About Skyhigh CASB
Skyhigh CASB is the leading Cloud Access Security Broker (CASB), a cloud-based, multi-tenant service that enables companies to embrace cloud services with appropriate levels of security and governance while lowering overall risk and cost. It acts as the first line of defense of the cloud service by providing organizations with real-time control over their data.
The goal of Skyhigh CASB is to prevent cloud security failures and ensure that cloud services and applications are always protected.
Cloud Services
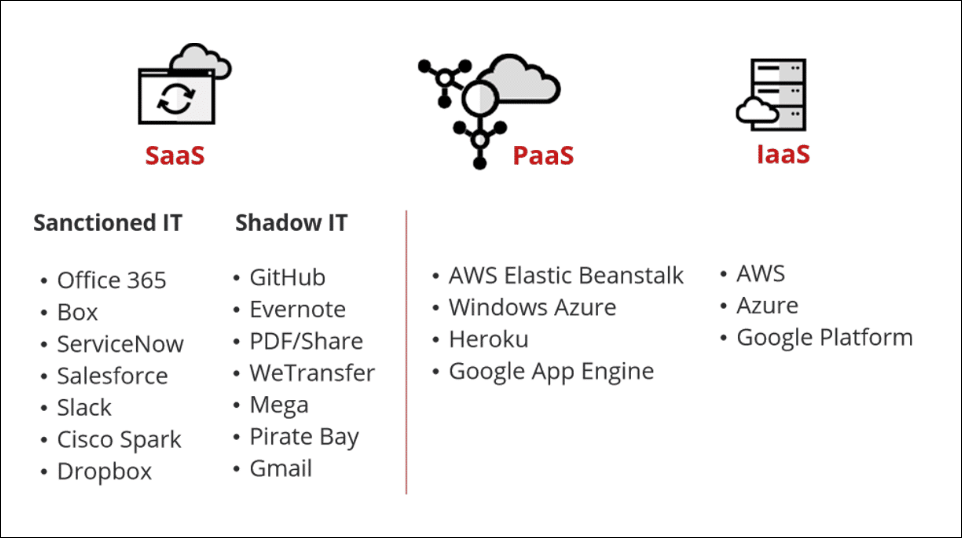
There are three models of cloud services that Skyhigh CASB takes into consideration: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
SaaS refers to the usage of applications and can be sub-categorized into two services:
- Sanctioned IT services - Includes company-approved services such as Office 365, Box, ServiceNow, and Salesforce, which are deployed across the entire organization and approved by the IT department.
- Shadow IT services - Include other services in use but may or may not be supported through the organization’s IT department. These include applications like GitHub, Evernote, PDF/Share, or social media applications such as Facebook and Weibo.
PaaS provides computing platforms that include operating systems, programming language, windows, and databases. Examples include AWS Elastic Beanstalk, Windows Azure, Heroku, and Google App Engine.
IaaS refers to renting a space on an external server to run your applications. The main providers of these services are AWS, Azure, and Google Platform. You can also use these services to run custom-developed applications.
Skyhigh Security Cloud is designed to secure all three models.
SaaS
Skyhigh Security Cloud for SaaS enables the secure adoption of cloud services by providing activity monitoring, threat detection, data protection, and configuration auditing. With these cloud-native controls in place, organizations can benefit from cloud transformation without sacrificing the security of their data or users.
Customers deploying Skyhigh Security Cloud for SaaS can immediately benefit from centralized activity monitoring. Departments can get a clear understanding of how these cloud applications are used, leverage machine learning to identify trends, detect various levels of anomalies and threats, and have a centralized location from which to conduct investigations.
Shadow IT
Skyhigh Security Cloud Shadow IT provides visibility into cloud applications used in an organization that goes above and beyond what traditional Firewall and Proxy Log analytics are capable of.
The Skyhigh Cloud Registry, which provides a 50+ attribute risk assessment for more than 20,000 cloud services, is the primary driver behind this. The Cloud Registry allows Skyhigh Security customers to go beyond service categorization (cloud storage, CRM, productivity, etc.) and evaluate the risk of each service according to its attributes.
Access Points
One of the great benefits of having services in the cloud is that they can be accessed from anywhere and from any device. Access points, in simple terms, are the different ways in which data in the cloud can be accessed.
There are three access points that CASB considers - Users, Devices, and Network.
Users
Who is accessing the cloud applications?
- Employees
- Partners
- Vendors
- Customers
Devices
How are they accessing the cloud applications?
- Desktops
- Laptops
- Smartphones
Network
How are they connecting to the cloud applications?
- Corporate network
- VPN
- Home-office Wi-Fi
- Public networks
Skyhigh Security Cloud Features
Skyhigh Security Cloud strives to provide cloud security with four main product features: Visibility, Compliance, Data Security, and Threat Protection.
Visibility
- Identifies sensitive data and different user groups.
- Performs On-demand Scans to identify sensitive content.
- Conducts continuous risk assessments.
- Maintains the Cloud Registry.
- Gain visibility into unsanctioned applications and control their functionality.
Compliance
- Set regulations for violations of sensitive data.
- Puts additional controls in place for certain groups.
- Enforce data loss prevention (DLP) policies on data in the cloud, in sync with your endpoint DLP and helps to intercept, delete, and quarantine data.
- Audit for misconfiguration against industry benchmarks and automatically change settings.
Data Security
- Aims to stop data breaches before they occur.
- Shuts down access to the cloud, limits user ability to read-only, and provides encryption services.
- Adds increased authentication requirements for suspected anomalous activities.
- Prevent unauthorized sharing of sensitive data to the wrong people.
- Block sync/download of corporate data to personal devices.
- Container optimized strategies for securing dynamic and ever-changing container workloads and the infrastructure on which they depend.
Threat Protection
- Detects anomalous activity.
- Detects insider threats and compromised accounts and malware.
- Detects brute force login attempts.
Control Points
Control points decide how you control data traffic flowing to and from the cloud. Skyhigh Security Cloud provides a multi-mode deployment that covers all their use cases across all users, devices, and services. Broadly, they can be categorized into two modes:
- Out-of-band Deployment Modes. These deployment modes use asynchronous APIs that help cover traffic from user-to-cloud as well as from cloud-to-cloud.
- Inline Deployment Modes. These deployment modes refer to a proxy that sits between the traffic from user-to-cloud and cloud-to-cloud. To implement inline controls, CASB can be implemented in forward and reverse proxy mode.

