Office 365 Lightning Link (Real-time Collaboration Control)
Lightning Link is used to apply real-time controls using Office 365 synchronous events to monitor the activity of external users accessing the sensitive documents and block. Previously, you could define Sanctioned DLP policy types for API and Reverse Proxy deployments. While Reverse Proxy policies are used to apply inline controls using Skyhigh CASB reverse proxy solution, API policies are used to enforce compliance policies in near-real-time (after the user activity is complete).
Using only API policies leaves a window of potential data leaks: from the time the file or folder is shared with an external user to the time Skyhigh CASB's API policy takes effect and removes sharing for external users. This window could be up to 2–3 minutes and external users might access the sensitive document if they open the link sent to their emails immediately.
Lightning Link policies provide an additional layer of protection by monitoring the activity of external users accessing sensitive documents and blocking them in real-time without having to deploy a proxy.
But, real-time policies only work with document metadata tags and do not support content-based rules such as Data-Identifier, Keyword, and Regular Expression.
Lightning Link Policies
Only the following rules are supported in Lightning Link policies:
- Classification
- Collaboration for Files and Folders
- Collaboration for Shared Links > Anyone on web. No Sign-in required.
- Collaboration for Shared Links > Anyone in organization with link. Anyone at a specified company who has the link can access it. Sign-in required.
- File Name
- File Path/Folder ID
The following rules are not supported:
- Content rules such as Data-Identifier, Keywords, and Structured Data Fingerprint.
- Metadata rules File Type, and File Size
Block is the only response action available with Send email notification to.
Collaboration Rules for Shared Links
Lightning Link policies can be used to monitor and block the activity of generating anonymously shared links or shared links with organization-wide access. To achieve this, use Collaboration rules for Shared Links. This way, the shared link generation is blocked during the time of generating the shared link itself.
Collaboration Rules for Files and Folders
Use Collaboration rules for Files and Folders to enforce a Lightning Link policy for external users based on their email/domain. But, depending on whether your Office 365 tenant has the latest sharing experience rolled out by Microsoft, the blocking can happen either during the time of inviting these external collaborators or during the time of external users accessing the shared file or folder. See below for more information.
- The behavior described below is applicable only if you are inviting specific people by using the share option in SharePoint/OneDrive (applicable for policies with Collaboration rules for files or folders).
- Microsoft is rolling out a new sharing experience for Office 365 (described here). If your tenant has the new sharing functionality, external users receive a unique link for the file or folder shared with them and they have to enter an OTP (sent to their email) when they try to access the link from email invite (previously external users were expected to log in with an Office 365 account or any other Microsoft account which isn't a requirement anymore). With this new external sharing experience, Lightning Link cannot block external user collaboration during the time of inviting external users (as this information isn't available then) but blocks external users based on policy match, when they are trying to access the link. Hence, use Lightning Link as an additional layer of protection on top of regular near real-time policies as it covers the scenario of external users accessing the sensitive data before near real-time policies can take effect and remove external sharing (a potential data leakage window of up to 2 minutes).
- If your Office 365 tenant doesn't yet have the above external user sharing experience described above, the following behavior applies.
- If an external user is invited to a file or folder for the first time in any given SharePoint site, the collaboration invite email is sent to the external user, but the user is not allowed to access the file or folder using the link. (Our real-time collaboration control listeners are invoked when an external user tries to access the link.) Also, when the first-time user is blocked from accessing the link, the domains/users specified in the from part of the collaboration rule is not considered. This means a first-time user is blocked no matter who invited the user, as long as the user is a match according to the domains/users specified in the to section of the collaboration policy.
Classifying Documents for API Deployments
For API deployments, all documents with sensitive data in OneDrive/SharePoint must have appropriate classification names assigned before real-time policies can be applied to control collaboration activity on these documents. You must define DLP policies to scan the content of the document in near real-time and classify the documents based on policy match.
All content-based DLP rules, such as Data-Identifier, Keywords, and Structured/Unstructured Data Fingerprint can be used with the Classification rule to tag sensitive documents in OneDrive/SharePoint. It is possible to define multiple document classifications in the same policy by specifying a comma-separated classification values.
IMPORTANT: To classify documents already created/updated before deploying Skyhigh CASB for Office 365, define the policies as shown, and run an On-Demand Scan by attaching these policies.
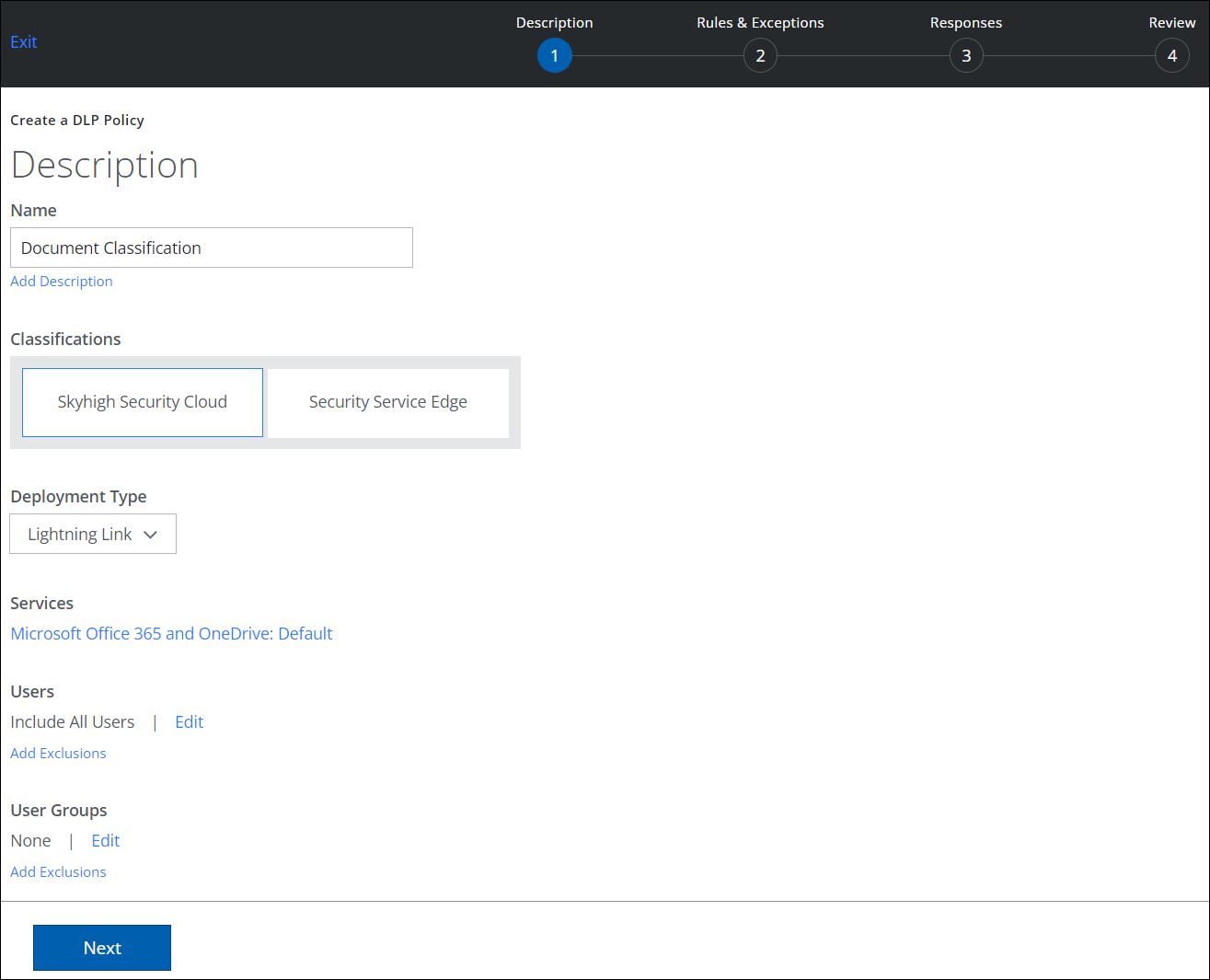
See the following example policy, which detects confidential keywords in documents and classifies those documents with a classification name of SensitiveDataType and value of Confidential.
NOTE: This policy is of type API and the documents are scanned for sensitive content and classified in near real-time after the documents are uploaded/updated in SharePoint/OneDrive.
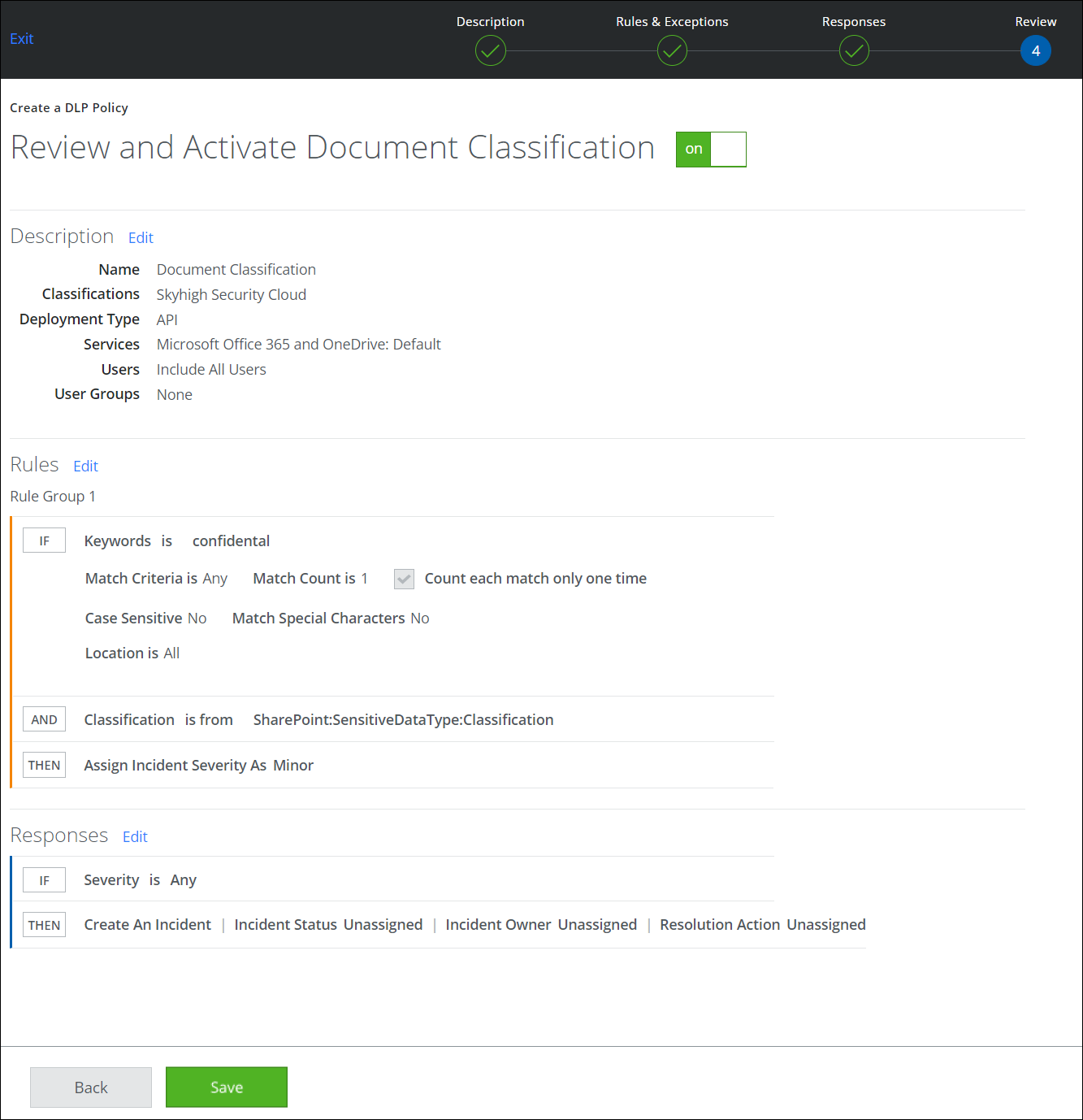
This diagram defines how document tags are applied in near real-time:
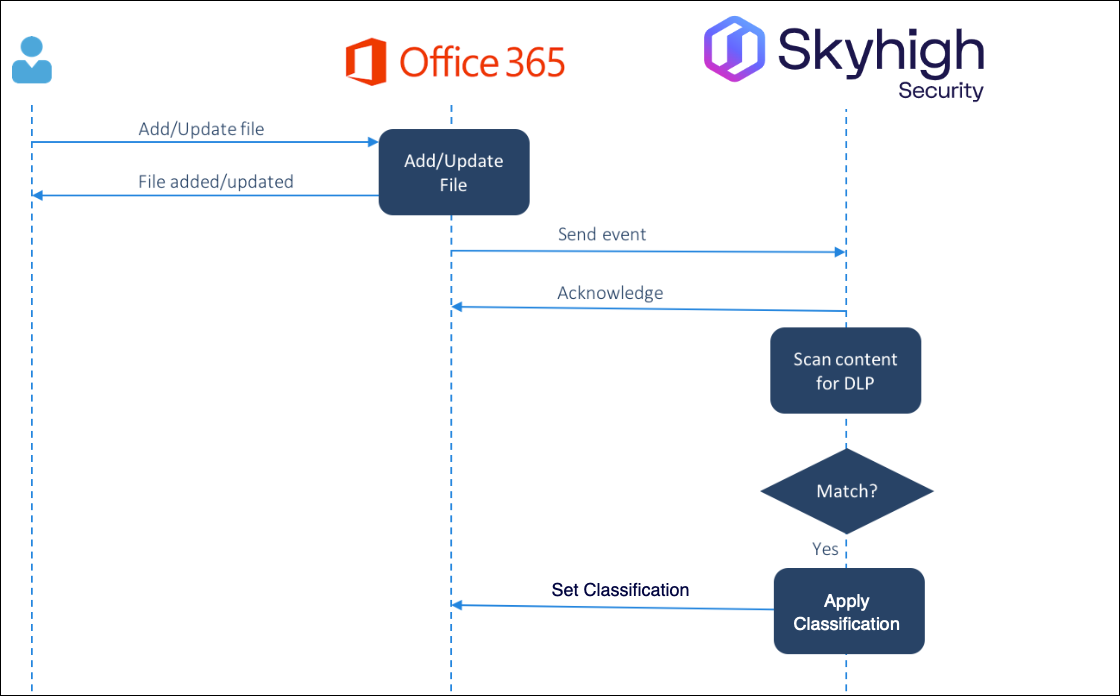
Block Sharing Sensitive Data for Lightning Link Deployments
This policy example defines a Rule that acts on a shared file (or folder having one or more files) using the classification SensitiveDataType and value Confidential. The Response prevents external users from the gmail.com domain from accessing the document.
NOTE: Once active, this policy also blocks access to external users on a folder having one or more files with a given document classification either directly in that folder or in any of the subfolders (at any level).
Enable Synchronous Events in the SharePoint Add-in/App
Finally, enable Synchronous Events in the SharePoint Add-in/App. Once enabled, Skyhigh CASB registers synchronous event listeners with your Office 365 environment to monitor and block sharing activity in real-time.
- Select one of the following:
- Automatically monitor all site collections and any new site collection added in future:
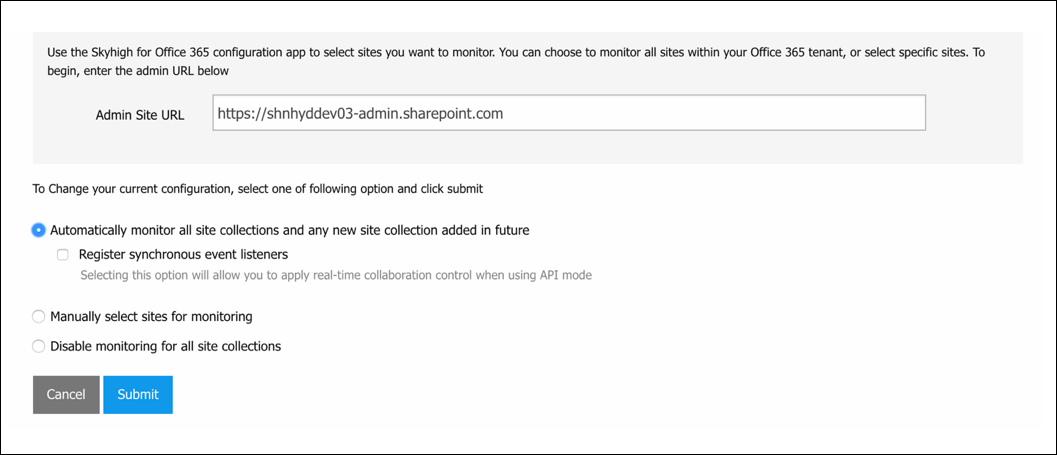
- Manually select sites for monitoring, to pick only some sites to monitor.
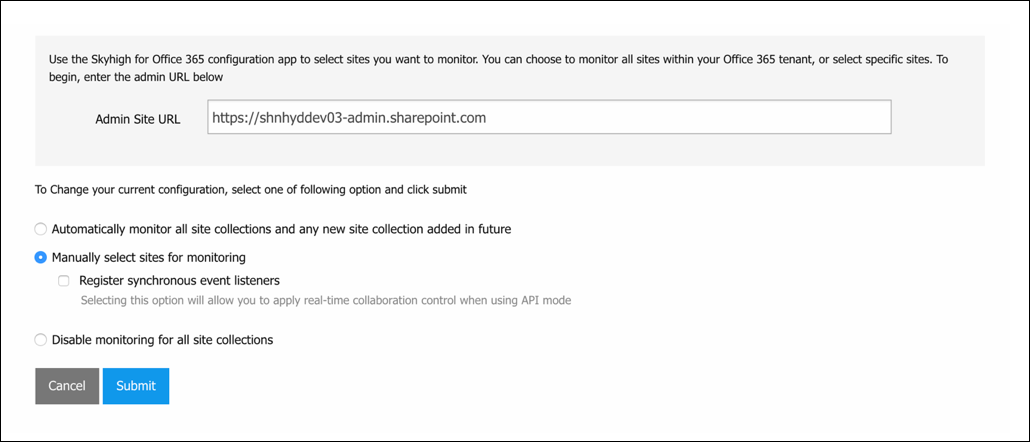
- Click Submit.

