Risky Web — Use Browser Isolation for Websites Considered a Risk
You can use Remote Browser Isolation (RBI) when allowing a user's request to access a website is considered a risk. You can also configure exceptions and other settings.
The web security functions that are implemented under Secure Web Gateway determine whether access to a website is considered a risk.
If a website is considered a risk at a given point in time, it does not mean that this evaluation is to remain forever. On the other hand, a website that is not considered a risk now might be considered one later.
This is because websites can change over time regarding their maliciousness. Also, the risk algorithm used to rate websites is continually getting better.
- On the user interface for Secure Web Gateway, select Policy > Web Policy > Policy.
-
From the policy tree in the navigation panel, select Browser Isolation > Risky Web.
The selected rule set appears in the configuration area on the right. -
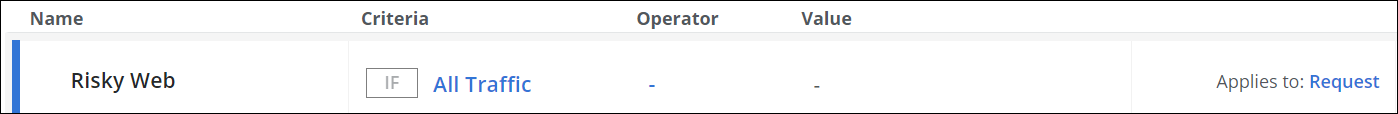
Configure when this rule set should apply.
-
Under Criteria, leave the default All Traffic, as you want the rules in this rule set to apply to all web traffic.
- Next to Applies to, leave the default Request, as you want the rules in this rule set to be processed in the request cycle of web filtering on Secure Web Gateway.
-
-
To let some requests skip the remainder of this rule set, which means the browser isolation rules are not processed for these requests, configure lists for the skipping rules that are preset here. They are shown under Preset Rules.
You can configure entries for domains, IP addresses, URL categories, and reputation risk levels in these lists.
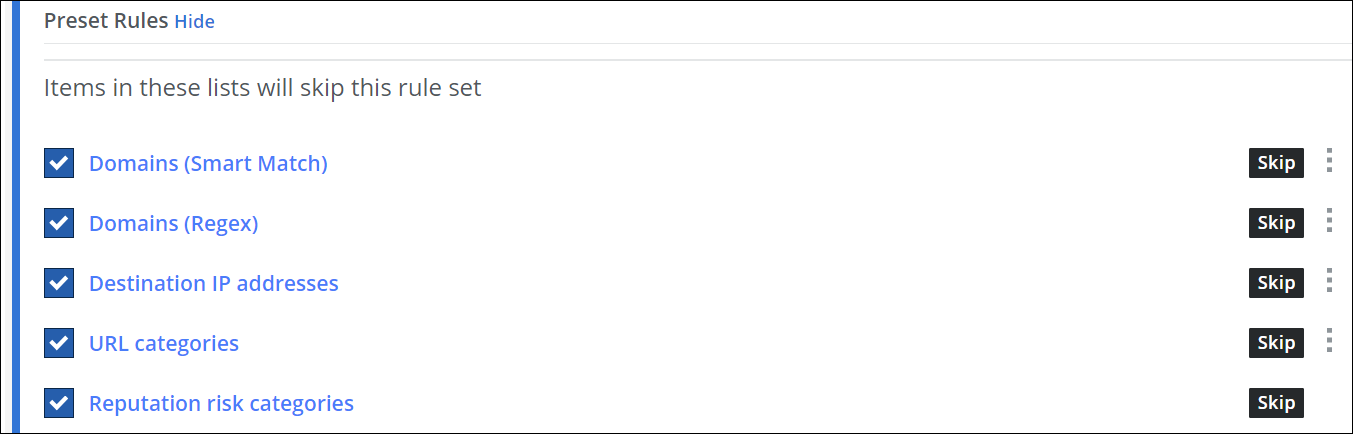
Click the three dots at the end of the row for a rule and work with the options for list handling that are provided. Or click the name of the list for a rule, for example, Domains (Smart Match), to work with these options.
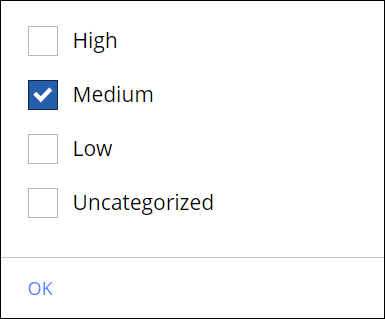
For the reputation risk levels, click the rule name and select a level, for example, Medium.
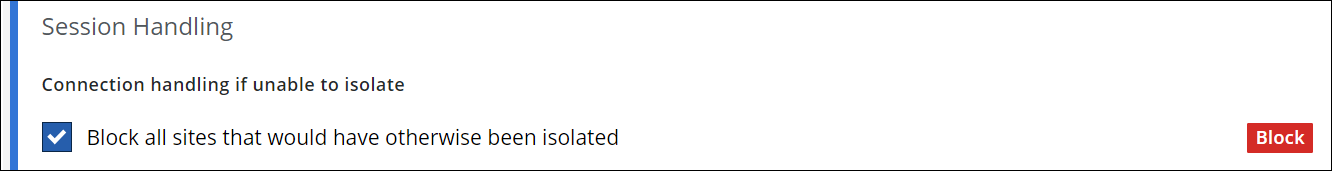
- Under Session Handling, configure what to do when browser isolation cannot be applied.
Leave the preset Block all sites that would otherwise have been isolated rule enabled or disable it. If you disable it, users can access these websites without browser isolation.
-
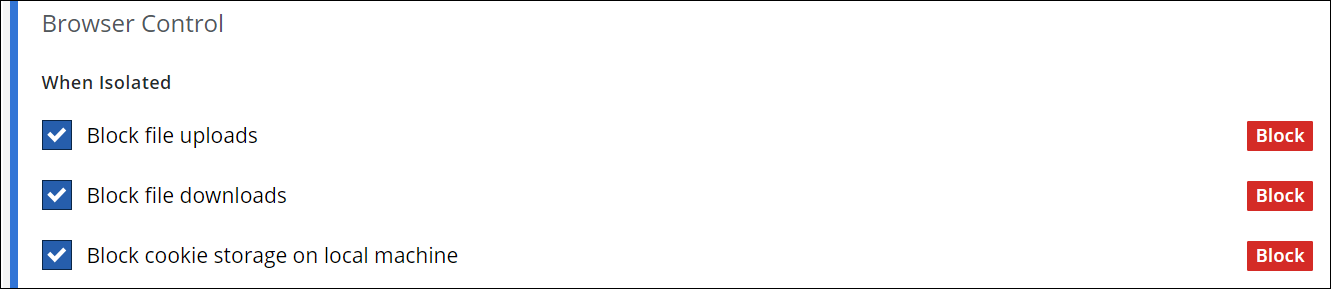
Under Browser Control, configure how to handle file uploads and downloads as well as cookie storage on a user's system when browser isolation is applied.
-
Block or allow file uploads.
-
Block or allow file downloads.
- Block or allow storing cookies on a user's system.
-
-
Under Browser Settings, configure whether browser isolation is indicated in a user's browser by a green border and a message.

-
Select Disable Browser isolation indicator to disable this indicator as needed.
Th browser isolation indicator is a green border, which is shown around a web page in the user's browser when browser isolation is applied. It is shown to indicate that this web security measure is in place. If the indicator is disabled, browsing the web is still protected by browser isolation, but this web security measure is hidden.
If you do not select this option, the green border is shown to indicate that browser isolation is applied. -
Select Disable Browser isolation pop-up to disable this pop-up as needed.
A pop-up message appears in the user's browser by default at the beginning of a session when full browser isolation is applied to it. It informs the user that this web security measure is being taken.
If you do not select this option, the pop-up message appears to indicate that browser isolation is applied.
-
-
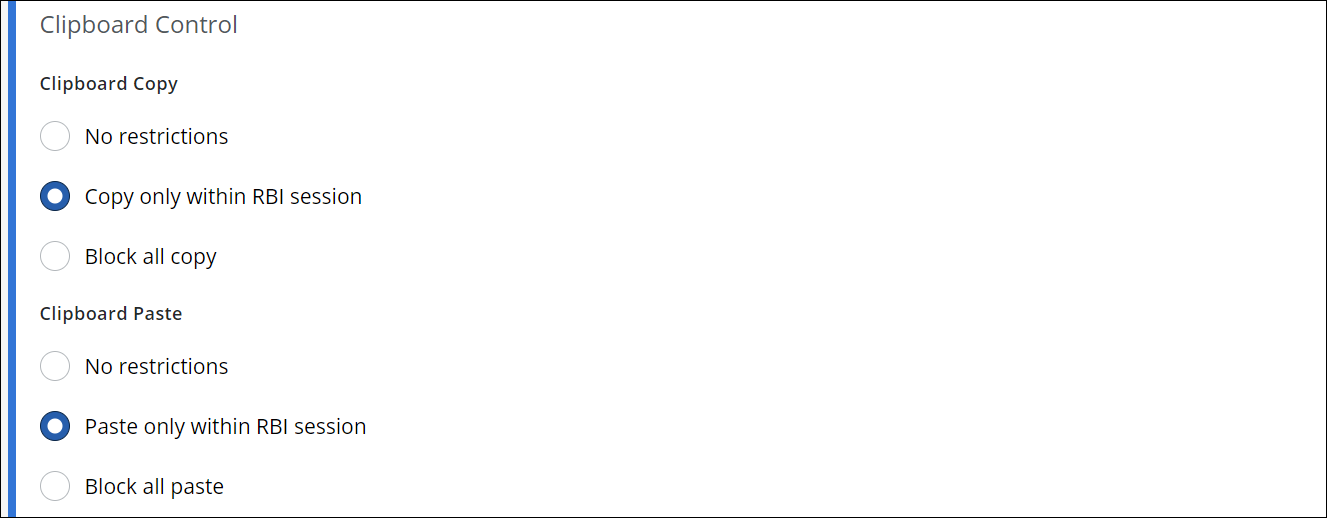
Under Clipboard Control, configure how to handle copying and pasting clipboard data when browser isolation is applied.
-
Configure copying: Impose no restrictions on it, allow it only within the same browser isolation session, or block it completely.
-
Configure pasting: Impose no restrictions on it, allow it only within the same browser isolation session, or block it completely.
-
You have now configured browser isolation for websites that are considered a risk, including exceptions and other settings.

