Cloud Activity Controls with CAI
-
 Watch the visual story about Creating Cloud Access Policy for CAI
Watch the visual story about Creating Cloud Access Policy for CAI
| Limited Availability: Cloud App Isolation (CAI) is a Limited Availability feature. To enable CAI for Sanctioned SaaS apps in your tenant, contact Skyhigh Security Support. |
Remote Browser Isolation (RBI) provides malware protection for day-to-day browsing by preventing malware from accessing end users' devices. RBI enables an isolated environment for web browsing activity like a sandbox or virtual machine, in order to protect your device from any malware. For details, see About RBI.
Cloud Access Controls with Cloud App Isolation (CAI) allow frictionless onboarding of longtail SaaS applications and prevent data exfiltration by deploying security controls using cloud access control policies along with RBI.
Skyhigh CASB provides Cloud Access Controls with CAI to enable secure access to cloud applications from managed and unmanaged devices for your organization's users. You can apply the following CAI controls to access cloud applications from both managed and unmanaged devices:
- Block File Uploads/Downloads
- Restrict Copy/Paste/Print activities
- Allow all activities
How it Works?
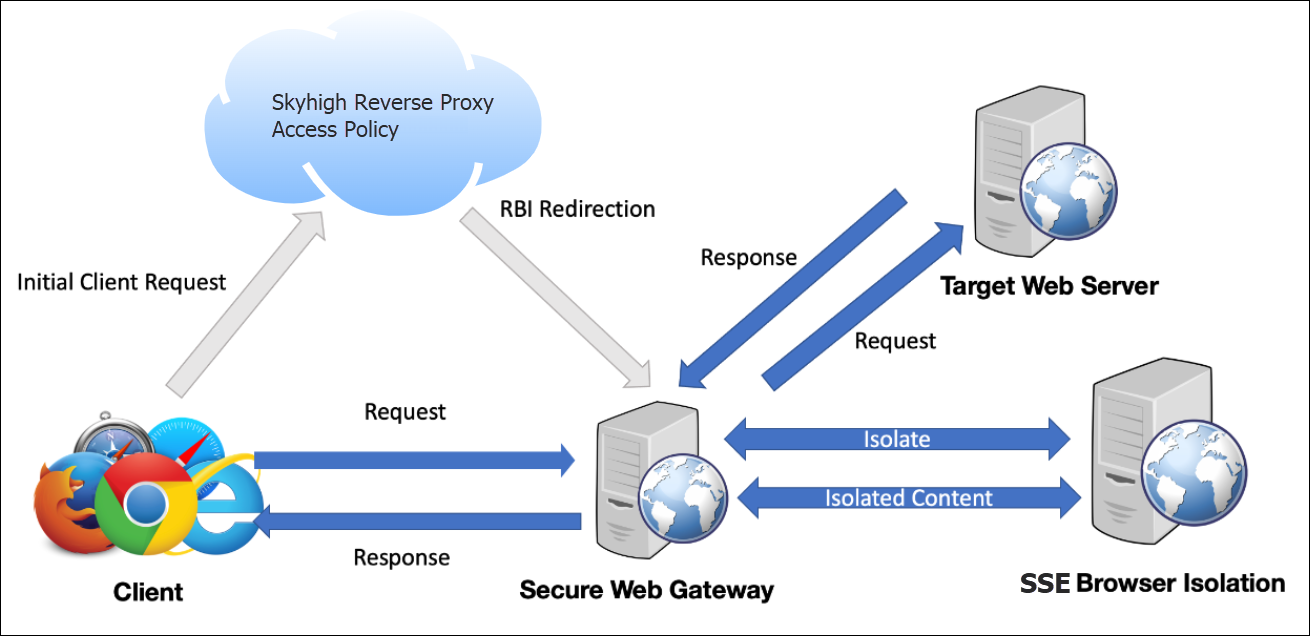
Users can access any cloud service via a Reverse Proxy (RP) vanity URL. During the SSO authentication (SAML 2.0), RP identifies whether the user device is managed or unmanaged based on the certificate present on the device (usually pushed by the organization's MDM system). If the device is identified as managed or unmanaged, the RP will initiate a secure RBI session for cloud application access based on the Cloud Access Policy (CAP).
RP supports the following CAI modes for secure access to cloud services from managed and unmanaged devices:
- Cloud App Isolation - Managed. Allows users from managed devices to access cloud services via RBI sessions.
- Cloud App Isolation - Unmanaged. Allows users from unmanaged devices to access cloud services via RBI sessions, and redirects users from managed devices to the cloud service.
- Cloud App Isolation - Redirect Managed, RBI Unmanaged. Redirects users from managed devices to the cloud service, and allows users from unmanaged devices to access cloud services via RBI sessions.
- Cloud App Isolation - RBI Managed, Block Unmanaged. Allows users from managed devices to access cloud services via RBI sessions, and blocks users from unmanaged devices to cloud services.
While the user is accessing the cloud service/app in RBI mode, Cloud Access Control policies will get enforced automatically, such as Block Download of file, or Restrict Copy/Paste activities, as per the policies defined.
Prerequisites for CAI Deployment
Make sure you have the following prerequisites in place for Cloud App Isolation (CAI) deployment.
- SKU for Managed/Unmanaged Devices. To enable CAI in your tenant, you must have the Skyhigh Remote Browser Isolation (RBI) Advanced - AddOn SKU or Cloud App Isolation SKU (RP-RBI Managed) standalone SKU for both managed and unmanaged devices, or the Cloud App Isolation – Unmanaged AddOn SKU for unmanaged devices.
- Assign the SKU code to your tenant. Make sure you assign the SKU code 10135 (Skyhigh Remote Browser Isolation (RBI) Advanced - AddOn)), 10235 (Cloud App Isolation SKU (RP-RBI Managed)), or 10139 (Cloud App Isolation – Unmanaged AddOn) to your tenant. Contact Skyhigh Security Support to assign the SKU code to your tenant by providing your Skyhigh-Tenant ID and BPS-Tenant ID.
- SAML Integration. Make sure the target cloud service providers (CSPs) support SAML integration. For example, if your target CSP is Airtable, make sure that Airtable supports SAML integration.
- Sandbox/Test instance for CSP. You must create a sandbox/test instance of the target CSP, and select your PreProd/UAT Skyhigh tenant for integration.
- Enable CSP in Skyhigh CASB. Make sure you can manage the target CSP under the list of available CSPs in the Skyhigh dashboard. Otherwise, contact Skyhigh Security Support to add the CSP and manage the service.
- SSO (SAML) Integration. You must complete the SSO (SAML) integration between the identity provider (Ping/Okta/Azure AD) and the CSP. You can then manage the service via Skyhigh's dashboard for Reverse Proxy integration.
- SAML Integration for Reverse Proxy. You must complete the SAML integration for Reverse Proxy.
- When integrating SAML with Reverse Proxy, you must upload both the IDP and SP certificates. It is mandatory to upload both certificates during the integration process.
- Test SSO Login via Reverse Proxy. (Optional) You must validate that SSO login works via Reverse Proxy.
Create a Cloud Access Policy for CAI
Use the Cloud Access Policy to block or restrict certain actions performed on managed and unmanaged devices. Let's say, you are accessing the Salesforce application from a managed device and want to restrict uploads and downloads. You must create a cloud access policy and apply the necessary conditions and actions to achieve the outcome.
NOTES
- You must create two separate cloud access policies with the Cloud App Isolation - Managed and Cloud App Isolation - Unmanaged modes to apply RBI activity controls on both managed and unmanaged devices.
- If you create a policy for either managed/unmanaged devices, the policy is enforced as below:
- Cloud App Isolation - Managed. All activity controls configured in this policy are also applied to unmanaged devices.
- Cloud App Isolation - Unmanaged. All activity controls configured in this policy are applied to unmanaged devices. Cloud services can be accessed directly via managed devices without any activity controls applied.
To create a Cloud Access Policy for CAI:
- Log in to Skyhigh CASB dashboard.
- Go to Policy > Access Control > Access Policies.
- Click Create Policy.
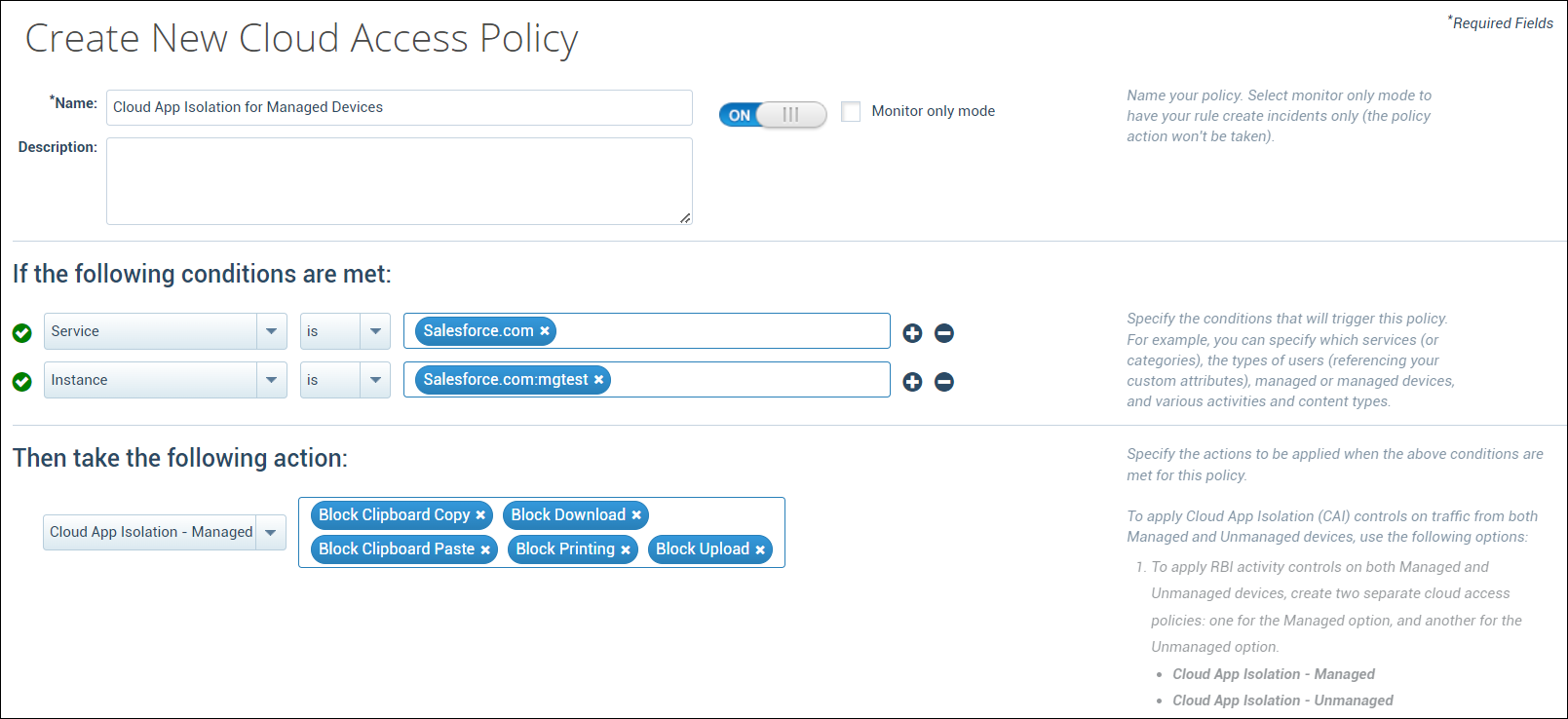
- On the Create New Cloud Access Policy page, configure these:
- Name. Enter a name for your policy.
- Description. Add a description, if needed.
- Conditions. Policies are built around conditions (rules) and actions. Conditions are used with IS or IS NOT arguments to define the specific situation when a policy should be enacted. You can create policies with the following conditions:
- Select the Service. Then enter the sanctioned service names.
- Select the Service. Then enter the sanctioned service names.
- Action. Actions determine the outcome when a policy is enacted.
- Select any one of the following CAI modes from the menu:
- Cloud App Isolation - Managed
- Cloud App Isolation - Unmanaged
- Cloud App Isolation - Redirect Managed, RBI Unmanaged
- Cloud App Isolation - RBI Managed, Block Unmanaged
- Select the activity controls to be enforced on the cloud service:
- Clipboard Copy
- Clipboard Paste
- Printing
- Upload
- Download
- Allow All (Select this if you do not want to apply any RBI activity controls.)
- Select any one of the following CAI modes from the menu:
- Click Save.
NOTE: Cloud applications cannot be accessed directly from unmanaged devices without restrictions.
If any CAP policies are violated, you can view the incidents on the Incidents > Policy Incidents page. For details, see Policy Incidents Page.