Configure Device Management for Office 365 with ADFS
When you configure Device Management for Office 365 with ADFS, the client device is directed to the Skyhigh CASB Control Point (Reverse Proxy) either through an IDP or CSP initiated redirection. The Skyhigh CASB Control Point interrogates the endpoint system for the required client certificate. The client certificate must be signed by the CA public certificate, which is imported into the Skyhigh CASB Access Security Manager. If the Endpoint has the client certificate that is signed by the CA, Skyhigh CASB considers the endpoint managed and if the Endpoint does not have the client certificate signed by the CA, Skyhigh CASB considers the endpoint unmanaged.
Skyhigh CASB proxy validates the certificate to identify the managed and unmanaged device. For a managed device, the proxy instructs the client to go directly to Office 365. For an unmanaged device, Skyhigh CASB reverse proxy blocks the notification page.
NOTE: Before you configure Device Management for Office 365 with ADFS, make sure to redirect the traffic to Skyhigh CASB. By default, ADFS and Office 365 uses WS-Fed authentication for SSO. To introduce Skyhigh CASB in between endpoint and Office 365, you need to modify the settings in ADFS to redirect the traffic to Skyhigh CASB for certificate validation.
Prerequisites
- Access to functional ADFS SSO setup for Office 365.
- Create a client certificate (public and private) using an internal Certificate Authority or PKI system.
- Distribute the client certificate (Cert+Key) to the customer's managed endpoints via an MDM, GPO, or other package management utility.
- Upload the signing certificate (public only) to the Skyhigh CASB Access Security Manager. As an optional step, you can configure the Certificate Revocation List (CRL) URL. This allows the Skyhigh CASB Access Control pane to query the CRL and determine if the existing certificates are still valid.
- Access to Skyhigh CASB admin tenant and existing Office 365 managed service.
Step 1: Configure ADFS
- Log In to the ADFS server and open ADFS Management.
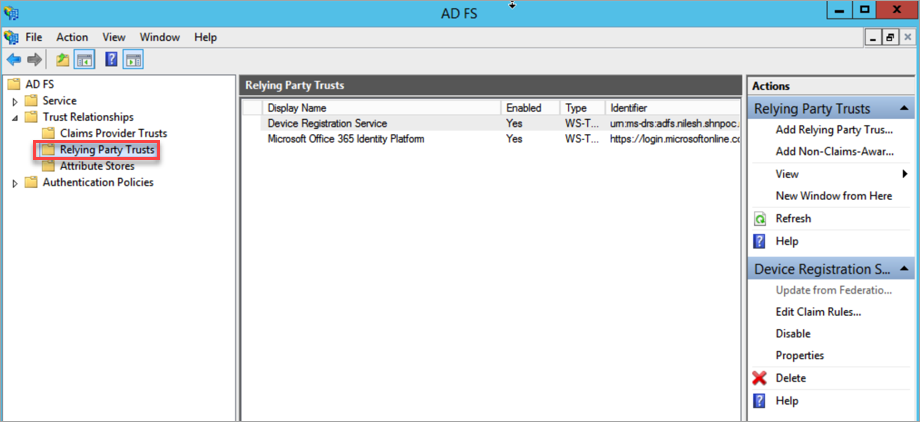
- Expand the Trust Relationships tab and click Relying Party Trusts.
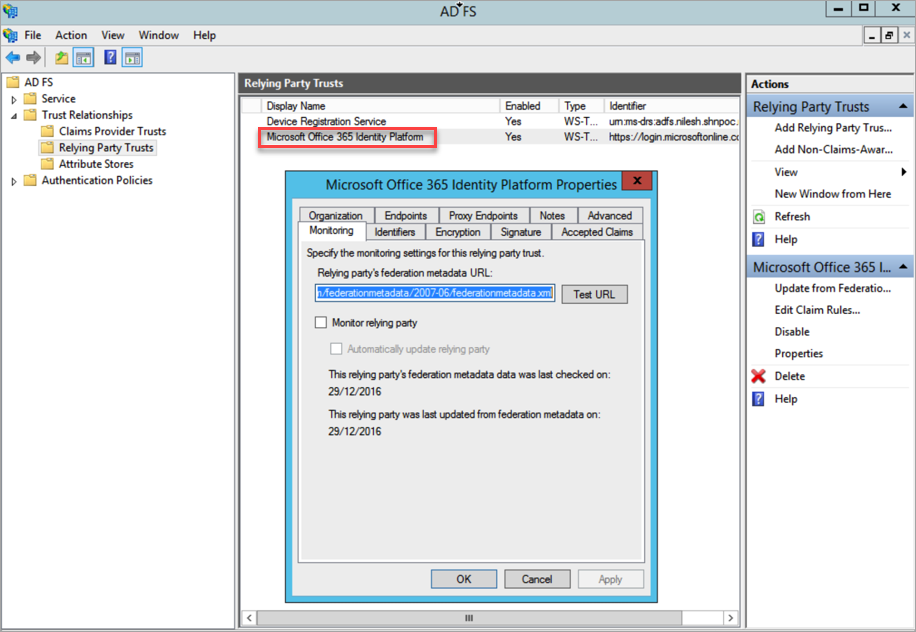
- Click Microsoft Office 365 Identity Platform and open properties. This option is created by default when you establish SSO with Office 365.
- Go to the Endpoints tab and double click the WS-Federation Passive Endpoints URL and modify the trusted URL:
- Replace the existing URL https://login.microsoftonline.com/login.srf? with the new URL https://login.microsoftonline.com<Skyhigh_Proxy_URL>/login.srf?shnsaml=
NOTES:
- To get the URL specific to your tenant, contact Skyhigh CASB Support.
- Do not forget to append the “=” symbol towards the end of the new URL. This is an important parameter used to redirect the user to Skyhigh CASB.
- To apply the settings, click OK.
NOTE: Before you begin to configure device management settings, verify whether your traffic is being redirected to Skyhigh CASB Proxy from ADFS. If your traffic is redirected, then you can start with the next step.
Step 2: Configure Device Management for Office 365 in Skyhigh CASB
- Log In to Skyhigh CASB as admin.
- Go to Policy > Access Control > Device Management.
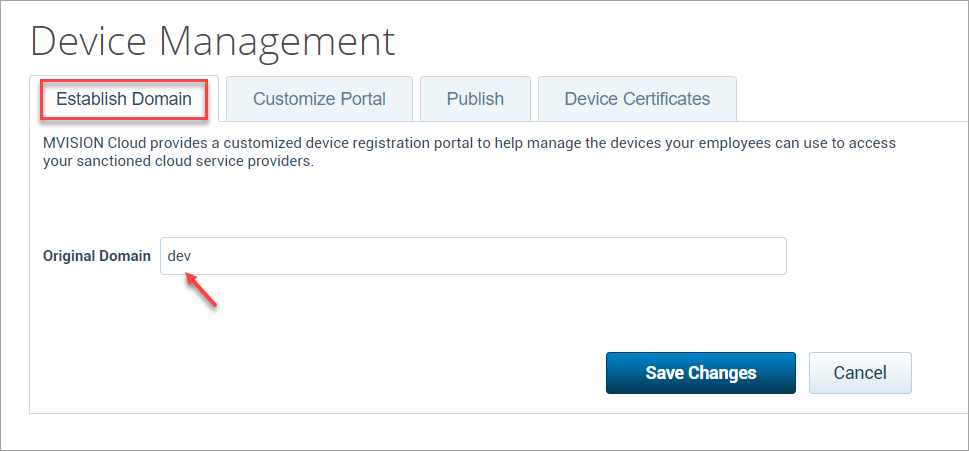
- Under Establish Domain, enter the Original Domain as Device.
- Under Device Certificates, activate the Enable Certificate Checks and configure these fields:
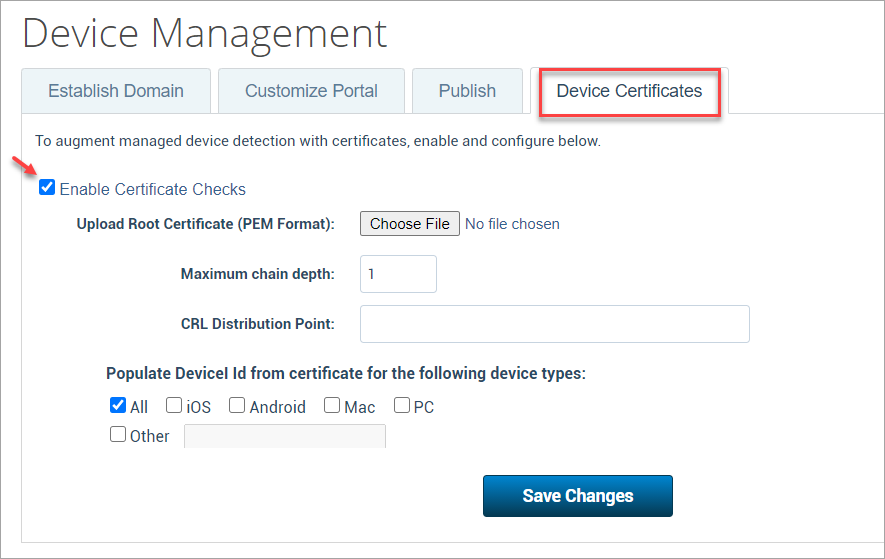
- Upload Root Certificate (PEM Format). Browse and upload the CA certificate of MDM or CA authority provided by the customer.
- Maximum chain depth. The chain depth number should be equal to the number of certificates in the chain.
NOTES:
- If you have more than one certificate (Root and intermediates), combine all of them to make a certificate chain.
- You don't have to activate the populated Device ID option only if you are performing the certificate checks and not integrating with MDM.
- Publish tab is required only when you are performing SAML proxy with SAML as an authentication protocol. Portal registration should be turned off when you are performing only Certificate validation.
- Click Save Changes.

