How CSR Works
Content Security Reporter (CSR) uses several elements that work together to provide reporting capabilities.
Content Security Reporter workflow
To successfully set up, use, and maintain CSR, understand the role for each component.
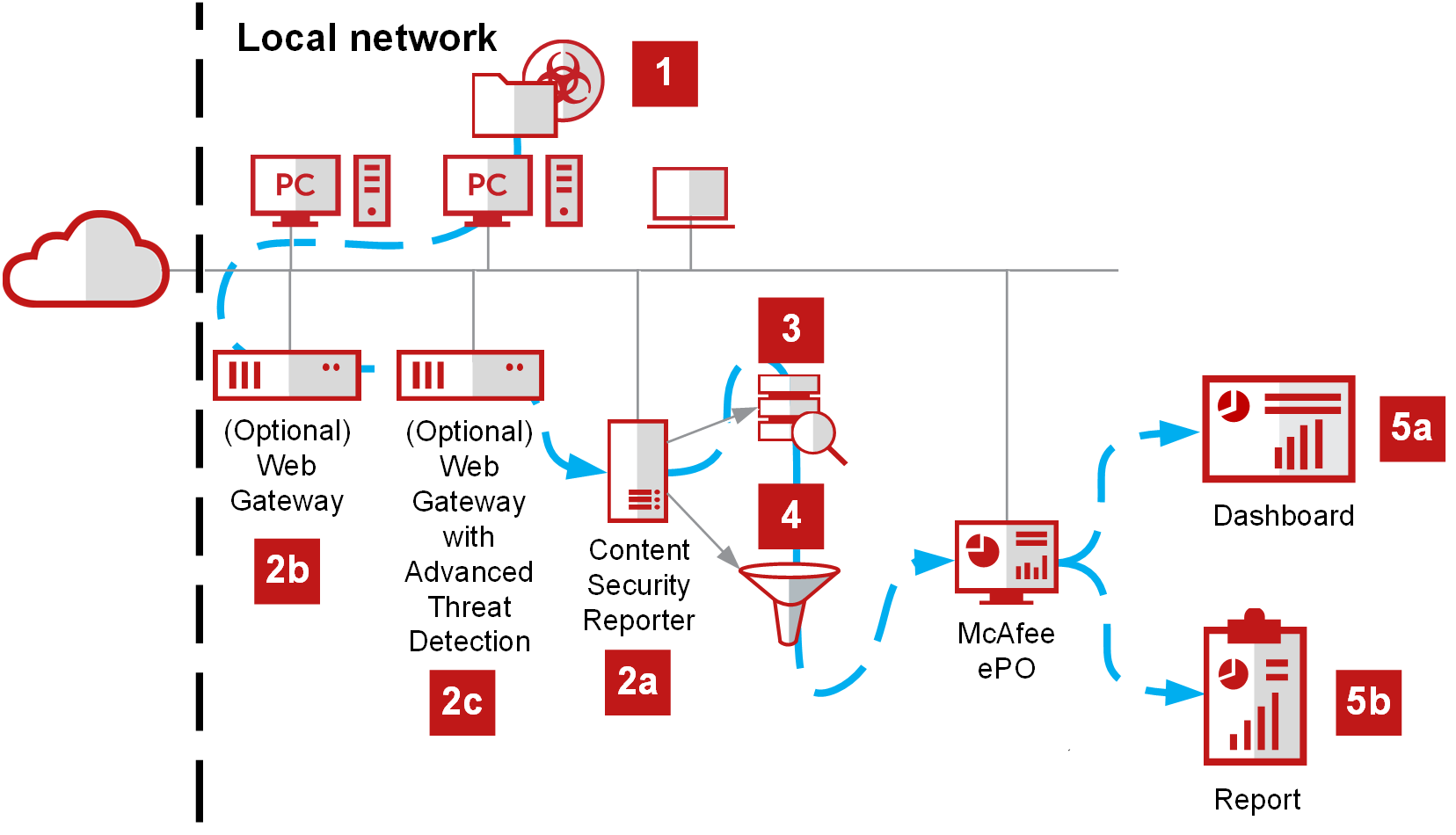
| Number | Description |
|---|---|
| 1 | On managed systems, an alert or event occurs. Depending on your configuration, the alert or event is logged to the CSR database. |
| 2a |
The CSR database saves the alert, authentication, email, and web data. |
| 2b |
Secure Web Gateway captures and logs the web event. It sends the logs to the CSR database. |
| 2c |
Advanced Threat Defense captures and logs the event. It sends the logs to the CSR database. |
| 3 | A CSR query retrieves data from its database and defines how it is displayed. |
| 4 | A CSR filter limits the data to specific users, websites, and threat reputations. The data is displayed in the Trellix ePO. |
| 5a |
Dashboard — Organizes your data in a customized view to provide detailed information for analysis. |
| 5b | Report — Combines queries, filters, and other elements into a PDF to provide detailed information for analysis. |

