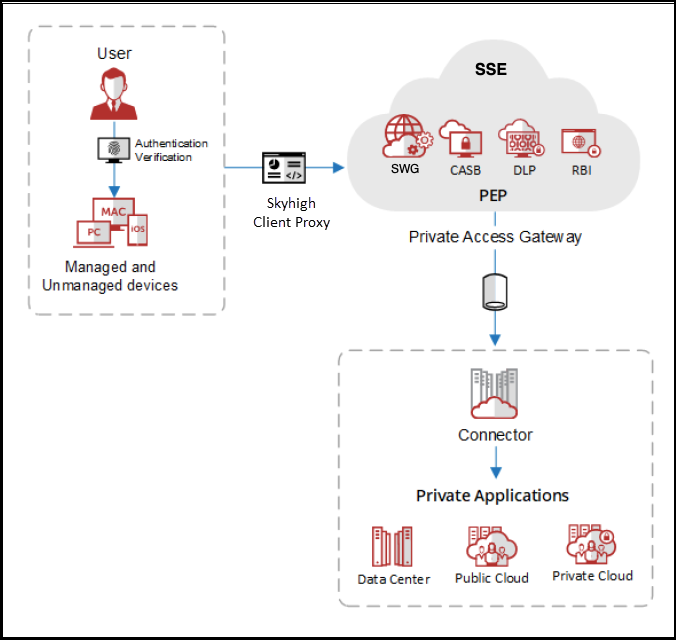
How Skyhigh Private Access Works
Skyhigh Private Access performs the following functions:
- Identity — Verifies all identities with strong authentication
- Device — Checks for the device security posture
- Network — End-to-end encryption of communication
- Policy Enforcement Point (PEP) — Enforcement of policies (web policy, DLP, RBI, and least privilege access)
- Private application — Monitor and control access to private applications
Key components
Skyhigh Private Access uses a variety of technologies to manage and control access to private applications, as shown in the following graphic:
- Skyhigh Security Client Proxy — The Client Proxy software is installed on the devices to facilitate SAML authentication. When the user is not authenticated, Client Proxy prompts the user to authenticate. It securely forwards the traffic to Skyhigh SSE. When forwarding the traffic, it encrypts and adds metadata along with the real-time device posture information.
- Skyhigh SSE — This is the Policy Enforcement Point, where it enforces the private access policy on the traffic forwarded by Client Proxy. This traffic is further routed over TLS tunnels to a Skyhigh Private Access Connector through a Private Access Gateway deployed in Points of Presence (PoPs).
- Connector groups — Connectors are logically grouped to achieve scalability and availability. Private applications are always associated with a connector group and not a connector directly. Every connector group should be associated with at least one private application.
- Connectors — A connector is a virtual machine deployed in the same environment (data center, private cloud, or public cloud) as the private application. It establishes a secure outbound connection with the Private Access Gateway and provides access to the requested application. It also updates the status of the private application to the Private Access Gateway.
- Application group — Create an application group to achieve scalability and logically manage different applications as one entity.