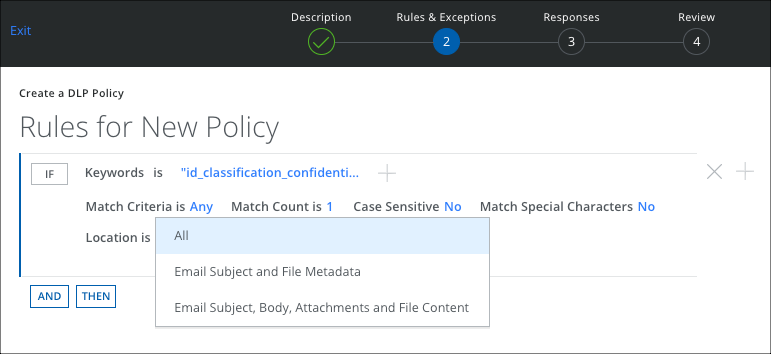
Microsoft Azure Information Protection (AIP)
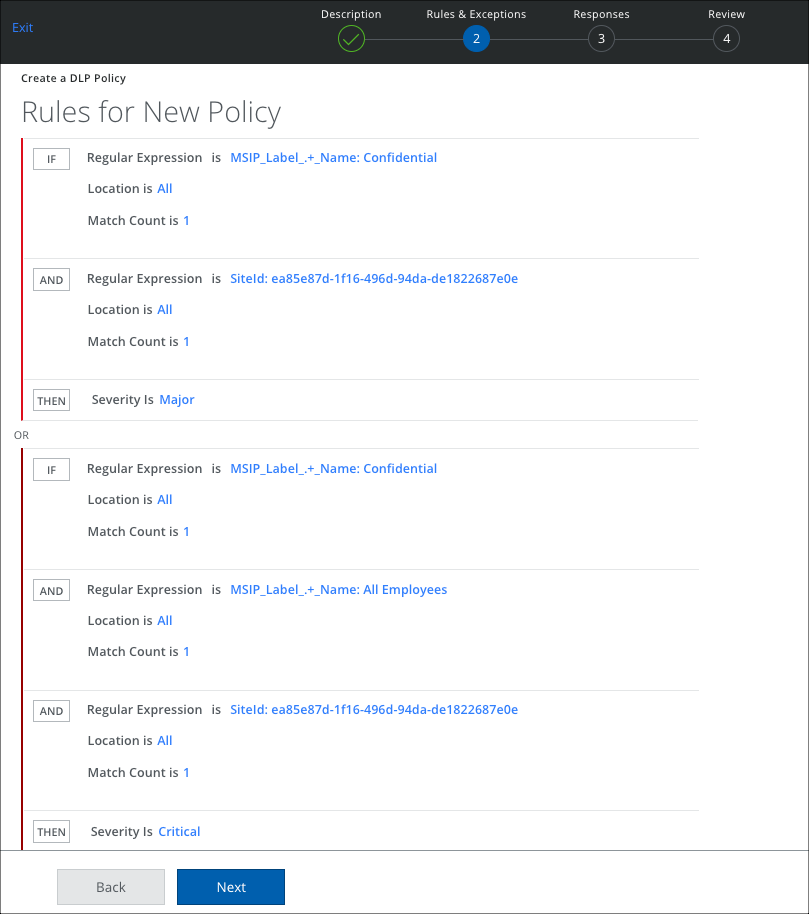
For Microsoft Advanced Information Protection (AIP) it is best to use a regular expression to match on the tag name and the site id. The following matches on all documents marked as Confidential within the organization with the site ID ea85e87d-1f16-496d-94da-de1822687e0e.
Another Rule Group is configured to detect subclassification levels that can be defined in AIP, for example, All Employees. The following shows an example of an AIP policy and how it's mapped to a Skyhigh CASB Policy:
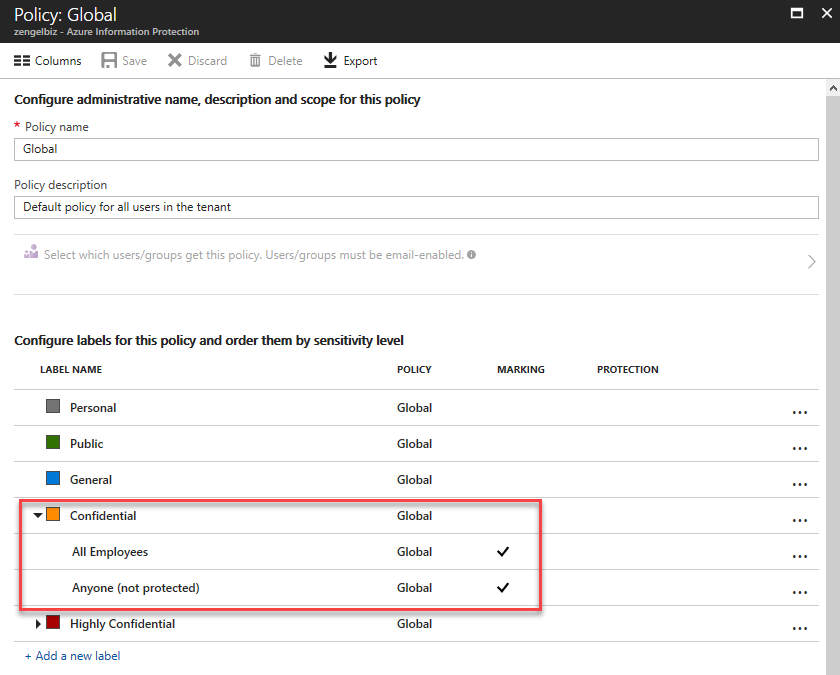
MSIP_Label_.+_Name: Confidential SiteId: ea85e87d-1f16-496d-94da-de1822687e0e
Titus Labs
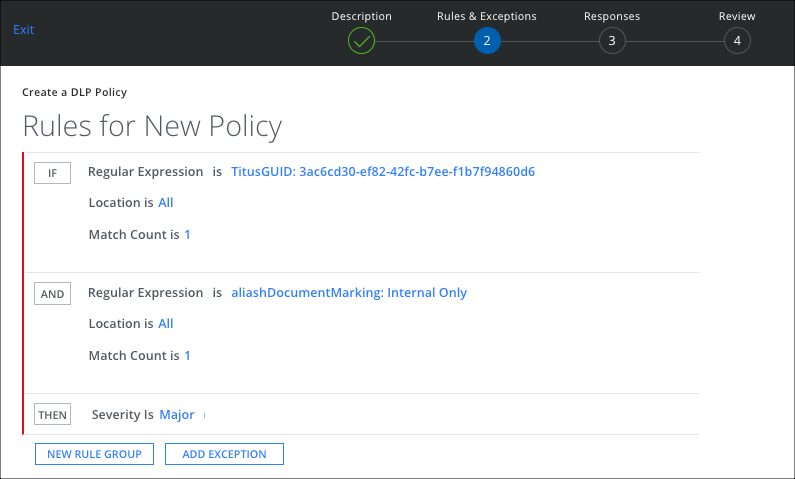
For Titus Labs, it is best to use a regular expression to match on the tag name and the TitusGUID. The following matches on all documents marked as Internal-Only within the organization with the TitusGUID 3ac6cd30-ef82-42fc-b7ee-f1b7f94860d6.
TitusGUID: 3ac6cd30-ef82-42fc-b7ee-f1b7f94860d6 aliashDocumentMarking: Internal Only
What's Next
You can now enable the policies with these rules to detect files with the appropriate classification labels. You can use this for example in an On-Demand Scan to enumerate all files with a specific classification or in a secure collaboration policy to prevent sharing of classified data with external parties.

