Configure the Ivanti Neurons MDM for iOS
Prerequisites
This article assumes your device is already managed with the Ivanti Neurons Mobile Device Management (MDM, formerly: MobileIron MDM) product. The enrollment of devices into Ivanti Neurons MDM is not within the scope of this document.
Configure the Server Root CA Certificate
- Go to the Configuration tab, search for Certificate configuration, and click on it.
- Enter the appropriate name in the Name field.
- In the Configuration Setup field, choose the server root CA certificate from the system.
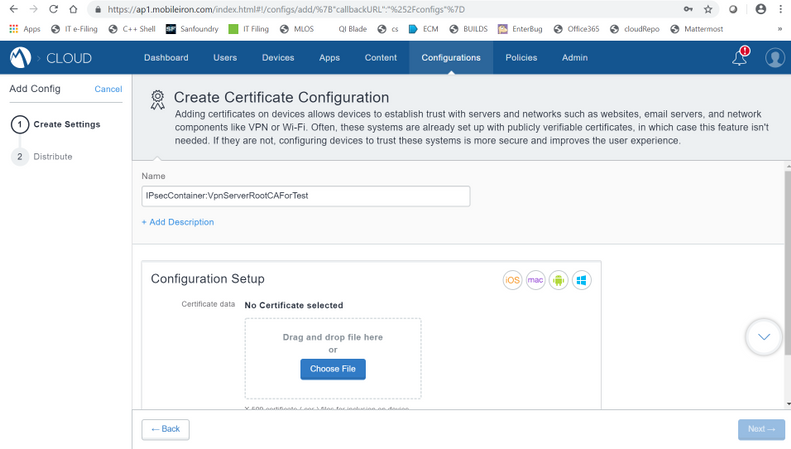
- Click Next → select in which device certificate to be pushed → click Done.
Configure Ivanti Neurons with the SCEP Server
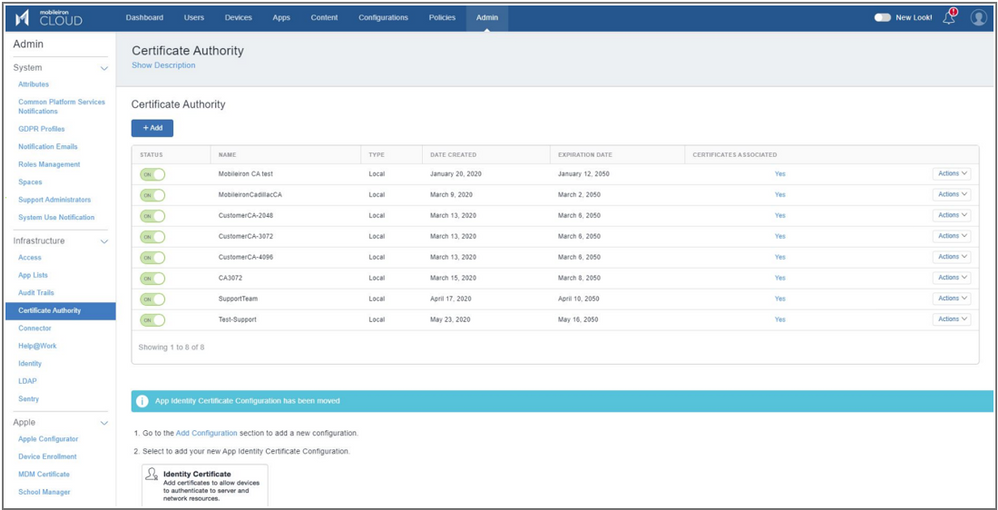
Step 1 : Configure a Certificate Authority
- Log on to Ivanti Neurons.
- Navigate to Admin → Certificate Authority ( on the left-hand pane ) → Add.
- Select Create a Standalone Certificate Authority → Continue.
- Complete the CA Certificate details, and click Generate.
You will now be able to see the generated CA Authority as shown below:
Configure Identity Certificate
Step 1: Go to Configurations tab, search for Identity Certificate configuration, and click on it.
Step 2: Configure Identity Certificate Template
- Navigate to Configurations → Add → Identity Certificate.
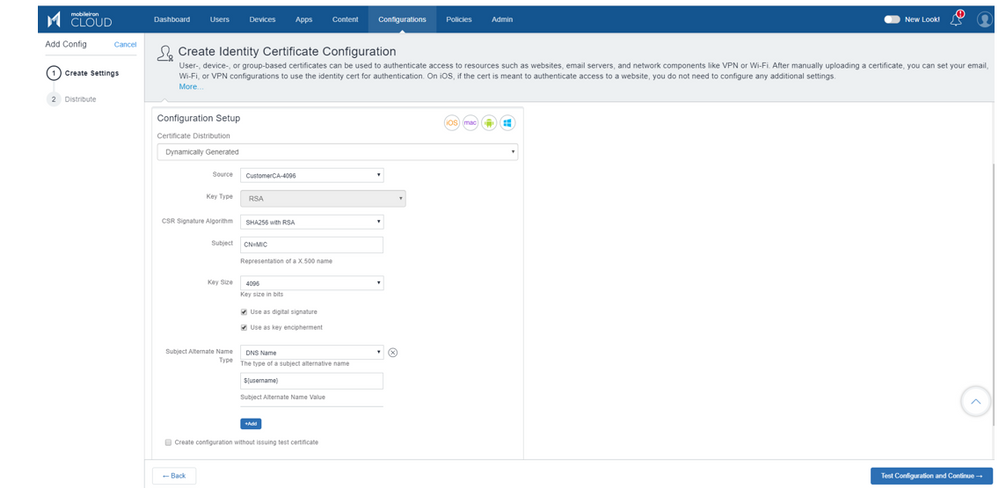
- From Configuration Setup, select Dynamically Generated.
- Select Source as the Certificate Authority you created in the previous step.
- Complete the field details.
- Click Test Configuration and Continue → Select distribution→ Save.
Create VPN Profile and distribute:
- Go to the Configurations tab, search for VPN configuration, and click on it.
- Enter all the required fields in the profile configuration.
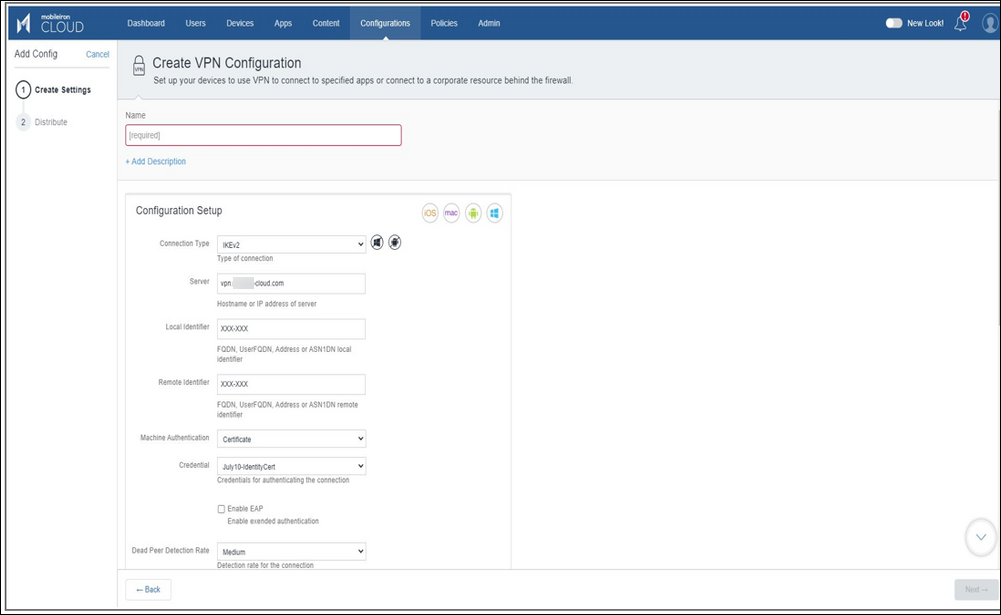
For example, the following are the values used in Dev/QA testing:
| Fields | Values |
|---|---|
| Server |
c<customer ID>.smcs.skyhigh.cloud The following information is required to configure an SMCS app in the MDM of your choice. VPN gateway address: c<customer ID>.smcs.skyhigh.cloud |
| Connection Type | IKEv2 |
| Local Identifier |
Client_Key1 (This string is SAN - (Subject Alternate Name) of client certificate) |
| Remote Identifier |
vpn.skyhigh.cloud (This string is SAN -( Subject Alternate Name) of server certificate) |
| Enable EAP | true |
| TLS Minimum Version | N/A |
| TLS Maximum Version | N/A |
| EAP Authentication | Certificate |
| Credential | IPsecContainer:ClientCertsIdentityForTest |
| Dead Peer Detection Rate | Medium |
| Server Certificate Issuer Common Name | VPN Server Root CA (This string is CN-Common Name of server root certificate) |
| Server Certificate Common Name | vpn.skyhigh.cloud (This string is CN-Common Name of server root certificate) |
| Use IP4 and IP6 subnets attributes | true |
| Enable IKEv2 Mobility and Multihoming Protocol (MOBIKE) | true |
| Enable Perfect Forward Secrecy (PFS) | true |
| Enable IKEv2 redirect | true |
| Enable NAT keep alive | true |
| NAT keep alive interval | 20 second(s) |
| IKE SA Params & Child SA Params |
Encryption Algorithm: AES-256 Encryption Algorithm: SHA2-256 Diffi e Hellman Group: 2 Lifetime In Minutes: 1440 |
| Proxy Setup | None |
Distributing/Pushing the profile:
- Click Next, and then click on Custom or All Devices.
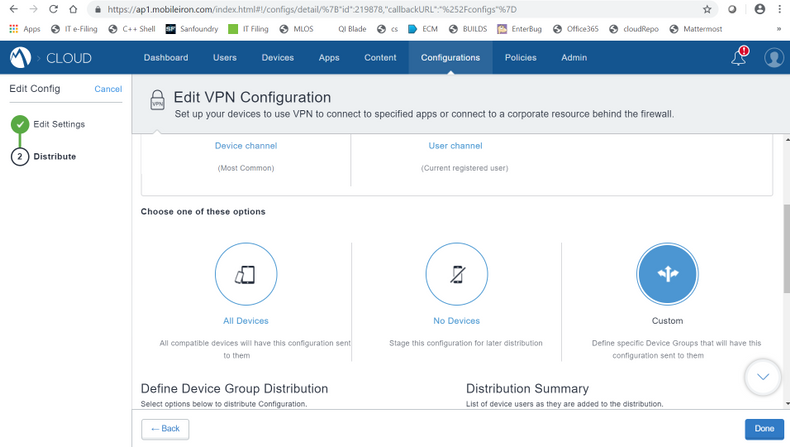
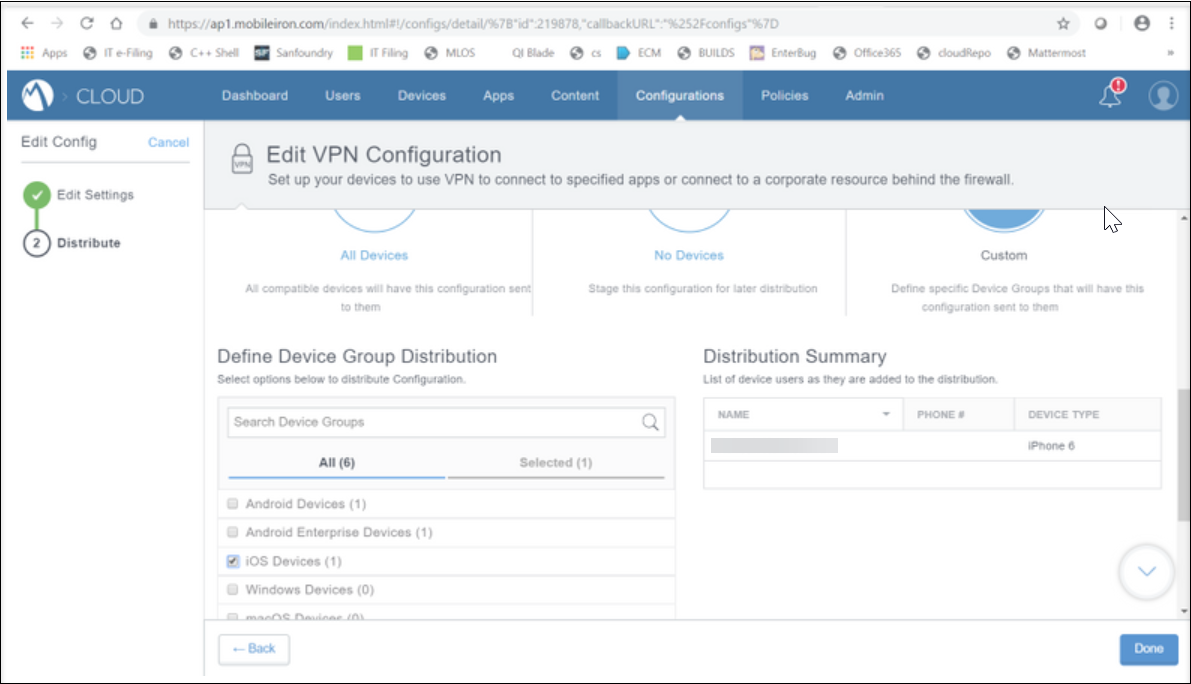
- If it is Custom, select in which mobile configuration to be pushed.
- Click Done.
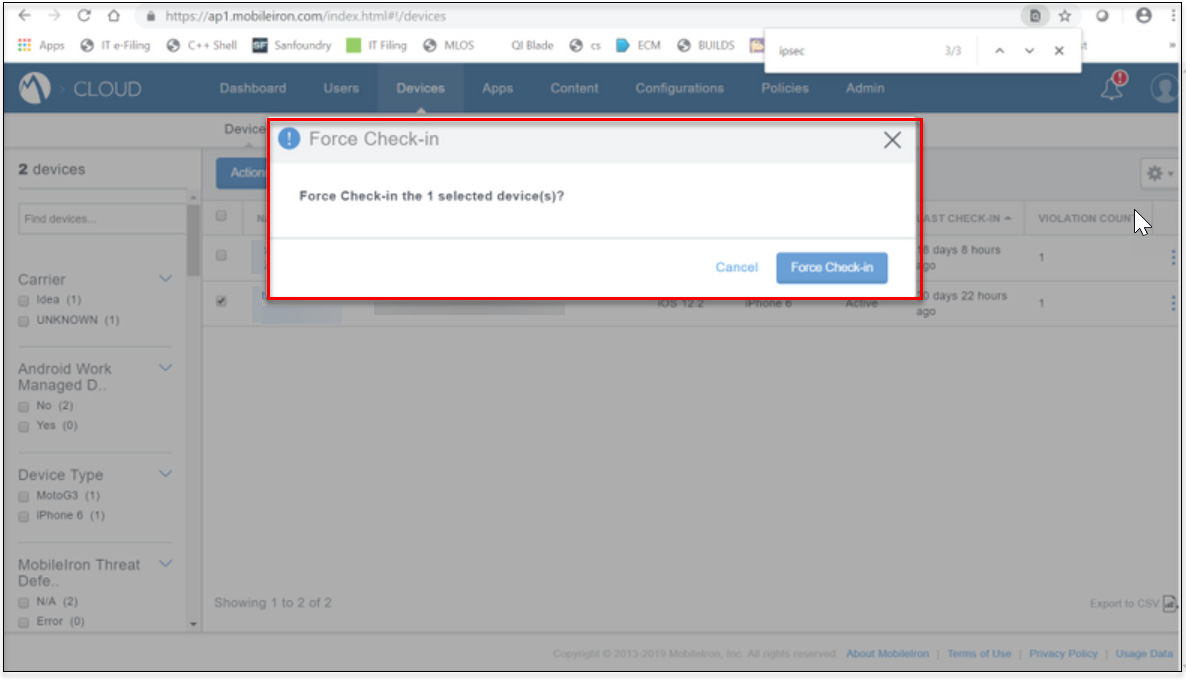
- For Force Check-in, go to Devices tab → click on Actions → select Force Check-in
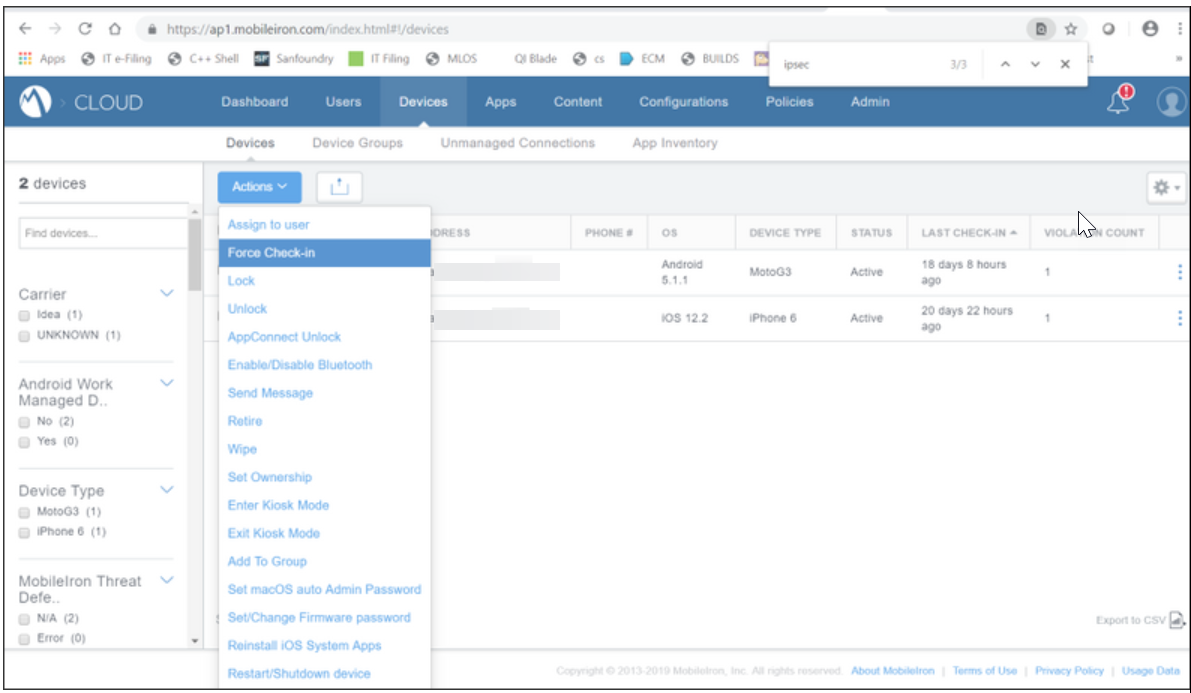
This opens a new window with the " Force Check-in" button. Click on that button, then the configuration will be pushed immediately.
Check the Status of the Push
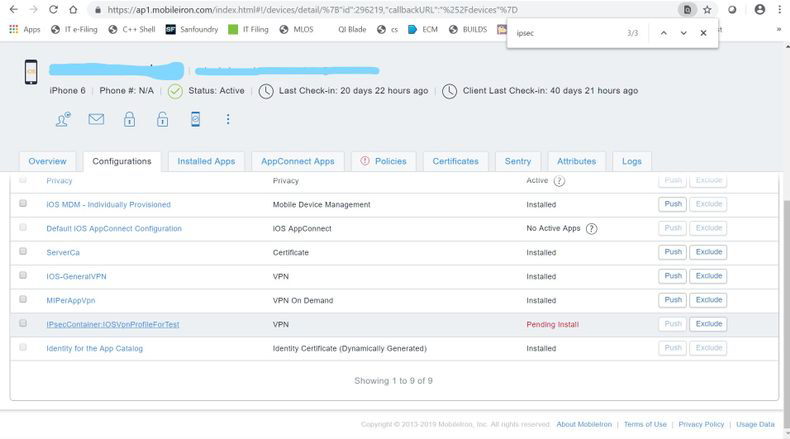
To check the pushed configuration status, Go to Devices tab, click on the registered device, and check the status of configuration.
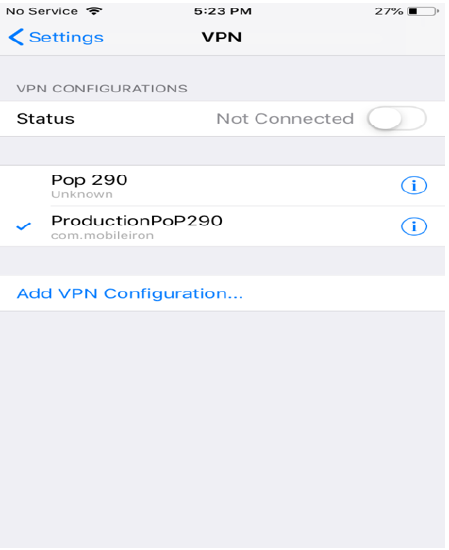
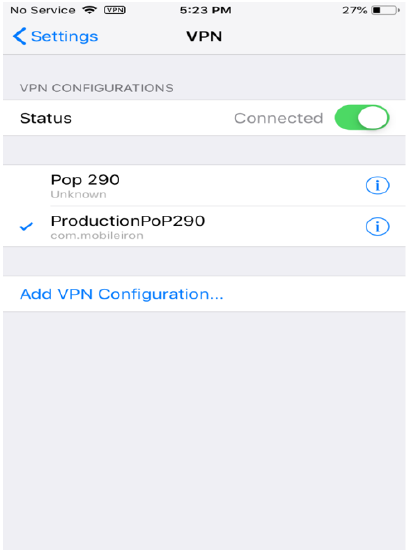
Verify the VPN Profile on your Device
Verify the distributed VPN profile in the IOS device (Settings → VPN):