Skyhigh Security for ChatGPT
Prerequisites
Make sure that you have any one of the following products to begin with:
- Skyhigh Security Shadow IT
- Skyhigh SSE (Cloud Proxy)
or
- Skyhigh Secure Web Gateway
About Skyhigh Security Capabilities for ChatGPT
This topic explains how Skyhigh Security can assist organizations with Artificial Intelligence (AI) tools such as ChatGPT. Skyhigh Security provides administrators the ability to manage AI applications in their Cloud, Hybrid, and On-Prem deployments via the following features:
- Increased visibility for ChatGPT in your organization.
- Determine the volume of data being uploaded.
- Identify which of your top talkers/users are using ChatGPT.
- Block complete access to ChatGPT and other AI applications.
- Apply specific controls, such as blocking uploads or logging into ChatGPT.
- Prevent sensitive data from being uploaded to ChatGPT.
Visibility
Monitor Usage
Skyhigh Security allows you to monitor the usage of ChatGPT along with other AI services within your organization via these pages:
- Analytics > Services
- Analytics > Web > Web Traffic
Services
Skyhigh CASB allows you to use the Services page to monitor the usage of AI services within your organization. The Services page displays metrics on cloud usage in your organization. Use this page to search, filter, and drill down to view the required information for AI services. For details, see About Services.
You must first create a saved view to save your AI services search query, and then create a corresponding My Dashboard card to monitor the usage of AI services within your organization. For example, you can create a dashboard card based on the saved view to track the trend in the usage of high risk AI services over a period of time or to track the data usage of high risk AI services in breakdowns. For details, see Create a Saved View and Dashboard Card.
To monitor the usage of AI services:
- In Skyhigh CASB, go to Analytics > Services.
- Use the omnibar to search for AI services, or select Artificial Intelligence as the Service Category.
- Select a date range for your search using the Date Picker.
- Save View. Click to create a Saved View from your AI services search query. You can use the same Saved View for multiple dashboard cards.
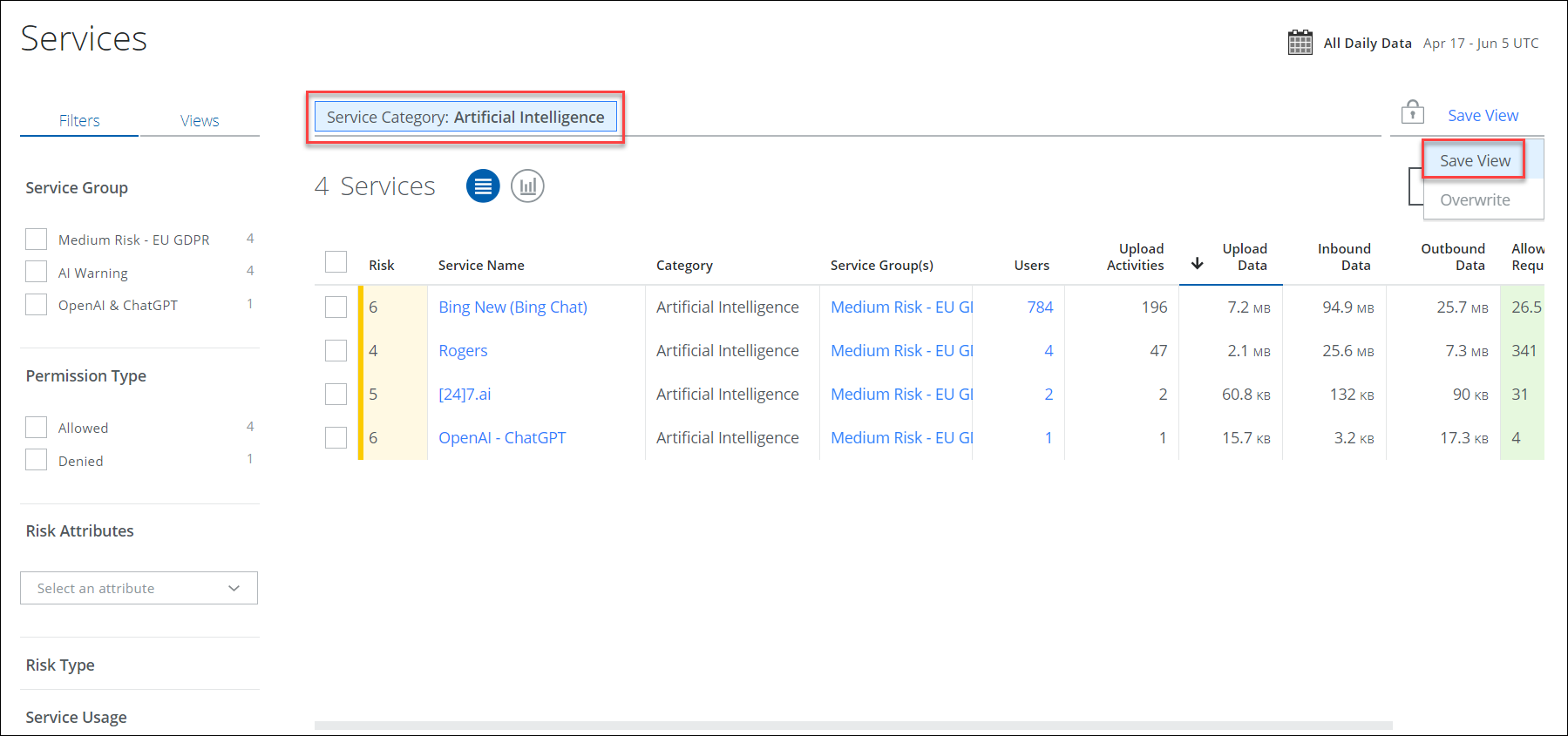
- In the Save A New View dialog:
- Name your Saved View. Enter a unique name for the view. (If you enter a name of a Saved View that is already being used, you see an error message. Enter a different name.)
- Make Public Within Your Company. Activate the checkbox to make the saved view public within your company.
- Add a Dashboard card. Activate the checkbox to add a dashboard card for the saved view.
By default, the dashboard card for the saved view displays a breakdown of the data for AI services based on the top services by total data volume.
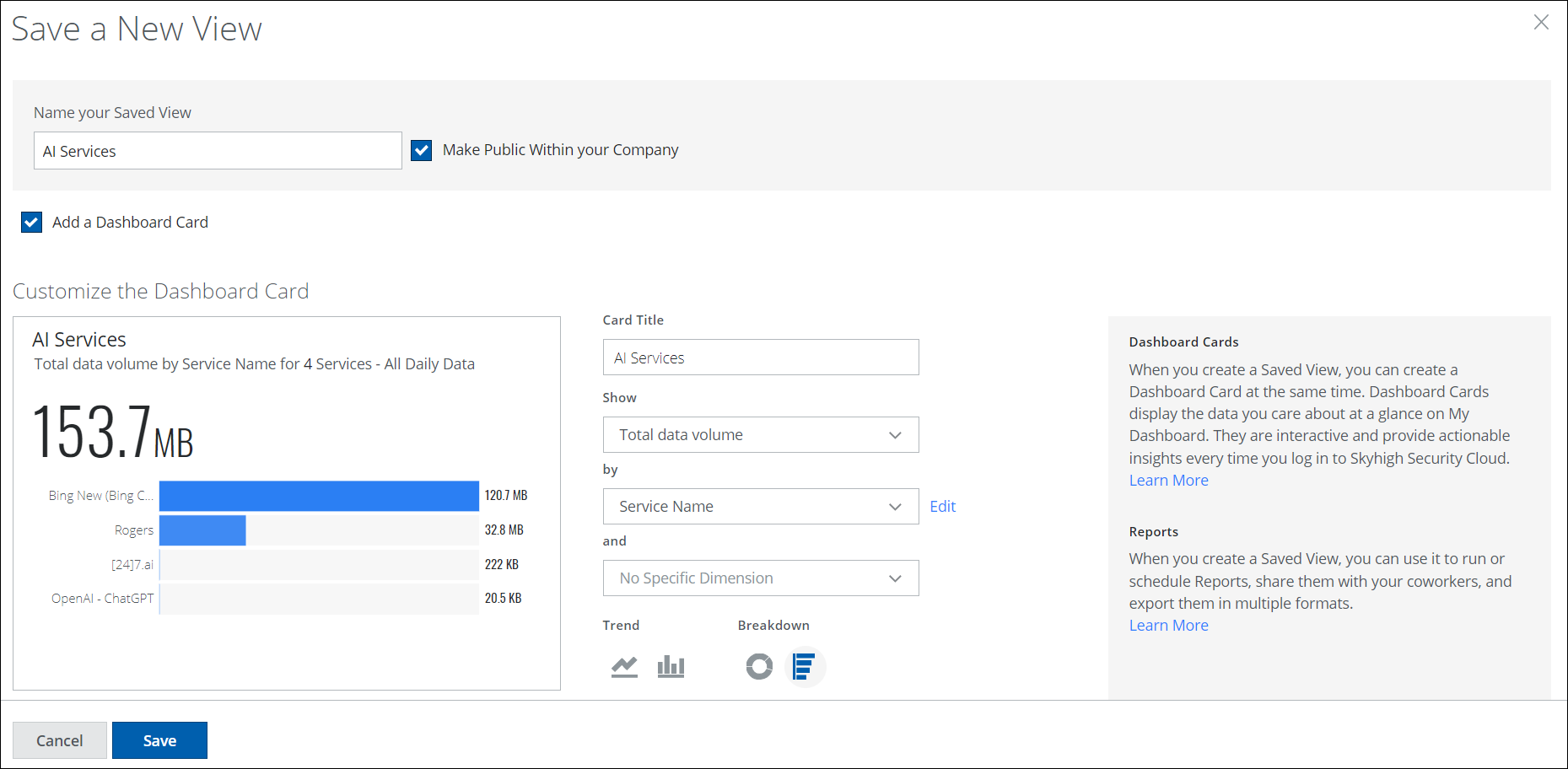
- Card Title. The name of the Saved View. You can change this to any unique name.
- Show. Select the primary filter to display. For example, select Number of services.
- by. Select the second filter to display. For example, select Risk Type, and then select High Risk.
- and. Select the dimension if available.
- Trend or Breakdown. Select the type of chart you would like to use.
- Trend: Trendline or Vertical bar. For example, select trendline.
- Breakdown: Donut or Vertical bar.
- Click Save.
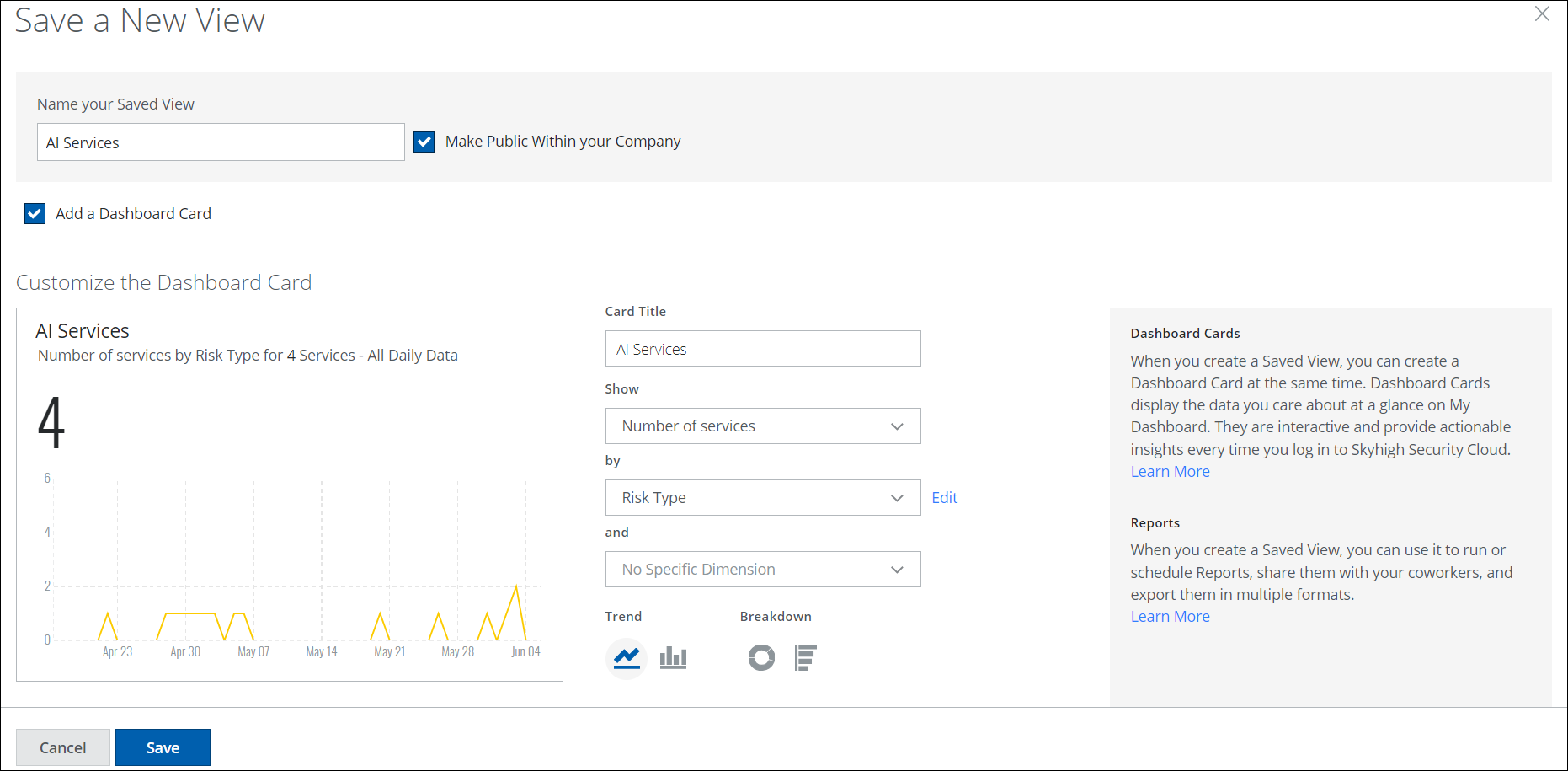
Your search is automatically run, and your Saved View appears in the Views tab. The newly created dashboard card appears as the last card on your Dashboard.
Assess Risk of AI Services
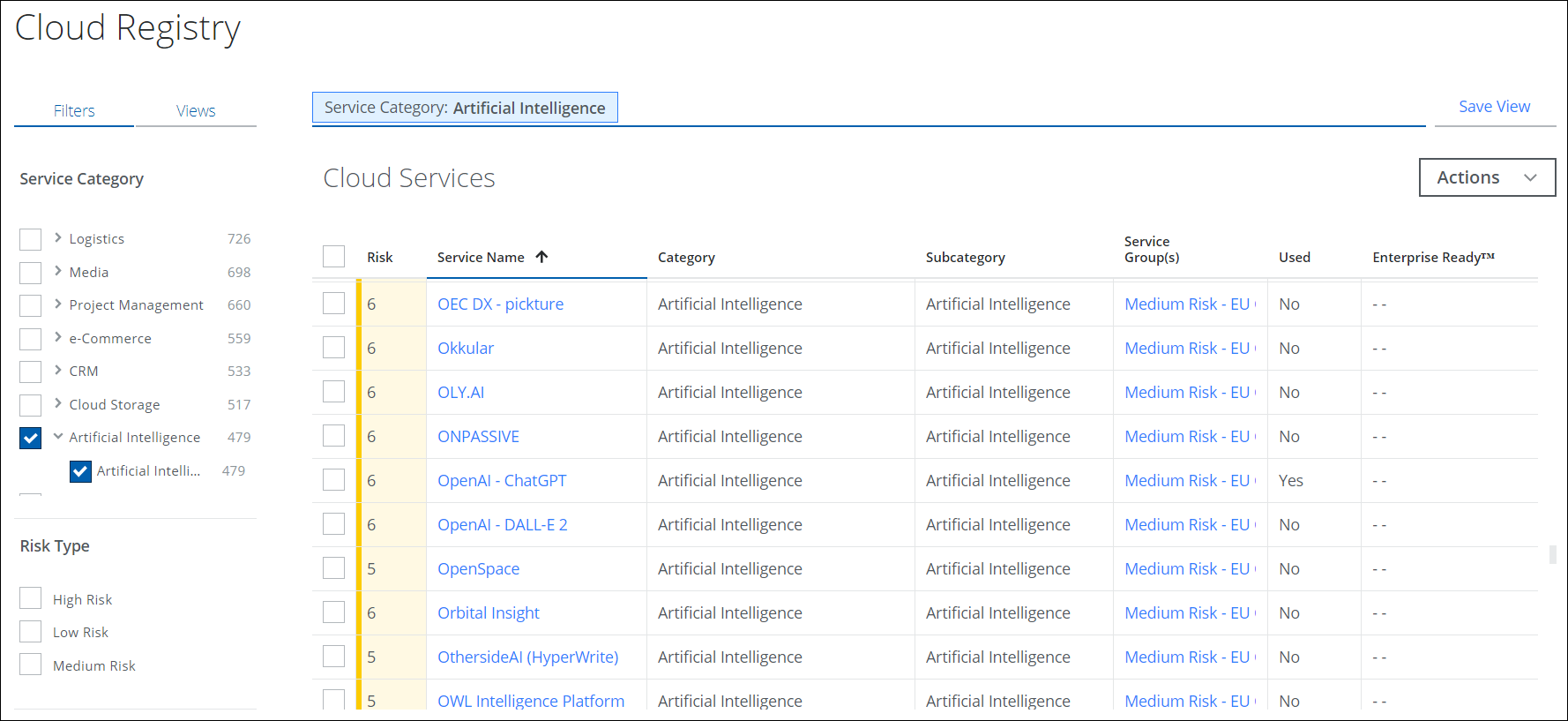
Skyhigh CASB allows you to assess the risk posture of all AI services used within your organization. The Cloud Registry page (Governance > Cloud Registry) provides users with the ability to search for AI services and view its risk scores and risk reports. You can filter AI services by multiple attributes including Category, Risk, Service Group, Active/Inactive, and Custom Attributes. For example, organizations can leverage this page to allow or block users from using ChatGPT within their organization. For details, see About the Cloud Registry.
To assess risk of AI Services:
- In Skyhigh CASB, go to Governance > Cloud Registry.
- Use the omnibar to search for AI services, or select Artificial Intelligence as the Service Category.
- Click the OpenAI - ChatGPT link in the table to display the Service Details page.
-
The Service Details page provides an overview of the risk assessment for ChatGPT and displays the advantages and disadvantages that contribute to its service risk score. For details, see Service Details Page.
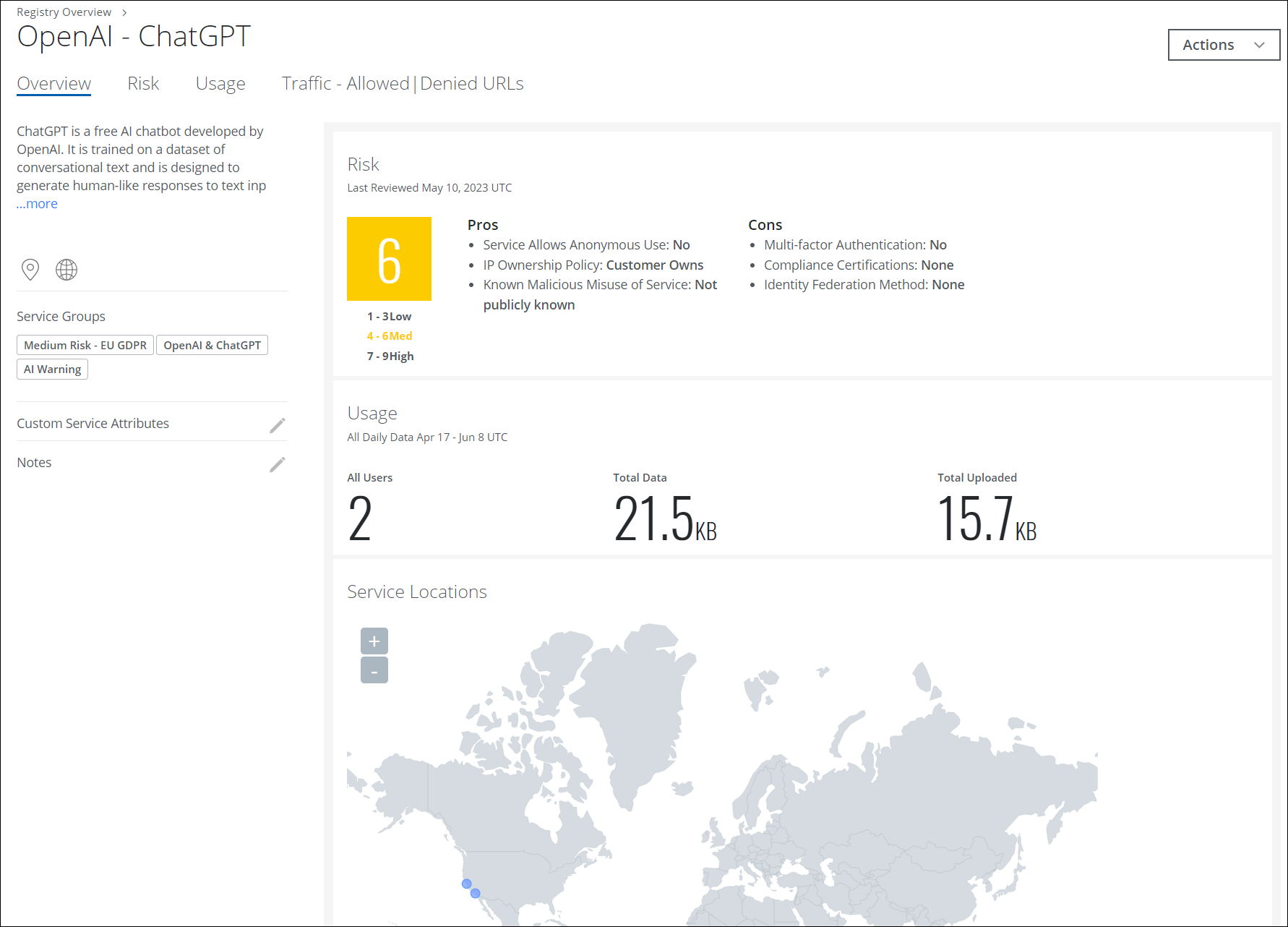
Understand Data Usage
You can leverage your Shadow IT data to determine the number of users and the volume of data uploaded to the ChatGPT service. For details, see About Services.
Use the OpenAI – ChatGPT filter to determine the following:
- Number of users using the ChatGPT site.
- Data volume linked with the ChatGPT site.
- Your existing proxy/firewall is blocking or allowing access to the ChatGPT site.
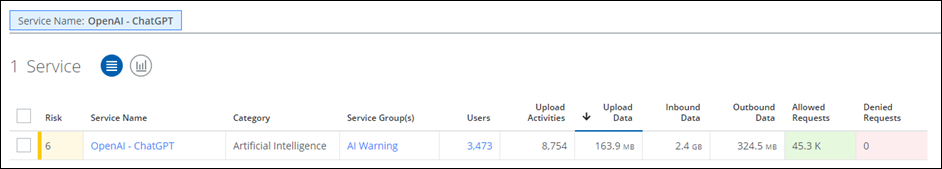
Block AI Services (Completely)
Create Skyhigh Service Groups
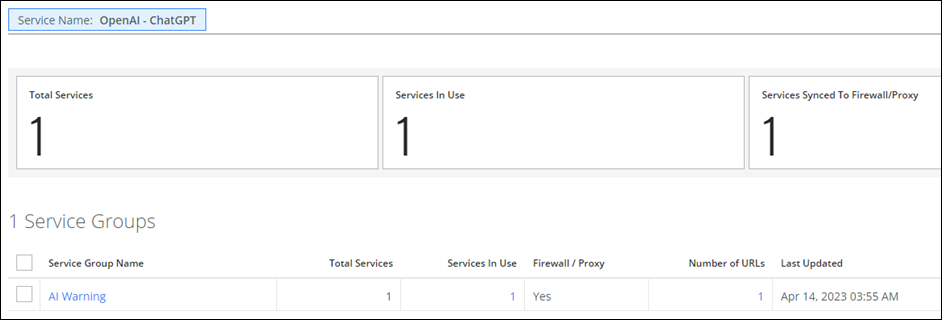
Skyhigh Security allows you to create a service group on the Skyhigh CASB dashboard based on the Artificial Intelligence category or the OpenAI - ChatGPT service name. The following example uses an AI Warning service group to share this information with your proxy/firewall. For details, see Create a Service Group.
Skyhigh CASB allows you to block all the AI services used within your organization based on service groups. The Service Groups page (Governance > Service Groups) provides users with the ability to create service groups, to categorize AI services into groups for Service Governance purposes.
To block AI services completely:
- Go to Governance > Service Groups.
- On the Service Groups page, go to Actions > Create Service Group.
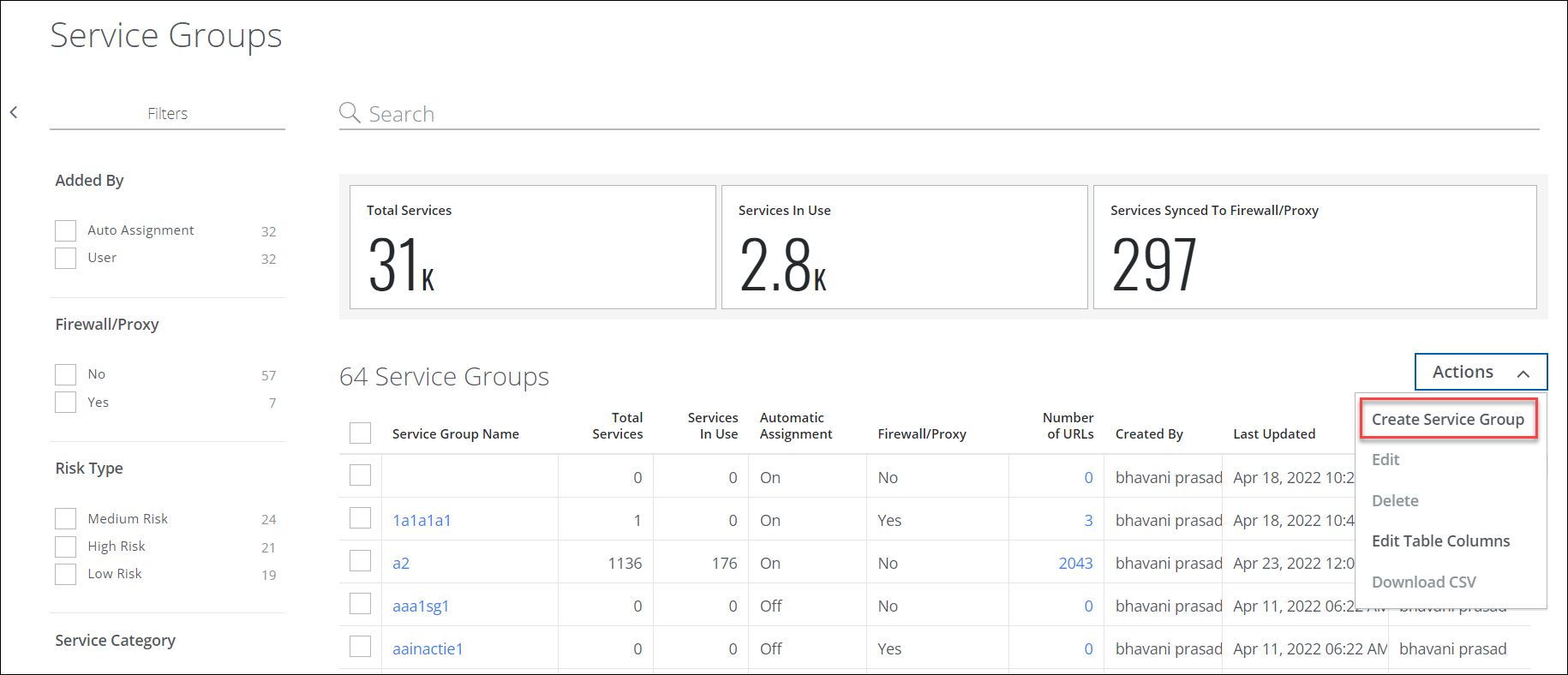
- Configure the following:
- Name. Enter a name to identify the Service Group.
- Description. Enter a description for your reference.
- Toggle Auto Assignment on and click Add Rules. This allows you to automatically add AI services to the service group.
- Under Auto Assignment Rules:
- Click Select to select the Rules parameters. For example, select Service Category from the list.
- Click Is, and select the values from the list. For example, select Artificial Intelligence.
- Add and apply the rules:
- If you want the rule to match the required rules or conditions, use IF, THEN logic.
- If you want the rule to match ANY rule, use OR logic.
- If you want the rule to match ALL rules, use AND logic.
- If you want the rule to state as not true, use NOT logic.
- Click Save.
NOTES
- You can name the service group based on your requirement.
- Skyhigh Security recommends that you create dynamic service groups using the Artificial Intelligence category.
Configure Closed Loop Remediation
You must configure Closed Loop Remediation so that your Skyhigh environment acts as an external web server, providing a URL to be used in the destination field of your proxy/firewall rule set. You can now copy and paste the link of the newly published service group for AI services into the destination field of your proxy/firewall rule set. For details, see About Firewall and Proxy Integrations.
Once done, you can then choose whether to block or coach users who attempt to access ChatGPT and other AI services. The published URL of the service group for AI services looks like this:
-
https://t76172-1001862871.do.myshn.net:8443/clr/serviceGroups/AI%20Warning?deviceId=2
Block AI Services (based on User Activity)
You can block the AI services used within your organization based on the user activity (login, upload) as shown in the following example from Skyhigh SSE Cloud Proxy.
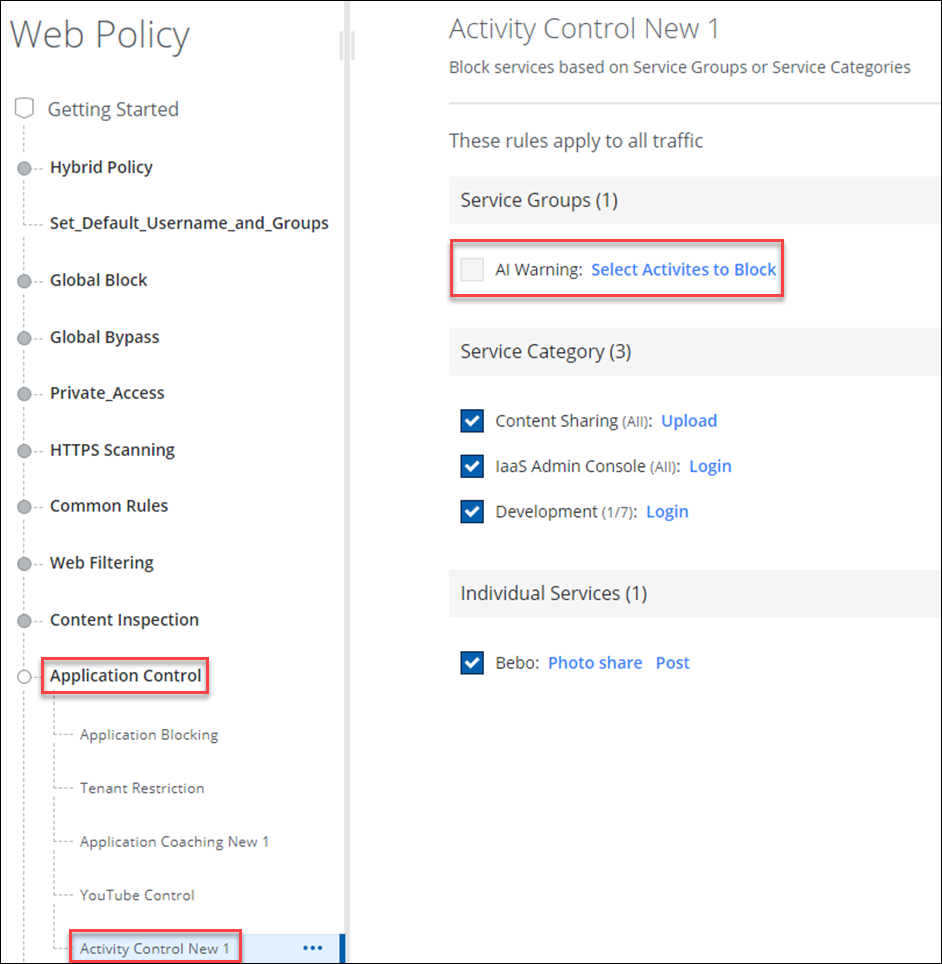
- Under Web Policy > Application Control, select Activity Control.
- Apply these activity controls to the AI Warning service group created earlier to this configuration.
- Edit these rules to apply to all traffic, and add the ChatGPT URL/Domain/Host information.
NOTE: For Secure Web Gateway (On-Prem) users, contact your Skyhigh Security engineer to understand how this is set up in the App Prism ruleset.
Coach users but allow access to ChatGPT
Skyhigh Security allows you to limit access to AI services used within your organization by providing access only to users with a business justification.
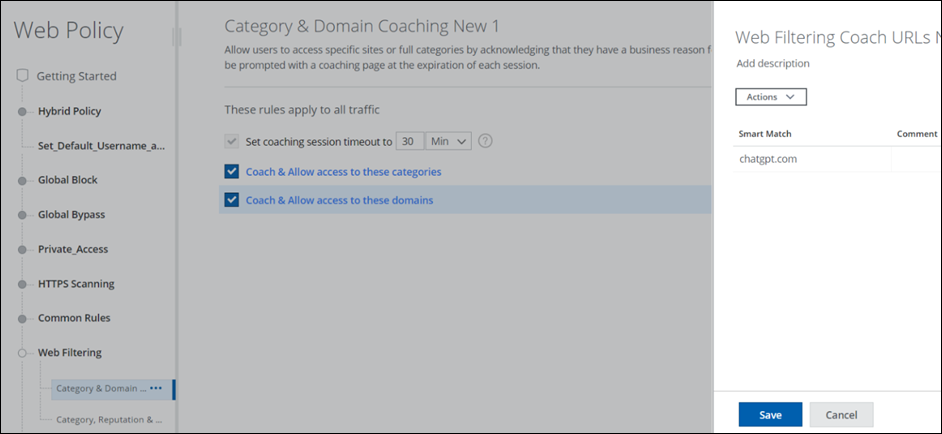
- Go to Web Policy > Web Filtering.
- Select or configure the Category & Domain Coaching rule.
- Select and edit Coach & Allow access to these domains.
- When presented, populate Smart Match with the ChatGPT domain under the Add New items view.
- Click Save, and Publish your policy.
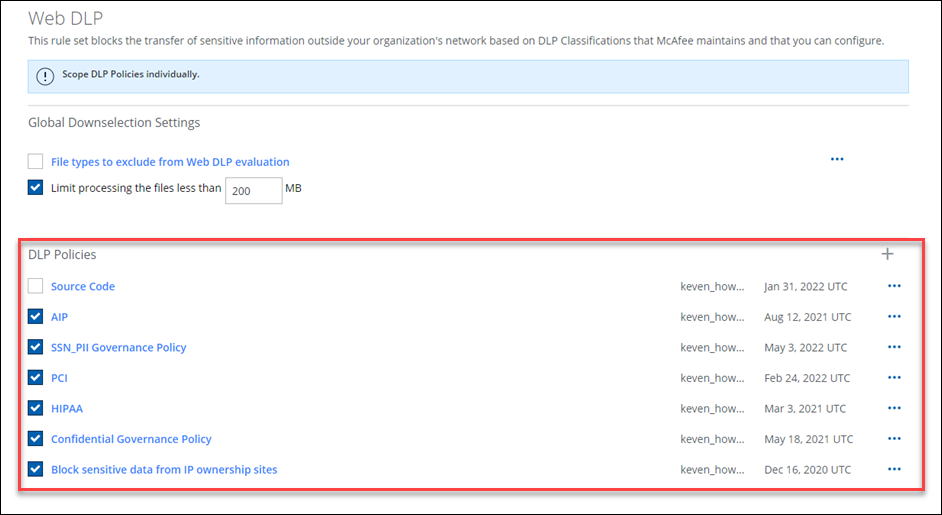
Coach with DLP filtering applied
Skyhigh Security allows you to block sensitive information or DLP (Data Loss Prevention) content from leaving the organization.
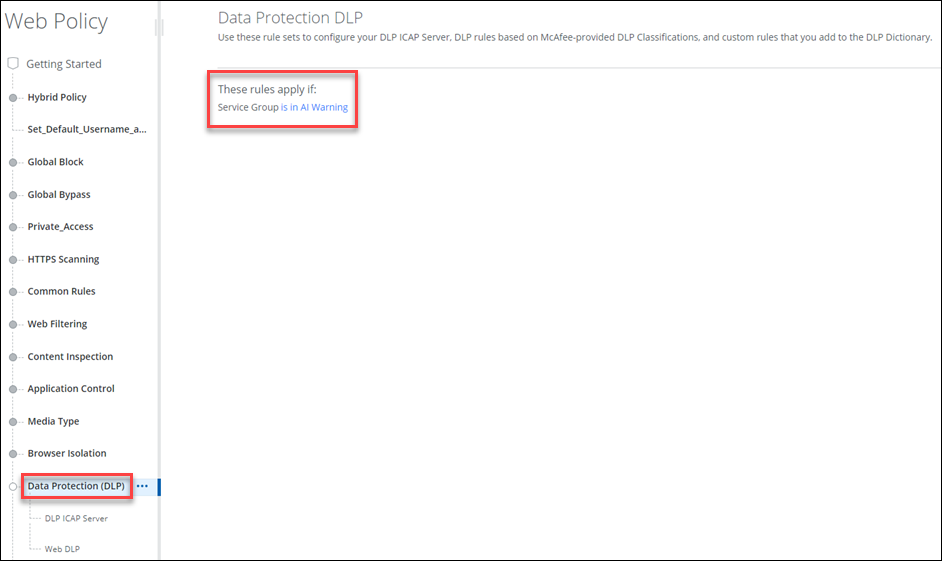
- Go to Web Policy > Data Protection (DLP).
- Select or configure These rules apply to all traffic, then choose URL/Domain/Host to populate the ChatGPT URL/Domain/Host information or select the AI service group.
- Create or build DLP Classifications within your DLP policies to only block content that matches your DLP Classifications and is posted to your AI service group or ChatGPT url.
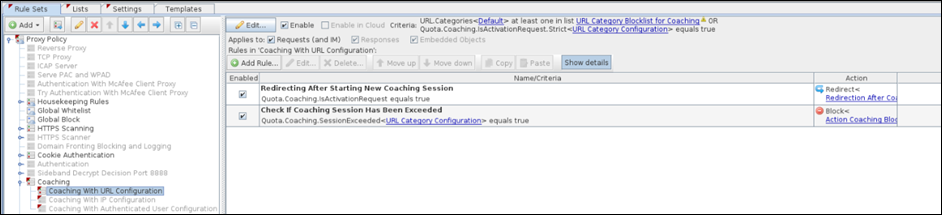
Security Controls for AI Services (Secure Web Gateway (On-Prem) users)
If you are using Skyhigh Security Shadow IT or SSE/UCE, you can use the lists generated from the Skyhigh Cloud Registry to perform activities such as block, monitor, coach by subscribing to those lists in your policies. For details, see Configure Closed Loop Remediation.
If you are using Secure Web Gateway (On-Prem), then coaching or blocking on-premise must be done via a URL list obtained from an external source because there is no built-in AI category or list. For coaching, you can use the standard coaching ruleset and modify the base ruleset as follows:
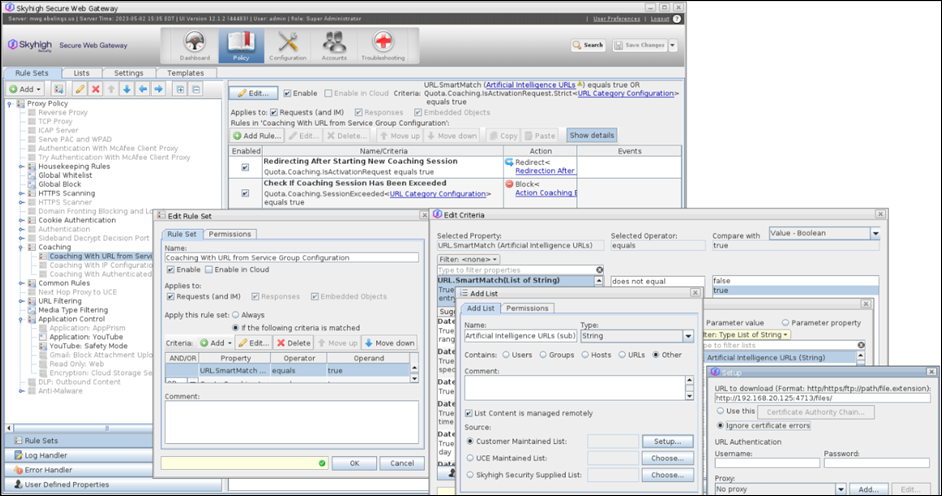
While syncing a DLP policy from Secure Web Gateway to the cloud, Skyhigh Security recommends using the standard coaching ruleset for Secure Web Gateway (On-Prem) filtering, and the Coaching with Cookies ruleset for the cloud. You can do this by using criteria in the cloud which equals True for the cookie-based ruleset and False for the standard coaching ruleset.
NOTES
- The Coaching with Cookies ruleset is available on the online ruleset library found at contentsecurity.skyhigh.cloud.
- The standard coaching and Coaching with Cookies rulesets are enabled, but only the cookie-based ruleset is set to sync to the cloud.

