VMware Workspace ONE UEM Integration Prerequisites
Mobile Device Management (MDM) integration allows Skyhigh CASB to interlace with the MDM solution to pull additional user information from the MDM database and validate it against the certificate on the user's device. Skyhigh CASB supports integration with Ivanti Neurons and VMware Workspace ONE UEM.
IMPORTANT: Only a single integration is supported (one VMware Workspace ONE UEM or one Ivanti Neurons). If you have multiple MDM deployments, we require multiple Skyhigh CASB tenants.
MDM Flow
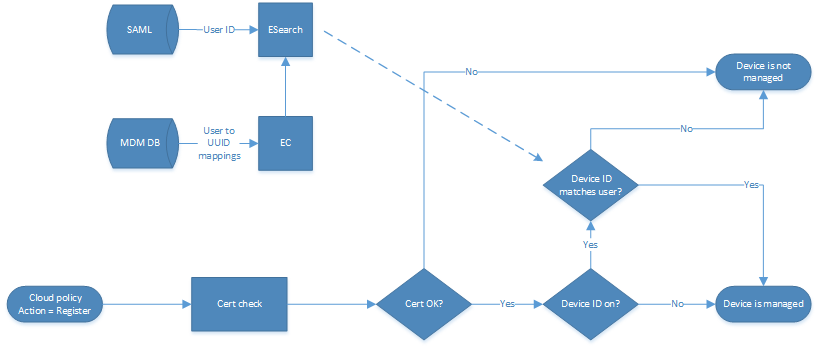
- The MDM system is deployed and configured to deploy device/user certificates on device enrollment.
NOTE: Depending on the MDM, this might be an internal function of the MDM (Mobile Iron), or it can be a requirement to integrate an external CA (VMware Workspace ONE UEM).
- When a device enrolls with the MDM, the MDM agent determines the device UUID, and this is captured in the certificate it is provided. In the Mobile Iron example below, the UUID is stored in the certificate SAN.
NOTE: For VMware Workspace ONE UEM, the UUID is stored in the DNS Name field in the certificate. This is how Skyhigh CASB determines if the device UUID matches the user and what is in the MDM database. This is achieved using a custom certificate template.
VMware Workspace ONE UEM Specific Prerequisites
To integrate Skyhigh CASB with VMware Workspace ONE UEM, make sure the following prerequisites are met.
Enterprise CA Integration
VMware Workspace ONE UEM requires a third-party CA server to act as the signing authority for the certificates deployed to user devices.
- Log in to the VMware Workspace ONE UEM Console.
- Go to Devices > Certificates > Certificate authorities and confirm there is a CA integration.
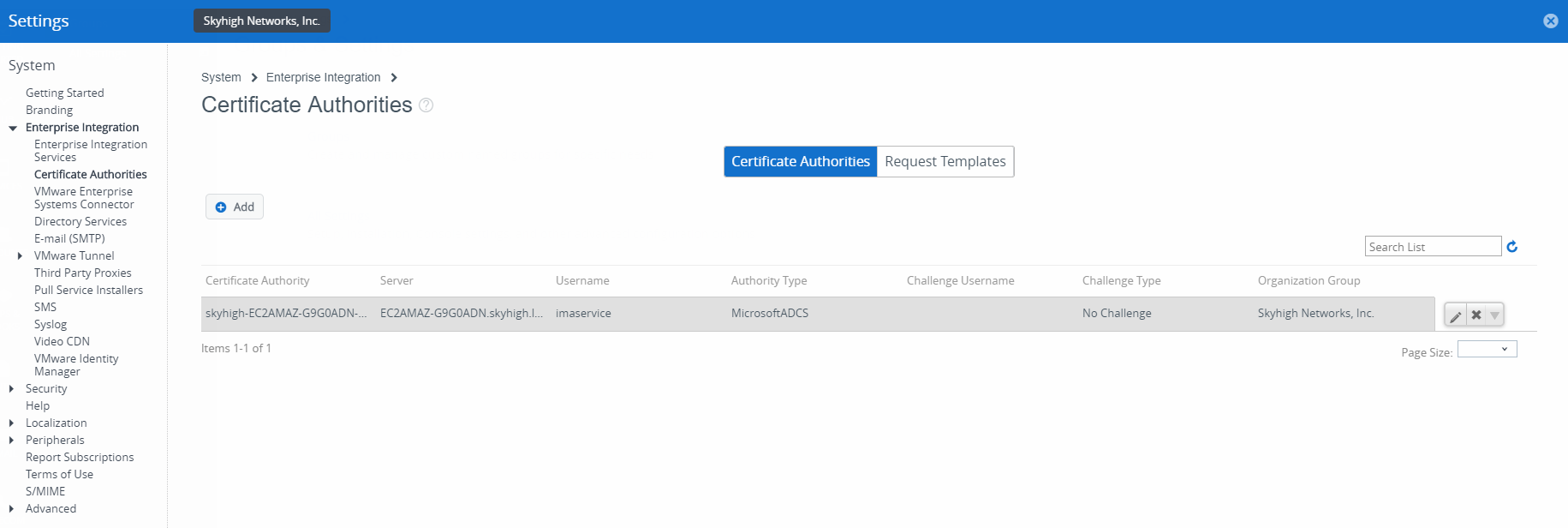
- Create a custom request template to integrate with your CA server. For more information, see the VMware Workspace ONE UEM CA Integration Guide for your chosen CA server platform.
Configure Device Profiles for Certificate-based Authentication
As devices are enrolled with VMware Workspace ONE UEM, they must be deployed with a certificate. The VMware Workspace ONE UEM agent takes care of this process, but, you must configure device profiles in the VMware Workspace ONE UEM console that are then attached to the device by the agent.
- In the VMware Workspace ONE UEM Console, go to Devices > Profiles and Resources > Profiles.
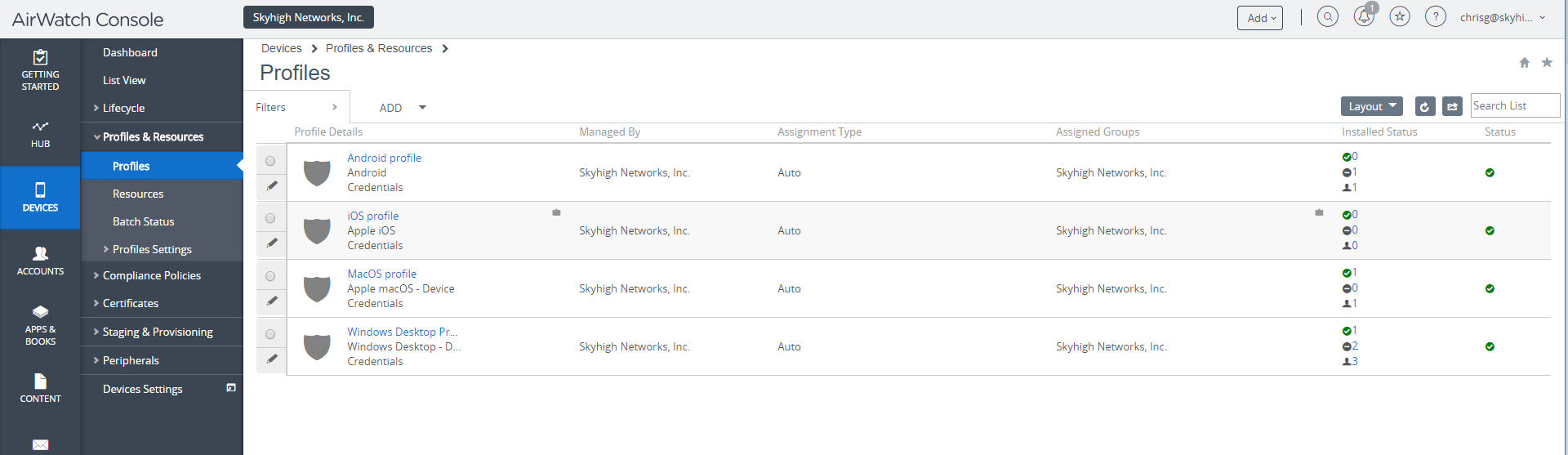
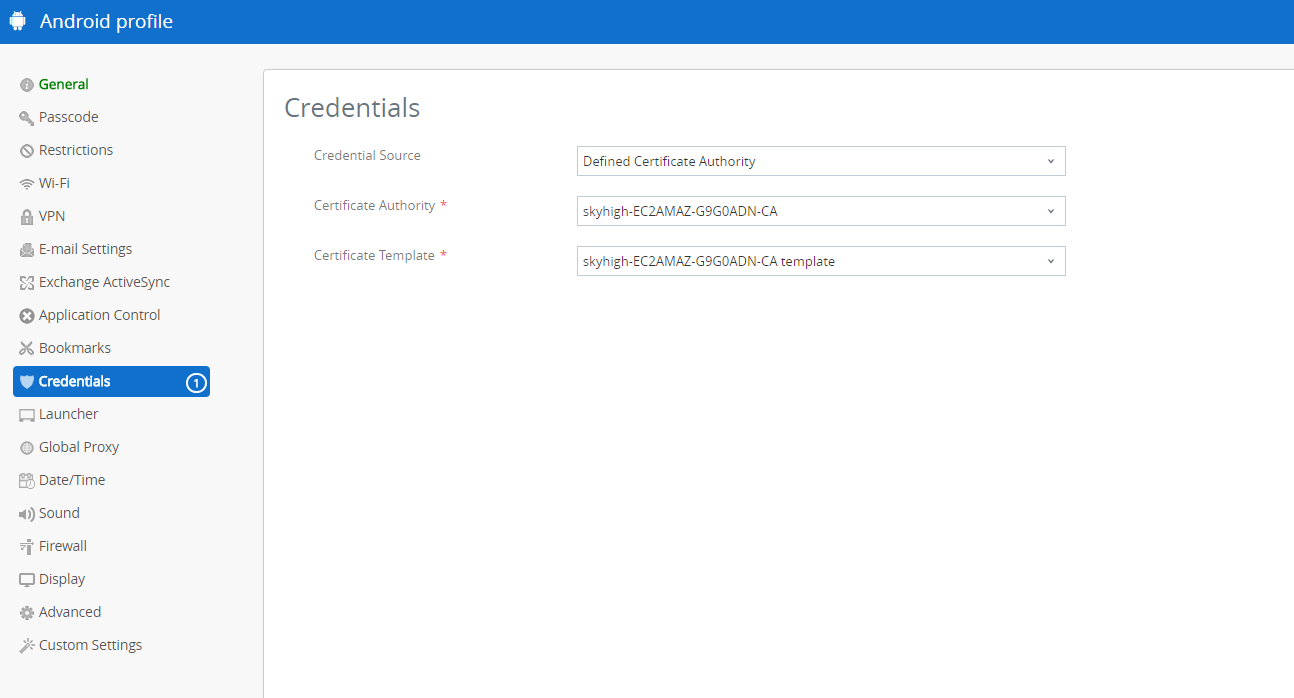
- Select any of the applicable profiles (that is, devices managed by Skyhigh CASB get this profile) and then select Credentials.
- Make sure the credential source has the Certificate Authority configured.
Verify That Managed Devices Receive the Certificate
Next, verify that the managed devices are receiving the CA-signed certificate. This is the certificate that is presented to Skyhigh CASB during the single sign-on process, and it must be present to pass the Cloud Access Policy.
Export the CA Public Certificate
The public key of the CA server must be exported. This is imported to Skyhigh CASB, which verifies the certificate provided by the managed device is signed by the authority CA.
To import the certificate:
- Log in to Skyhigh CASB.
- Go to Policy > Access Control > Device Management.
- Select the Device Certificates tab.
- For Upload Root Certificate, select Choose File and browse for your certificate file.
- For Populate Device ID, select All.
- Click Save Changes.

