Configure SSL Tap with Network Data Loss Prevention (NDLP) Monitor
Overview
In the Skyhigh Security Web Gateway 7.7.1 release, you can now direct decrypted HTTPS traffic to a TAP interface on the Web Gateway appliance. From this interface, other devices, such as DLP solutions, IPS solutions and Advanced Threat Protection solutions can inspect the decrypted traffic for monitoring and analysis purposes. This document provides an example of how to configure the SSL TAP functionality on Web Gateway to send decrypted SSL traffic to a Skyhigh Security NDLP Monitor 9.3.4 system.
Reference Topology
An example topology used in this example is depicted below:
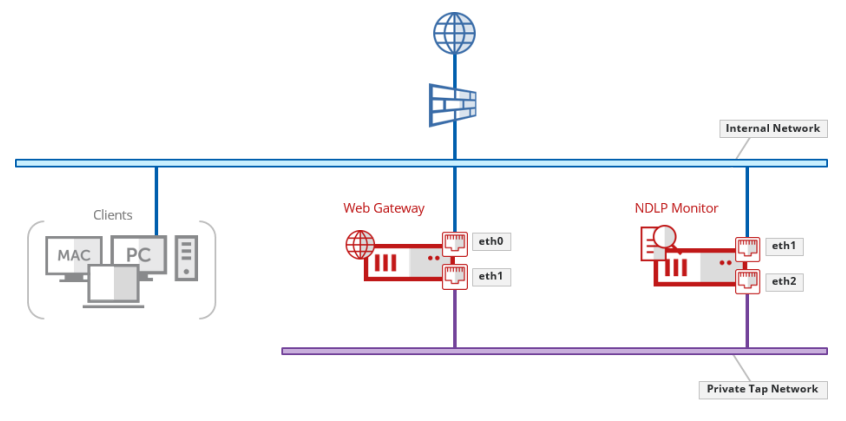
Web Gateway Configuration
Network Interface Configuration
In this example, the Web Gateway is configured as an Explicit Proxy, listening on port 9090 on the Internal Network using network interface eth0. The SSL TAP will be configured to direct the decrypted traffic to a second interface, eth1, that will be dedicated for use as a private TAP network.
When Web Gateway copies the decrypted packets to this interface we will configure the SSL TAP such that the packets retain their original Client IP Address, which enables the originator to be identified by NDLP Monitor. As a result, we don’t need to assign an IP address to this interface.
In the Web Gateway UI, navigate to Configuration -> Appliances -> Network Interfaces, select the eth1 interface, select the checkbox to enable the interface and then select Disable IPv4 under IP Settings in the IPv4 tab:
If the Web Gateway is configured to support IPv6 traffic, then repeat this step under the IPv6 tab.
SSL Tap Interface Configuration
The SSL Tap Interface configuration allows you to specify to which interface the decrypted packets are copied. More than one interface can be configured if required.
For each interface, you can configure the following settings:
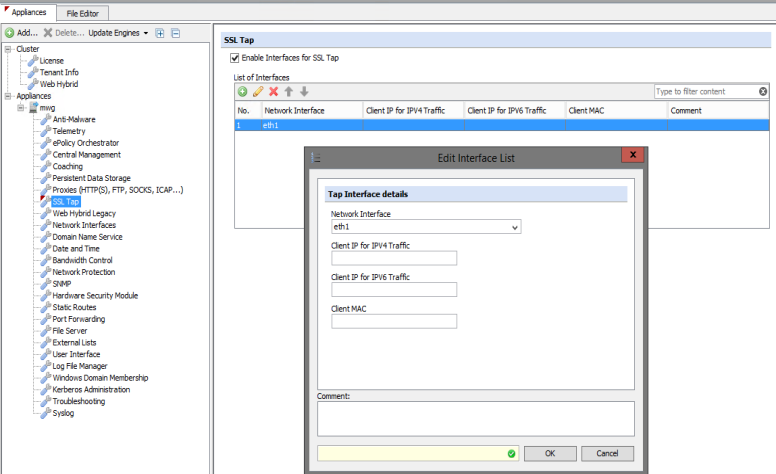
- Client IP for IPv4 Traffic: This specifies the IPv4 Address used as the Client IP Address when the decrypted packets are copied and sent on this interface. If not specified, then the original Client IP address in the HTTPS request received by the Web Gateway will be used (equivalent to the Web Gateway Client.IP property).
- Client IP for IPv6 Traffic: As above but for IPv6 traffic.
- Client MAC: This specifies the MAC Address used when the decrypted packets are copied and sent on this interface. If not specified, then the MAC address of the SSL TAP interface is used.
In this example, the SSL TAP will be configured such that the packets retain their original Client IP Address, which enables the originator to be identified by NDLP Monitor.
In the Web Gateway UI, navigate to Configuration > Appliances > SSL Tap, enable the SSL Tap functionality and add the eth1 interface, leaving the Client IP and MAC address fields blank:
In a Web Gateway cluster, this should be repeated on each Web Gateway appliance.
Enable SSL Tap Event
Once the SSL Tap Interface is configured, the actual copying of the decrypted traffic to the interface is enabled by calling the ‘Enable SSL Tap’ event in a rule.
Calling this event from a rule allows you to control exactly which request/responses are copied to the SSL Tap interface. For example, you might choose to call this Event from a Rule that uses one of more Criteria, such as a URL Destination, a URL Category or a specific group of Users.
In this example, the SSL TAP will be enabled for all SSL traffic.
In the Web Gateway UI, navigate to Policy -> Rule Sets -> SSL Scanner, and add the ‘Enable SSL Tap’ event to the Enable Content Inspection rule in the Content Inspection ruleset:
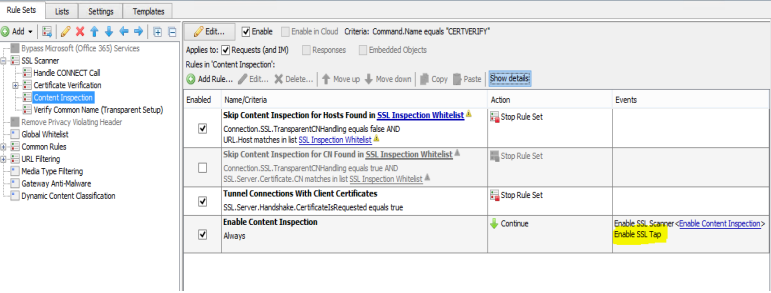
Note: SSL Content Inspection is a prerequisite for using the SSL Tap functionality.
Network DLP Monitor Configuration
Capture Interface Configuration
Each NDLP Monitor appliance has two capture ports: eth2 and eth3. In this example, eth2 is connected to the same private TAP network that was configured above.
Ordinarily, a NDLP Monitor port is designed to ‘sniff’ for traffic on the network and therefore requires that it be connected to a switch port that has Promiscuous mode enabled.
However, when the Web Gateway copies packets to the SSL Tap interface it sets the destination MAC address of the packets to the Broadcast MAC address (ff:ff:ff:ff:ff:ff) and as a result, the NDLP Monitor capture port will receive those packets directly without requiring Promiscuous mode to be enabled on the switch port.
Troubleshooting
Once the SSL Tap is configured, you can use the tcpdump packet capture utility on either the Web Gateway or on the NDLP Monitor appliance to confirm that packets are being copied to the SSL Tap interface.
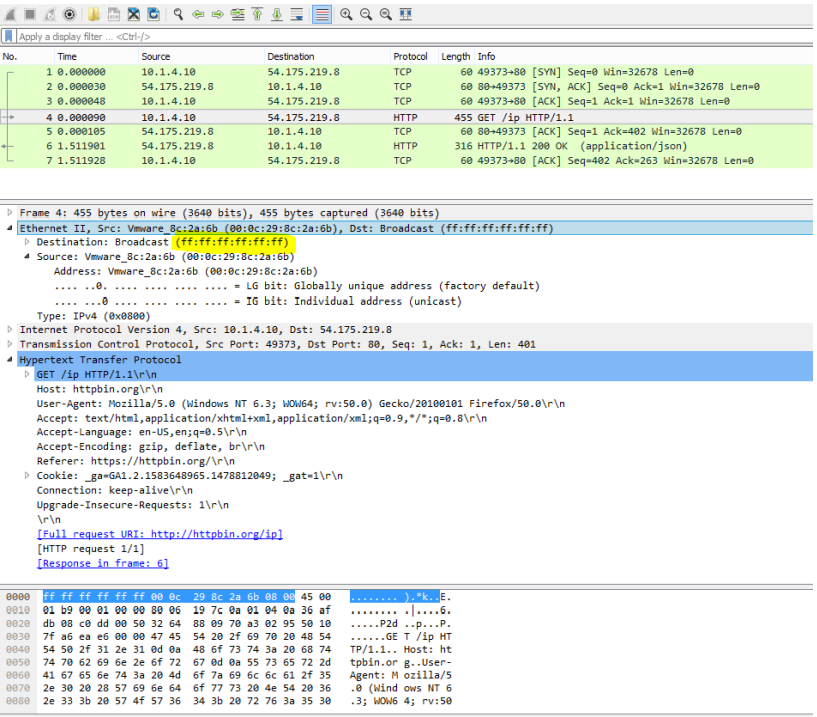
The Wireshark trace below shows an example of a Packet Capture run on the Private TAP Network showing the decrypted packets that have been copied for a HTTPS Request to https://httbin.org/ip
Note that that the Client IP address of the highlighted request is 10.1.4.10, which is the IP Address of the client workstation in this example and that the destination MAC address is the Broadcast Address.
DLP Incidents
Once traffic is being captured by NDLP Monitor, you can configure Policies and Rules to trigger Incidents when specific criteria are met, e.g. sensitive information being uploaded to specific websites.
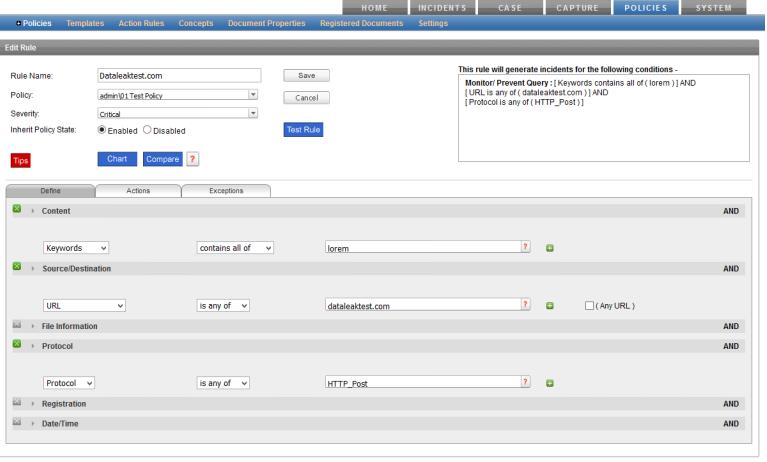
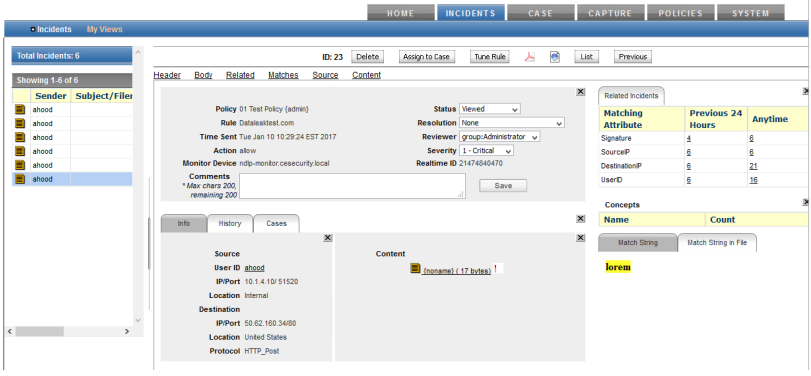
The screenshots below show an example Rule, which is configured to trigger an Incident when the keyword ‘lorem’ is detected in an HTTP_POST to the site dataleaktest.com and the resultant incident.
Optional Configuration
Skyhigh Security Logon Collector
By configuring the SSL Tap on Web Gateway to use the original Client IP when packets are copied to the SSL Tap interface, NDLP Monitor can identify the originating computer that sent the request. But, by default it has no direct knowledge of which user was logged into that computer at the time.
Skyhigh Security Logon Collector is designed to address this by collecting information from Active Directory and other sources, and mapping the IP Address of a computer back to the user who is logged onto it.
NDLP Monitor supports integration with Skyhigh Security Logon Collector and enables the User Information to be determined and displayed along with the Incident:
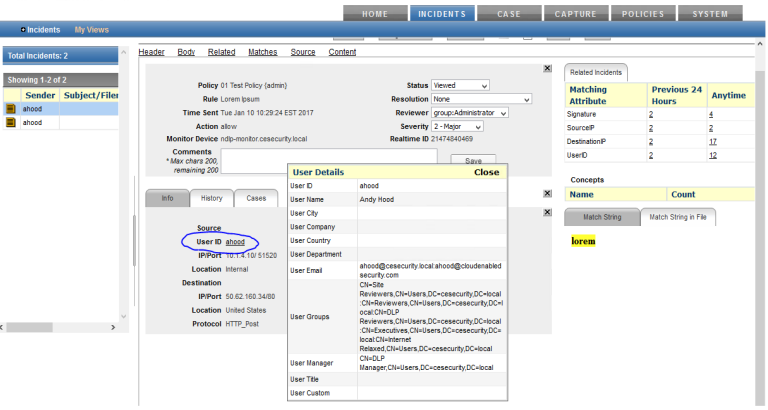
To configure Skyhigh Security Logon Collector, please refer to the Skyhigh Security Logon Collector Installation Guide and also follow the instructions in the Connect Skyhigh Security Logon Collector to Skyhigh Security DLP section of the Skyhigh Security Network DLP Product Guide. Failing to configure the necessary certificate authentication between the two will result in failure to retrieve the user details from Skyhigh Security Logon Collector.

