Integrate Skyhigh CASB for Google Drive with Okta SSO
To integrate Skyhigh CASB for Google Workspace with Okta SSO, you must first configure SSO without the SAML proxy, then integrate the SAML proxy.
Prerequisites
Before you begin, you must have the following accounts:
- Okta account
- Google Workspace account with at least 1 user account (admin + 1 user).
Phase 1 - Configure SSO without SAML Proxy
Add Google Workspace to Okta
- Login to the Okta admin console and navigate to Applications > Applications then click on "Browse App Catalog".
- Search for and select Google Workspace and add the app.

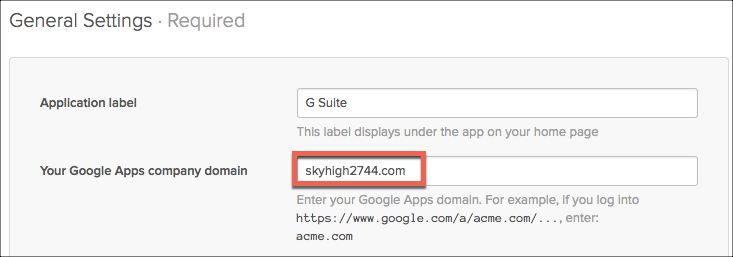
- Under General Settings, enter your public G Suite domain.
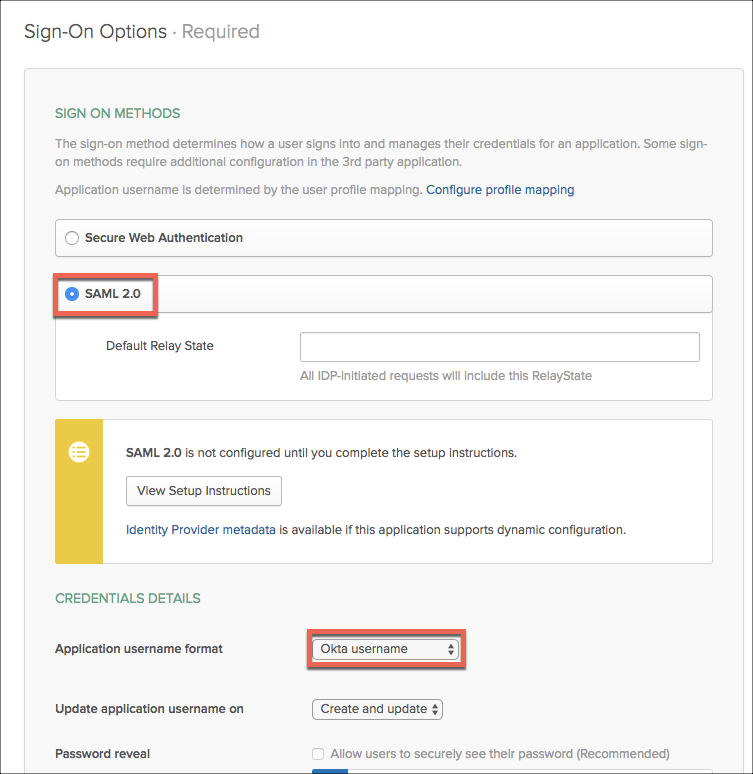
- Under Sign-On Options, select SAML 2.0 and Okta username.
Enable Provisioning for the Okta App
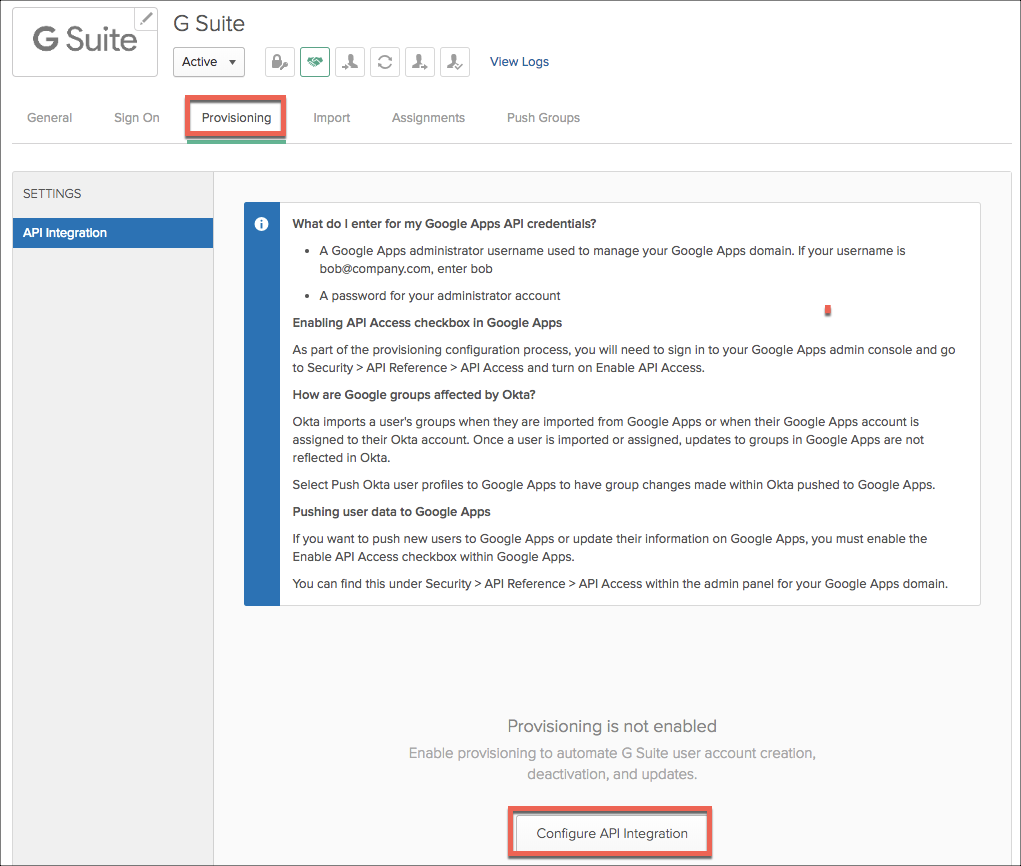
- Select the Provisioning tab, and Configure API Integration.
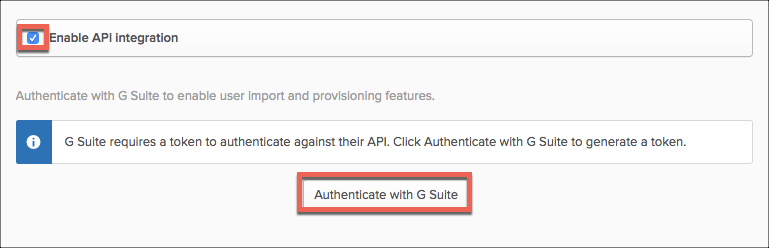
- Select Enable API integration and select Authenticate with GSuite.
- When asked to provide an account to authenticate, select the G Suite admin account and approve the access request.
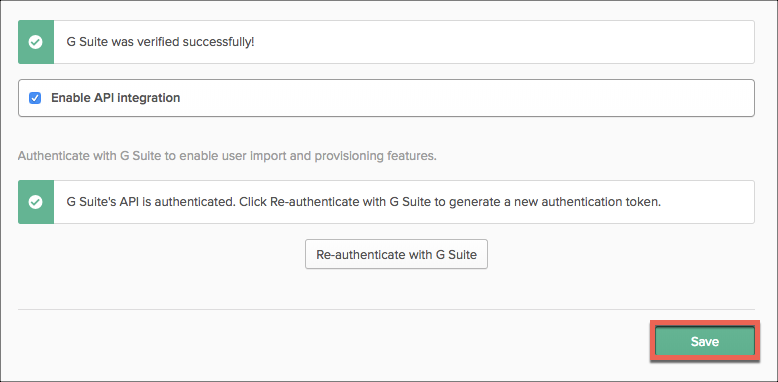
- Okta will report the GSuite connection is verified. Select Save.
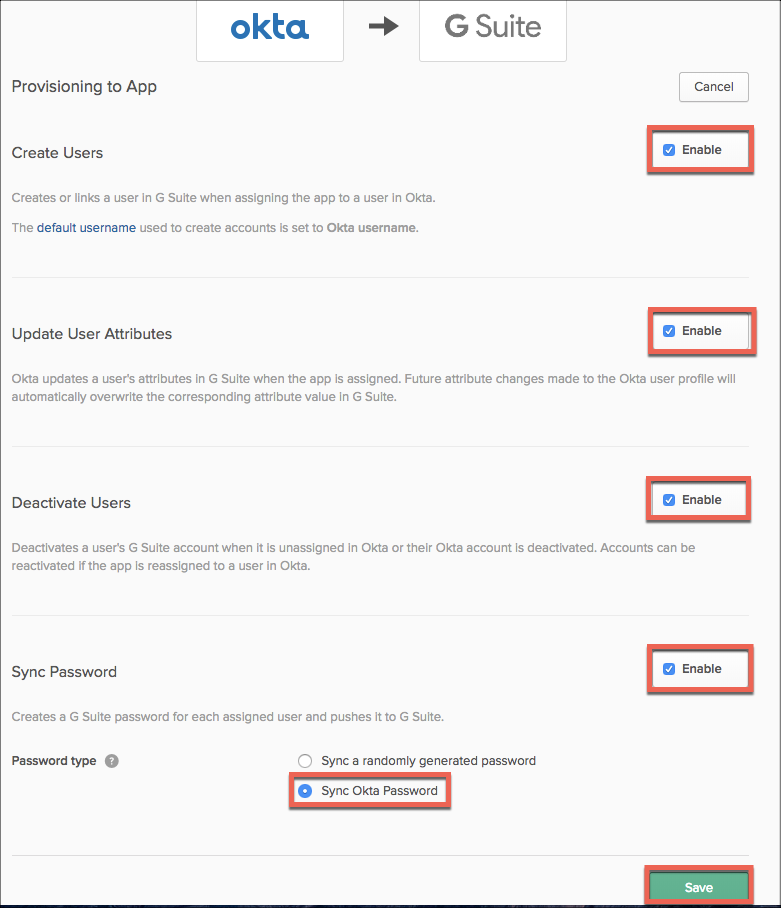
- Enable all the provisioning options, and select Sync Okta Password. Save the config.
- Select the Import tab, and Import Now.
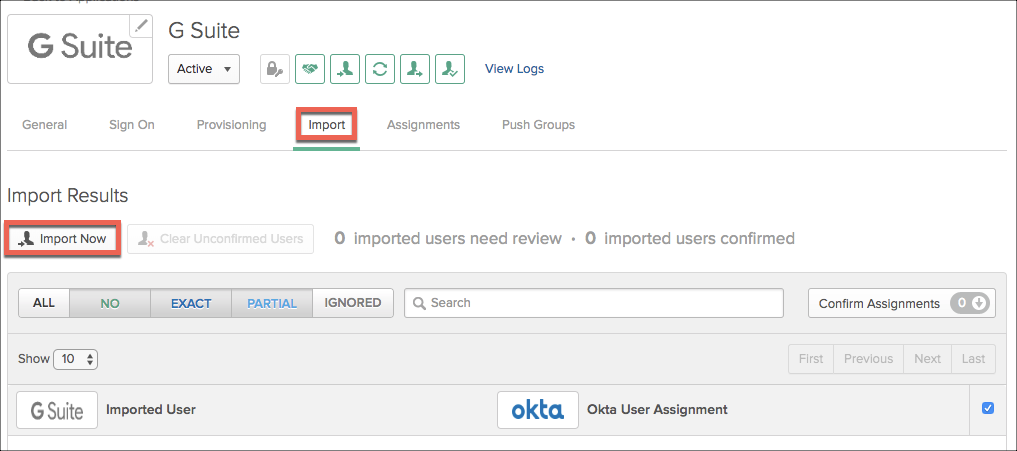
- If you have a similar user ID already in Okta (O365 user for example), Okta may suggest using this. Decline and make sure the import creates unique Okta users.
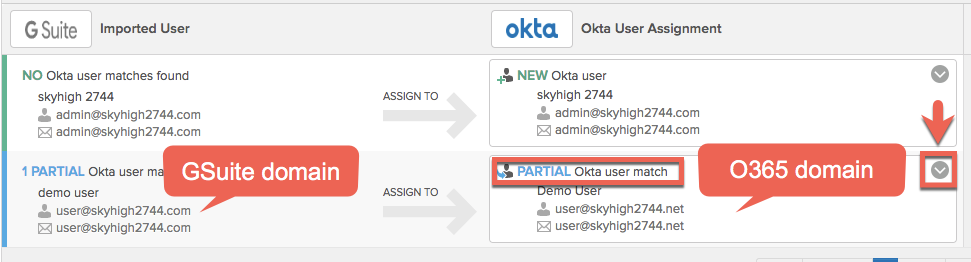
- Change it to the following.
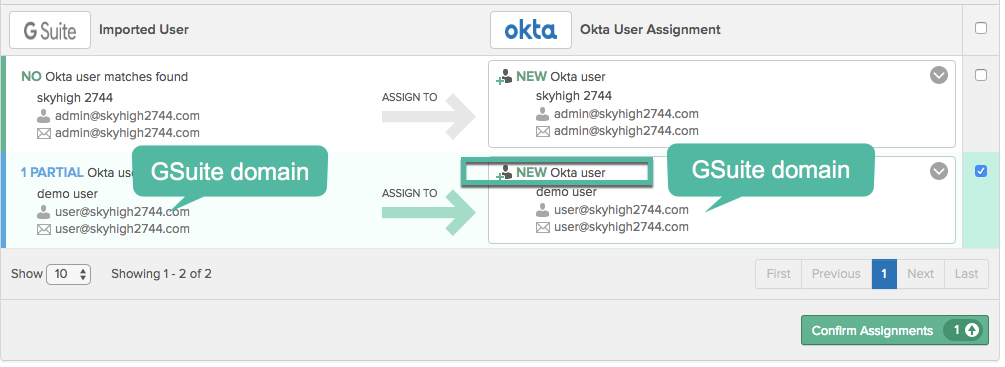
- Make sure only the user@ account is selected for import and then click Confirm Assignments.
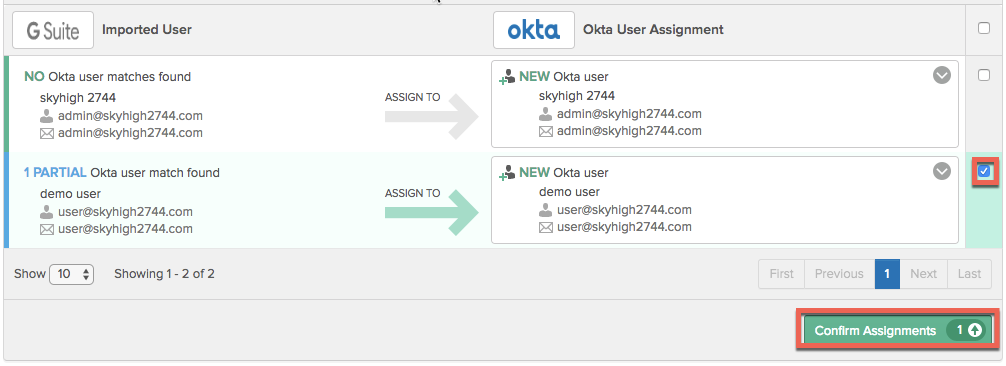
- Okta will confirm that one user will be imported. Click Confirm.
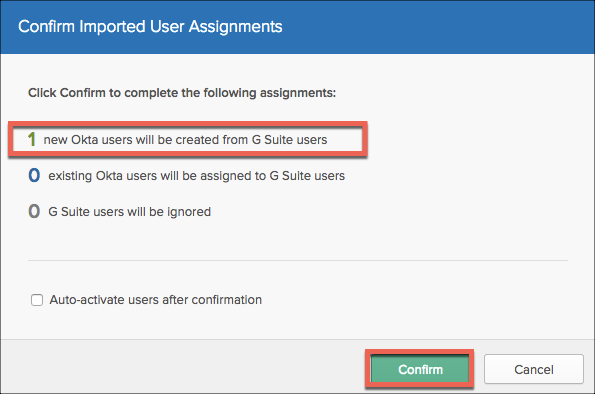
- Navigate to users and confirm the new user has automatically been created. Activate it.
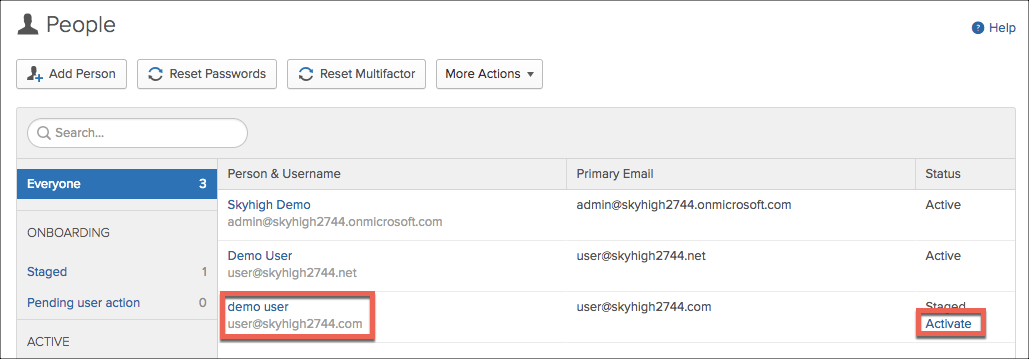
- Log in to the user's Gmail account and complete the Okta registration.

- Navigate to the GSuite Okta app Sign On page and select View Setup instructions for the SAML 2.0 setup.
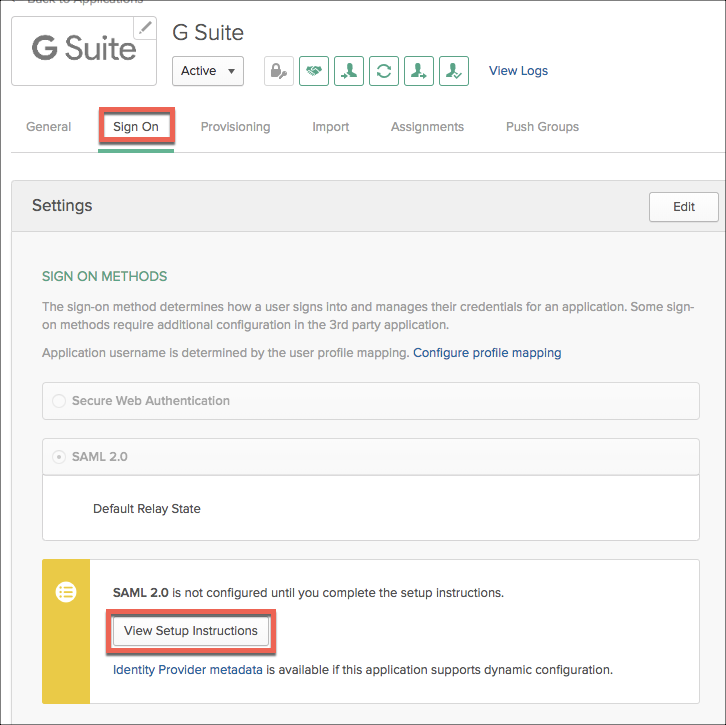
We will walk through these instructions in the next section.
Configure SSO in GSuite
- Login to the GSuite admin console (https://admin.google.com) and select Security.
- Find and select the Set up single sign-on SSO.
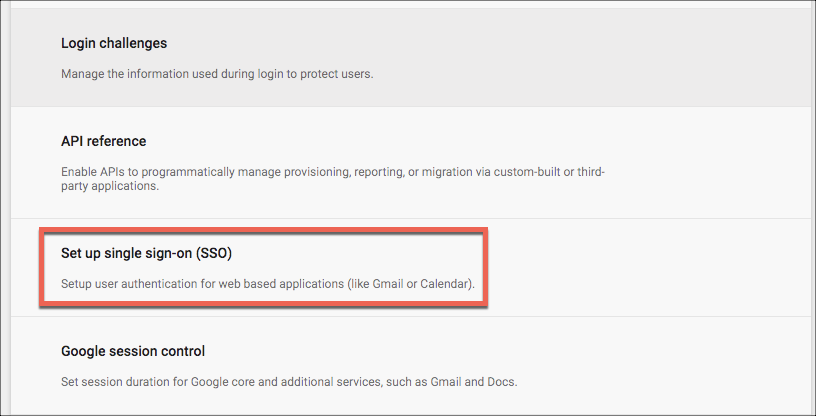
- Download the GSuite cert. This step isn't in the Okta instructions, but we will need this cert later for the SAML Proxy (SP CERT).
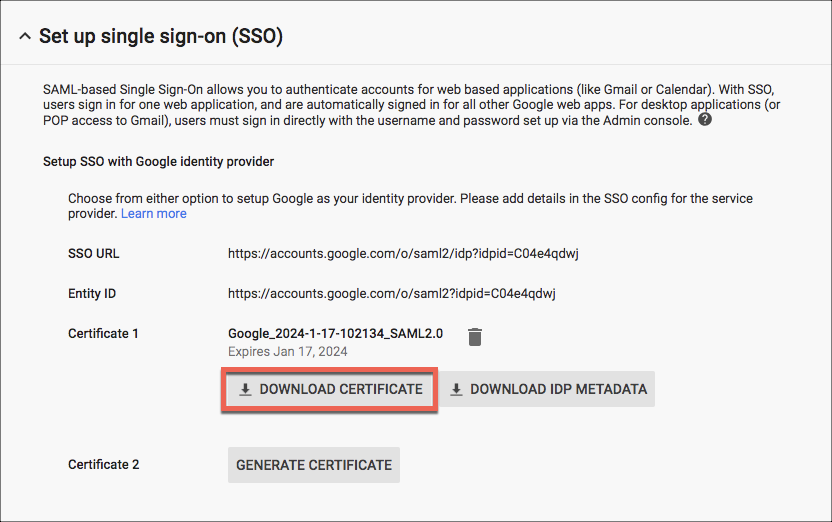
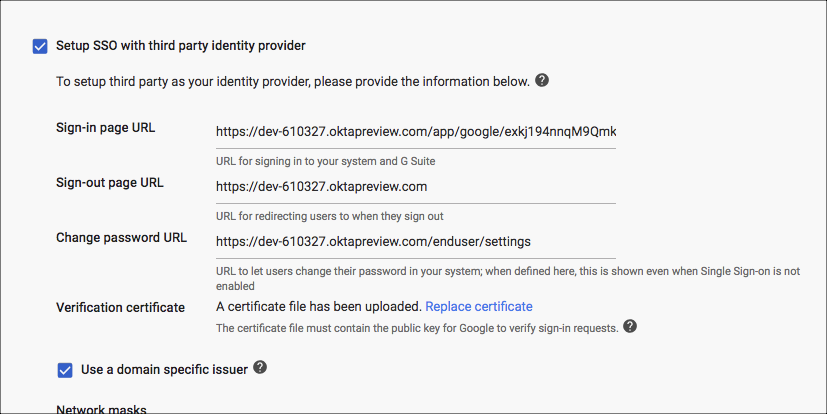
- Activate the checkboxes Setup SSO with third party identity provider and Use a domain specific issuer. Complete the fields as provided in the Okta instructions.
- Upload the Okta IDP certificate as provided in the Okta instructions. Keep this certificate for later when we configure the SAML proxy (IDP CERT).
- Click Save.
- You will be logged out of your GSuite account while SSO is enabled. Log back into the admin console and check the SSO settings. When using your admin account to access the admin console, SSO is bypassed.
Test IdP Initiated Authentication
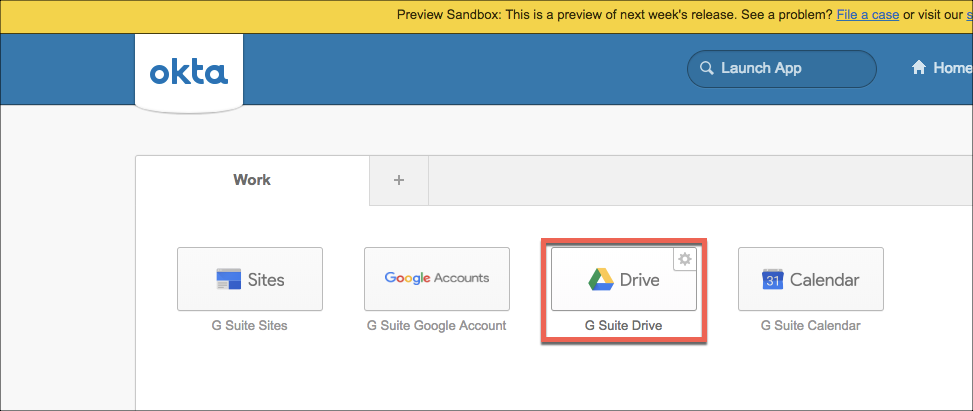
- Use a new browser or Chrome incognito window and login to Okta using your user account.
- Select GDrive from the apps window.
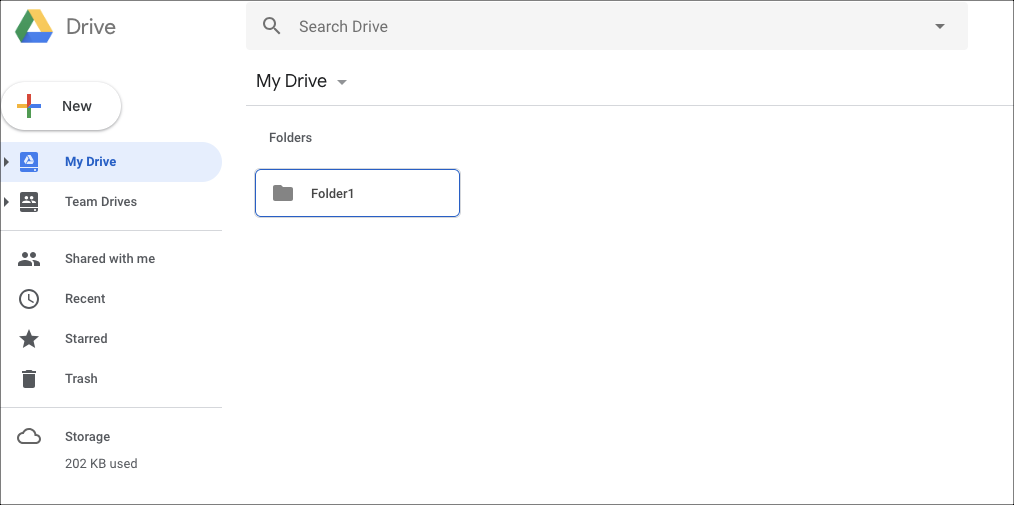
- If successful, you will be logged into GDrive automatically.
Phase 2 - Integrate the SAML Proxy
Enable the SAML Proxy
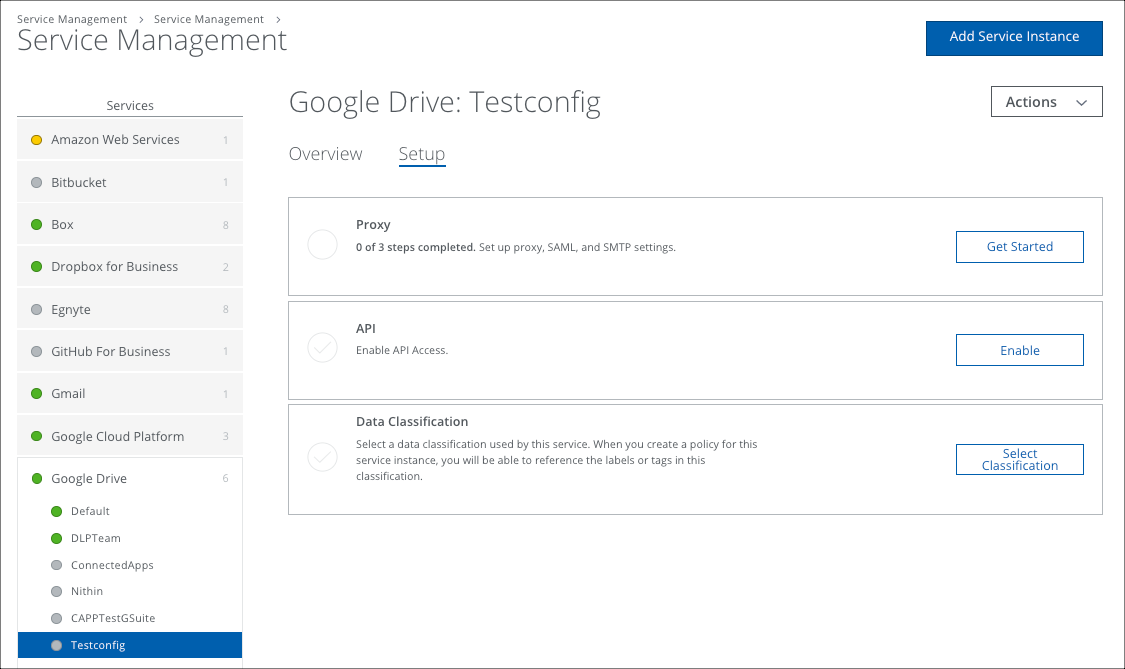
- Login to Skyhigh CASB and go to Settings > Service Management.
- Use an existing Google Drive instance, or create a new one and select the Setup tab. One the Proxy row, select Get Started.
- For Configure Proxy select Configure.
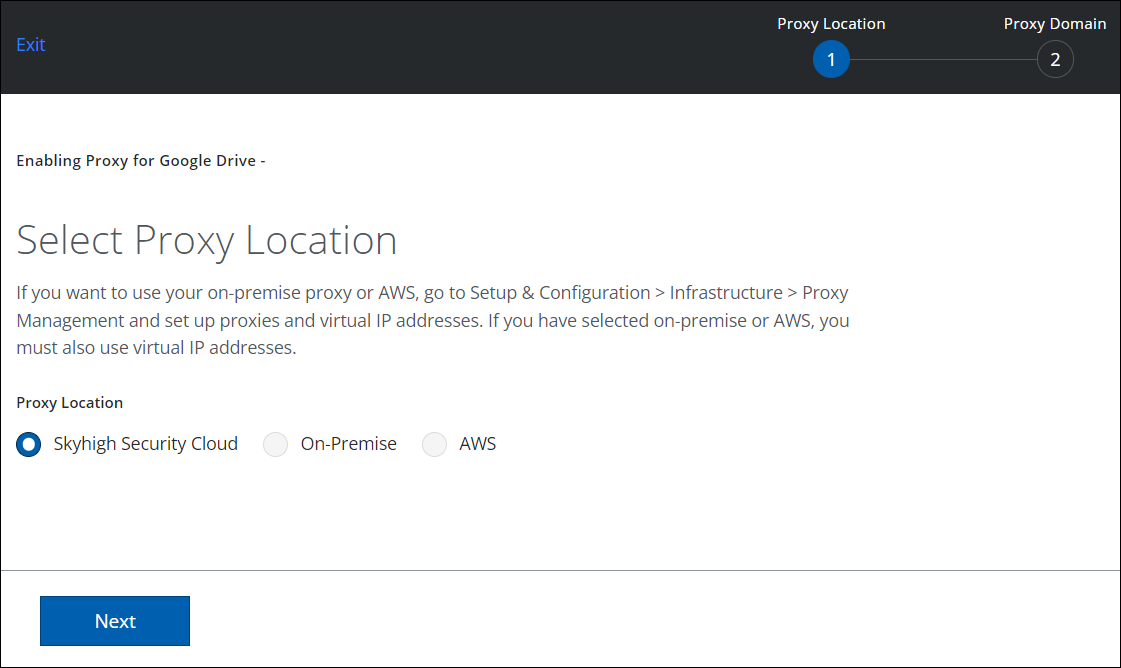
- For Proxy Location, select Skyhigh Security Cloud.
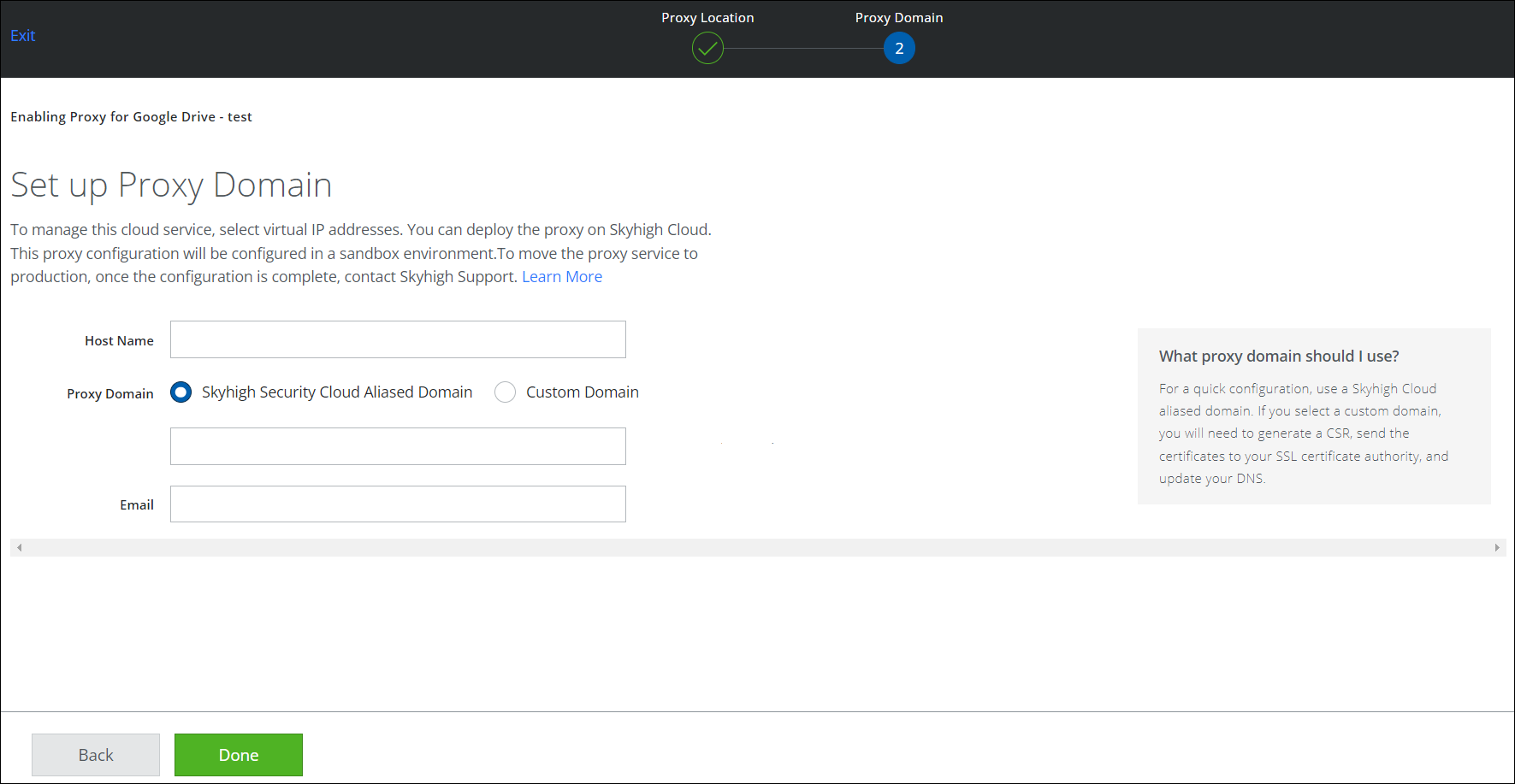
- On the Set up Proxy Domain page, accept the defaults and hit done (no input required).
- Back at the main proxy page, for SAML Proxy, select Configure.
- Upload the IDP cert collected from Okta earlier.
- Upload the SP CERT collected from GSuite earlier.
- Download the SAML Proxy certificate (SAML PROXY CERT).
- The SAML Proxy is now enabled.
- Finally, copy and keep handy the proxy URL as you will need this later.
- Paste this URL into a browser and make sure it works. If not, contact Skyhigh CASB Support. Do not continue until this works.
Reconfigure Okta to Use the SAML Proxy
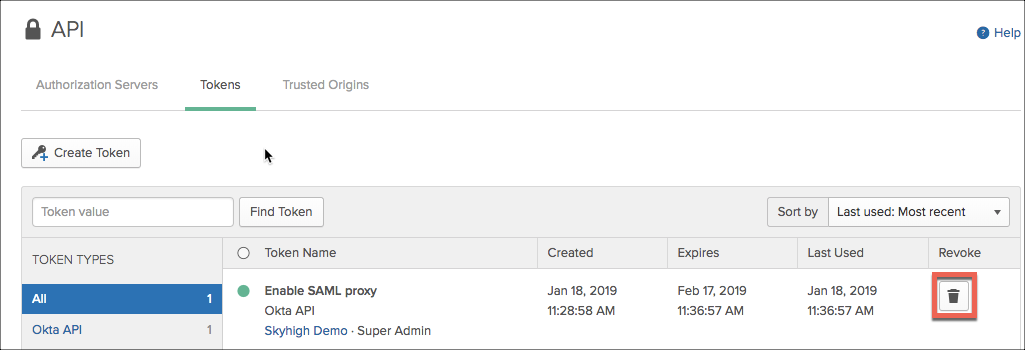
- Log in to Okta Admin and navigate to Security > API. Select the Token tab and Create Token.
- Copy the token and save it safely. Once you click the Got It, it won't be displayed again.
- Navigate to the Skyhigh CASB / Okta ACS URL tool and completed as follows:
- Okta URL. the Okta URL for your Okta tenant - just up to the .com. Do not use the -admin URL. For example, https://dev-610327.oktapreview.com.
- Okta API token. As obtained earlier from Okta.
- Skyhigh CASB proxy URL. You will need to build this parameter from your proxy domain, instance name, service name and GSuite domain to look like this. www.google.com.gsuite.def.skyhigh2241.myshn.net/a/skyhigh5459.net/acs
This is built like this:
www.google.com.<PROXY SERVICE NAME>.<INSTANCE NAME>.<TENANT DOMAIN>.myshn.net/a/<GSUITE DOMAIN>/acs
NOTE: No https:// is required on this field. See the following screenshot:
- Click Submit. You should see a list of apps obtained from Okta. Select the G Suite application and note the current URL is DEFAULT.
- Click Submit and the login URL will be changed to include the SAML proxy.
- Now check that the full Login URL as shown in the table of application reflects to this template:
https://www.google.com.<PROXY SERVICE NAME>.<INSTANCE NAME>.<TENANT DOMAIN>.myshn.net/a/<GSUITE DOMAIN>/acs?shnsaml
For example:
https://www.google.com.gsuite.def.sk...et/acs?shnsaml
NOTE: If you need to revert back, simply enter the proxy URL as 'DEFAULT' and submit.
Reconfigure GSuite to Use the SAML Proxy
- Login to the GSuite Admin Console and find the SSO settings.
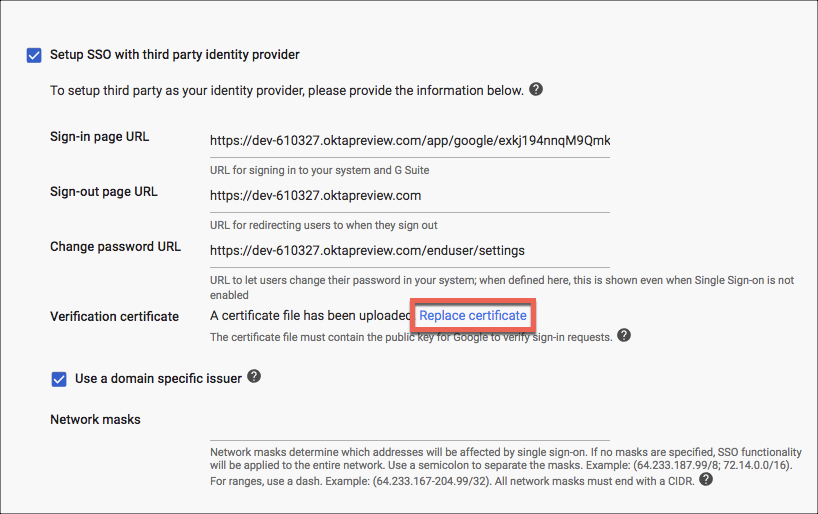
- Select Replace Certificate and upload the Skyhigh CASB proxy certificate obtained earlier.
Optional: Delete the API Token in Okta
Now that the Okta ACS has been updated to leverage the SAML Proxy, you no longer need access to the API. The token generated earlier can be revoked (as required).
Create a Cloud Access Policy
- Create a Cloud Access Policy to look for Google Drive, and check for a certificate. Managed devices will be redirected, non managed devices will be blocked.
- Test the policy by attempting to login to a Google Suite service using both a managed and unmanaged device.

