Integrate with Advanced Threat Defense
Introduction
This article describes how to integrate Secure Web Gateway with Advanced Threat Defense (ATD). As a prerequisite, it is assumed that the ATD appliance has already been configured and is ready to accept files from Web Gateway.
Web Gateway Rule Configuration
To be able to deposit files into ATD for deeper analysis, you need the right rules placed in your filtering policy.
There are two main options for "how" Web Gateway can handle files that need to be scanned by ATD:
Option 1: Wait for the Result. This means Web Gateway will hold up the download of the file until ATD is done scanning it and only deliver it to the end user if the file has not been convicted as malicious. This can take some time, but it prevents what is called "patient 0", where an end user gets infected before the file has been deemed malicious.
Option 2: Offline Scanning. In this case Web Gateway will not hold up the download and the end user can immediately receive the file. ATD is doing the scan in the background and once completed further action can be taken (for example an email notification can be sent).
Option 1: Wait for the Result
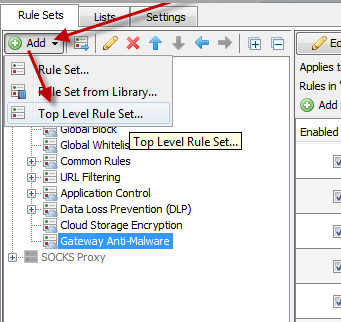
Open the Rule Set Library by navigating to "Policy" and then selecting "Add > Top Level Rule Set > Import rule set from Rule Set Library"
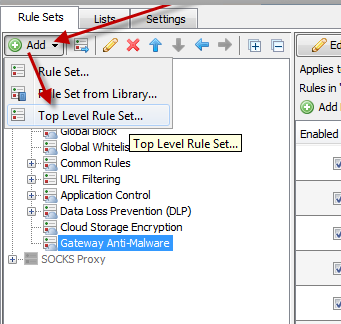
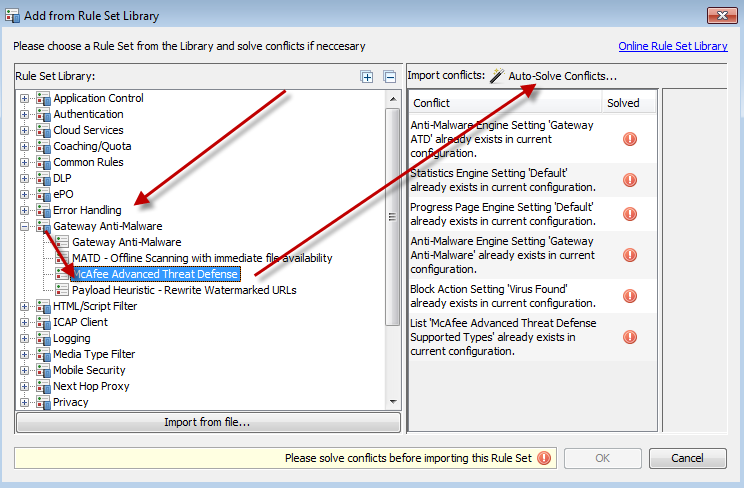
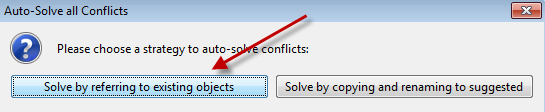
Select "Gateway Antimalware > Advanced Threat Defense" and also click "Auto-SolveConfl icts > Solve by referring to existing objects"
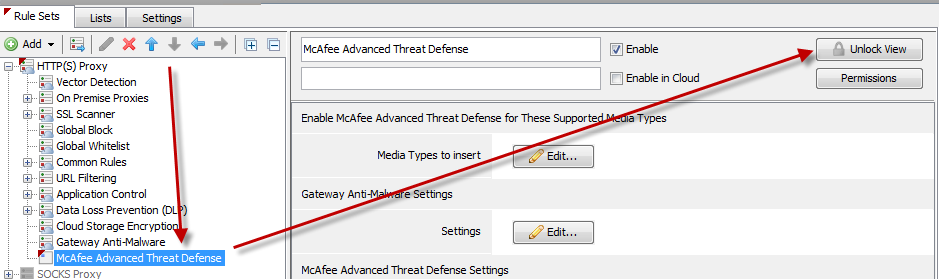
Place the new rule set directly after your existing "Gateway Anti-Malware" rule set andpress "Unlock View". Then proceed to the step "ATD Settings" further down in this article.
Option 2: Offline Scanning
Web Gateway is not waiting for ATD to finish the scan and the file is delivered immediately to the end user. Once the ATD scan is completed, further action (for example an email notification) can be taken.
Open the Rule Set Library by navigating to "Policy" and then selecting "Add > Top Level Rule Set > Import rule set from Rule Set Library"
Select "Gateway Antimalware > MATD - Offline Scanning with immediate fi le availability"and also click "Auto-Solve Conflicts > Solve by referring to existing objects"
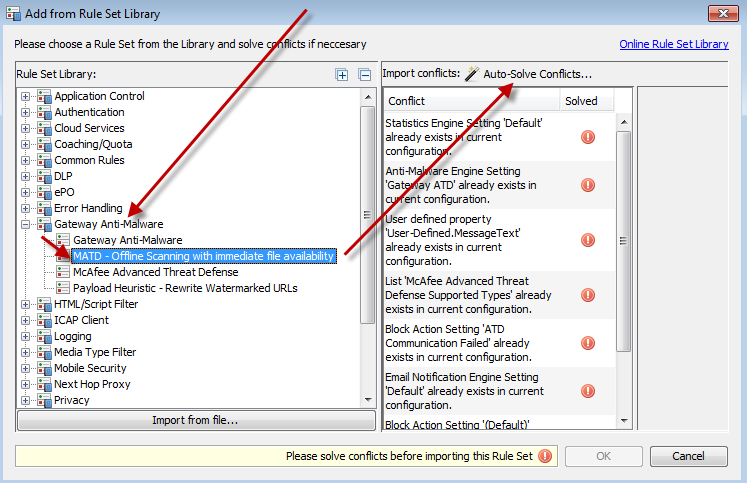
Two new rule sets have been imported. It is very important that you place them correctly in your policy tree!
Place the rule set "MATD - Init Offline Scan" directly after your existing "Gateway Anti-Malware" rule set.
Place the rule set "MATD - Handle Offline Scan" as the very first ruleset in your policy tree. It is especially important that this rule set comes before any authentication or whitelisting/blacklisting rules.
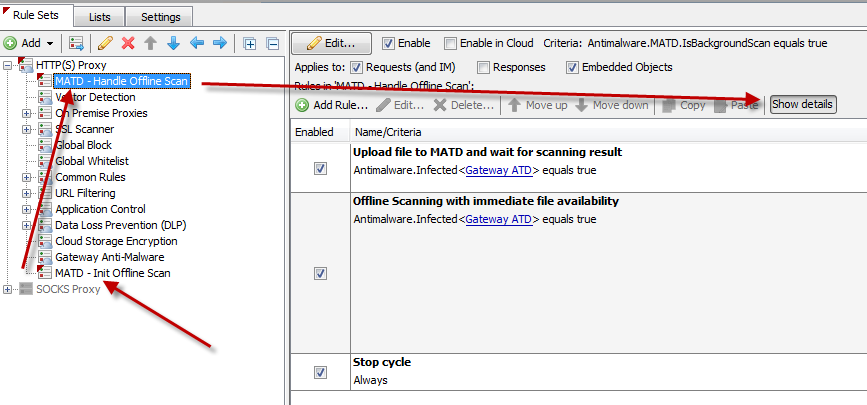
NOTE: The Offline scanning option has a default timeout of 5 seconds. That means, if Web Gateway cannot reach an ATD appliance to do the offline scanning within 5 seconds, it will call the Error Handler and by default, the end users would receive a block page. You can prevent this by configuring the Error Handler to "fail open".
ATD Settings
To define the settings needed for Web Gateway to communicate with ATD, you can either click on the "Show details" button and then select the "Gateway ATD" link or you can go through "Settings > Engines > Anti-Malware > Gateway ATD"
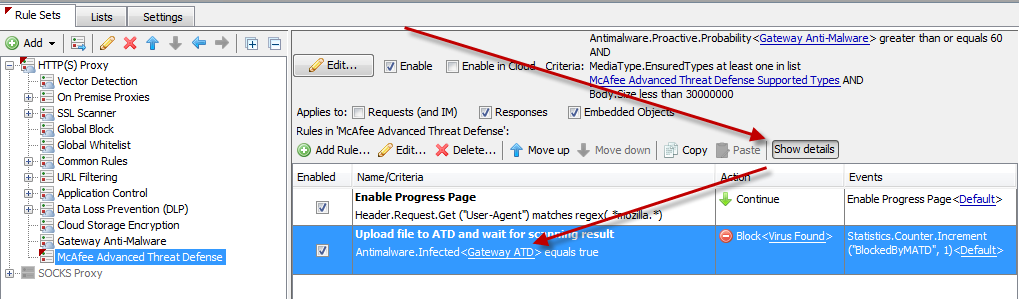
The basic setup for ATD only requires few changes:
- "User name" - Provide the username that Web Gateway will use to login to the ATD appliance. This username is defined on the AYD appliance and should have the "allow multiple logins" options checked.
- "Password" - Provide the password for the account above.
- "Server List" - Enter the IP address of your primary ATD appliance prefixed with "https://". Unless the UI port of your ATD appliance deviates from the default 443, it does not need to be entered.
All further settings are good default values and do not need to be adjusted in most cases.
Note that the option "Reuse Previous Detection...." is highly recommended to be enabled. This allows Web Gateway to re-use existing results for the same file (based on file hash) and can not only speed up the scanning process, but also prevent infection of additional end users from the same file.
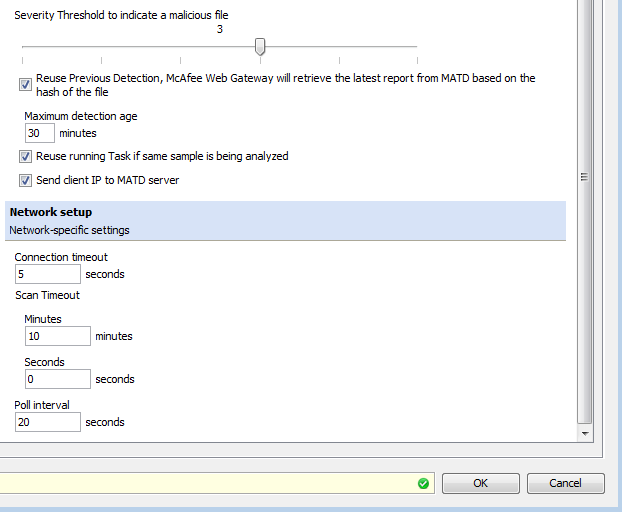
Once completed, simply "Save Changes" and your MWG appliance will start to deposit files into your ATD appliance.
Error Handling Rules
In case Web Gateway cannot communicate with the external ATD appliance or other issues arise, the Web Gateway rule engine will call the error handler just like it does for other features. For the ATD integration, default error handler rules are available in the rule set library.
Navigate to "Policy >> Error Handler >> Default >> Add >> Rule Set from Library"
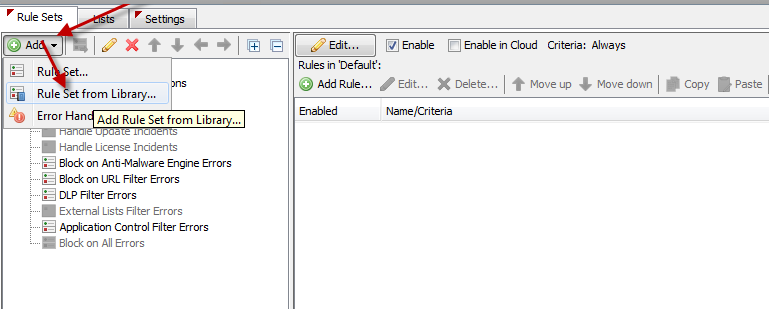
Select "Error Handling > Block on ATD Errors" and click on "Auto-Solve Conflicts > Solve by referring to existing objects"
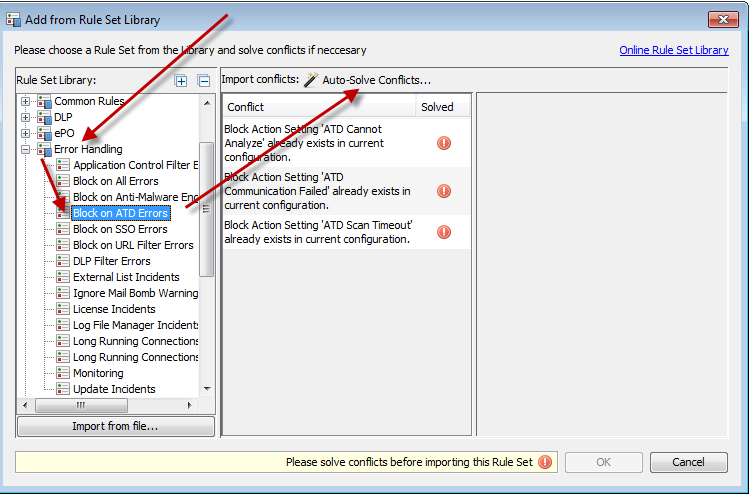
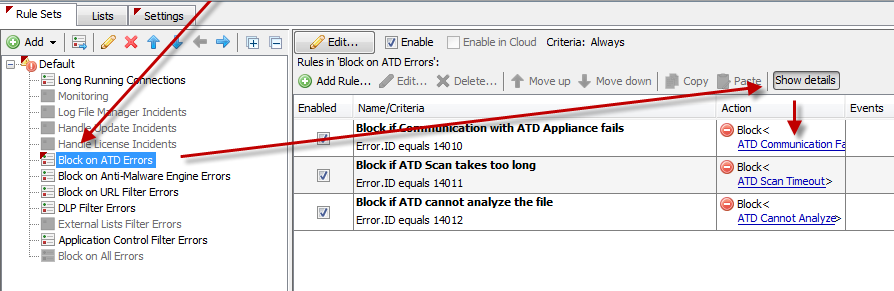
A good spot to place the new rule set is right above your existing Anti-Malware Engine error rules.
By expanding the rule through a click on "Show details" you can see what action is being taken under what error condition and you can adjust the actions as needed (for example to fail open instead of blocking)
Fine Tuning
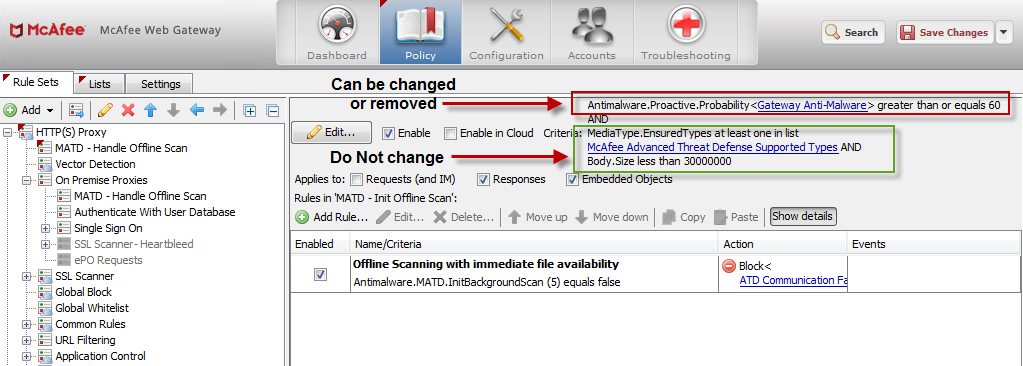
Not every file is being sent to the ATD appliance for analysis.
By default, only supported media types and files smaller then 30MB are being sent. We recommend that these settings stay in place.
In addition there is a default rule that only allows files that have a 60% or greater probability of being malicious (as rated by the Gateway Anti-Malware engine) to be sent over to ATD. Depending on your environment and the type of files your end users are downloading, this can result in very few or very many files being sent to ATD. You can adjust this value or eliminate the condition all together depending on your needs.