Configure reporting for Advanced Threat Defense in Content Security Reporter
Introduction
As of Web Gateway version 7.4.1, it is possible to create a rule set to generate log files that can be processed by CSR that includes information about traffic scanned by MATD. The Rule Set Library in version 7.4.1 does not include a rule set with a valid log format that can be processed by CSR. There is a Rule Set that exists in the library in that version with the name MATD Scanning Log for Content Security Reporter, but it is not complete as it is missing the required log file header and also does not have all of the required log fields. The purpose of this article is to provide details on setting up a rule set to generate log files that CSR can process to create reports on MATD detection data.
Log File Format
The recommended log fi le header for the MATD log format is: time_stamp "auth_user" src_ip status_code "req_line" "categories" "rep_level" "media_type" bytes_to_client bytes_from_client "user_agent" "virus_name" "block_res" "application_name" "matd_severity" "matd_server" "matd_taskid" "matd_hash" "filename" "matd_background_scan"
While not all of these fields are required, the above log format is recommended because it will provide the most comprehensive overview of web traffic that has been scanned by MATD. The MATD log format in CSR is an extension of the Web Gateway log format, so in addition to the existing requirements of the standard Web Gateway log file, the MATD parser requires the columns “matd_severity”, “matd_server”, “matd_taskid”, “matd_hash”, “filename”, and “matd_background_scan”. The parser will reject any MATD log files if any one of the required fields is missing. All of the MATD columns require surrounding quotes in the log fields (and header) except for “matd_severity”, which is valid with or without surrounding quotes.
Rule Set Configuration on MWG
The attached rule set can be imported into Web Gateway to create the recommended log file for use with CSR.
- Under Policy, select Log Handler in the bottom left and then right-click on the desired Log Handler. In the example below, the "Default" log handler is used. Select Add and then Rule Set from Library.
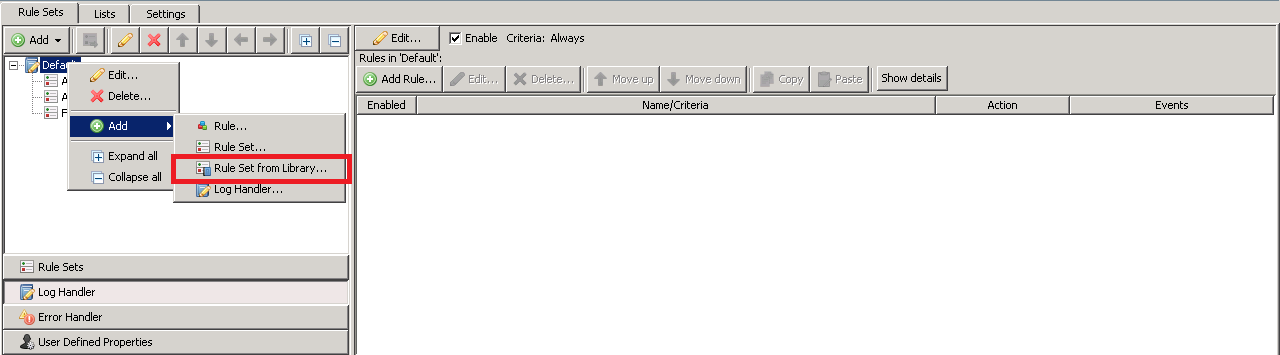
- Select Import from file and then choose the xml fi le that has been downloaded from this page.
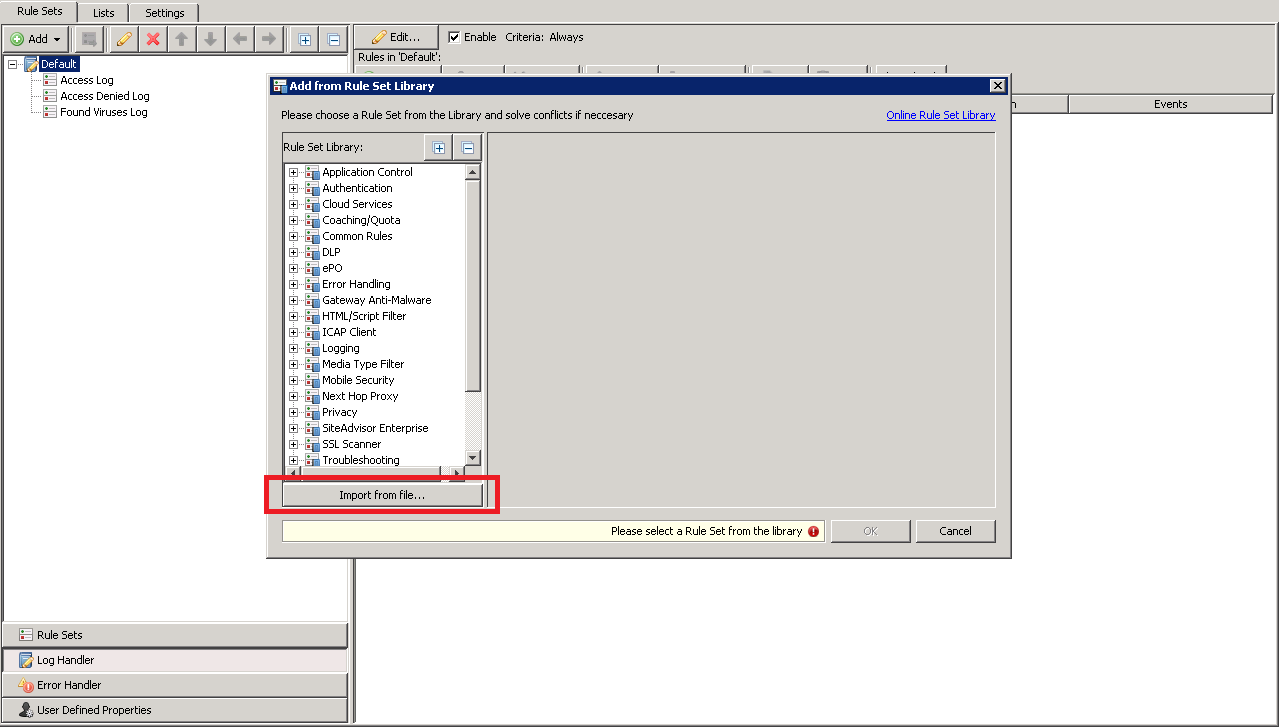
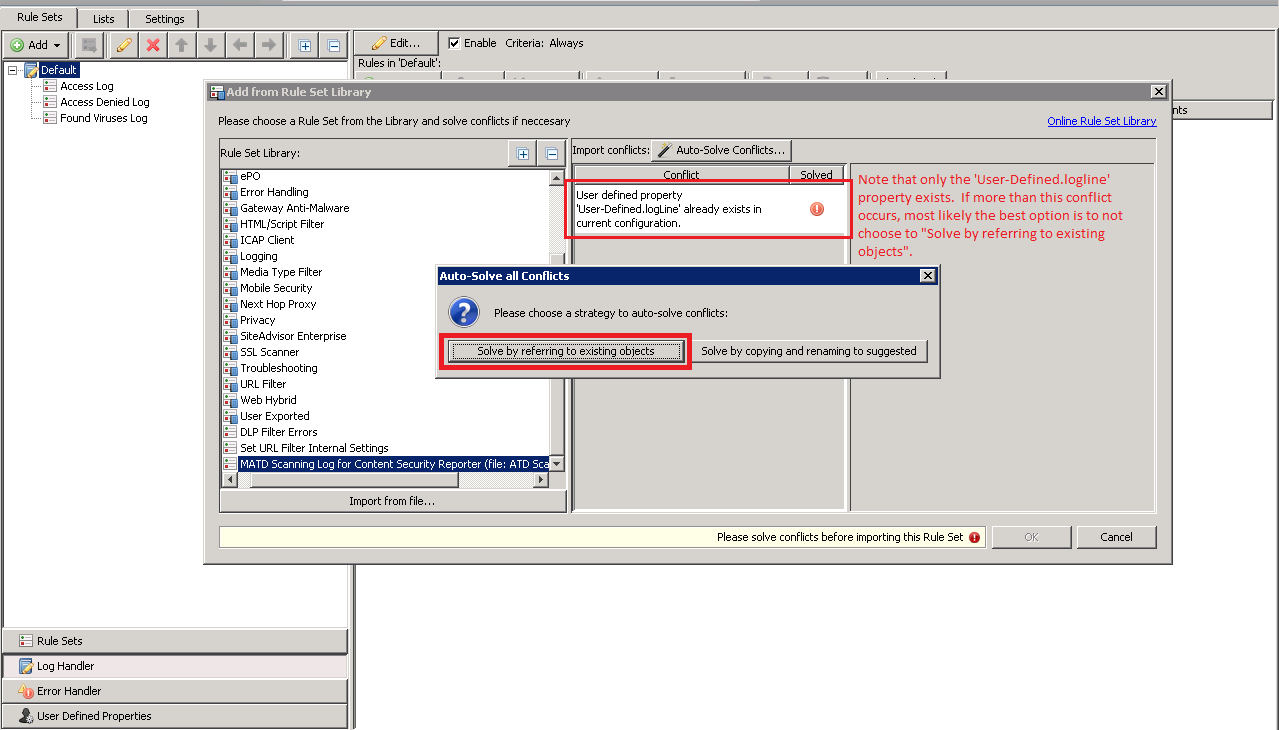
- If the only conflict that displays is that the 'User-Defined.logline' property, choose Solve by referring to existing objects. Otherwise if a "File System Logging Engine Setting" for "MATD Scanning Log" conflict occurs, it is necessary to either remove that settings object or you can choose to Solve by copying and renaming to suggested. It is possible the rule set will not import correctly if there is more than the one conflict shown below and the Solve by referring to existing objects option is chosen. Click OK to finish the import.
- The new rule set should be visible under the chosen Log Handler.
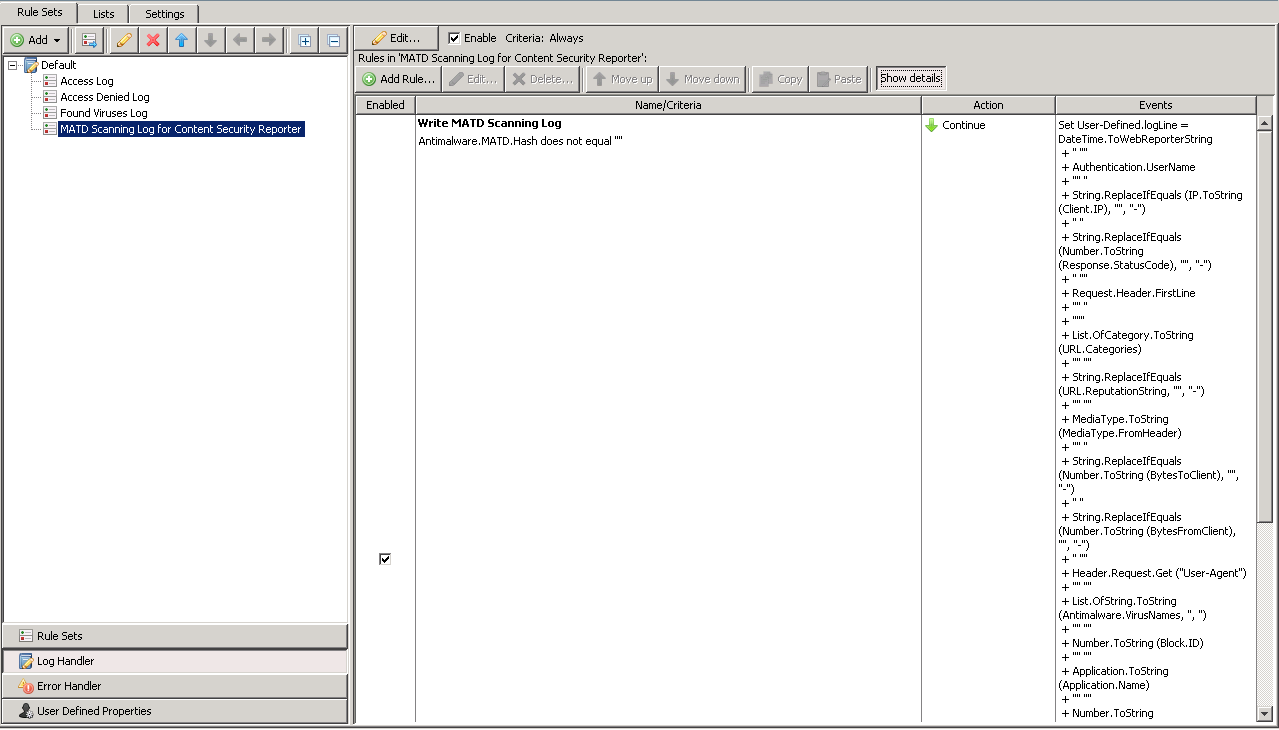
- The log file that will be created with this rule set can be found by going to Troubleshooting, expanding the desired MWG appliance on the left-hand side, choosing Log Files, and then double-clicking on atdscan.log in the list of log directories displayed.
Log File Pushing
For information on configuring Web Gateway to push the atdscan.log file to CSR for processing, follow the instructions in Configure log file pushing in SWG.
Example Log File Contents
#time_stamp "auth_user" src_ip status_code "req_line" "categories" "rep_level" "media_type" bytes_to_client bytes_from_client "user_agent" "virus_name" "block_res" "application_name" "matd_severity" "matd_server" "matd_taskid" "matd_hash" "filename" "matd_background_scan"
[11/Apr/2014:12:34:28 -0500] "" 172.18.2.250 403 "GET http://www.malicioussitename1.com/download/wajam_uninstall.exe HTTP/1.1" "Malicious Sites" "High Risk" "" 7453 184 "Wget/1.14 (linux-gnu)" "MATD: Gateway Anti-Malware: Artemis!8350BB40E623" "80" "" "5" "http://matdappliance1.local" "2794" "8350bb40e6235571ca2c9fdb038026f4" "wajam_uninstall.exe" "false"
[11/Apr/2014:12:43:10 -0500] "" 172.18.2.250 403 "GET http://www.malicioussitename2.com/ivo/minecraft18.exe HTTP/1.1" "Malicious Sites" "Minimal Risk" "" 7412 183 "Wget/1.14 (linux-gnu)" "MATD: Gateway Anti-Malware: Artemis!A6DFC0F1F373, MATD: GTI File Reputation: TYPE_UNKNOWN" "80" "" "5" "http://matdappliance2.local" "2797" "a6dfc0f1f37346222eb18b95a631ffc2" "minecraft18.exe" "false"

