Setup the Domain Controller
Install "Support Tools"
Install the Microsoft package for support tools which includes ktpass which is required to generate the keytab files.
- For Server 2003: http://www.microsoft.com/download/en...ng=en&id=15326
- For Server 2008, it should come installed by default.
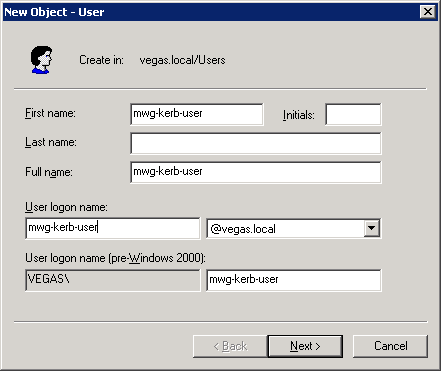
Create the user in Active Directory
To start, you must first create a user in AD. This user will later be associated with your keytab within a later step. Make sure the account has the following items enabled:
- The user cannot change the password
- The password never expire
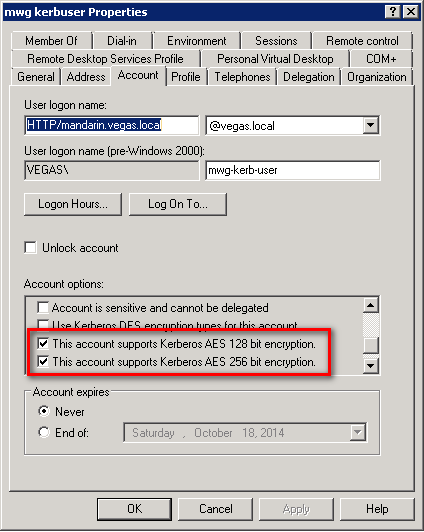
Higher encryption methods
On the user account you will want to enable the options for support of AES128 or AES256 for Kerberos Authentication:
Generate the keytab
Once the user is created, we need to generate a keytab based on that user.
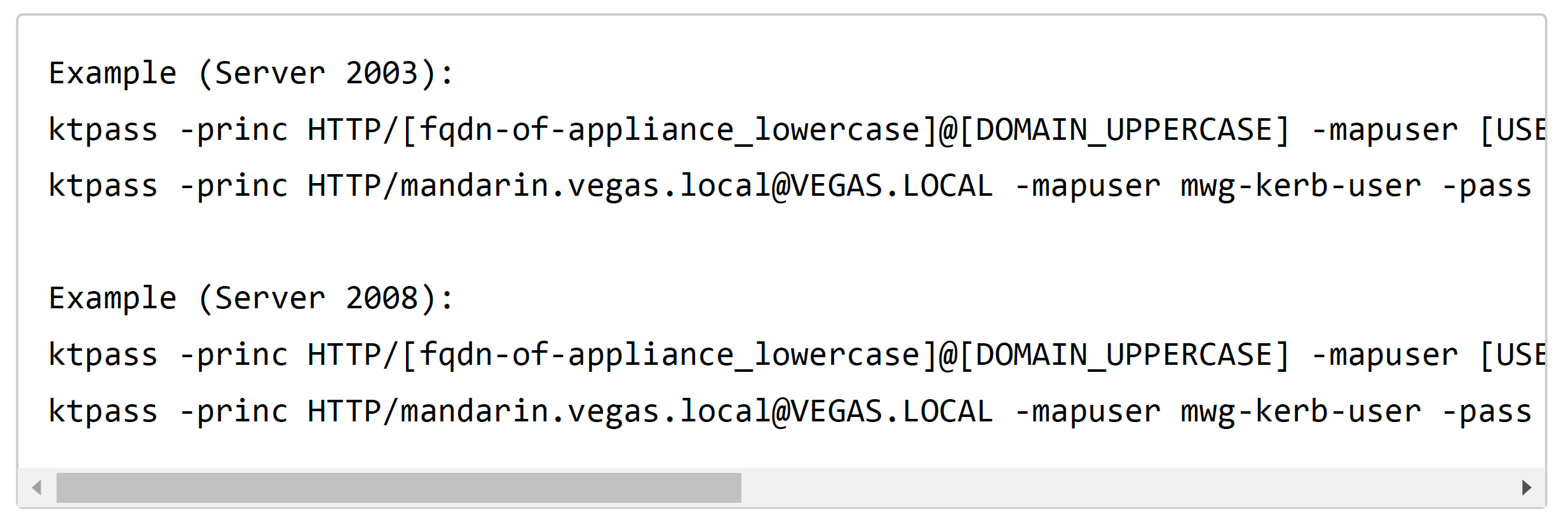
Syntax
The syntax can vary based on security restrictions within your domain, and based onyour domain controller type (2003/2008).
Possible -crypto:
- DES-CBC-CRC is used for compatibility.
- DES-CBC-MD5 adheres more closely to the MIT implementation and is used for compatibility (default on 2003).
- RC4-HMAC-NT employs 128-bit encryption.
- AES256-SHA1 employs AES256-CTS-HMAC-SHA1-96 encryption.
- AES128-SHA1 employs AES128-CTS-HMAC-SHA1-96 encryption.
- All states that all supported cryptographic types can be used (recommended on 2008).
Possible -ptype:
- KRB5_NT_PRINCIPAL is the general principal type (recommended).
- KRB5_NT_SRV_INST is the user service instance.
- KRB5_NT_SRV_HST is the host service instance.
Keytab generation output
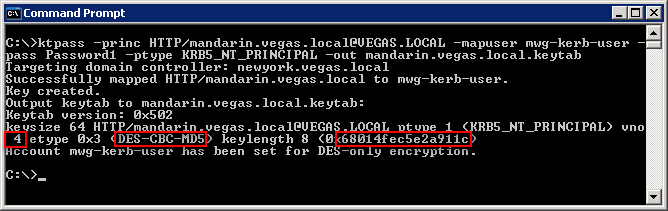
When generating the keytab, it will output important information that you will need to take note of for later steps (mapping additional SPNs). Please see the text highlighted in RED.
- Output from Windows 2003 Server
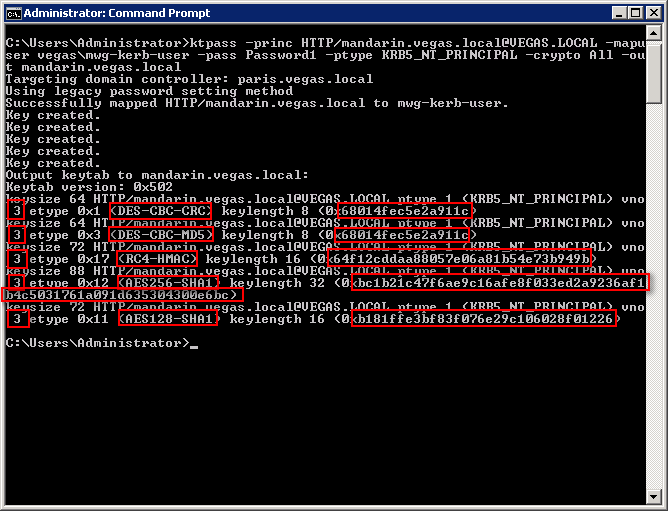
- Output from Windows 2008 Server
In Windows 2008, there will be much more output to the screen. This is because -crypto All was specified so all supported methods will be output.
Map multiple SPNs to one user/keytab(optional)
Why it's important
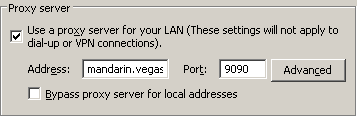
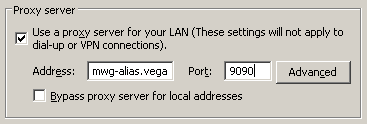
If you have your clients pointed to the Secure Web Gateway in different fashions, you must make sure that you have a keytab that includes each convention (FQDN / Alias):
Map multiple SPNs to the User (perfomed on AD server)
- As noted in the Keytab generation step, copy the command output from above, it will be used in commands on the Secure Web Gateway.
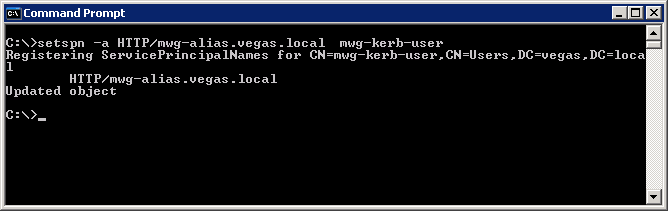
- Then use the setspn command to associate any new SPNs with the keytab user (mwg-kerb-user in this case).
# For HTTP
> setspn -a HTTP/mwg-alias.vegas.local mwg-kerb-user
# For SOCKS
> setspn -a RCMD/mandarin.vegas.local mwg-kerb-user
> setspn -a RCMD/mwg-alias.vegas.local mwg-kerb-user
Map multiple SPNs to the Keytab (perfomed on SWG OS)
7.3.x Note: As of version Secure Web Gateway 7.3, there is no need to add additional SPNs via the CLI. Secure Web Gateway's kerberos library was updated to a more modern approach, where if the client presents a ticket, the Secure Web Gateway will attempt to decrypt it using the available keys in the keytab. This reduces the need to add other SPNs to the keytab. You will still need to run the setspn commands from AD.
- Transfer the .keytab to the Secure Web Gateway filesystem (using a tool such as WinSCP).Note: This is not for importing, only for mapping/merging purposes.
- Login over SSH (using a tool such as putty).
- Install krb5-workstation tools, this includes the utility ktutil:
# yum install krb5-workstation - Move to the /usr/kerberos/sbin directory:
# cd /usr/kerberos/sbin (for older versions)
# cd /usr/bin
- Use ktutil, in order to add SPNs to the keytab generated above (in my example the.keytab is in the /root folder).
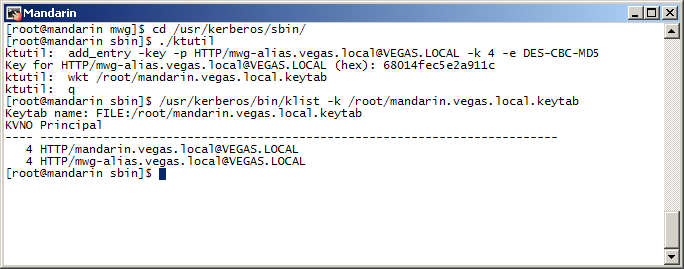
The commands used to add my alias:
# ./ktutil
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e DES-CBC-MD5
[ktutil will prompt for key (from keytab generation)]
wkt /root/mandarin.vegas.local.keytab
q
See below screenshot for example:
Server 2008: See below for commands needed when updating a keytab generated on Server 2008. Please note, the encryption names used from the keytab generation output may differ from the ktutil input (For example AES128-SHA1 = AES128-CTS andAES256-SHA1 = AES256-CTS).
# ./ktutil
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e DES-CBC-CRC
68014fec5e2a911c
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e DES-CBC-MD5
68014fec5e2a911c
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e RC4-HMAC
64f12cddaa88057e06a81b54e73b949b
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e AES256-CTS
bc1b21c47f6ae9c16afe8f033ed2a9236af1b4c5031761a091d635304300e6bc
add_entry -key -p HTTP/mwg-alias.vegas.local@VEGAS.LOCAL -k 4 -e AES128-CTS
b181ffe3bf83f076e29c106028f01226
wkt /root/mandarin.vegas.local.keytab
q
- Transfer the resulting .keytab file back to your workstation(/root/mandarin.vegas.local.keytab).
Multi-domain configuration (optional)
In the event that you have multiple domains, it may be necessary to create users and generate keytabs on both domains. You will then need to merge the keytab before importing into the Secure Web Gateway, this will allow the Secure Web Gateway to authenticate users in multiple domains.
Why it's important
If you have an environment with multiple domains the following would be good reasons to perform these steps:
Multiple domains with no trust relationship - If there is no trust relationship it is necessary to create a user and generate a keytab for each domain. You may also need to add any additional SPNs to the user/keytab, see scenario #2.
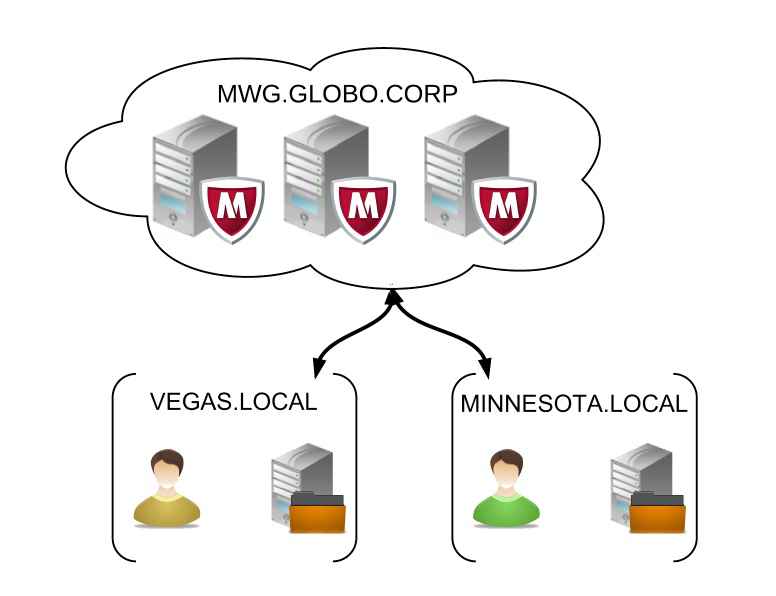
Scenario 1:
- Users proxy settings are set to "mwg.globo.corp".
- User created in AD in both domains VEGAS.LOCAL andMINNESOTA.LOCAL.
- Keytab contains two SPNs:HTTP/mwg.globo.corp@VEGAS.LOCAL
- HTTP/mwg.globo.corp@MINNESOTA.LOCAL
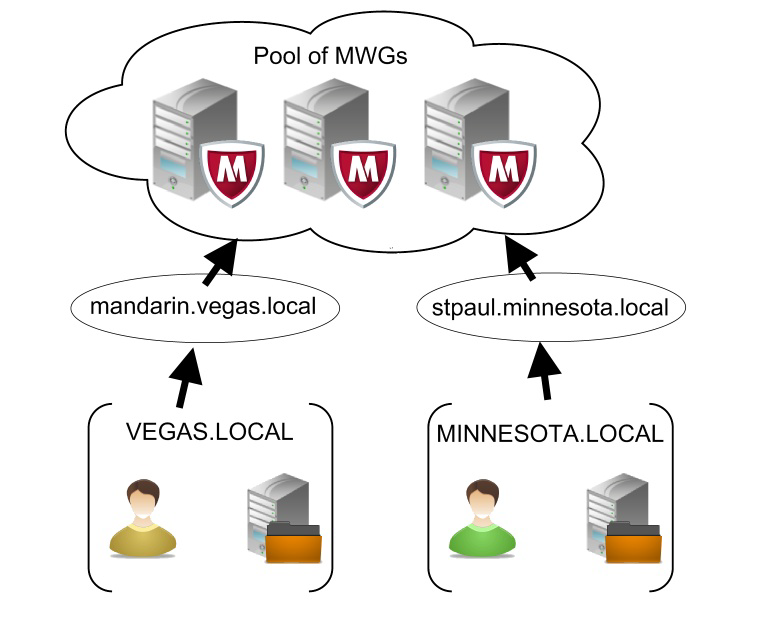
Scenario 2:
- Users proxy settings are set dependent on their domain. Users inVEGAS.LOCAL are pointed to "mandarin.vegas.local". Users inMINNESOTA.LOCAL are pointed to "stpaul.minnesota.local".
- User created in AD in both domains VEGAS.LOCAL andMINNESOTA.LOCAL. Each user account has been associated with its corresponding SPN.
- Keytab contains two SPNs:
Multiple domains with trust relationship, but domain controllers are indifferent locations - If the DC's have a trust relationship but the DCs are distrubted across the world, it is a good idea to have the local DC generate tickets for users local to that DC. In this scenario one would need to generate a keytab in each sub-domain and merge the keytabs.
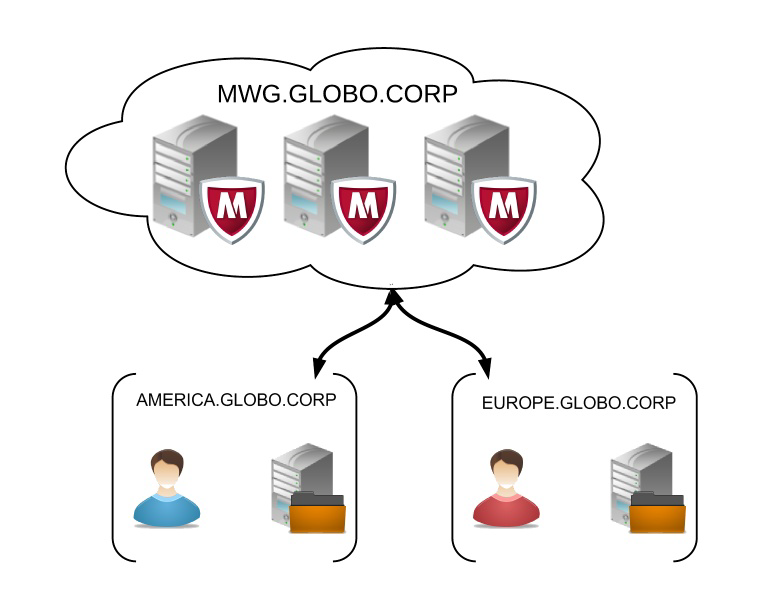
Perhaps your company has a number of regions with domain controllers in each location, the following would apply:
- Users proxy settings are set to "mwg.globo.corp".
- User created in AD in both domains EUROPE.GLOBO.CORP andAMERICA.GLOBO.CORP.
- Keytab contains two SPNs:
Merging keytabs
- Transfer both of the keytab files to the Secure Web Gateway using WinSCP or related tool (if it was not already done in Mapping SPN process).
- Install krb5-workstation tools (if it was not done already):
# yum install krb5-workstation -
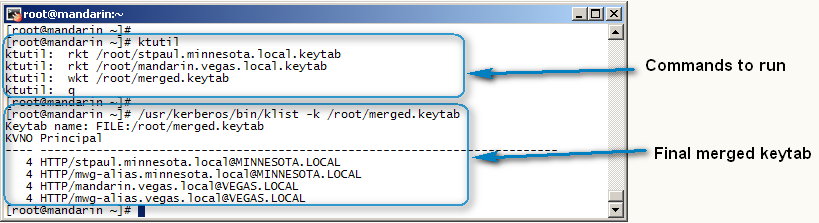
To merge the keytabs we will use the utility ktutil. The following commands willmerge stpaul.minnesota.local and mandarin.vegas.local, into a file called merged.keytab.
# ktutil
rkt /root/stpaul.minnesota.local.keytab
rkt /root/mandarin.vegas.local.keytab
wkt /root/merged.keytab
q
/usr/kerberos/bin/klist -k /root/merged.keytab
Conclusion
Now you should have one keytab that can be imported into the Secure Web Gateway UI.

